Method for conducting secrete handling for PC broadside-on mobile terminal information
A mobile terminal, PC technology, applied in the direction of electrical digital data processing, telephone communication, computer security devices, etc., can solve the problem of no security technology and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
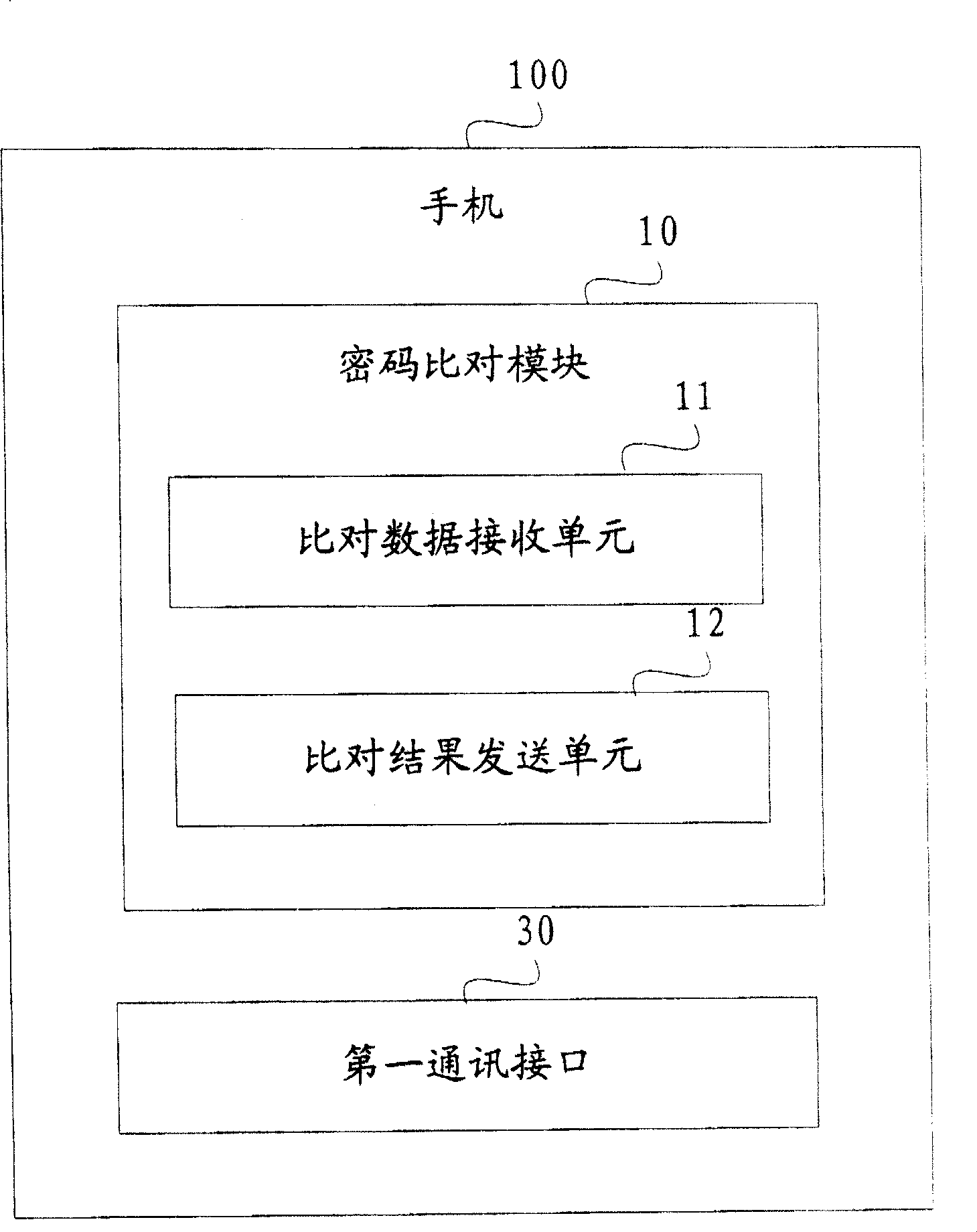
[0018] Such as figure 1 Shown is a schematic structural diagram of the mobile phone according to the embodiment of the present invention.
