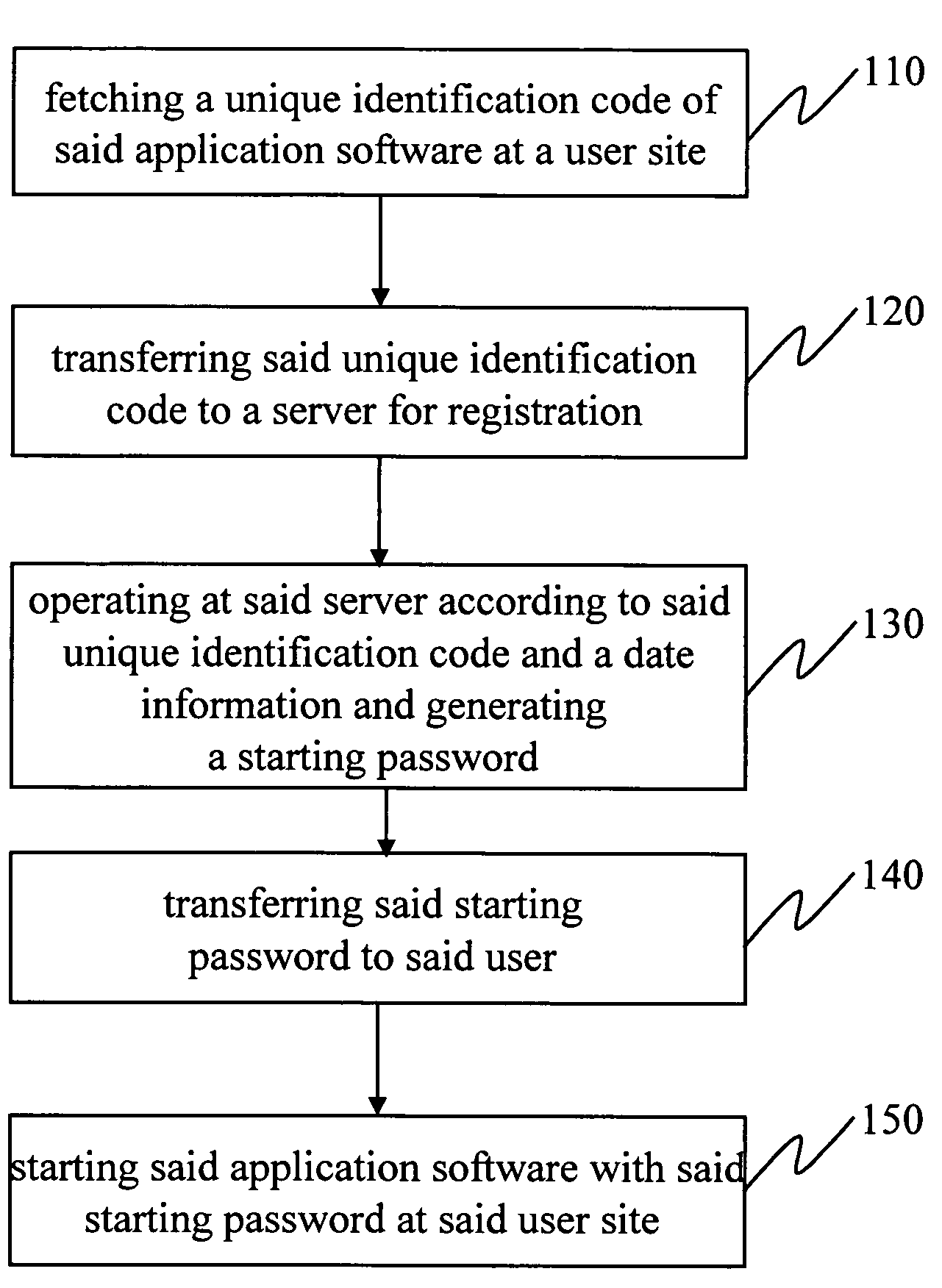
Encryption method of application software
a technology of application software and encryption method, applied in the field of encryption method, can solve the problems of expired passwords, inability to modify starting dates, and inability to permanently valid passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
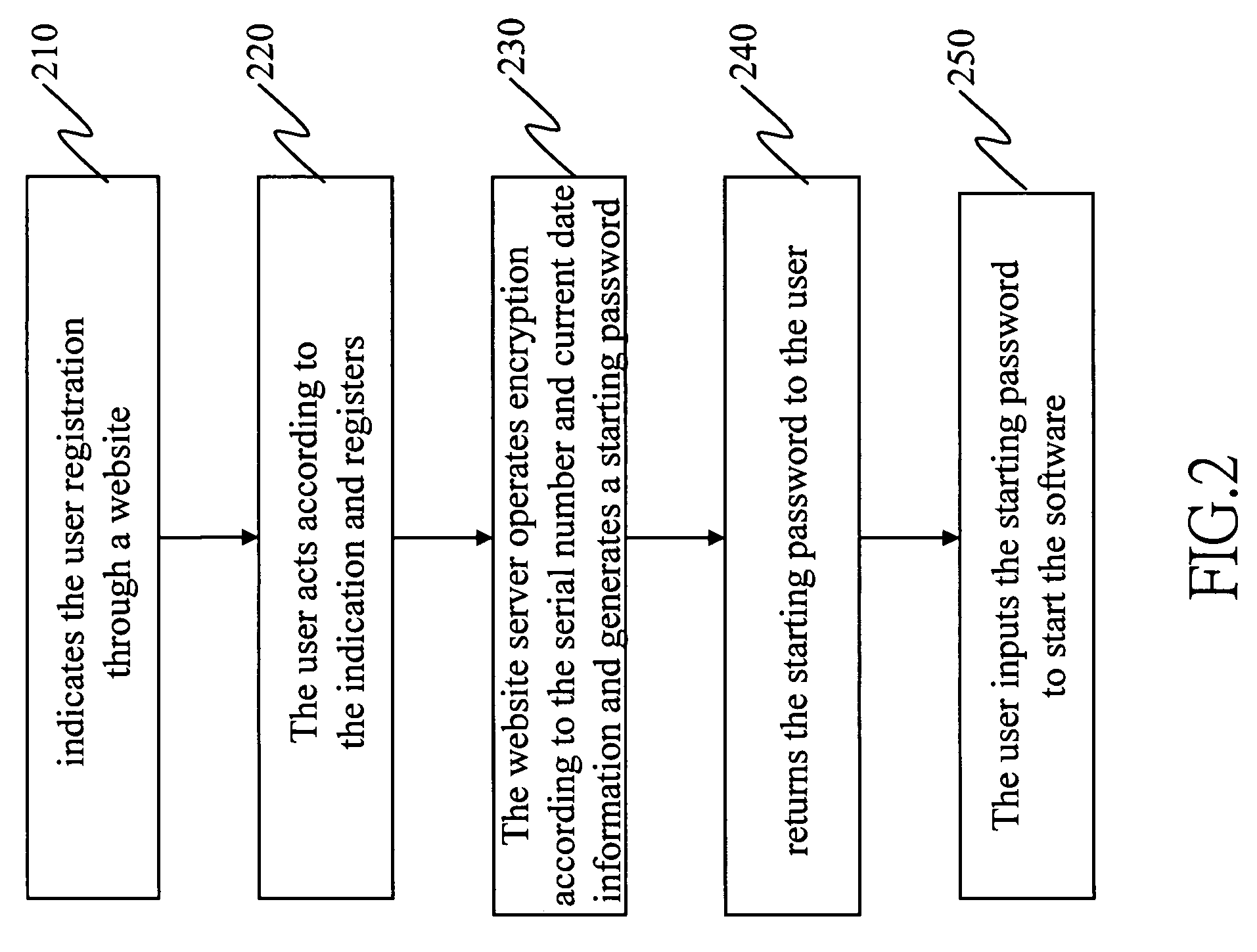
[0020]The process of generating a password is shown in FIG. 2, which is flowchart of the invention. First it indicates the user to use the software serial number for registration through a website (step 210). The user acts according to the indication and registers (step 220). The system verifies the registered user. It does not permit repetitive registration. For a user who repeats to register, the system indicates the user no need to register. The server judges the times of registration of the same account number, if detecting the registration account number being massively used, then it terminates the registration of that serial number account to prevent the serial number being stolen. The website server operates encryption according to the serial number and current date information and generates a starting password (step 230). It returns the starting password to the user (step 240). The user gets the starting password, inputs it to start the software (step 250).
[0021]The software...
second embodiment
[0023]FIG. 4 shows the operation flowchart of the invention. After a website downloadable software being installed and initiated, the software first checks whether the user has a password to start, if the program has been started with password, it goes ahead. Otherwise, the user has to register a new account number from the website (step 410). The system fetches the hard disk serial number as a unique identification code of the user and provides to the user (step 420). The user uses the unique identification code to apply a starting password (step 430). The website server checks whether the account number being massively used or incomplete in payment. If the account number is massively used, it identifies the illegal user. If the user has not finished the payment, the operation cannot continue. If the above examination conditions all pass, the website sever operates encryption according to the unique identification code and the server current date to generate a starting password (st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com