Method and apparatus for detecting same wireless terminal
A wireless terminal and detection unit technology, applied in security devices, wireless communication, selection devices, etc., can solve the problem of inability to identify authenticity and other problems, and achieve the effect of reducing fraudulent behavior and reducing harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
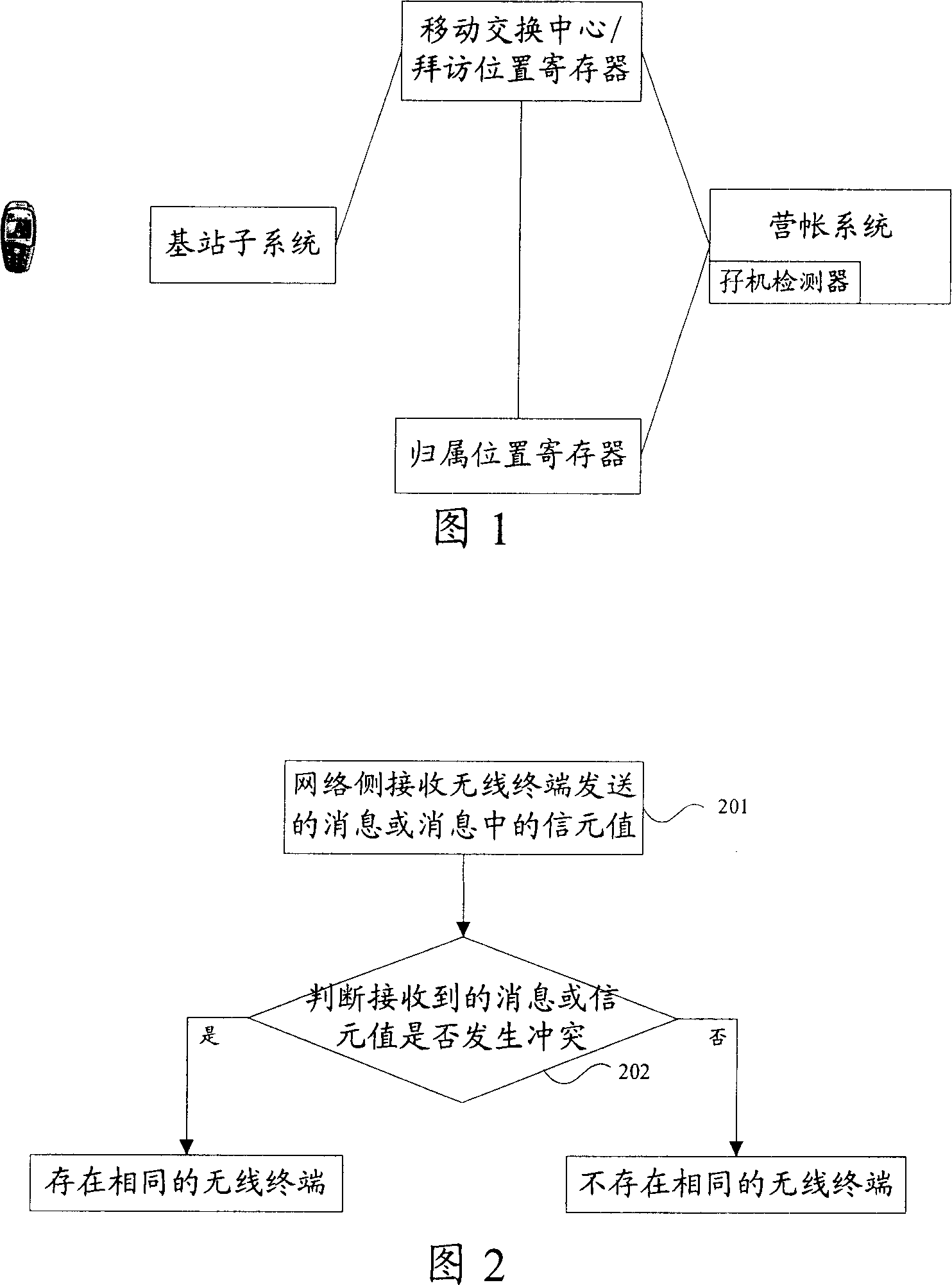
[0058] In this embodiment, it is determined whether there is the same wireless terminal by detecting the call counter value returned by the wireless terminal. The value of the call counter (count) can be regularly updated through the home location register on the network side, and issued to wireless terminals within the jurisdiction. The network side compares the latest count value reported by the wireless terminal with the latest count value saved by the network side, and if they are not the same, it indicates that the same wireless terminal exists. The service may be but not limited to voice service, short message service or data service, and the wireless terminal will report the latest count value saved by itself in the message of initiating or accepting the above services.
