Method and device for solving Hash collision
A first-in-first-out queue and idle address technology, applied in the field of solving Hash conflicts, can solve problems such as long search time and Hash conflicts, and achieve the effect of solving Hash conflicts, saving bandwidth, and realizing wire-speed forwarding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] join Figure 4 , a method for adding a linked list, the method includes the following steps:
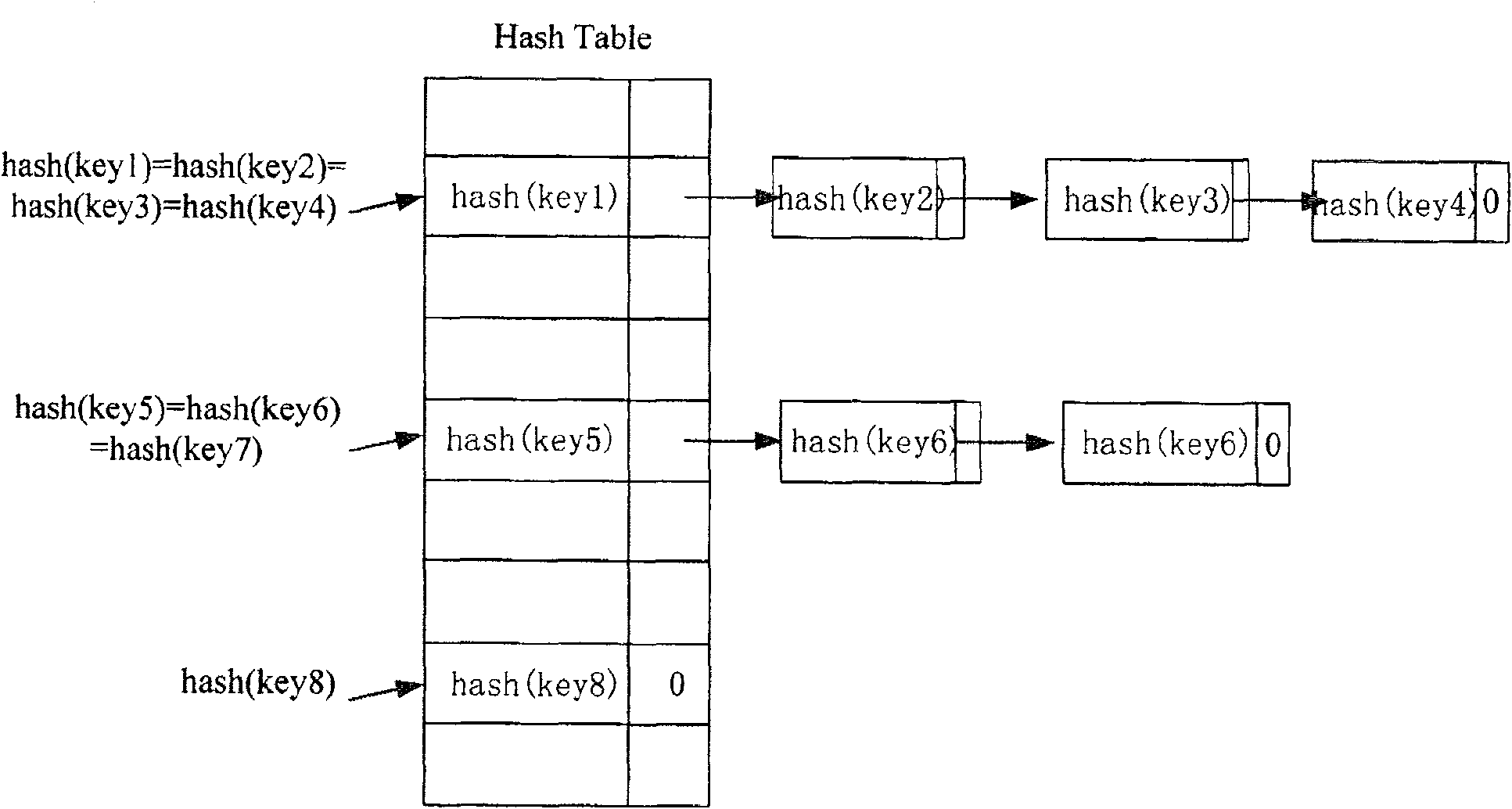
[0050] Step 101: Perform a hash operation on the information to be stored, look up the hash table according to the operation result, and find the head of the linked list corresponding to the operation result. The hash table here is composed of a linked list head, a pointer and a linked list tail.
[0051] Step 102: judge whether the head of the linked list is empty, if it is empty, execute step 103; otherwise, execute step 104;
[0052] Step 103: Fill the head of the linked list with the operation result of the information to be stored.
[0053] Step 104: Determine whether the content stored in the head of the linked list is the same as the operation result of the information to be stored, if they are the same, go to step 105; otherwise, go to step 106.
