System and method for securing computer system against unauthorized access
a computer system and system technology, applied in the field of automatic computer systems, can solve problems such as security breaches and suspicious behavior, and achieve the effect of defeating computer security breaches
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
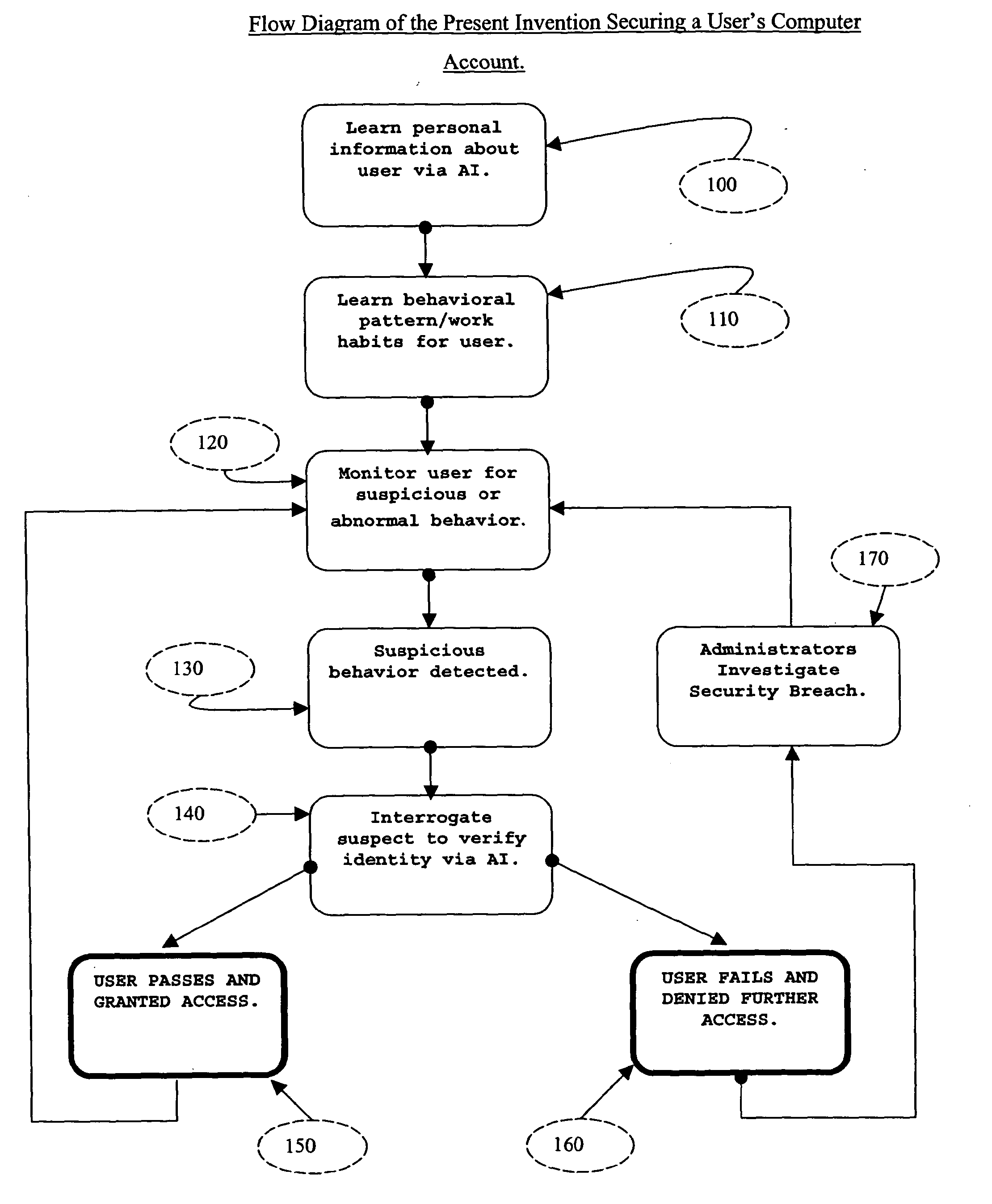
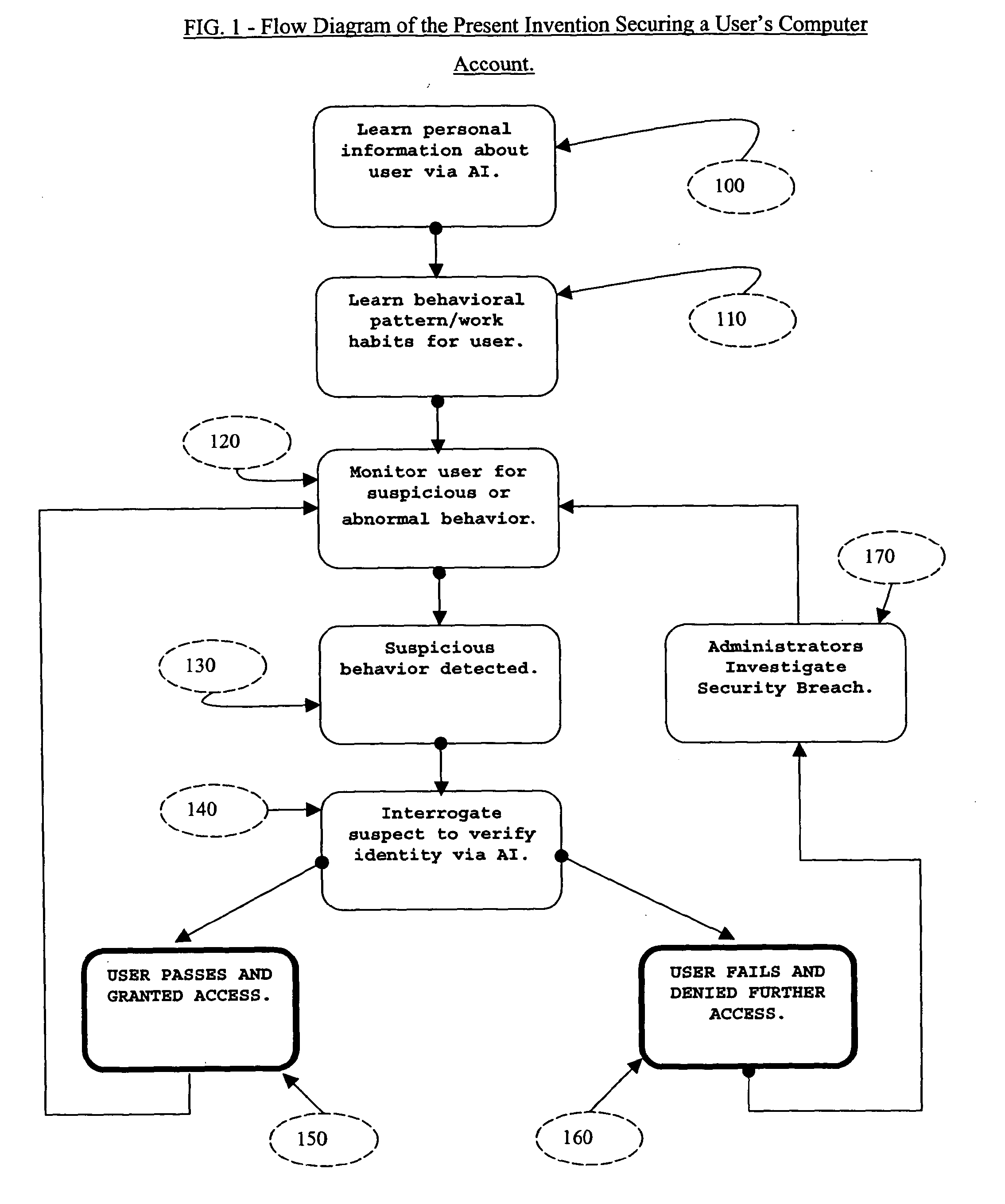
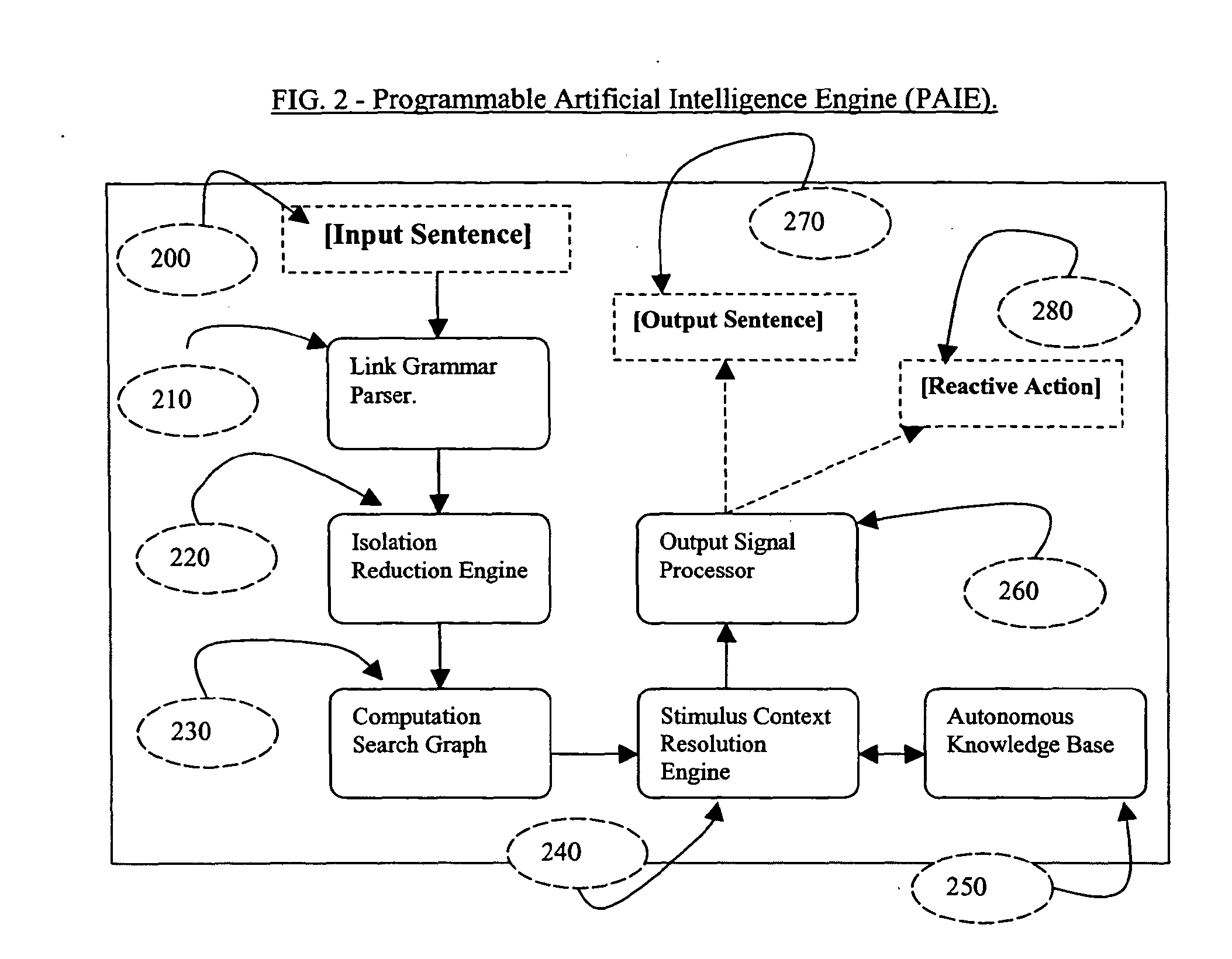
[0041]The present invention secures a computer user's account against unauthorized access, by defeating two kinds of security breaches on computer systems, which are identity theft and insider espionage. Identity-theft occurs when thieves steal user identities such as passwords and then use it to illegally gain access to an authorized user's computer account. Insider espionage occurs when an “insider” belonging to an organization chooses to use his / her access privileges to steal information from the computer network of the organization. The present invention also contains a PAIE on which interactive applications can be developed to engage in intelligent interactions with humans.
[0042]FIG. 1 is a flow diagram illustrating the present invention and the steps that it takes to secure a computer users account against unauthorized access. The flow diagram depicts how the present invention works to secure each legitimate computer user. The present invention can secure several users concurr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com