[0059] The principle of this method is: the updated count value sent by the HLR is received by one of the host or the clone wireless terminal, while the count value saved in the other is not updated, s...
Embodiment 2
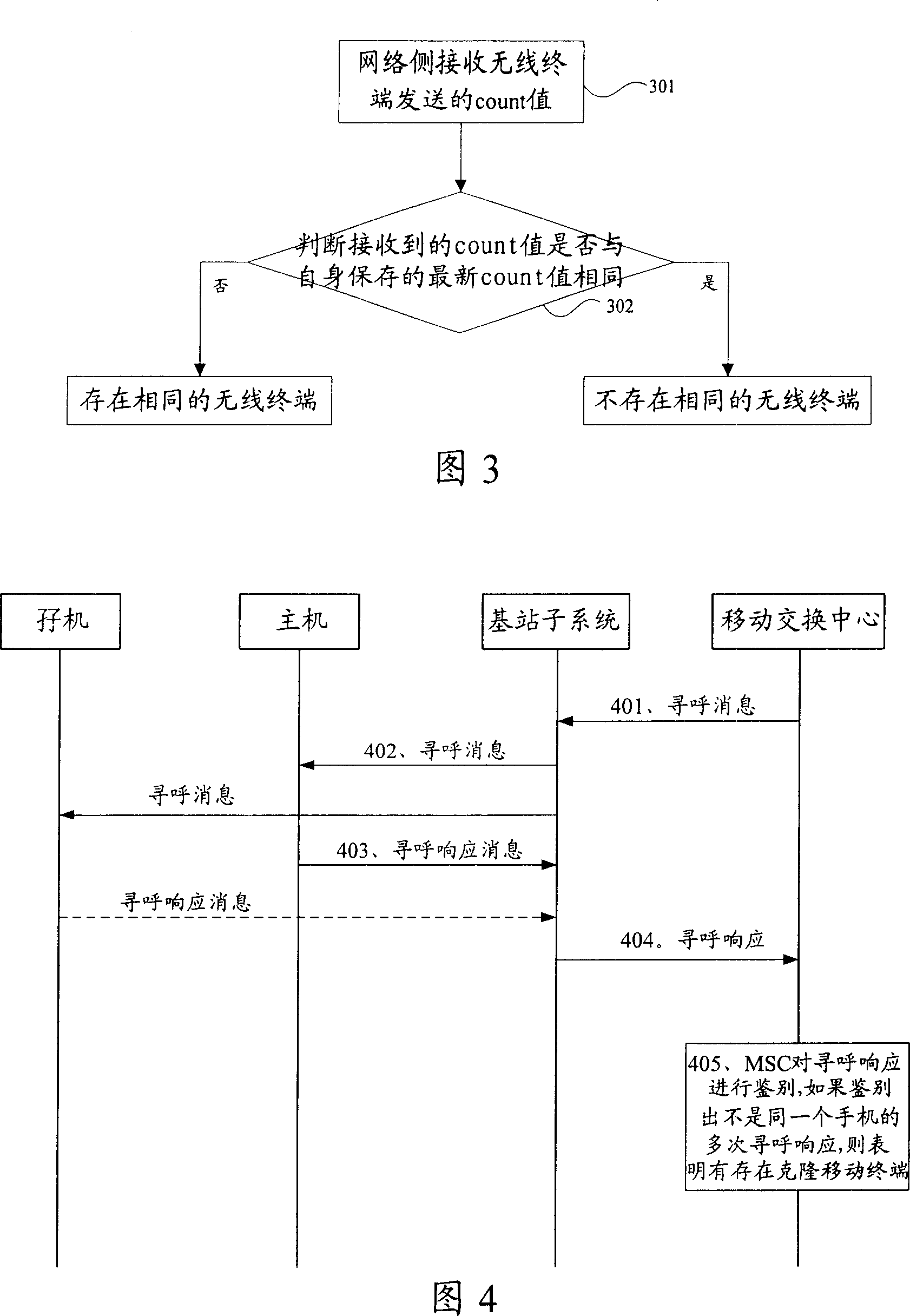
[0065] In this embodiment, it is determined whether there is the same wireless terminal by detecting the paging response message returned by the wireless terminal. That is, the MSC judges whether there is a cloned wireless terminal of the called party user according to receiving multiple paging response messages. FIG. 4 is a flowchart of a method for detecting the same wireless terminal according to a paging response message in this embodiment. The method specifically includes the following steps:
[0066] In step 401, the MSC sends a paging message to the base station subsystem (BSS) to page the called user.
[0067] Step 402, the BSS pages the wireless terminal through the paging channel on the air interface. Since the International Mobile Subscriber Identity (IMSI) and Electronic Serial Number (ESN) of the cloned wireless terminal user are the same as those of the host, the cloned wireless terminal user can also receive and process the paging message on the air interface. ...