[0054] Step 105: Do not process the operation results of the information to be stored.
[0055] Step 106: Determine whe...
Embodiment 2
[0072] see Figure 5 , a method for deleting an entry in a linked list, the method specifically includes:
[0073] Step 201: When there is information to be deleted, perform a hash operation on the information to obtain the operation result, find the corresponding entry in the hash table according to the operation result, and release the entry, that is, the content in the entry delete;
[0074] Step 202: Determine whether there is a pointer pointing to the next entry in the current entry, if yes, execute step 203, otherwise, execute step 204.
[0075] Step 203: Modify the pointer of the previous entry of the current entry to the pointer stored in the current entry, if the current entry is the head of the linked list, put the content of the next entry pointed to by the pointer into the head of the linked list;
[0076] Step 204: delete the pointer of the previous entry of the current entry;
[0077] Step 205: Write the address of the current entry into the write FIFO module ...
Embodiment 3
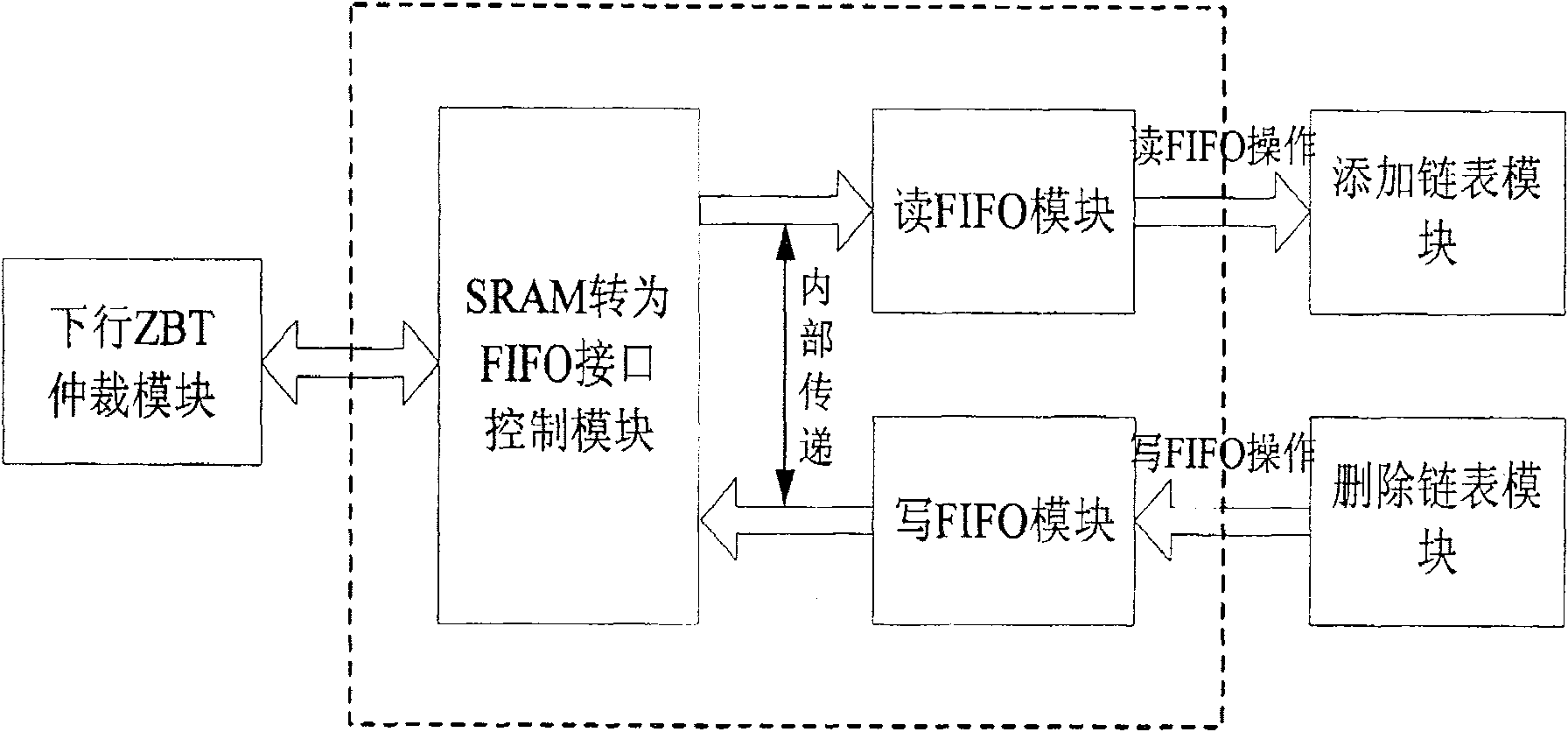
[0082] see Figure 6 , to the maintenance method of the conflict (idle) address in the Hash table structure, this method applies image 3 The modules in the schematic diagram provided are carried out, and the specific steps are as follows:
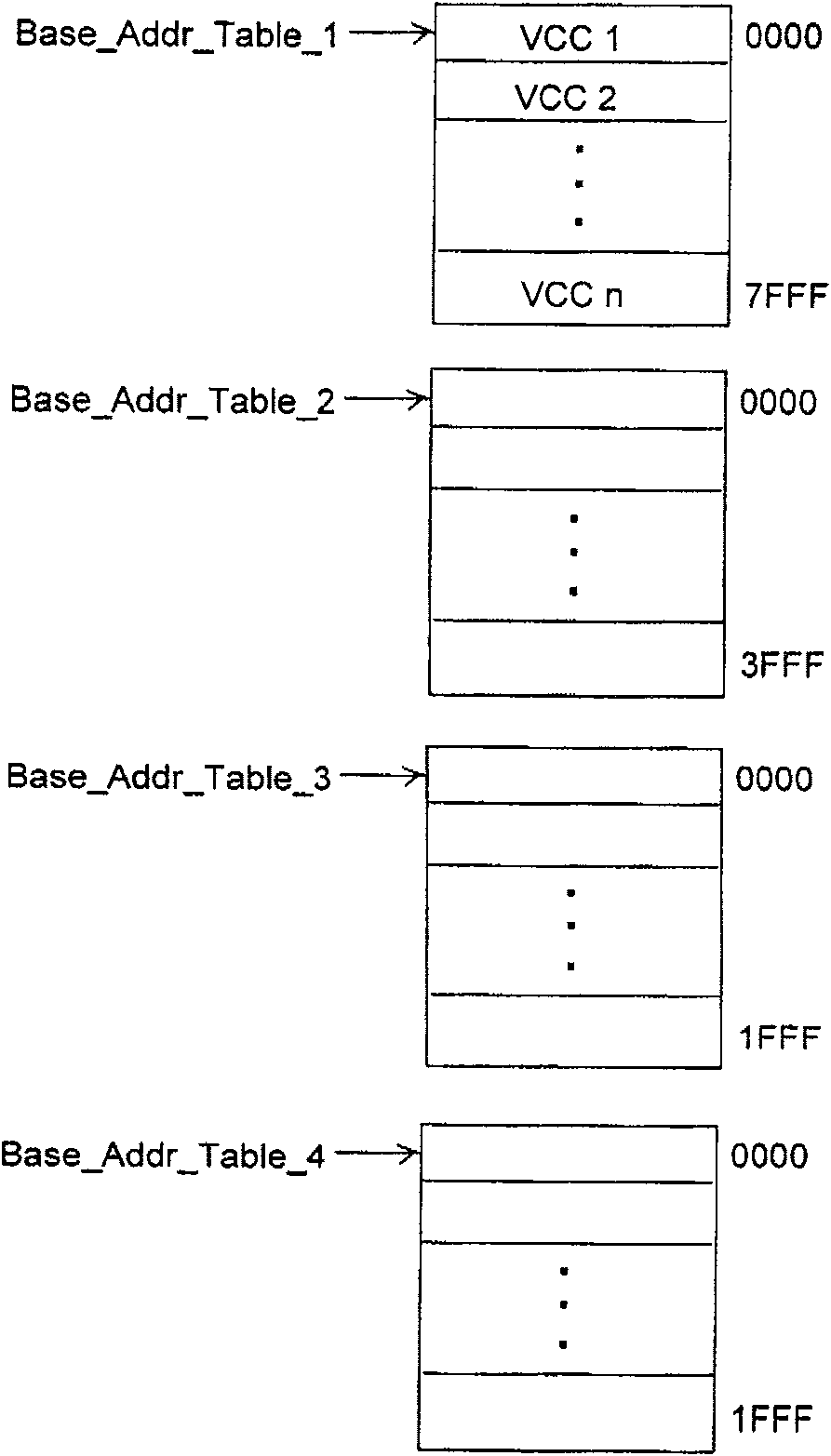
[0083] Step 301: Initialize the free address pool, and write the conflicting address into the corresponding offset address.
[0084] In this embodiment, two 16×13bit FIFO reset signals are first pulled high, and the FIFO is reset for 8 time periods, and then pulled low, mainly because the FIFO has certain requirements for the length of the reset signal.
[0085] A preset value is set for the number of conflicting addresses in the read FIFO module and the write FIFO module. The preset value can be set according to experience, and this embodiment takes 4.
[0086] Then send an application to the downstream ZBT (Zero-Bus Turnaround, zero bus delay), and write the 8k conflict addresses into the corresponding offset addresses in sequence. Afte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com