On-vehicle communication system
a communication system and vehicle technology, applied in the field of vehicle communication systems, can solve the problems that the communication system connected to the network outside the vehicle may be subject to cyber-attacks and the process operation of the ecu may be affected by cyber-attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
modification 1
[0073][Modification 1]
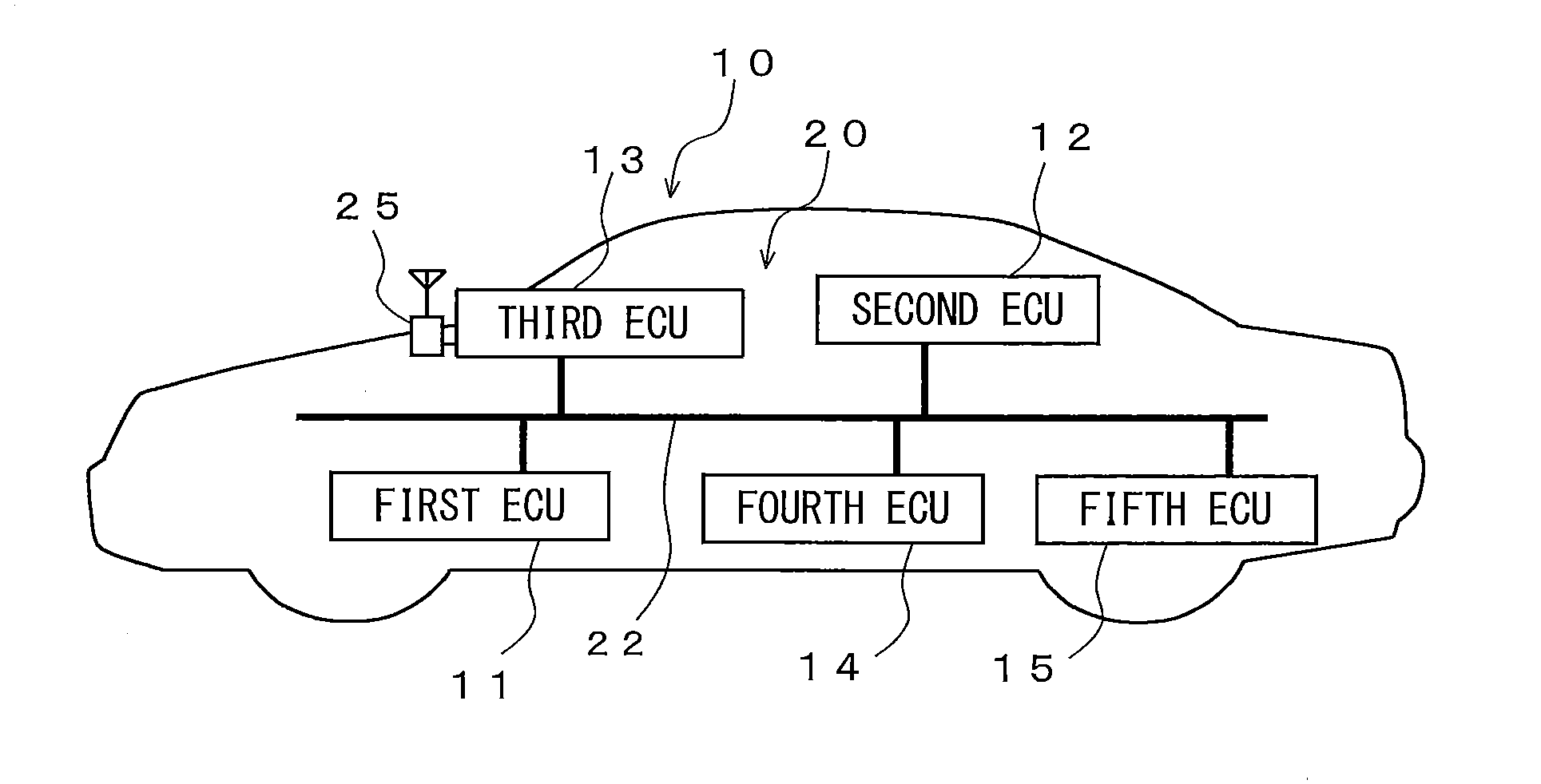
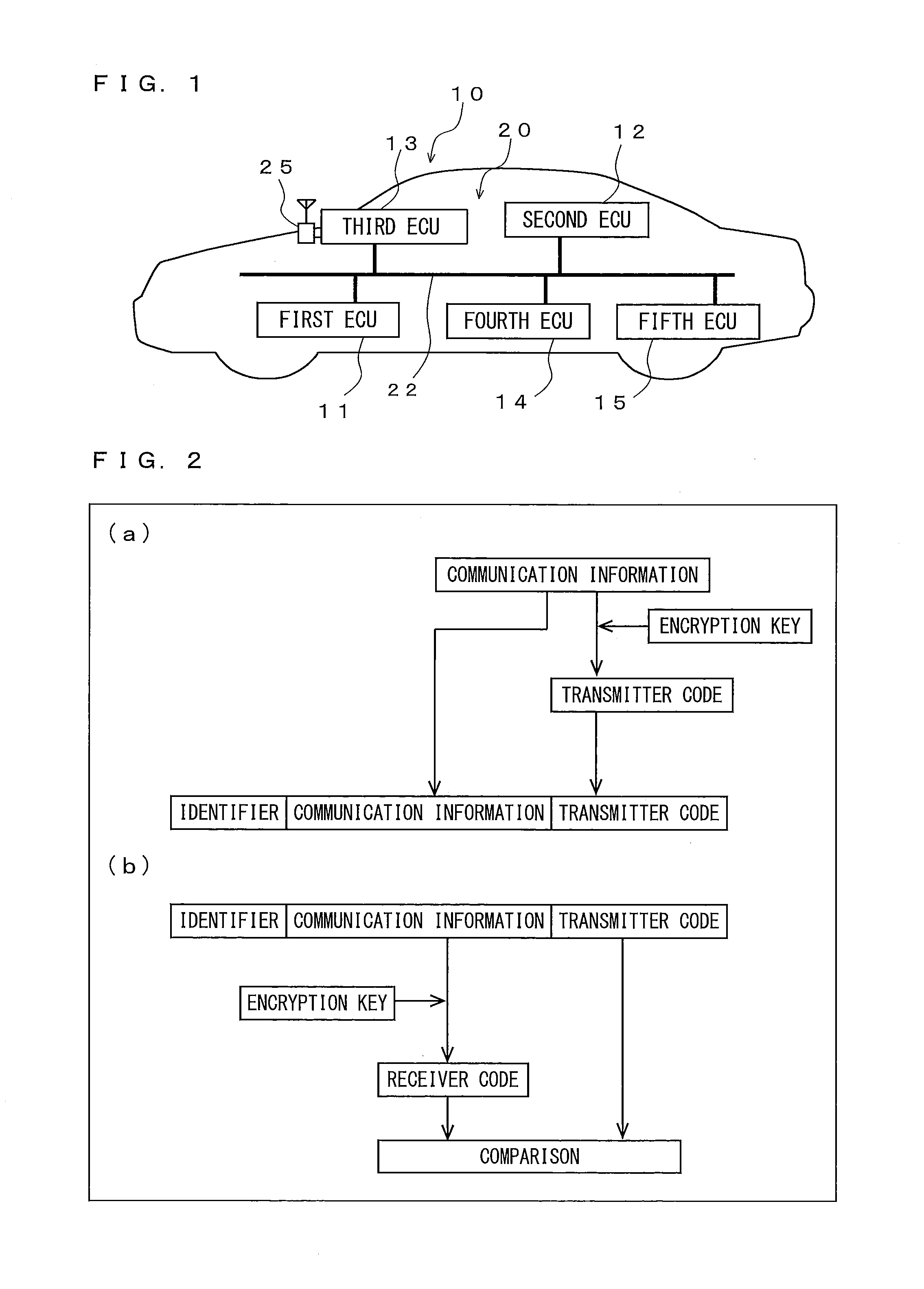
[0074]In modification 1, the fourth ECU 14 is an ECU for transmitting communication information to an external device via the third ECU 13. For example, the fourth ECU 14 has only the second encryption key K2 among the first encryption key K1 and the second encryption key K2. In a case where authentication of the data frame (that is, data frame including the communication information (hereinafter, referred to as “information for outside”) transmitted from the third ECU 13 to an external device) transmitted from the fourth ECU 14 to the third ECU 13, is performed, a message authentication code is generated by using an accumulated travel distance of the vehicle. The fourth ECU 14 may have both the first encryption key K1 and the second encryption key K2.
[0075]In the on-vehicle communication system 10 having the third ECU 13 connected to the network outside the vehicle, in a case where the data frame including the information for outside is illicitly intercepted, ...
modification 2
[0083][Modification 2]
[0084]In modification 2, similarly to modification 1, the fourth ECU 14 is an ECU for transmitting the communication information via the third ECU 13 to an external device. For example, the fourth ECU 14 has only the second encryption key K2 among the first encryption key K1 and the second encryption key K2. In a case where authentication of the data frame to be transmitted from the fourth ECU 14 to the third ECU 13, is performed, the message authentication code is generated by use of challenge data in a challenge and response method, unlike in modification 1. The fourth ECU 14 may have both the first encryption key K1 and the second encryption key K2. FIG. 6 shows a flow of message authentication according to modification 2.
