Quick and safe real-time database access method
A database and security technology, applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve the problems of reducing write operation efficiency and low efficiency, and achieve the effect of fast access and improved access efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
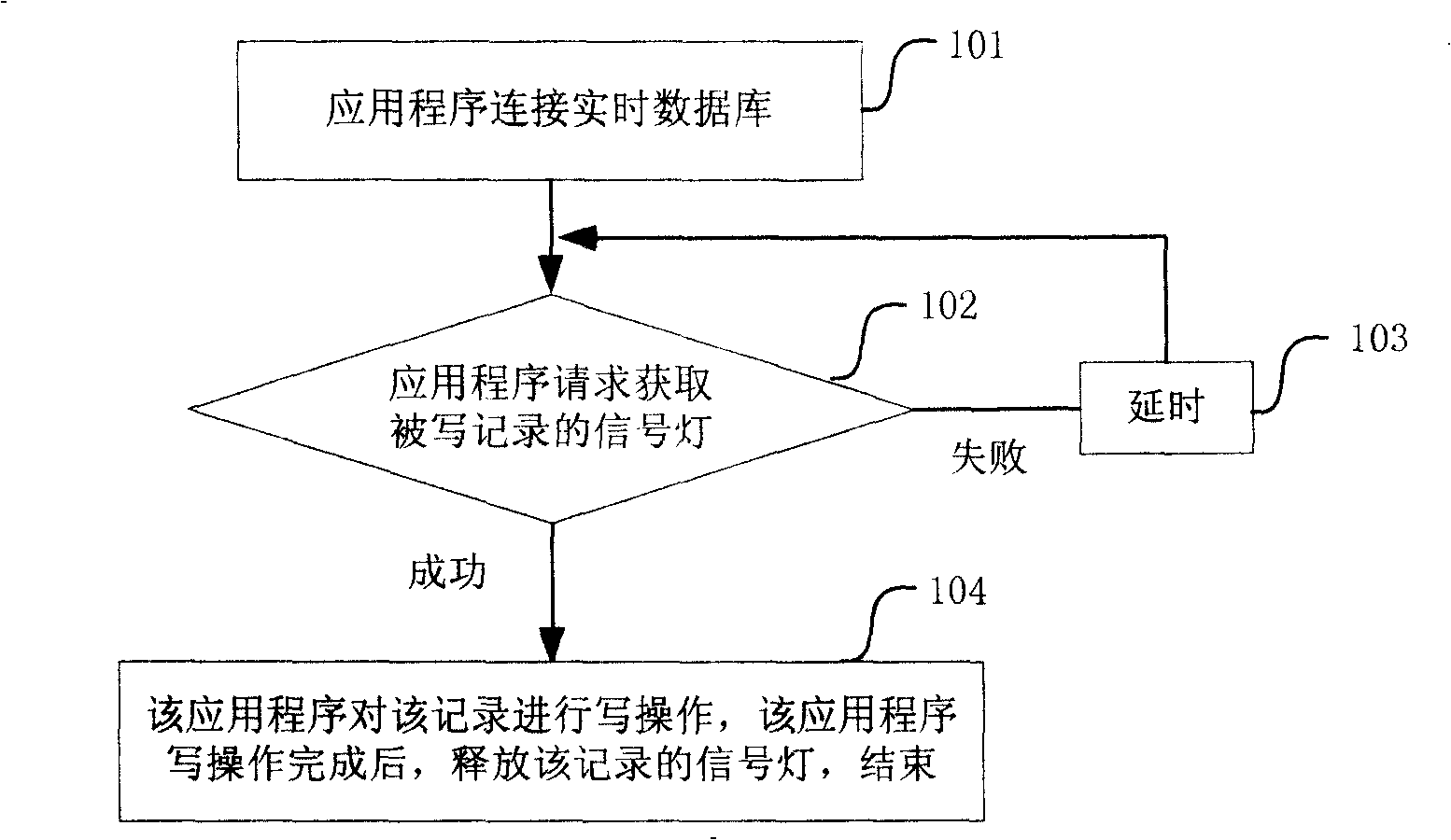
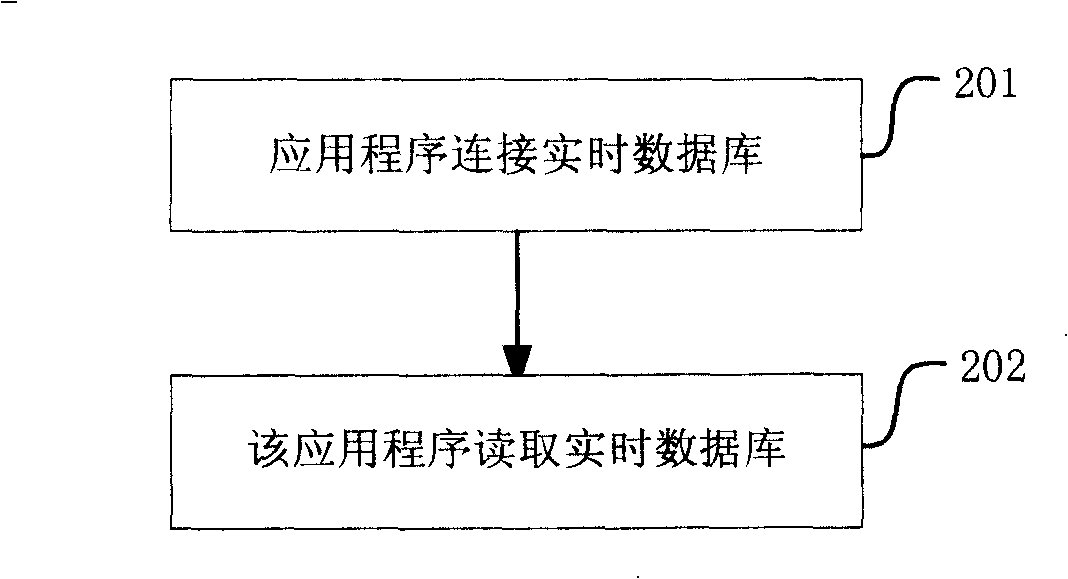
[0027] Through the analysis of real-time database access behavior, it is found that there are three main operations on real-time database: read, write and update. in:
[0028] The read operation refers to reading the data in the real-time database, which will not have any impact on the real-time database, but it is necessary to stop all read operations on the real-time database when the real-time database is updated;