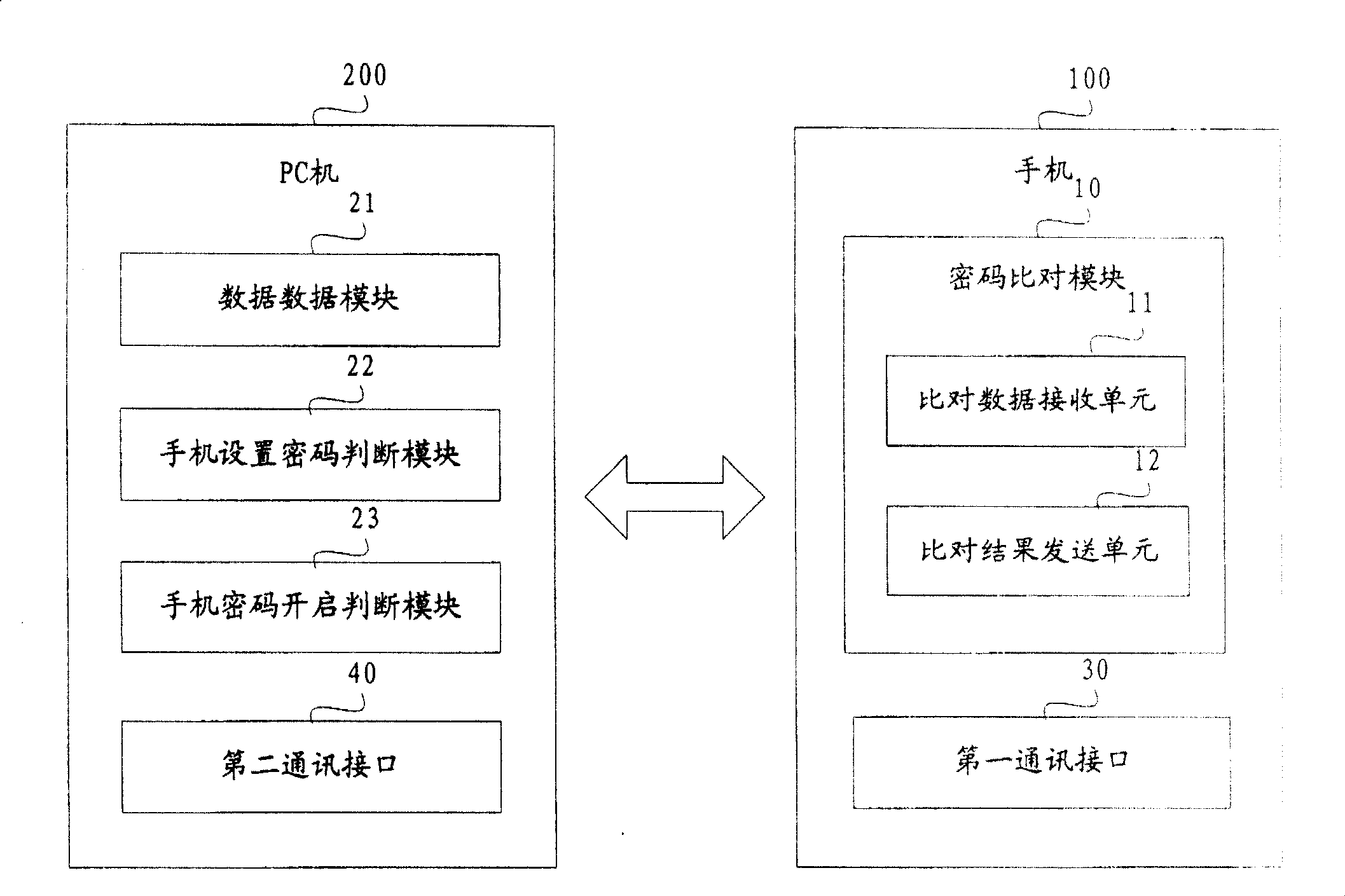
[0019] The mobile phone 100 of the present invention includes a password comparison module 10, a first communication interface 30 (such as a USB interface, a bluetooth interface, an infrared interface, a ZigBee interface) and a first communication interface 30 (such as a USB interface, a bluetooth interface, an infrared interface, etc.) interface or Wi-Fi interface), wherein, 10 in the password comparison module includes a comparison data receiving unit 11, a comparison result sending unit 12; the comparison data receiving unit 11 receives the data received from the first communication interface 30, and compares The comparison result sending unit 12 sends the comparison result data received from the comparison data receiving unit 11 and compared by the password comparison module 10 to the first communication interface 30 .
