Vehicle Segment Certificate Management Using Shared Certificate Schemes
a technology of shared certificates and vehicle segments, applied in the direction of public key infrastructure trust models, wireless communication, transportation and packaging, etc., can solve the problems of limited vehicle privacy, no method proposed to date has completely satisfied all design goals, and the balance between scalability and privacy is not easy to achieve. achieve the effect of improving vehicle privacy and enhancing vehicle privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
case 1
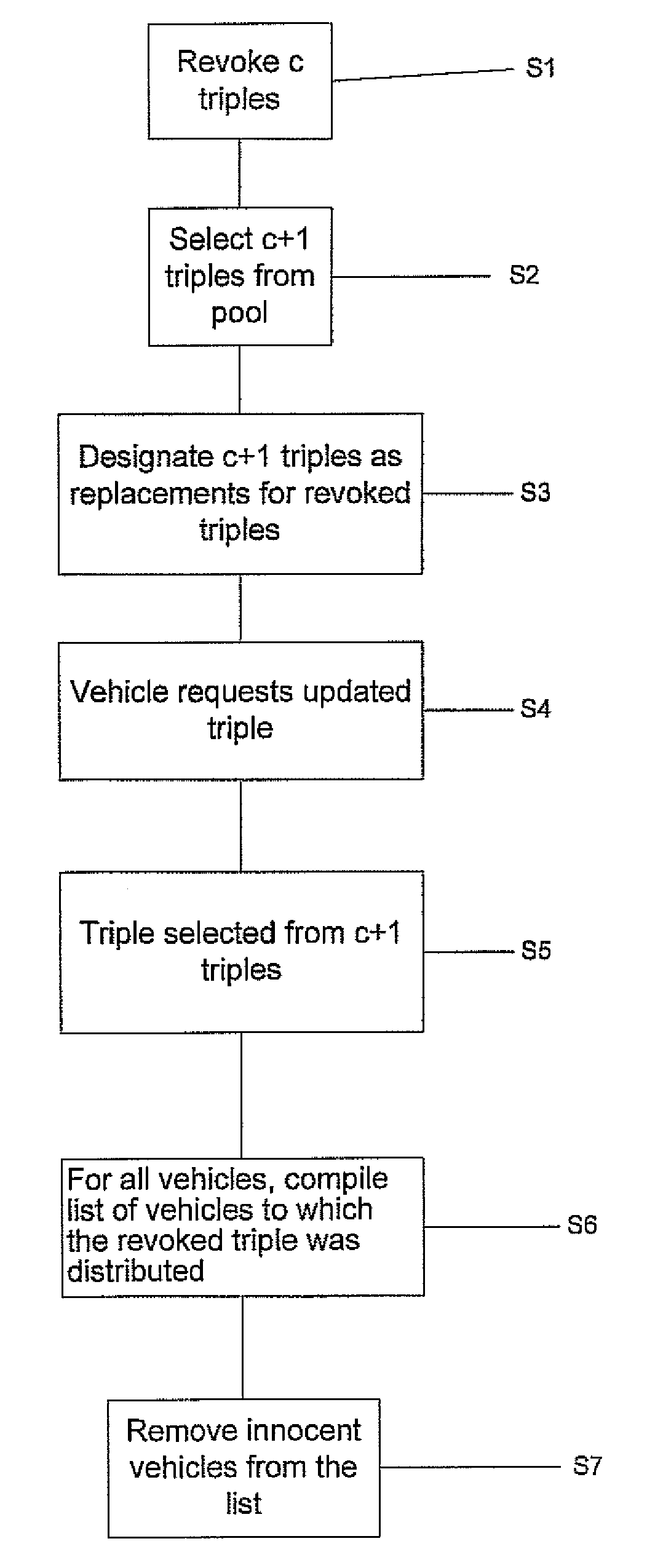
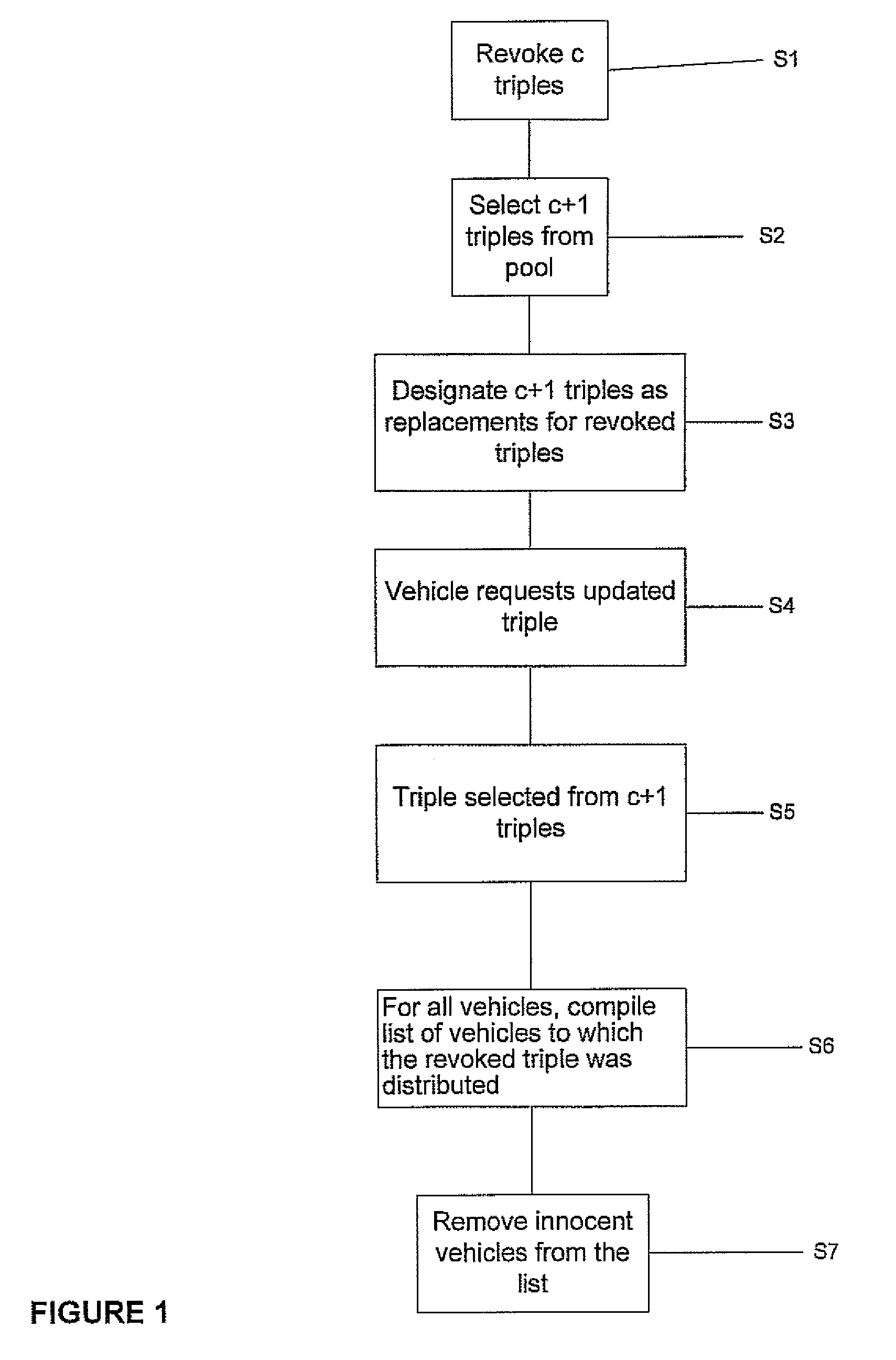
[0159]Single Malicious Vehicle: More formally, assume that one particular vehicle uses one of its anonymous triples k for some malicious activity that is detected by an RSE. As a consequence, the triple k as well as additional triples k(1), . . . k(c) are revoked. At this point, it is hard to detect which vehicle generated the malicious message as several vehicles were assigned triple k and thus any one of them could have potentially acted maliciously.
[0160]However, unlike in the basic combinatorial scheme, not all vehicles that previously shared triple k receive the same new triple k′ upon completion of their update request, as each of them may receive any of the additional new triples k′(i) with some probability. Now, if the previously malicious vehicle continues its malicious activity using the new triple k′, thus forcing this new triple to be revoked again, the set S(k) of vehicles that share k′ with the malicious vehicle is largely different from the set S(k′) of vehicles that ...
