Method for revising terminal configuration, network side management unit, terminal and system
A management unit, network-side technology, applied in the direction of network data management, electrical components, security devices, etc., can solve the problems of non-confidentiality, difficult maintenance, leakage, etc., to facilitate expansion and transformation, simplify configuration and upgrade, prevent The effect of equipment switching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
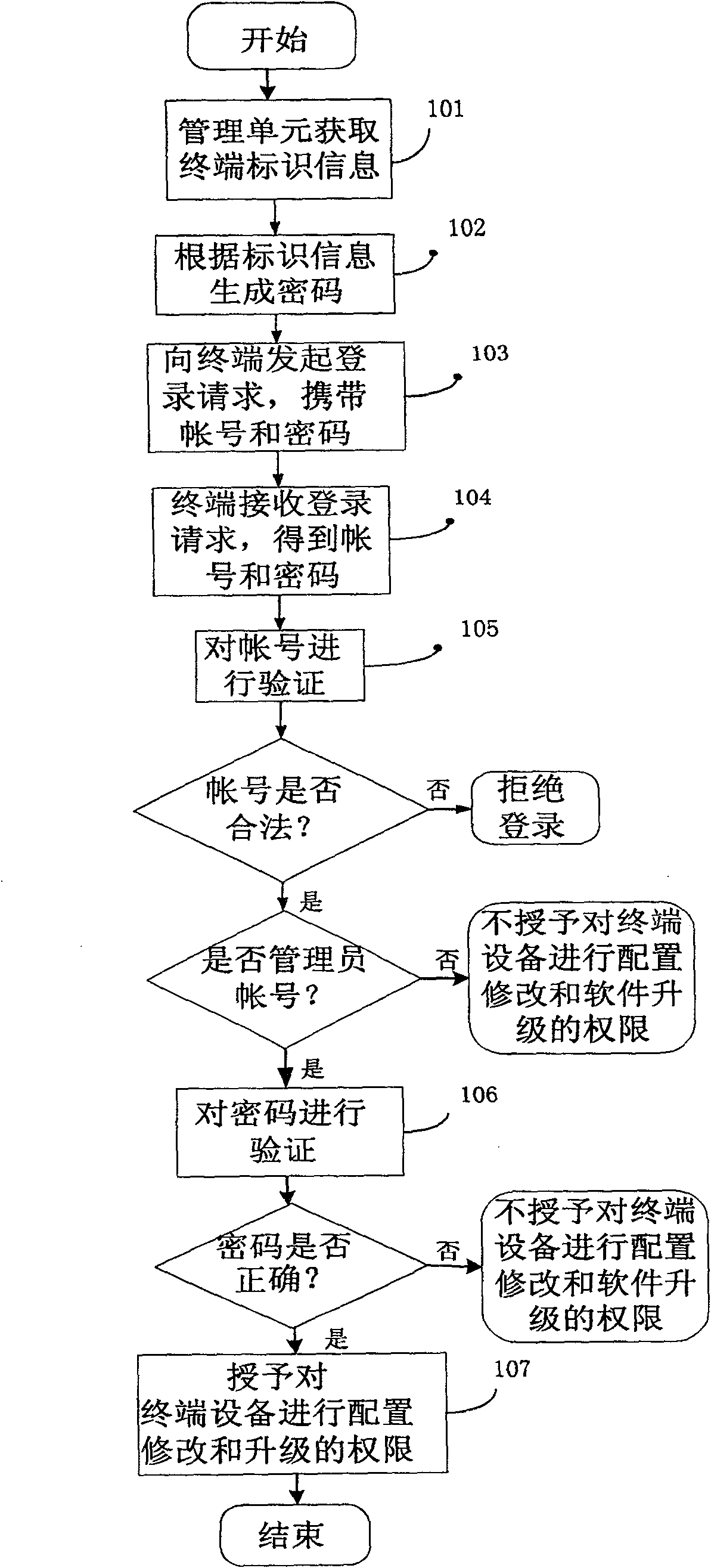
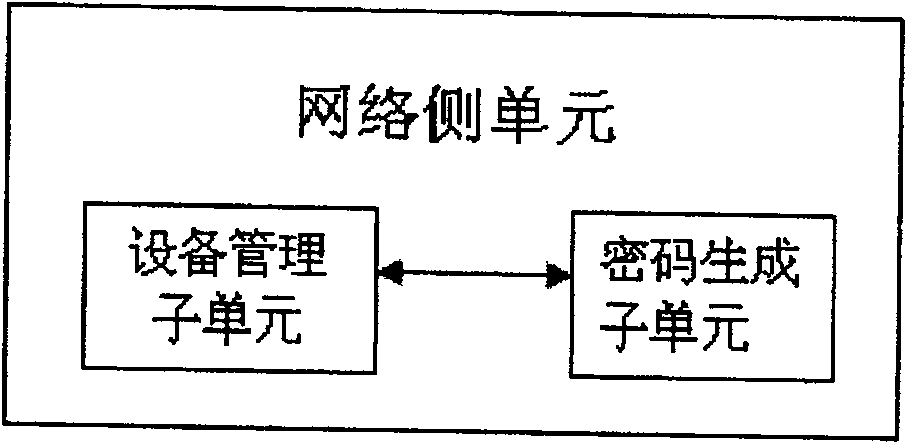
[0060] refer to image 3 , to describe the network side management unit. The network side management unit of the present invention may be a hardware or software function module integrated in the central office system, including: a device management subunit and a password generation subunit. When logging in to the device from the network side management system, the device management subunit of the management unit obtains the identification information of the terminal device, which can be an identifier such as a MAC address or a product number; the password generation subunit of the management system has a built-in encryption algorithm , the encryption algorithm generates a password after calculation according to the identification information, and feeds back the password to the device management subunit, and the password is invisible to the operator. The device management subunit initiates a login request to the terminal device. The login account is generally carried in the lo...