[0029] The write operation refers to the modification of the data value in the real-time database, which does not affect the read operation of the real-time database, but the write operations to the same record are mutually exclusive, that is, the same record cannot be written at the same time. And when the real-time database is updated, it is necessary to stop all write operations to the real-time database;
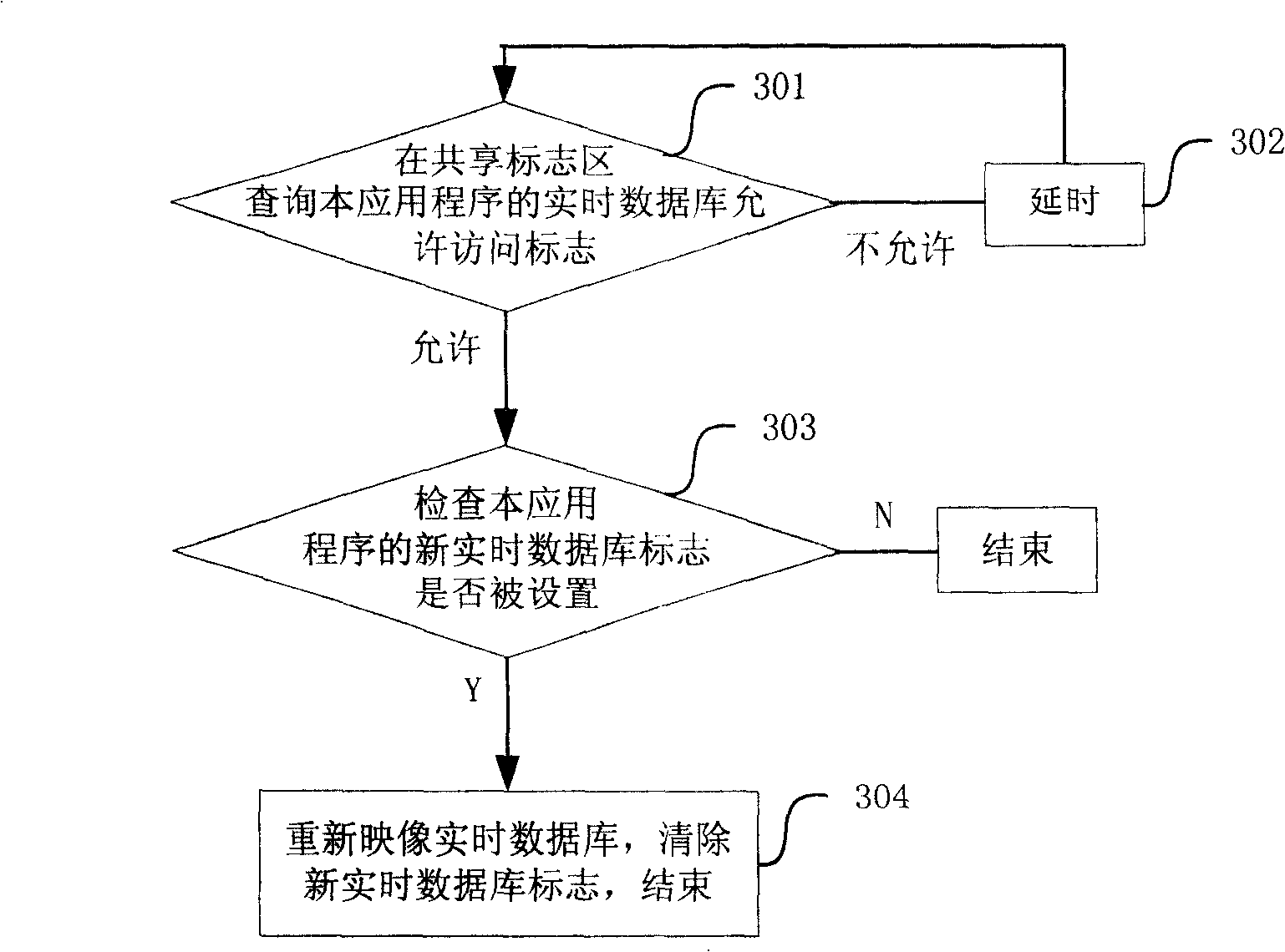
[0030] The update operation refers to the update of the entire real-time database data. It needs to reload the data to the memory, which affects all oper...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com