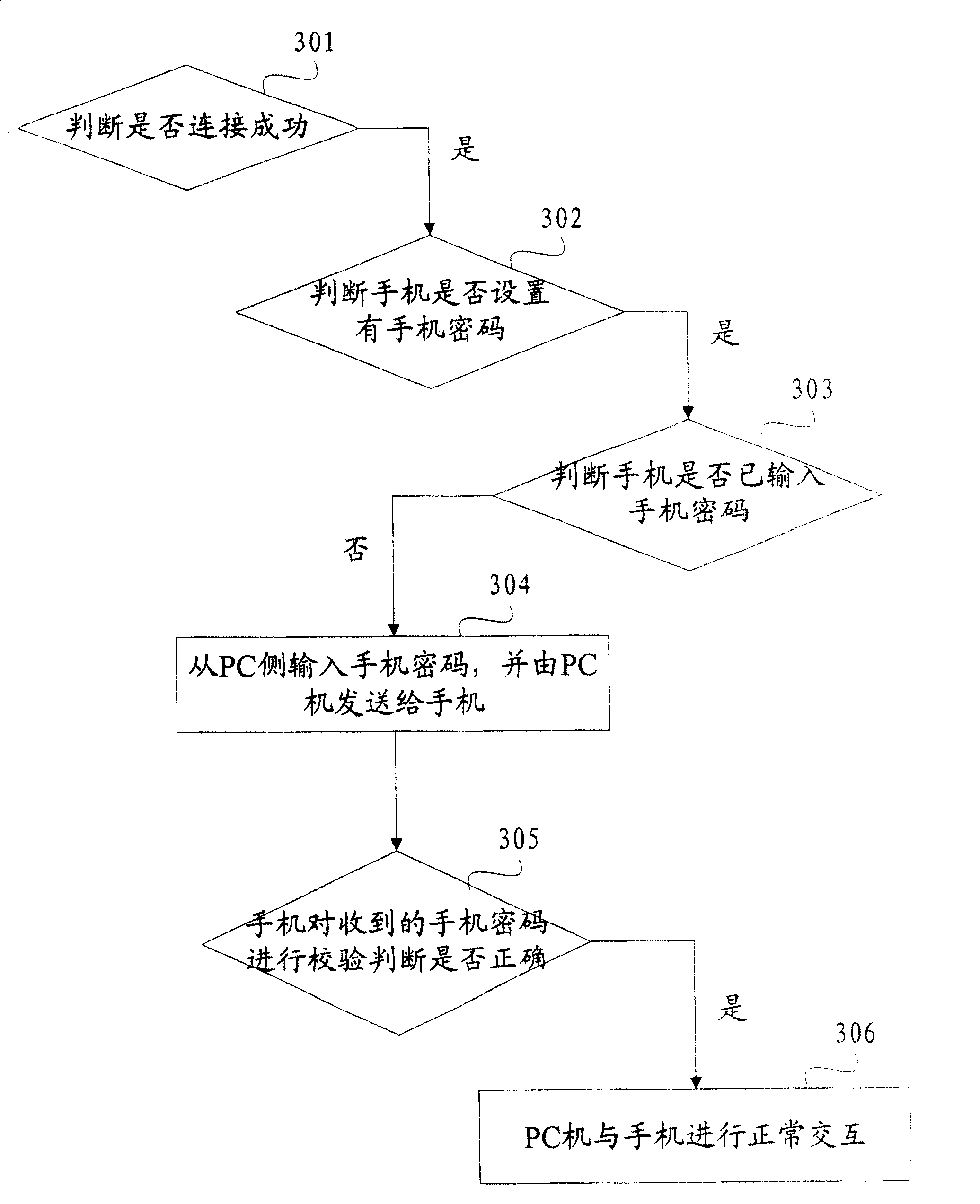
[0020] Such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com