A method for carrying out numbering to working operation on channel protection ring
A channel protection and protection ring technology, applied in the field of optical transmission network, can solve the problems of complex implementation mechanism, unsatisfactory reliability, and high dependence on inter-node communication, and achieve enhanced reliability and robustness, high reliability, and simple process Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
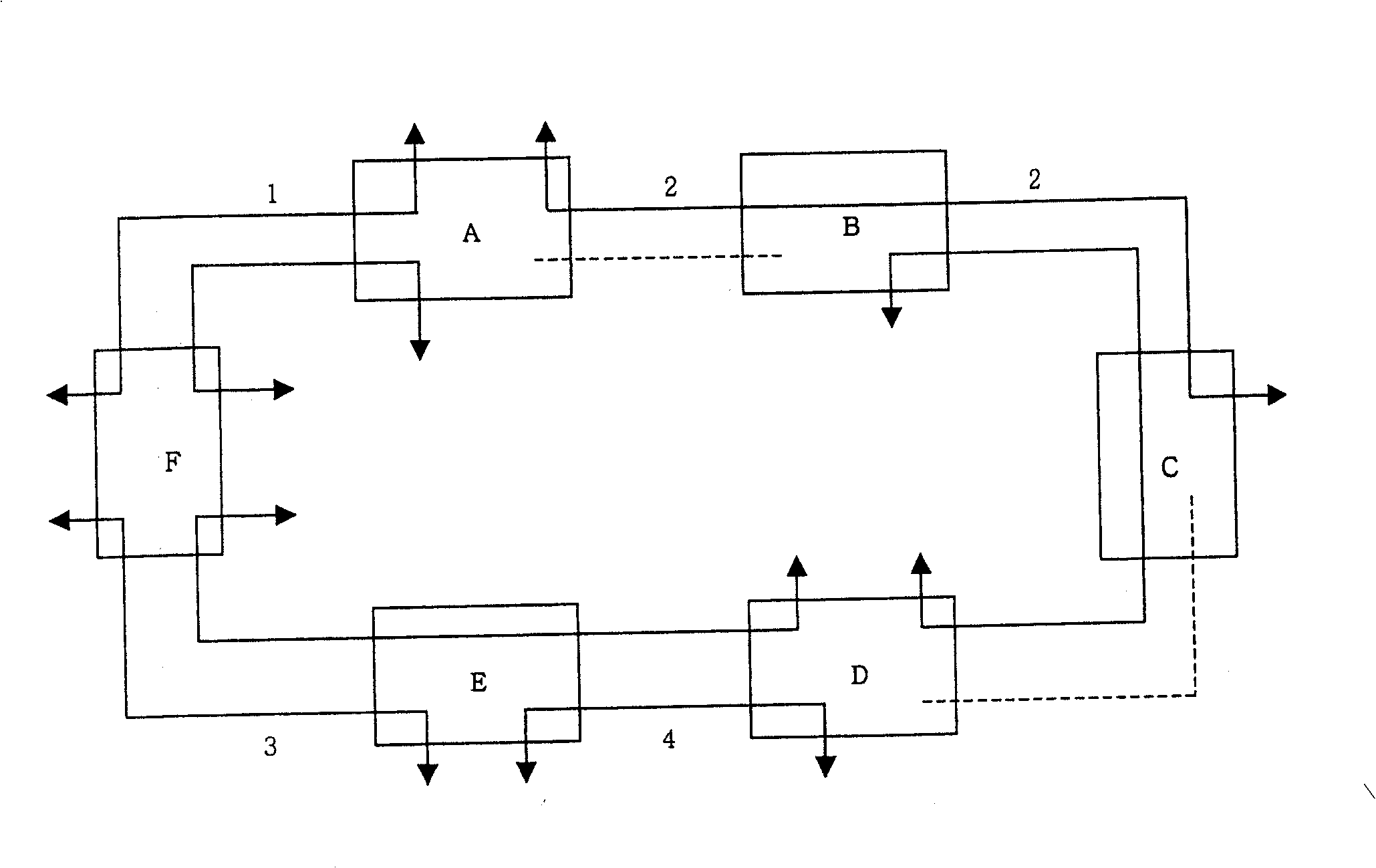
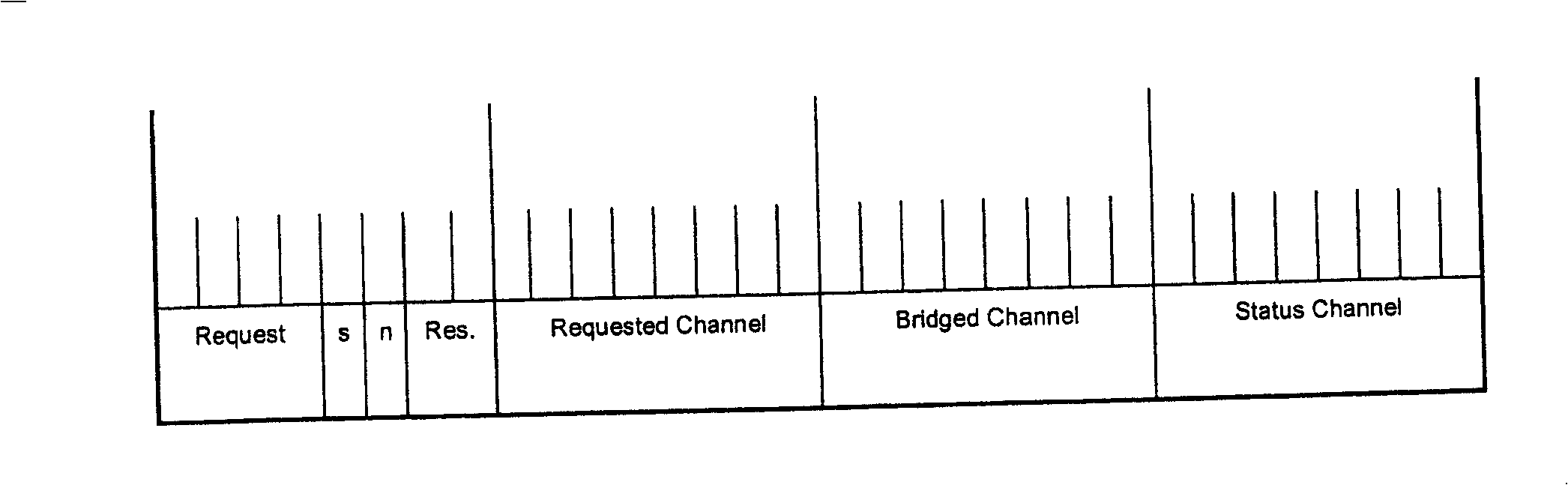
[0058] In this embodiment, each node in the protection ring is allocated a unique identification (ID) on the ring, and the unique identification (ID) of the node on the ring is used as the basis of the service number to interact on the ring, and finally based on the The unique identifier generates the service number of each working service on the ODUk protection ring. Specific steps are as follows:
[0059] 1. Assign a ring-wide unique identifier (indicated by Y here) for each node on the protection ring. For example, the ring node ID can be used directly, but the unique node identifier used to generate the service number is not limited to the ring node ID, and It can be allocated according to IP or manual allocation.
[0060] 2. Specify a uniform direction (clockwise or counterclockwise) on the ring, here we take clockwise as an example.
[0061] 3. Each node on the ring performs the following service numbering action: if the node has a clockwise insertion or extraction (AD...
