Method for protecting the computer data
一种计算机、计算机系统的技术,应用在计算机安全装置、计算、电数字数据处理等方向,能够解决没兴趣、效能无法实质的提升、影响计算机正常运作等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
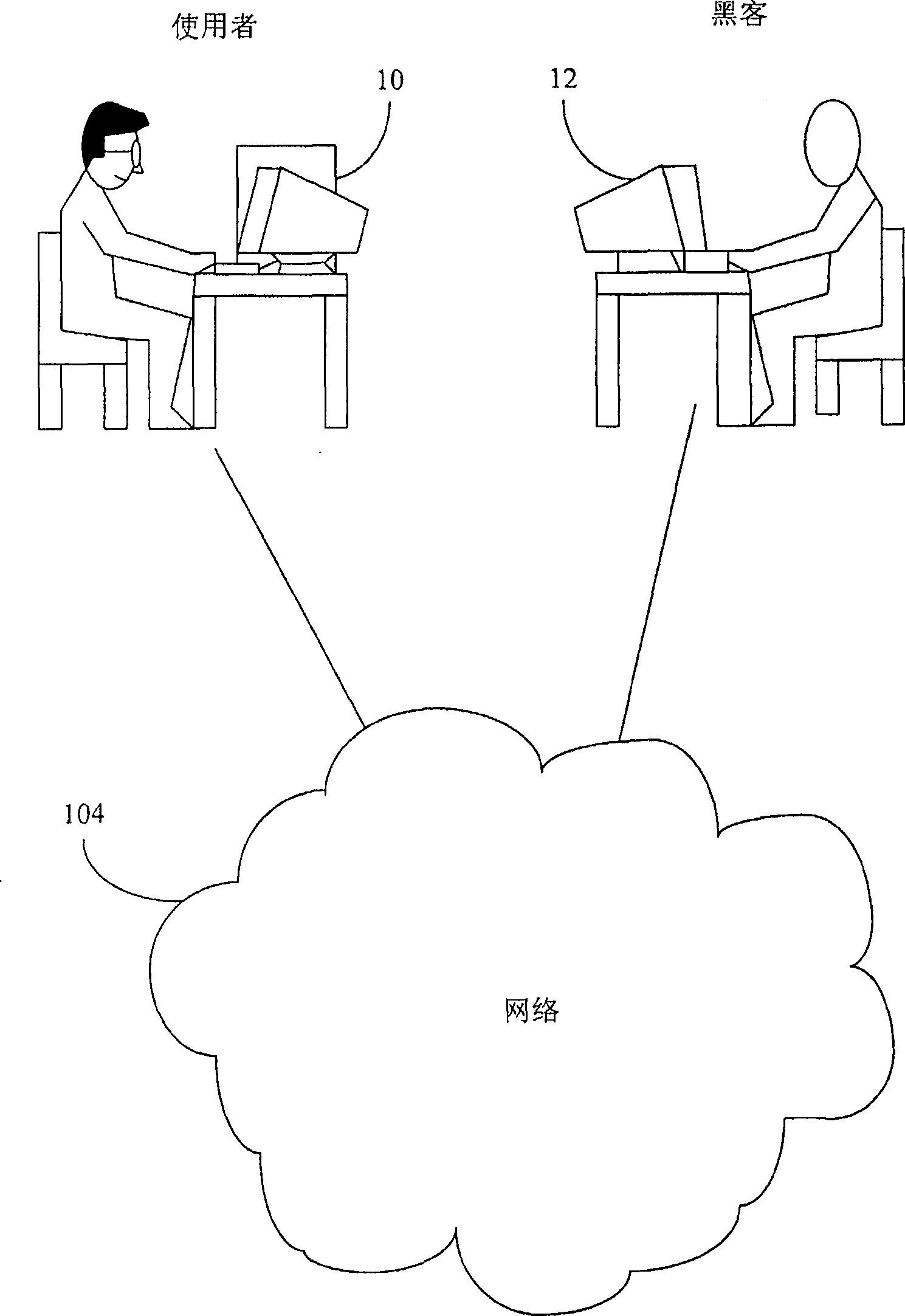
[0036] Please refer to figure 1 , this figure shows a basic network structure diagram. After a user 10 is connected to the network 104 , the data stored on the computer by the user 10 may be destroyed or stolen due to the intrusion of the hacker 12 through the network 104 . For example, if the hacker 12 can decode the password set by the user 10 , he can browse the data stored in the computer by the user 10 through the network 104 . In addition, the hacker 12 may also make a virus and spread it through the network 104 , and the user 10 will load back the file with the virus when using the network 104 . When these virus-bearing files are loaded back to the computer of the user 10, under specific conditions, such as when the infected file is executed or the macro program is executed, it will further sneak into the program module of the operating system, wait for an opportunity to occur, and execute damage. action. Therefore, the present invention provides a system and method ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com