Multiring control method, node using the method, and control program
a control method and control program technology, applied in the field of multi-ring control methods, can solve problems such as the inability to protect the system, the network efficiency reduction, etc., and achieve the effect of efficient disposal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
[0057]A first method for efficient discard of a ring frame in a relay ring will be described with reference to FIGS. 1 and 2 and also to the flowchart of FIG. 12 showing the operation of the first embodiment.
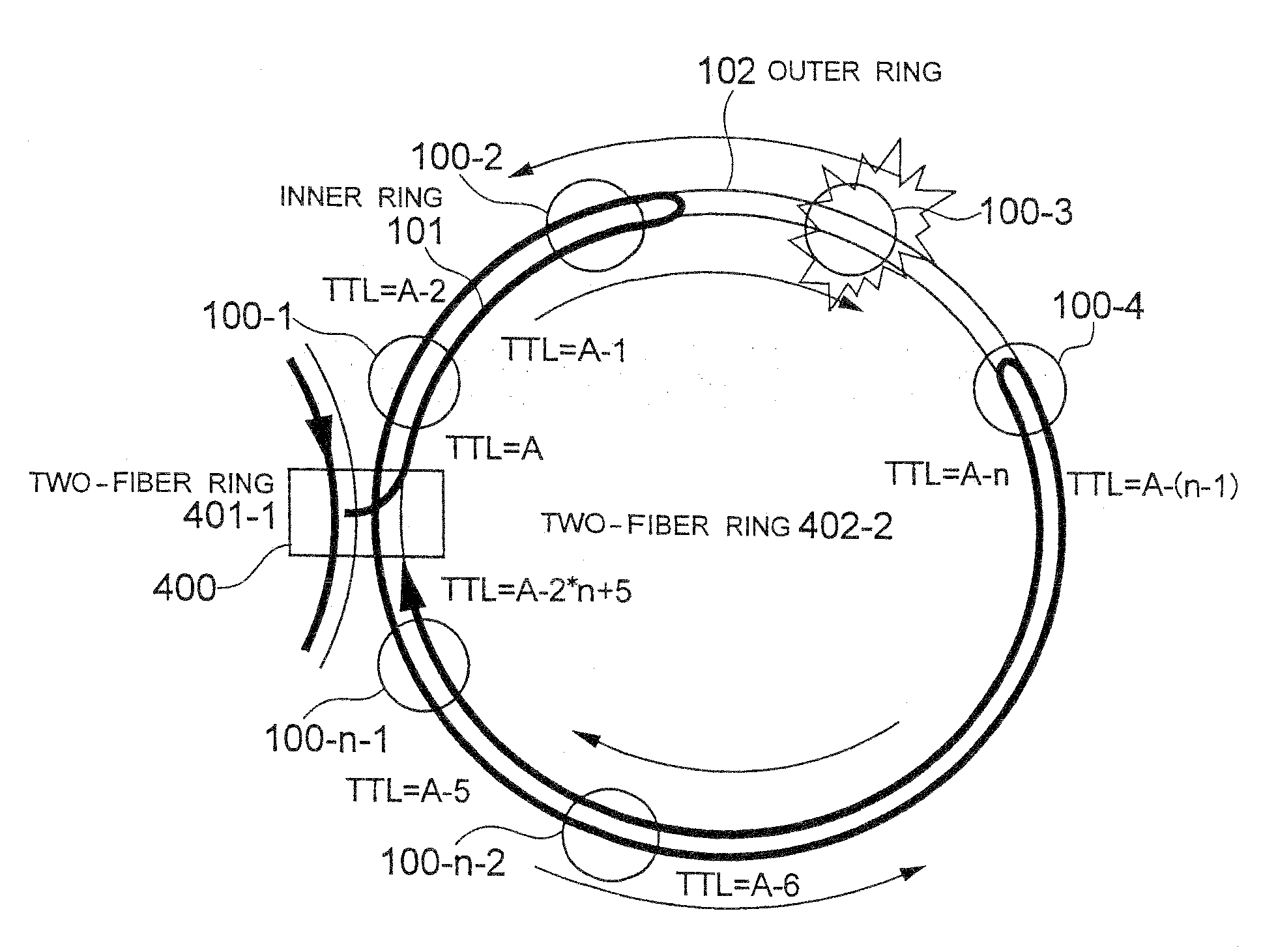
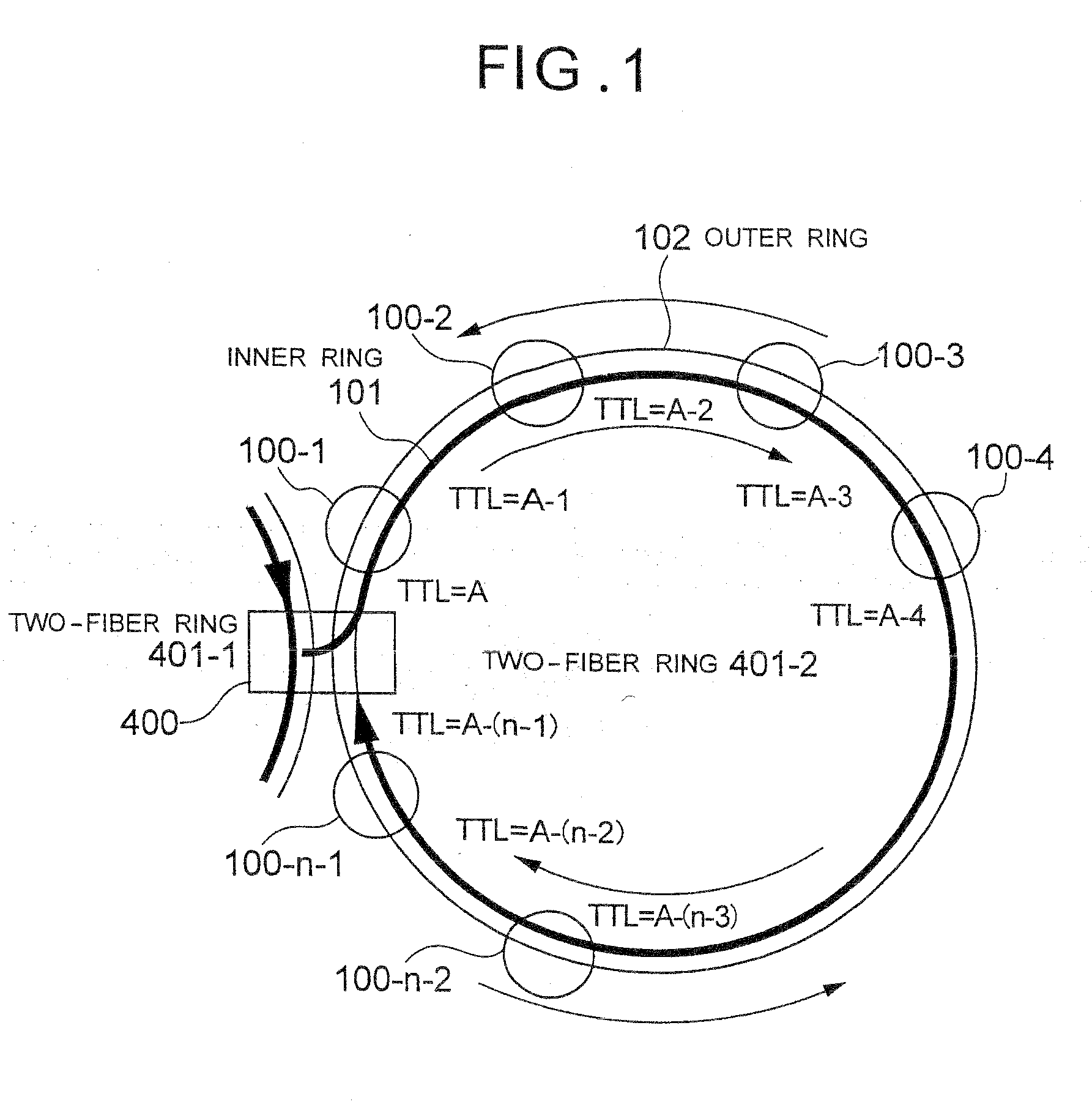
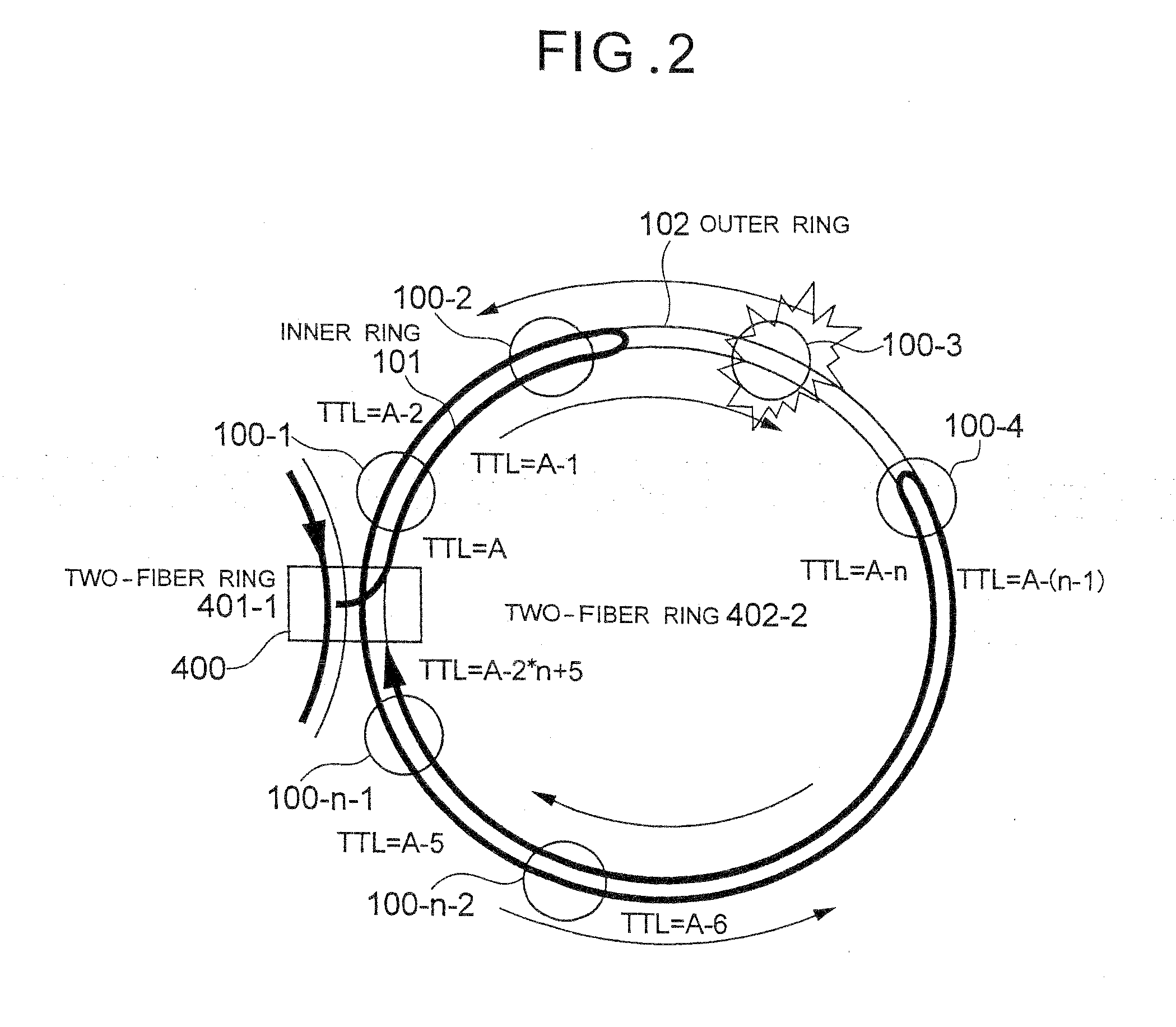
[0058]FIG. 1 shows a multiring configuration in which two-fiber rings 401-1 and 401-2 each formed of ring nodes 100 are bridged by a ring node 400. In the two-fiber ring 401-2, a total of n number of ring nodes 100 and 400 are connected.
[0059]The ring node 400 is given in advance the addresses of the ring nodes 100 and 400 and the total number n on the two-fiber rings 401-2 bridged by it. Description will be made by assuming that a ring frame transmitted in an inner ring 101 and an outer