Embodiment 2
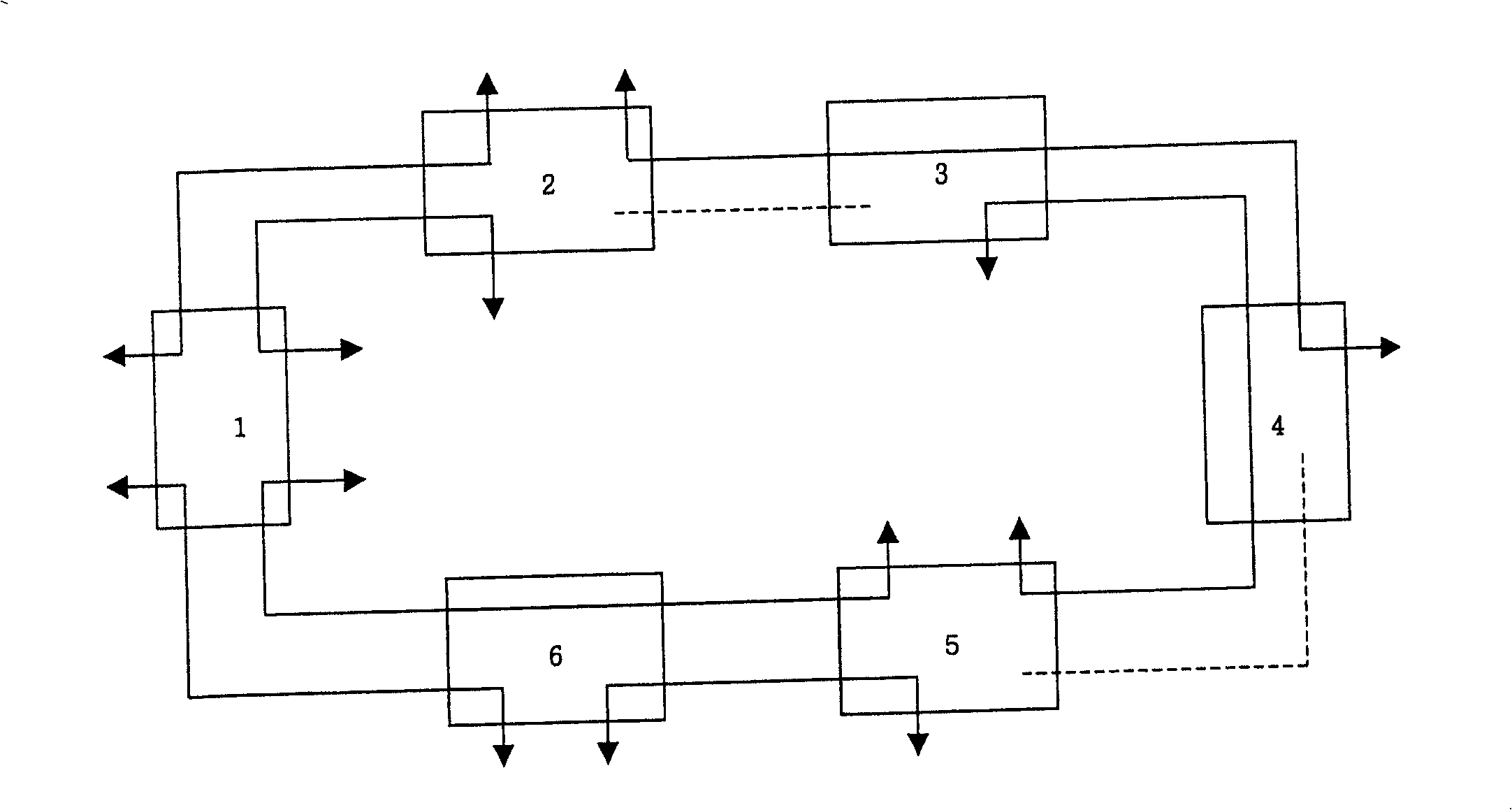
[0077] In the first embodiment above, the node on the protection ring corresponding to one end of the working service notifies the other end of the working service of the identifier of the node, and the other end numbers the working service based on the identifier. In Embodiment 2, the node on the protection ring corresponding to one end of the working service numbers the working service based on the identifier of the node, and then notifies the node at the other end of the working service. The specific steps can be as follows:
[0078] 1. Assign a ring-wide unique identifier to each node on the protection ring, for example, designate each node of the protection ring to use the ring node number as the ring-wide unique identifier.
[0079] 2. Specify a uniform direction on the ring, such as clockwise.
[0080] 3. Each node on the ring performs the following service numbering actions: if a node has a clockwise insertion or extraction (ADD\DROP) work service from the protection ...
Embodiment 3
[0087] For the numbering of multicast services, Embodiment 3 of the present invention needs special explanation. Here, one multicast service sent to multiple nodes is equivalent to multiple services for service numbering. The service configuration is as follows Figure 5 , Figure 5 The multicast service is sent from node 1 and received at nodes 2 and 3.
[0088] For such a multicast service, we can equivalently consider that node 2 receives a work service from node 1, and itself (node 2) sends another work service to node 3. In this way, we equate the multicast service to Image 6 Two working operations are shown. The difference is that the service received by node 2 from node 1 is the same as the service content sent by node 2 to node 3 . As for the service number, it does not affect whether the two services are the same. In this way, applying the service numbering method proposed by the present invention and putting it into the previous embodiment 1 (or embodiment 2), ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com