case 2
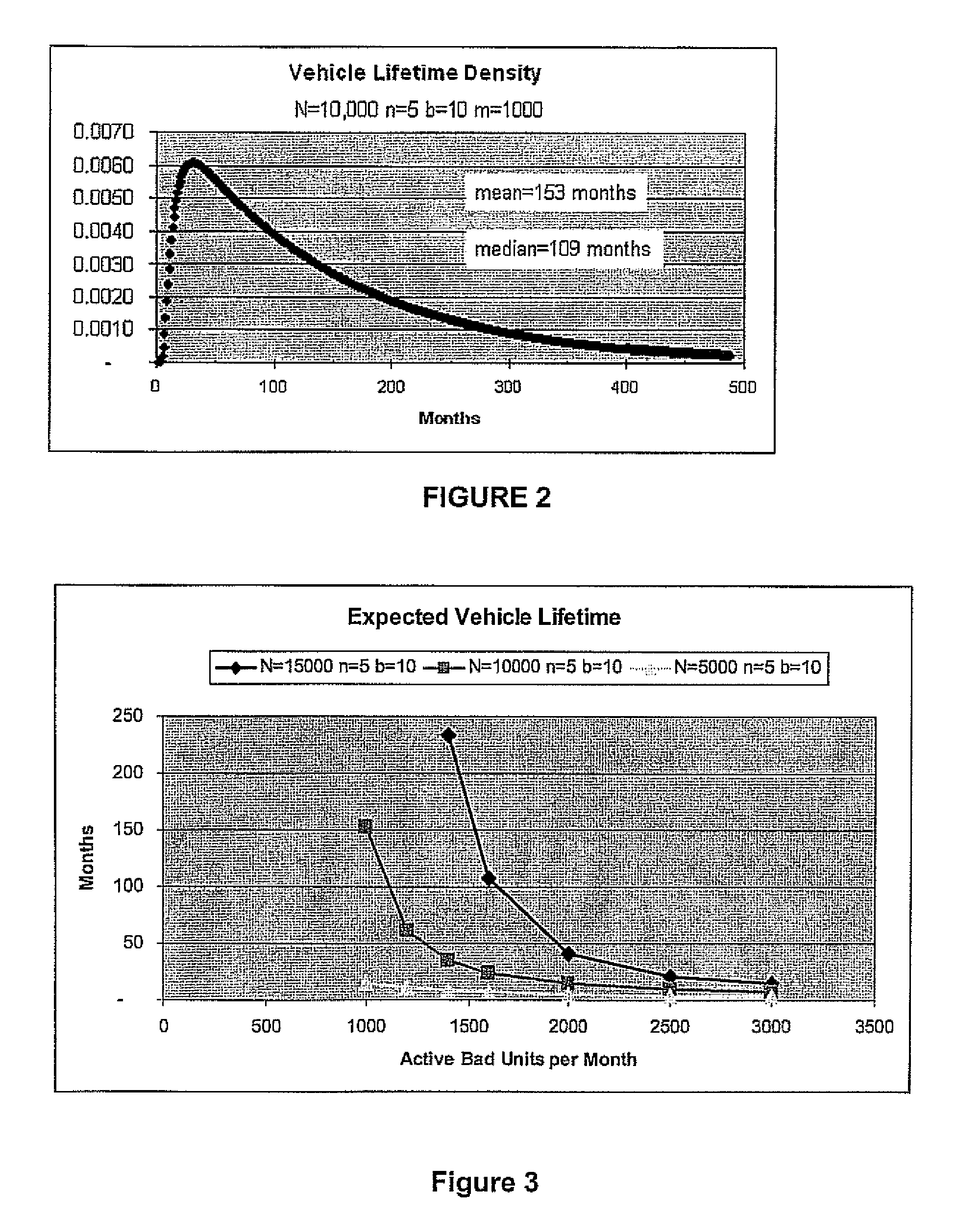
[0167]Multiple Malicious Vehicles: The above analysis assumed the existence of a single vehicle that sends maliciously generated messages. A much more realistic scenario might involve multiple vehicles that at any given time are concurrently sending maliciously computed messages, potentially from different geographic locations. In fact, the worst case scenario is a large-scale attack where every triple in the pool is used by one or more vehicles to send malicious messages. As we now describe in more detail, by making a number of reasonable assumptions on the distribution of vehicles and on the distribution of attackers, the analysis of this apparently more involved scenario follows from a careful extension of the previous analysis for a single attacking vehicle.
[0168]In addition to the already defined parameters N, n, b, c, L, t, V, u, we consider the number of RSE's or geographic areas g in the country. Each geographic area can have lower or higher vehicle density, with potentially...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com