Security techniques for cooperative file distribution
a security technique and file technology, applied in the field of communication methods and systems, can solve the problems of inability to obtain files from other users, linear increase in bandwidth requirements, and rapid increase in cos
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
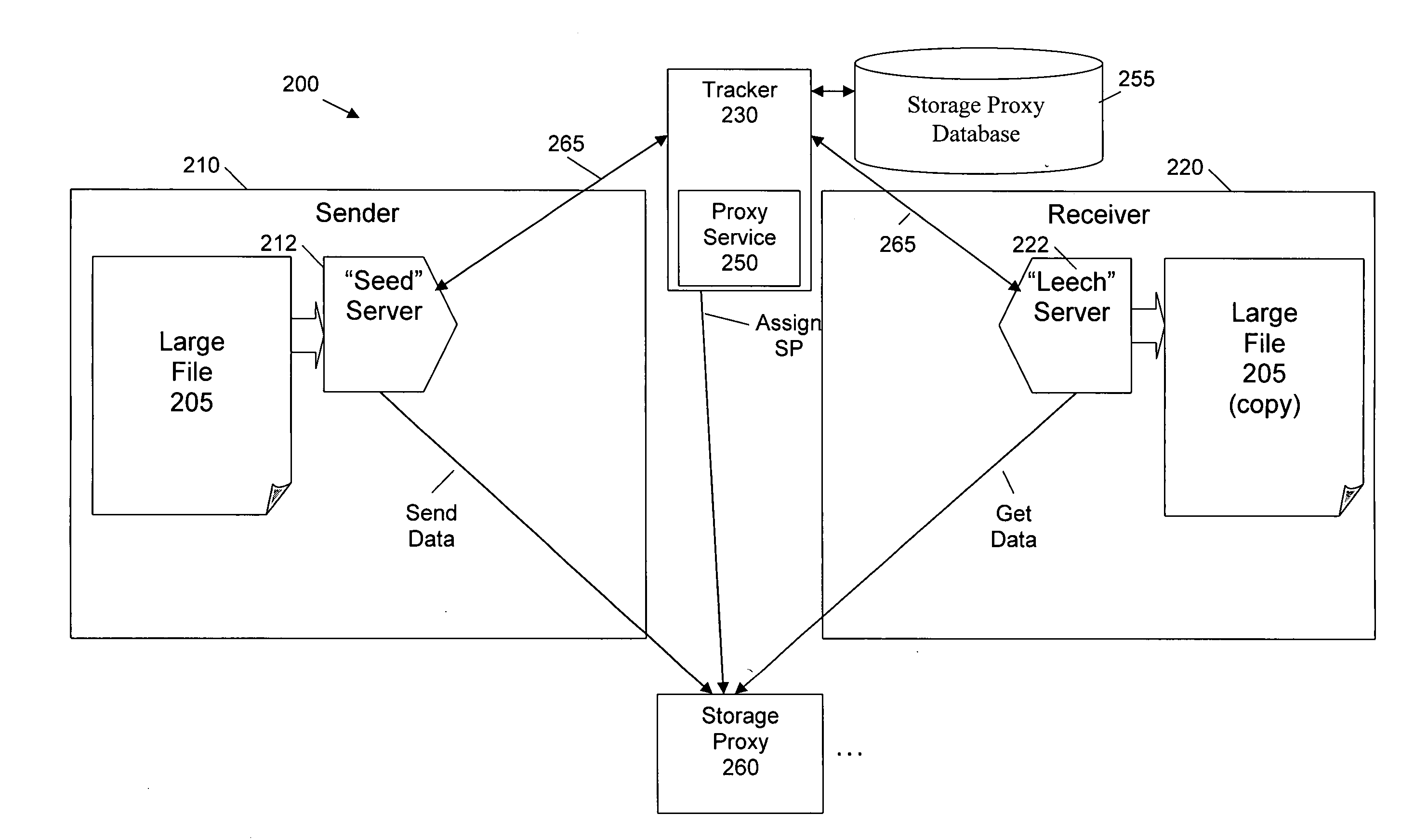
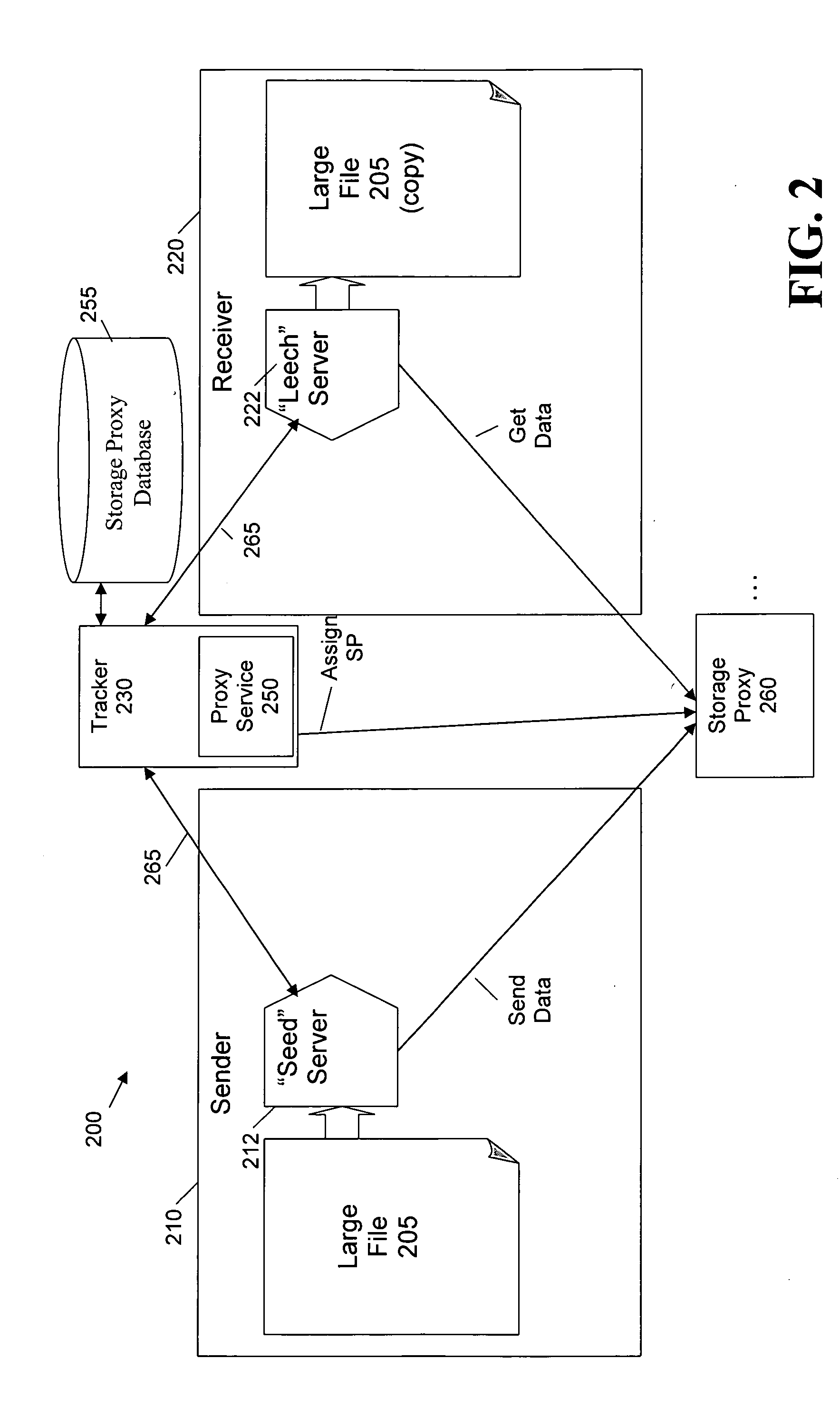
[0024]The present invention provides improved security techniques for a cooperative file distribution system.