Embodiment 2
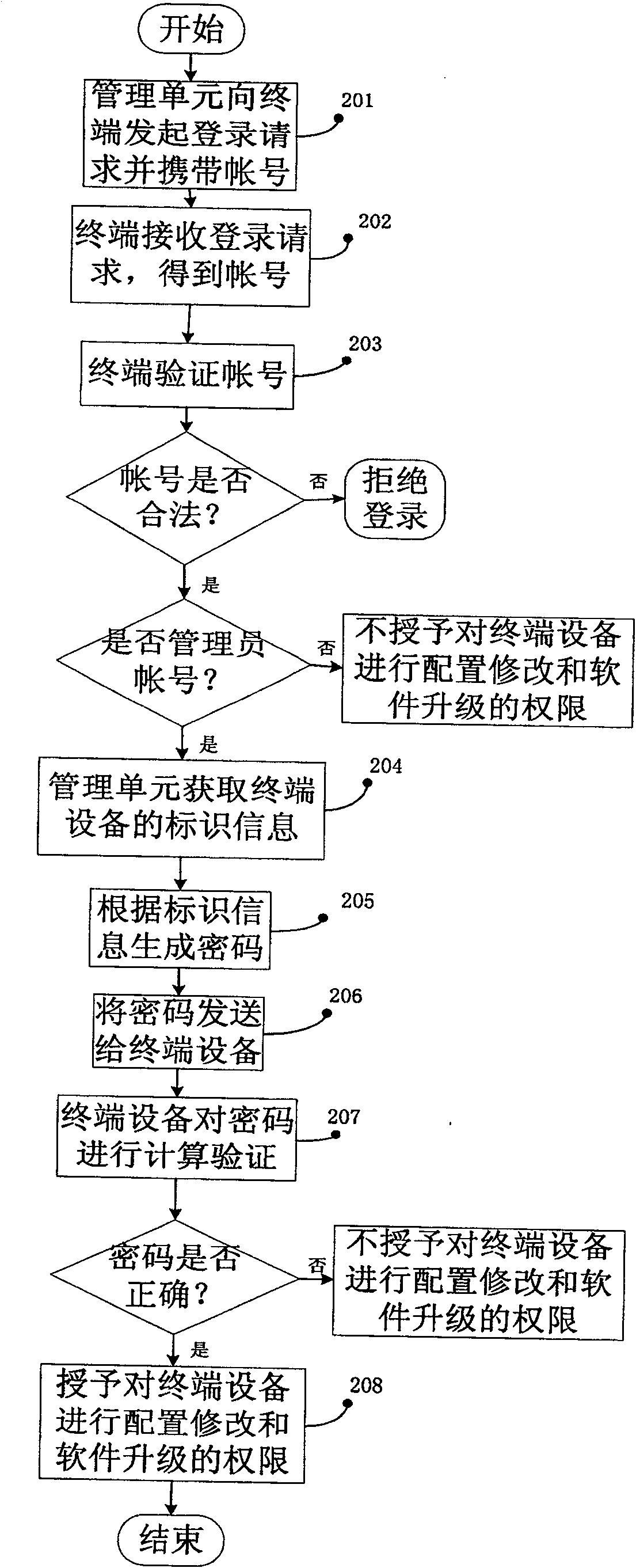
[0063] refer to Figure 4 , to describe the terminal device of the present invention. The terminal equipment includes a user management unit and a password verification unit. The user management unit is used to receive a login request and a password from the network side, and verify the password by the password verification unit; if the login request carries a login account, verify the validity of the login account; if the login account is not valid If the login account is legal, the login request is accepted and the login is allowed, and then it is verified whether the login account is an administrator account. If it is not an administrator account, the authority to modify the configuration and upgrade the software is not granted, and if so, the password verification unit is triggered. The password is verified; the password verification unit has a built-in encryption algorithm, which is the same as the encryption algorithm in the corresponding network side management unit, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com