Information processing device, information recording device, information processing system, program update method, program, and integrated circuit
a technology of information recording and information processing device, which is applied in the direction of program/content distribution protection, digital transmission, instruments, etc., can solve the problems of unauthorized copying of contents, large loss of right owner's advantage, and difficulty in providing a safe program without security holes, so as to prevent users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0100]In the following, an embodiment of the present invention will be described with reference to the attached drawings.
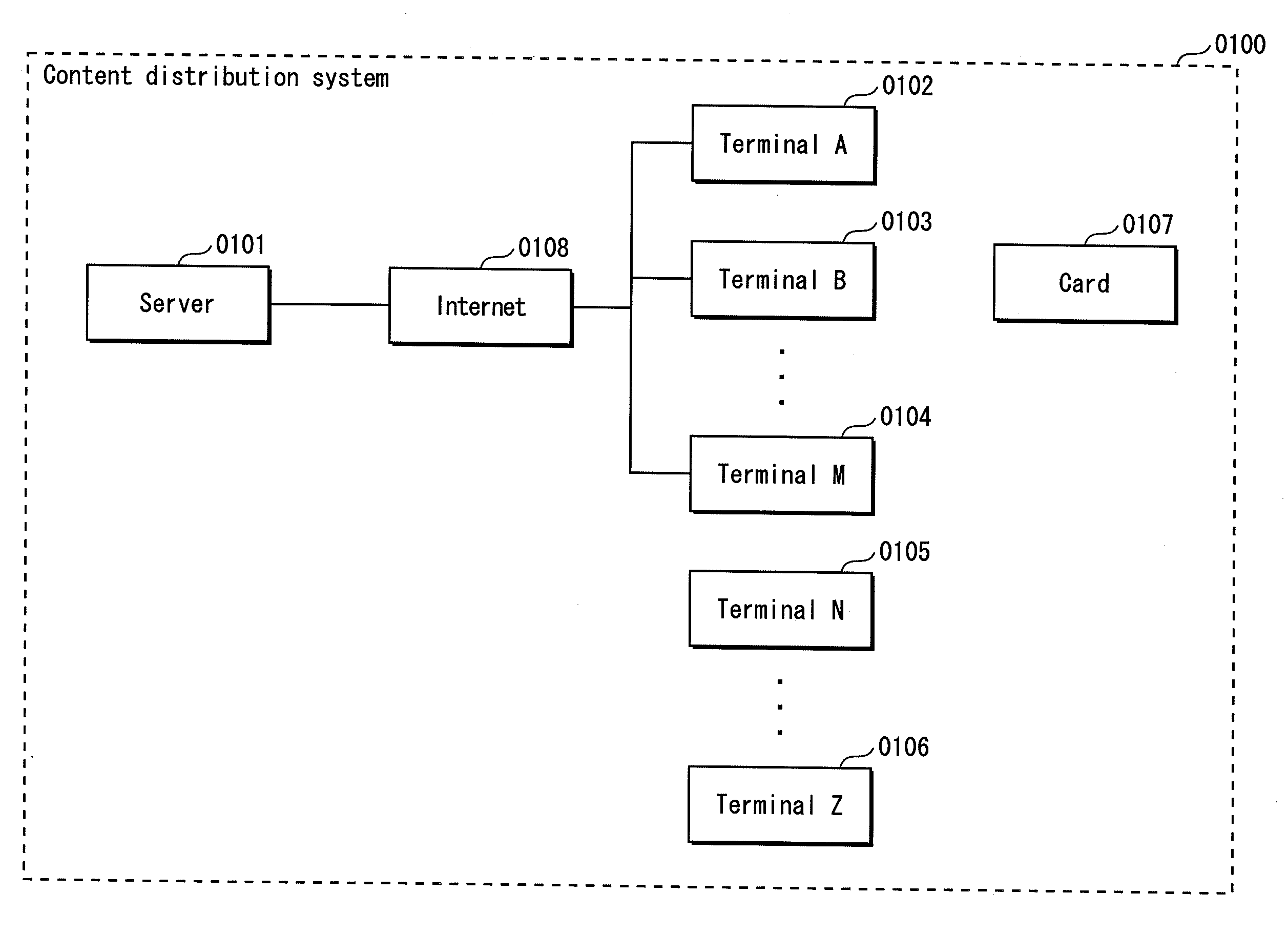
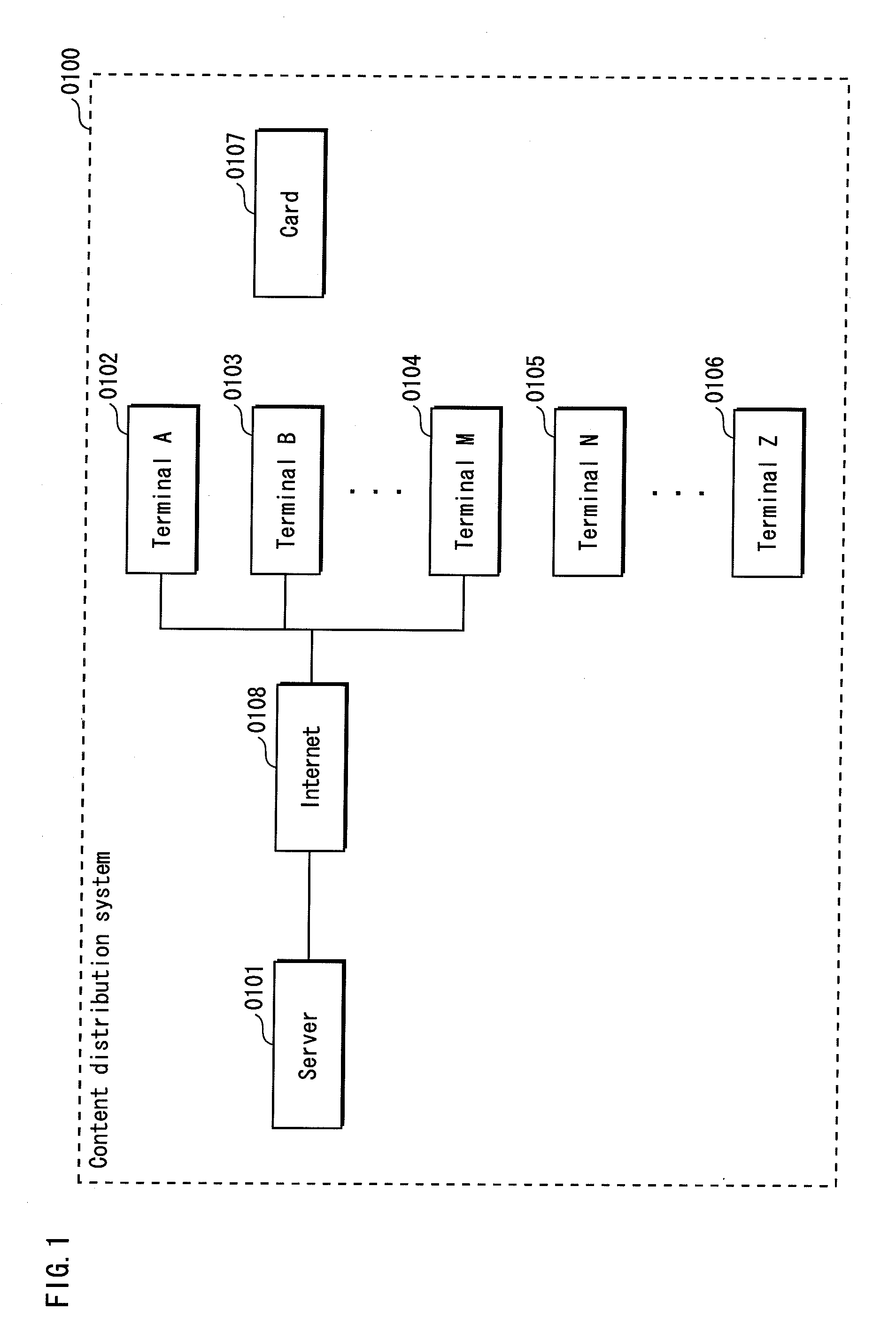
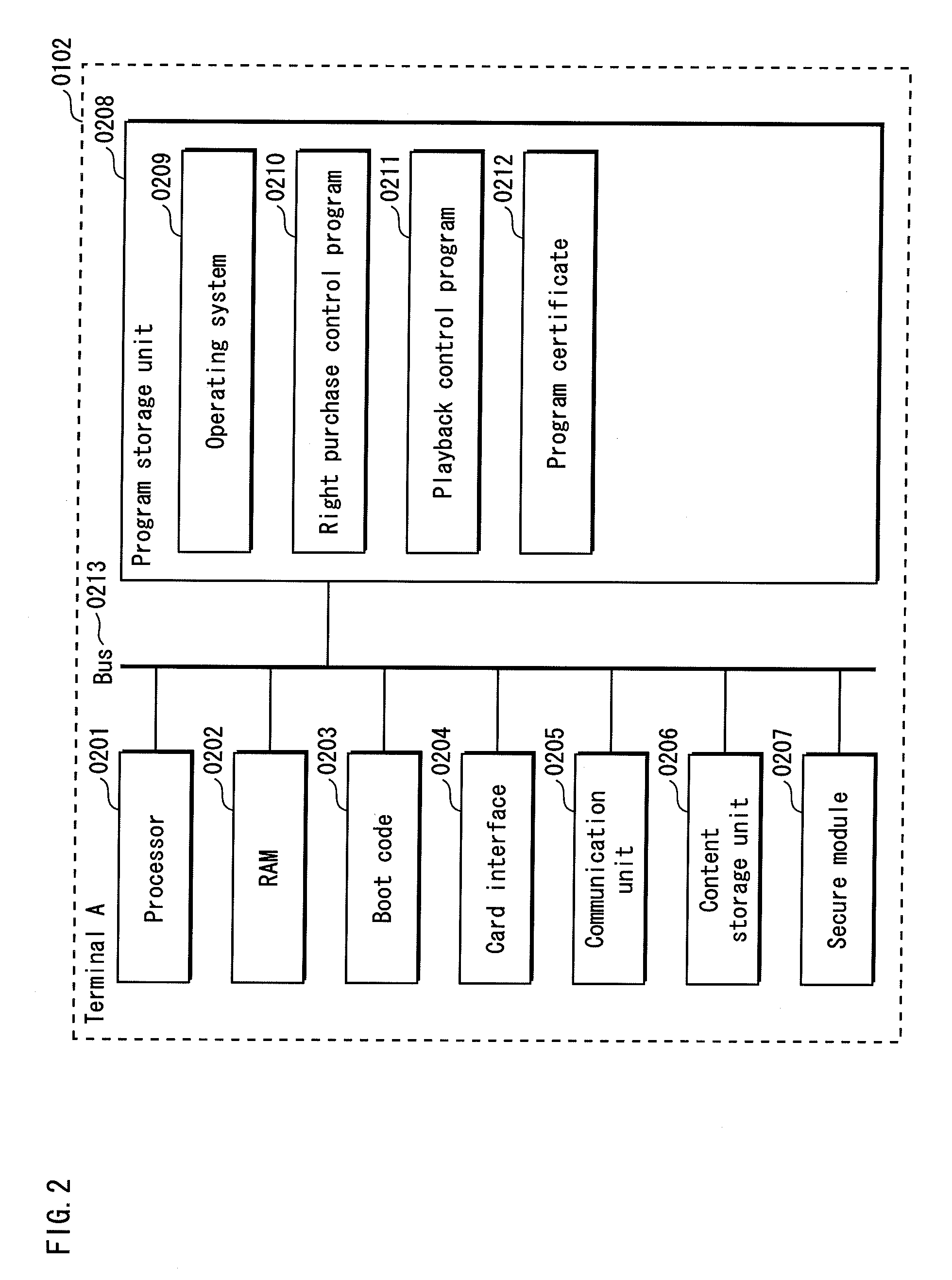
[0101]FIG. 1 shows the structure of a content distribution system 0100. The content distribution system 0100 is composed of a server 0101, a terminal A 0102, a terminal B 0103, . . . a terminal M 0104, a terminal N 0105, . . . a terminal Z 0106, and a card 0107. The server 0101 is connected with the terminal A 0102, the terminal B 0103, and the terminal M 0104 via the Internet 0108. The terminal N 0105 and the terminal Z 0106 do not have means for directly performing communication with the server 0101. The terminal A 0102, the terminal B 0103, . . . the terminal M 0104, and the terminal N 0105, . . . the terminal Z each have a card interface, and can transfer data among them via the card 0107.
[0102]Note that, although FIG. 1 shows only the terminal A 0102, the terminal B 0103, and the terminal M 0104 as terminals that are connected with the server 0101, one or mor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com