BitTorrent Framework
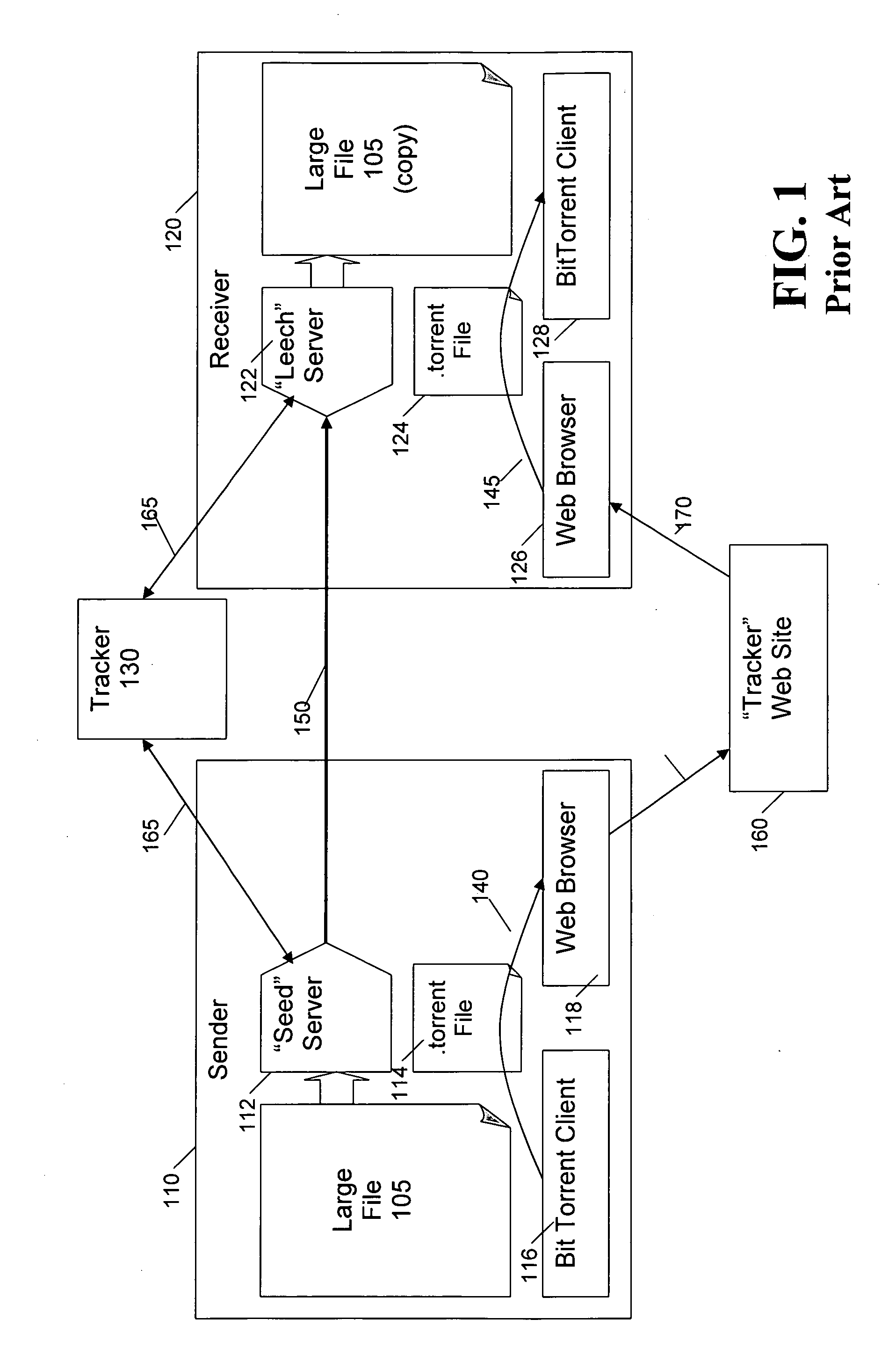
[0025]FIG. 1 is a schematic block diagram illustrating a conventional BitTorrent file distribution system 100. As shown in FIG. 1, a sender 110, desiring to send one or more large files 105 to a receiver 120, interacts with a tracker 130 that is part of the BitTorrent file distribution system 100. For a more detailed discussion of the BitTorrent file distribution system 100, see, for example, BitTorrent Protocol, http: / / www.bittorrent.com / protocol.html, or BitTorrent Guide, http: / / www.bittorrent.com / guide.html, each incorporated by reference herein.
[0026]Generally, to publish one or more files 105 using the BitTorrent file distribution system 100, a corresponding static file 114 with extension .torrent is put on a web server 160. In particular, as shown in FIG. 1, a BitTorrent client 116 executing on the sender computing device 110 typically initiates a we...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com