Security authentication method of radio-frequency identification system
A radio frequency identification system and security authentication technology, which is applied in the field of radio frequency identification system security authentication based on hash function, can solve the problems of increasing system cost, being vulnerable to counterfeiting attacks and retransmission attacks, and tags being easily traced, so as to ensure legality. performance, cost reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0021] The specific implementation of the radio frequency identification system security authentication method is as follows:
[0022] First, the RFID system is initialized.
[0023] The radio frequency identification system includes three components: background database, reader and tag. When the system is initialized, a unique identifier ID is assigned to each tag. The background database has the identifier ID of all tags. In the background database, each tag Create an array (oldID, newID). The array corresponding to each tag is (0, newID) during initialization, newID is the ID value of each tag, and the oldID value is 0 when initialized.
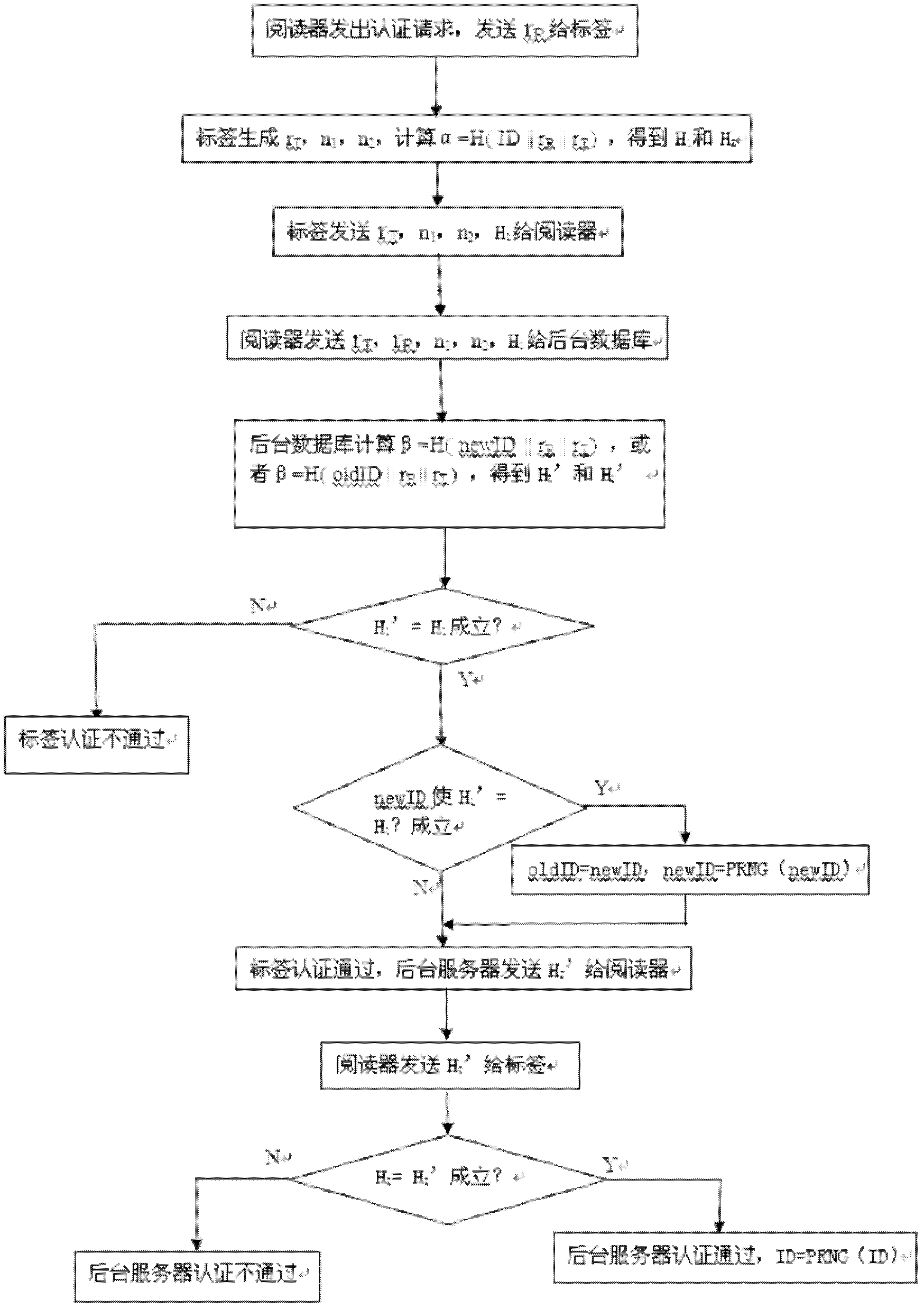
[0024] Second, the security authentication process, such as figure 1 As shown, including five rounds of communication process:
[0025] (1) In the first round, the reader sends data to the tag;
[0026] The reader generates a pseudorandom number r R , the reader sends a query authentication request to the RFID tag, and sends r R give ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com