[0085]The fourth ECU 14 sends an access request to the third ECU 13 when transmitting, to the third ECU 13, the data frame including the information for outside (for example, vehicle speed information). The third ECU 13 that has received th...
modification 3
[0089][Modification 3]
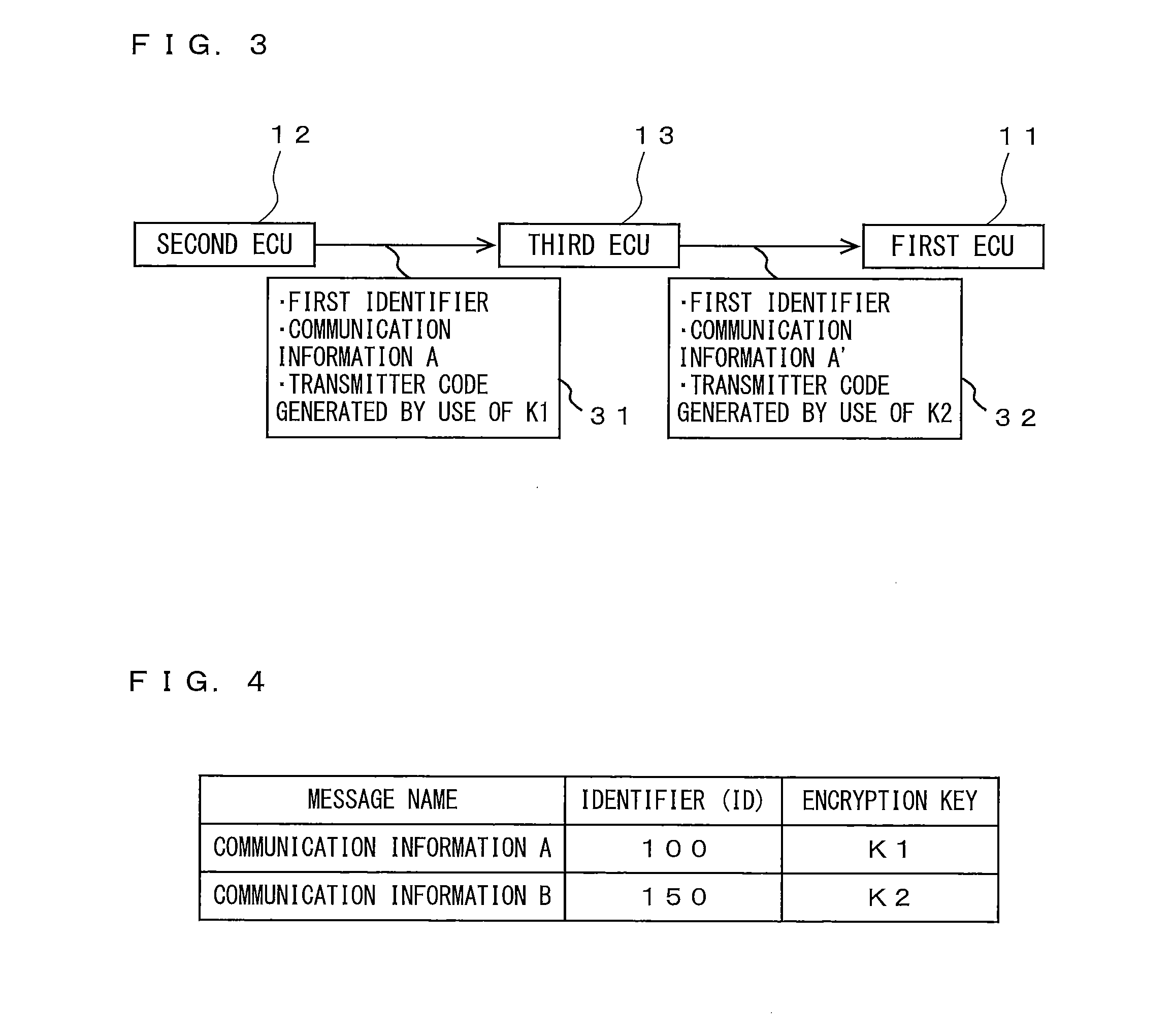
[0090]In modification 3, the fourth ECU 14 is an ECU for transmitting the data frame including communication information C to be used by each of the first ECU 11 and the third ECU 13. The fourth ECU 14 has the first encryption key K1 and the second encryption key K2. The fourth ECU 14 assigns, to the data frame including the communication information C, a first transmitter code generated by use of the first encryption key K1 and a second transmitter code generated by use of the second encryption key K2.
[0091]The fourth ECU 14 performs the transmission-side process when transmitting the data frame including the communication information C. The fourth ECU 14 generates the first transmitter code from the communication information C by use of the first encryption key K1, and generates the second transmitter code from the communication information C by use of the second encryption key K2. As shown in FIG. 7, the fourth ECU 14 transmits, to the on-vehicle network 20,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com