Method for processing AK context
A processing method and context technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of difficulty in determining the number of AK contexts, reduce system security, and fail to switch, and achieve simple and feasible technical solutions. Switching, avoiding difficult effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
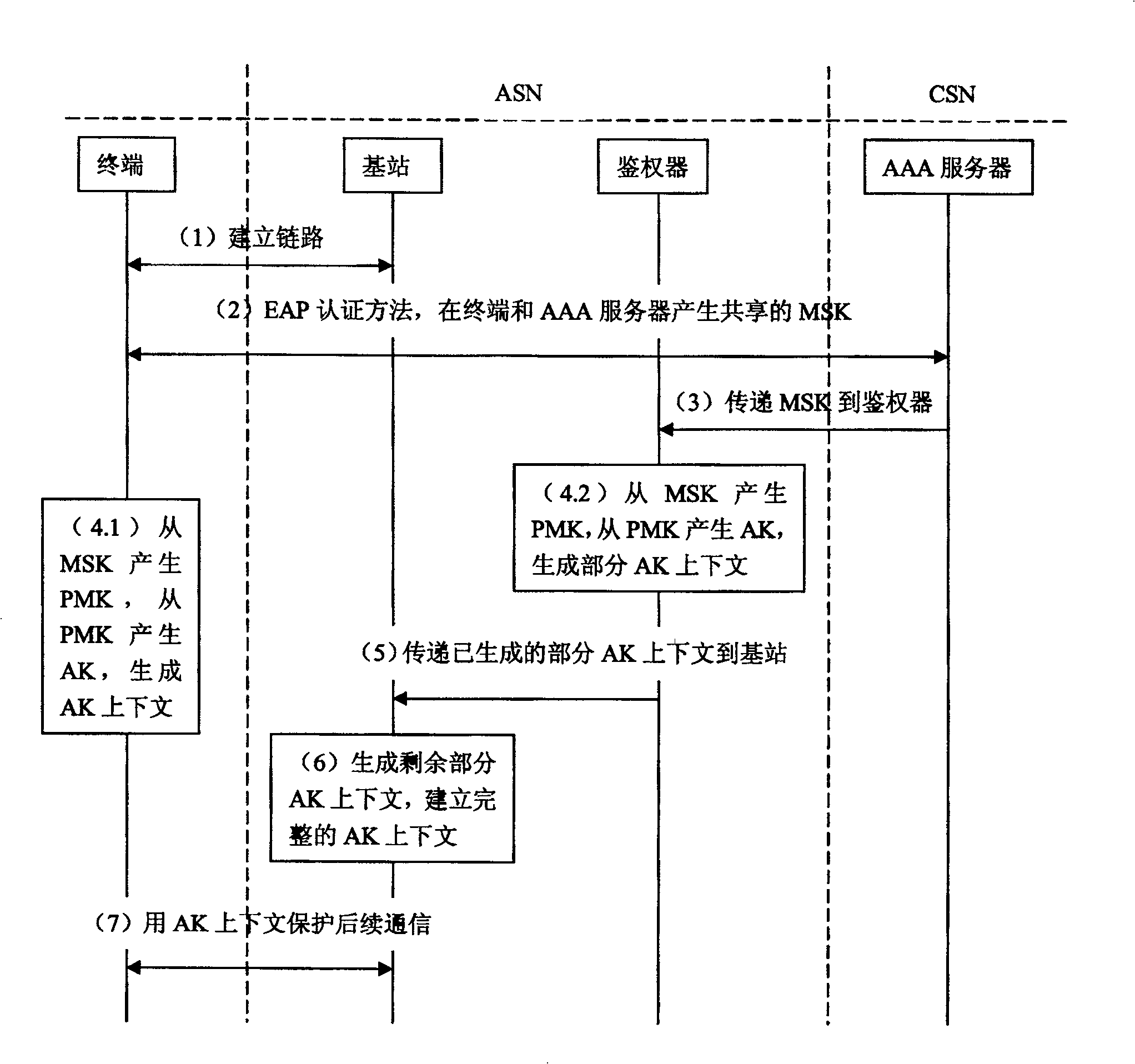
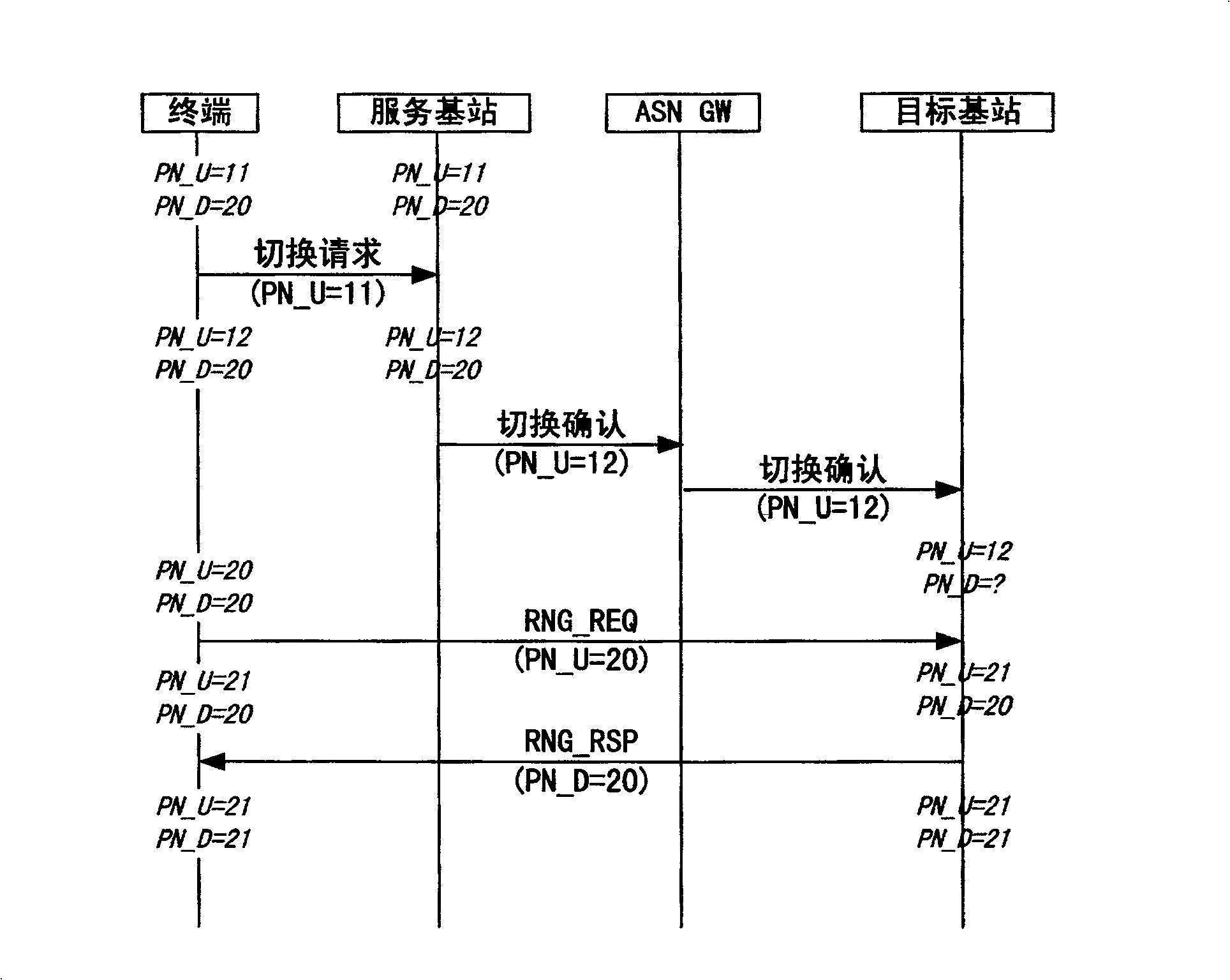
[0034] An embodiment of the present invention provides an AK context processing method, including: when a terminal switches between different base stations, the target base station obtains the value of the PN_U of the terminal from the serving base station; the target base station receives the ranging request message sent by the terminal, The ranging request message contains the value of PN_U of the terminal, wherein the value of PN_U is greater than or equal to the value of PN_D saved by the terminal; the target base station according to the value of PN_U of the terminal contained in the ranging request message and the terminal obtained from the serving base station The value of PN_U determines whether the received ranging request message is legal, and if it is legal, the value of PN_D of the target base station is set to be greater than or equal to the value of PN_U of the terminal contained in the ranging request message.
[0035] Through the above method, when the terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com