System and method for reduced hierarchy key management
a hierarchy key and key management technology, applied in the field of system and method for can solve the problems of unwieldy and expensive implementation and use of conventional products that provide management of encryption/decryption keys, and achieve the effects of reducing hierarchy key management, reducing cost, and being easy to implemen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
)
[0014] Terms used to describe the present invention are defined as follows:
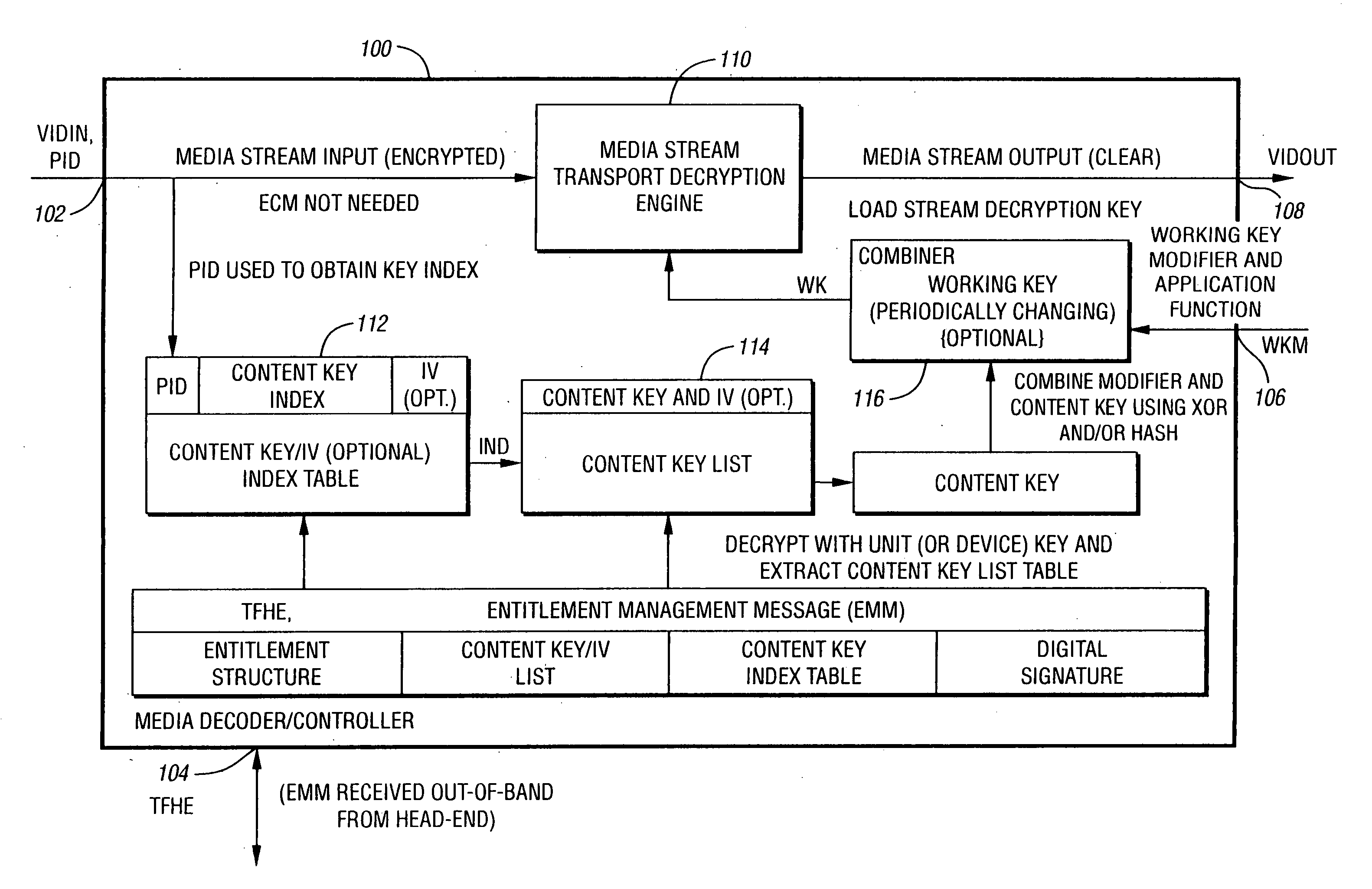
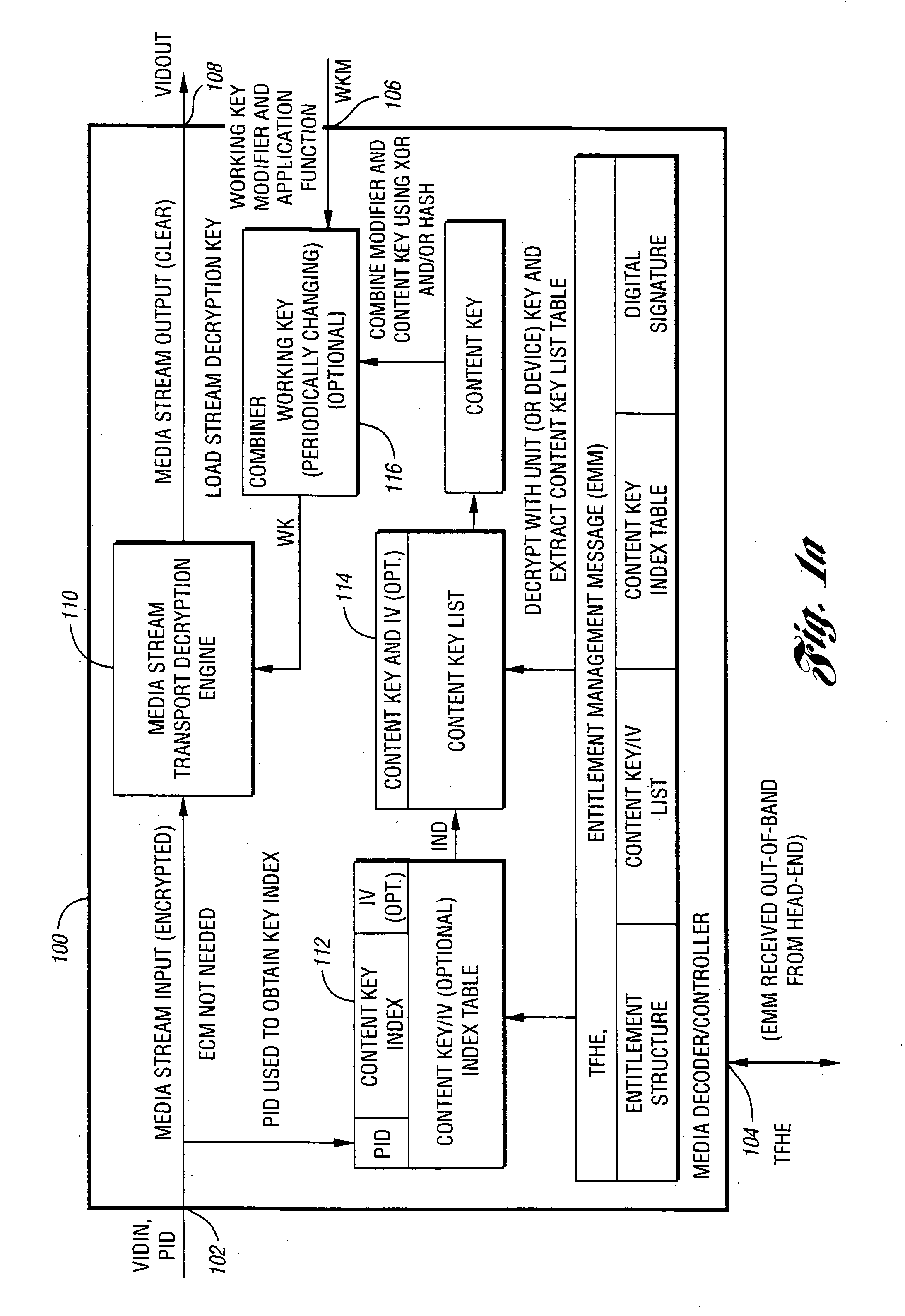
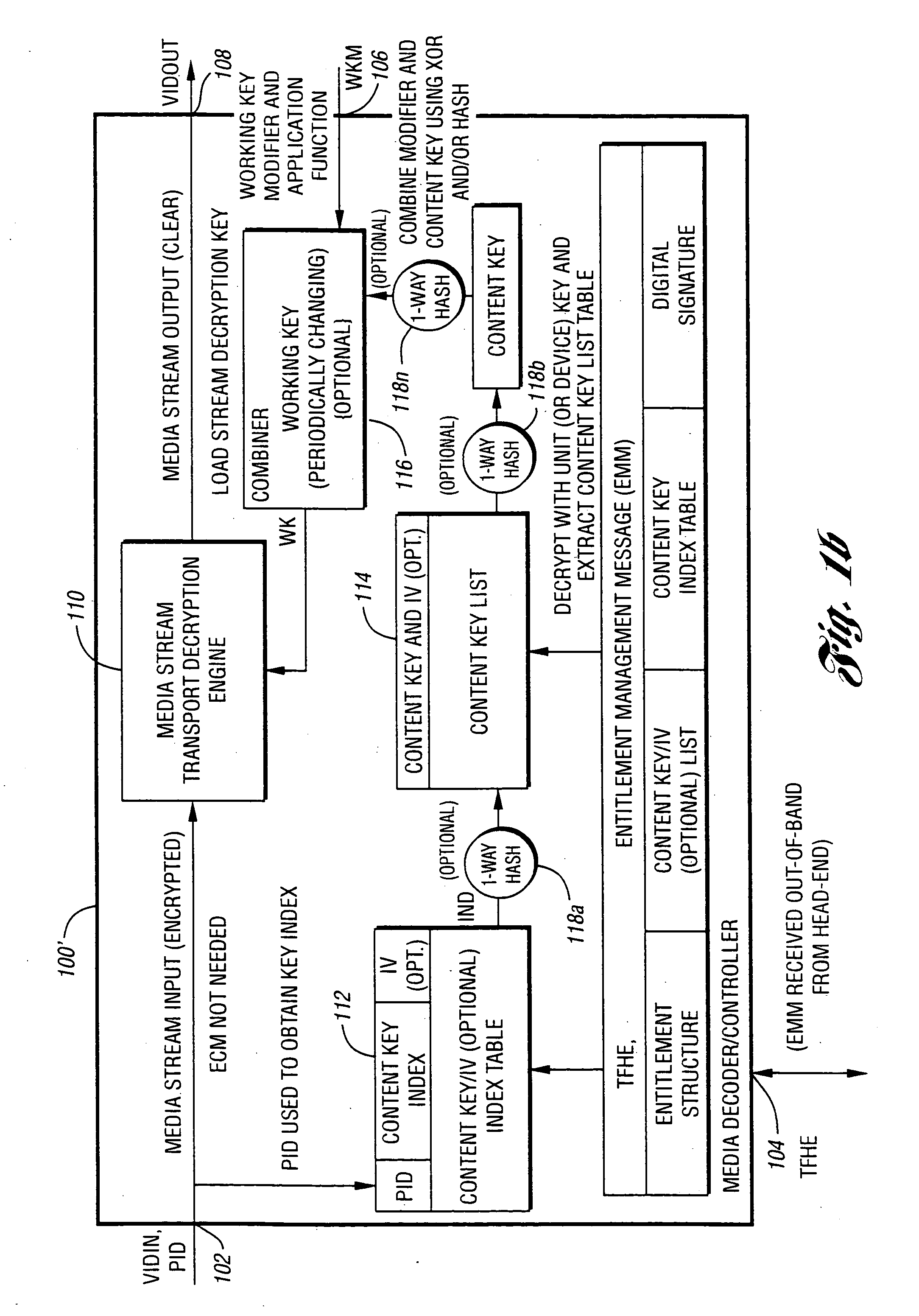
[0015] AES: Advanced Encryption Standard. AES is generally a much more secure algorithm to use for the storing of digital content in a digital video recording when compared to DES. The standard key length used for AES is 128 bits.
[0016] DES: Data Encryption Standard. A fixed-key-length security algorithm that employs 56-bit length keys. Any 56-bit number can be implemented as a DES key. The relatively short key length renders DES vulnerable to brute-force attack wherein all possible keys are tried one by one until the correct key is encountered (i.e., the key is “broken”).
[0017] Electronic Code Block (Mode): ECB, In ECB the message is divided into 64-bit blocks, and each block is encrypt separately. Encryption is independent for each block.
[0018] Entitlement Control Message (Stream): ECM, Messages that generally define access requirements of a program, specify the tiers required for subscription, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com