ring 102 between the ring nodes 100 and 400 is the same as the ring frame 180 shown in FIG. 13. However, it is not necessarily required that the ring frame transmitted through these rings have the same configuration as the ring frame 180, and the ring frame in this embodiment may have at least t...
embodiment 2
[0066]A ring node configuration for inter-ring bridging for realization of the first method for efficient discard of a ring frame will be described with reference to FIG. 3.
[0067]FIG. 3 shows the configuration of the ring node 400 bridging the two-fiber rings 401-1 and 401-2 shown in FIG. 1.
[0068]The configuration of the ring node 400 is symmetrical about a ring bridge 650. In FIG. 1, functional blocks corresponding to each other in the symmetrical configuration are indicated by symbols such as x-1 and x-2 (x: functional block number). For ease of description, indication with “-1” and “-2” is omitted in the following description.
[0069]The ring node 400 is constituted by multiplexing circuits 130 and 131, protection switches 150, TTL comparators 610 and 611, pass / drop determination circuits 620 and 621, TTL setting circuits 630 and 631, ring protection processing / topology management circuits 640, and the ring bridge 650. The inner ring 101-1 and the outer ring 102-1 belong to the sam...
third embodiment
[0081]A method for protection from an inter-ring bridge node fault in accordance with the present invention will be described with reference to FIGS. 4 to 6 and also to the flowchart of FIG. 13 showing the operation of the third embodiment. It is assumed that a faulty-end lap protection method based on the conventional art is used as an in-ring protection method.
[0082]FIGS. 4 to 6 show a multiring configuration in which two-fiber rings 701-1 to 701-3 each formed by ring nodes 700 are bridged by ring nodes 710.
[0083]In each of the two-fiber rings 701-1 to 701-3, each of the ring nodes 700 and 710 belonging to the two-fiber ring monitors the fault condition of its junction links. In the event of a fault, the ring node notifies the other ring nodes 700 and 710 belonging to the same two-fiber ring 701-1, 701-2, or 701-3 of fault information. The ring nodes 710-1, 710-2, and 710-3 for inter-ring bridging belong to one protection domain 704. If a fault occurs at one of the ring nodes 710-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com