Embodiment 3
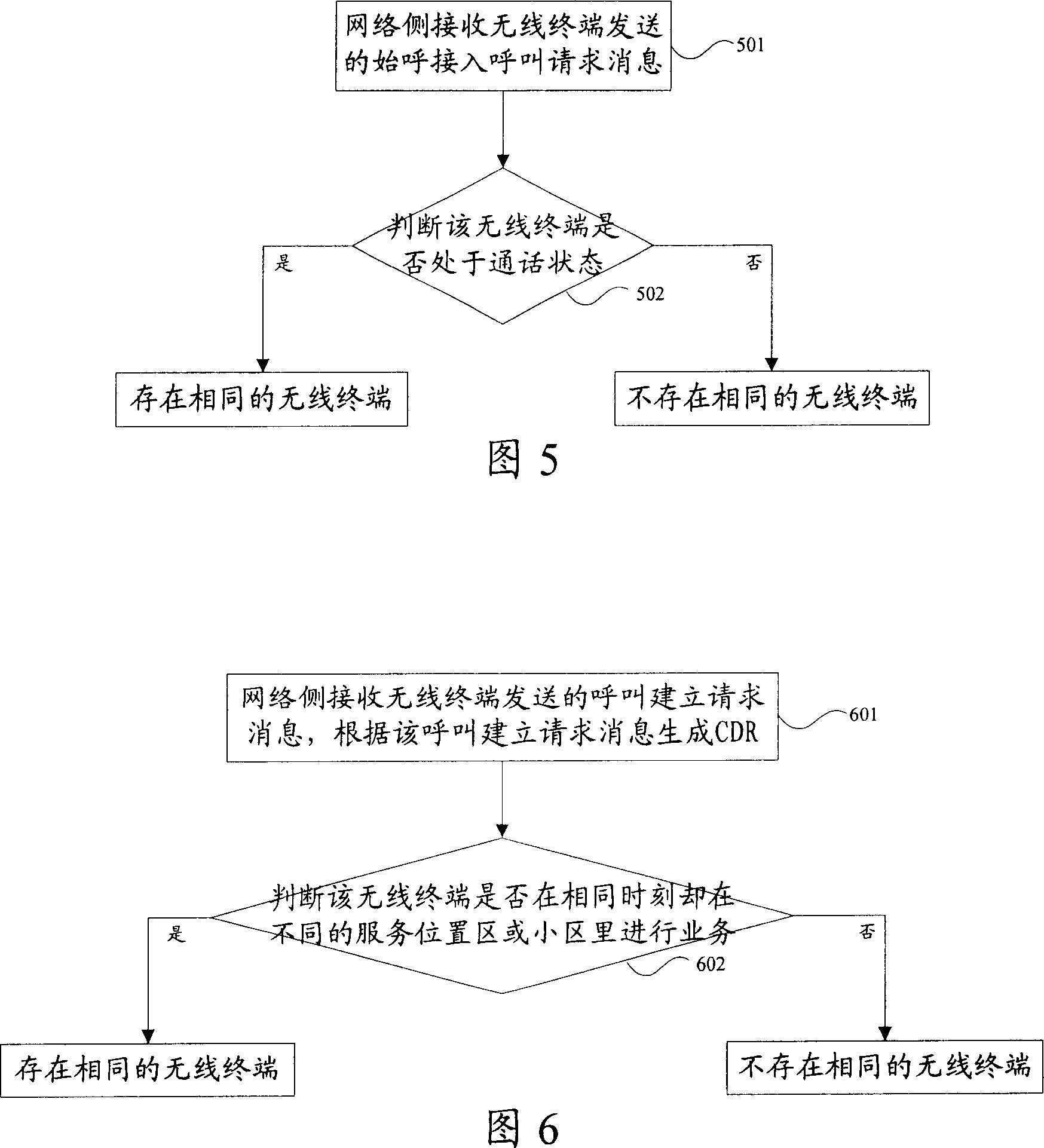
[0073] In this embodiment, it is determined whether the same wireless terminal exists by detecting the originating and accessing call request message sent by the wireless terminal. This embodiment is to detect whether there is a cloned wireless terminal in the calling party user. Firstly, on the network side, the state information of the wireless terminals within the jurisdiction of the network is stored, and the state information includes whether the wireless terminals are in a talking state or in an idle state at a certain moment. After the call connection from the calling party to the called party is established, during the call, the wireless terminals of the calling party and the called party are both in the call state. If the MSC receives an IMSI message with the same IMSI The originating and accessing call request of another wireless terminal, since the originating and accessing call request message can only be sent when the user's wireless terminal is in a non-communica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com