Method for authentication of identity of network user
An identity authentication and network user technology, applied in the field of identity authentication that prevents user operations from being blocked by specific external software programs, can solve problems such as increased maintenance costs, easy to be tracked and analyzed by plug-ins, and achieve the effect of improving efficiency and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The invention provides a network user's identity authentication method, which prevents specific external programs from shielding or replacing the user's network operations.
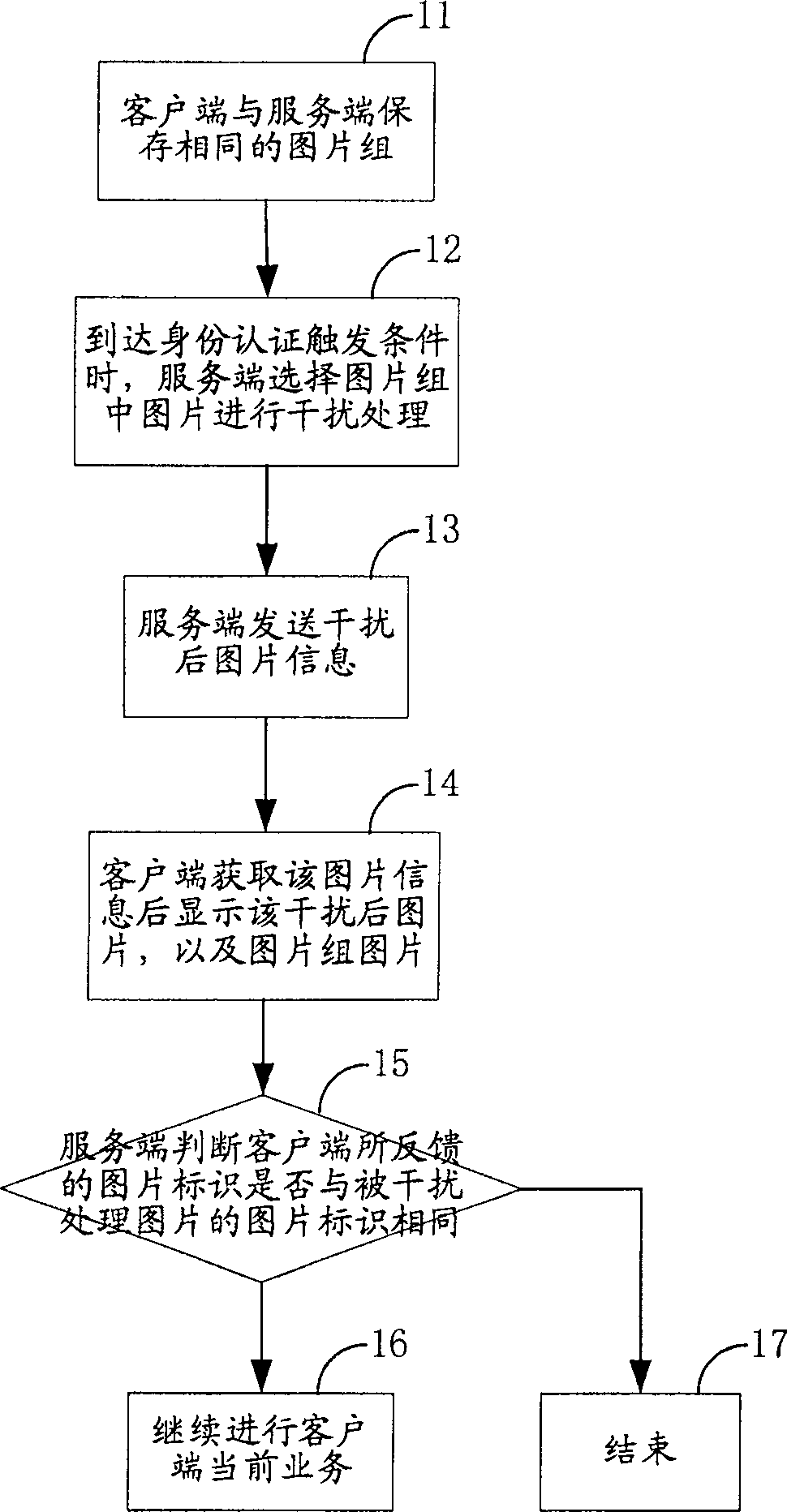
[0049] refer to figure 1 , illustrating an implementation method of an identity authentication method of the present invention.
[0050] 11) The client and the server save the same picture group; the client and the server can save one picture group or multiple picture groups, and each group of pictures should consist of at least two pictures;
[0051] 12) When the identity authentication trigger condition is reached, the server selects at least one picture in the picture group for interference processing, and obtains the disturbed picture;
[0052] The arrival of the identity authentication trigger condition can be the timer reaching the preset business operation duration, or the business has reached a certain stage, which can be used alone or in combination according to the characteristics of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com