Method and device for realizing the extended authentication protocol in the wireless network
An extended authentication protocol, wireless network technology, applied in the field of wireless communication, can solve problems such as limited parameter information, inability to ensure network security performance, and inability to complete the EAP authentication process well, to improve security and maintain benefits Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
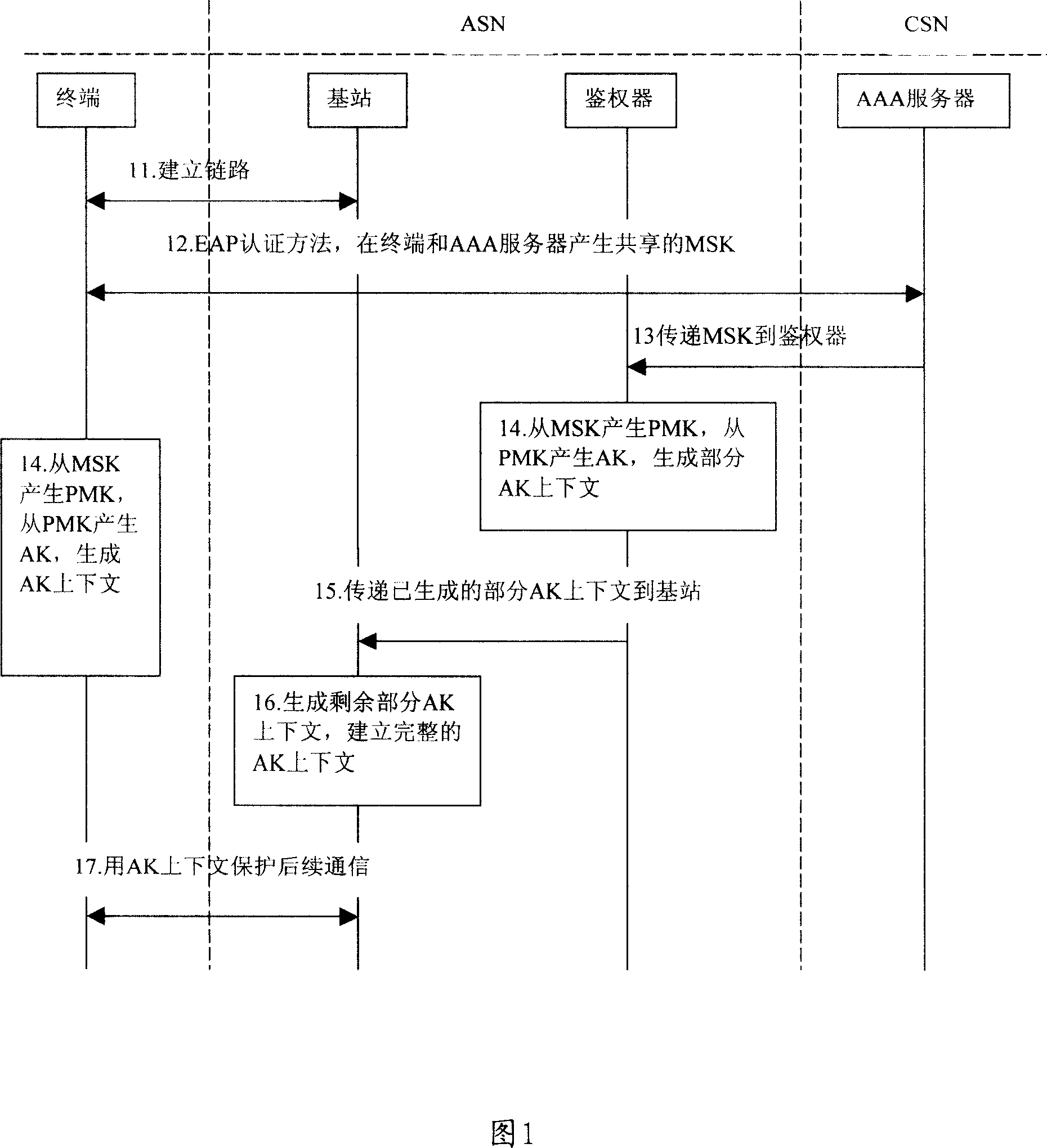
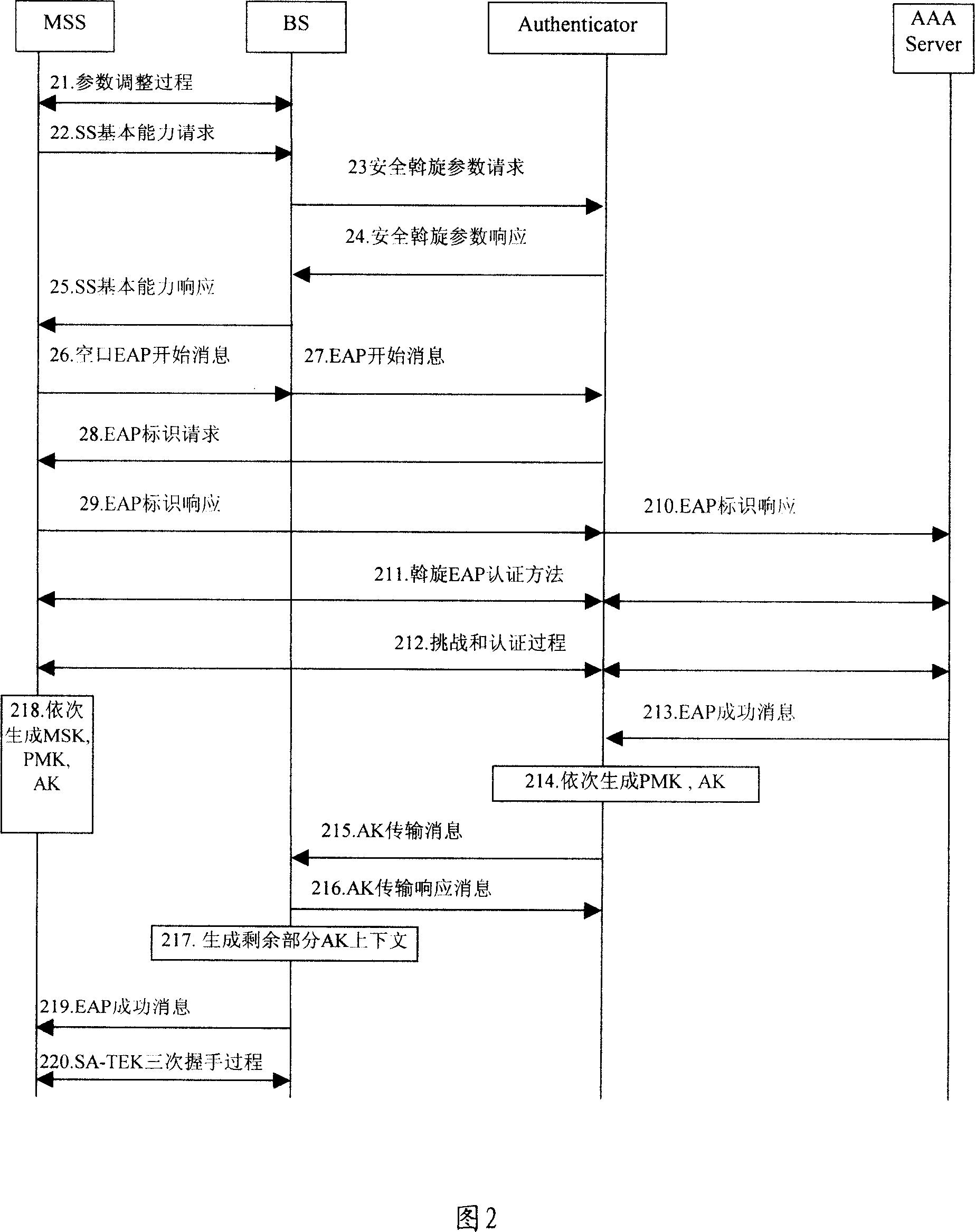
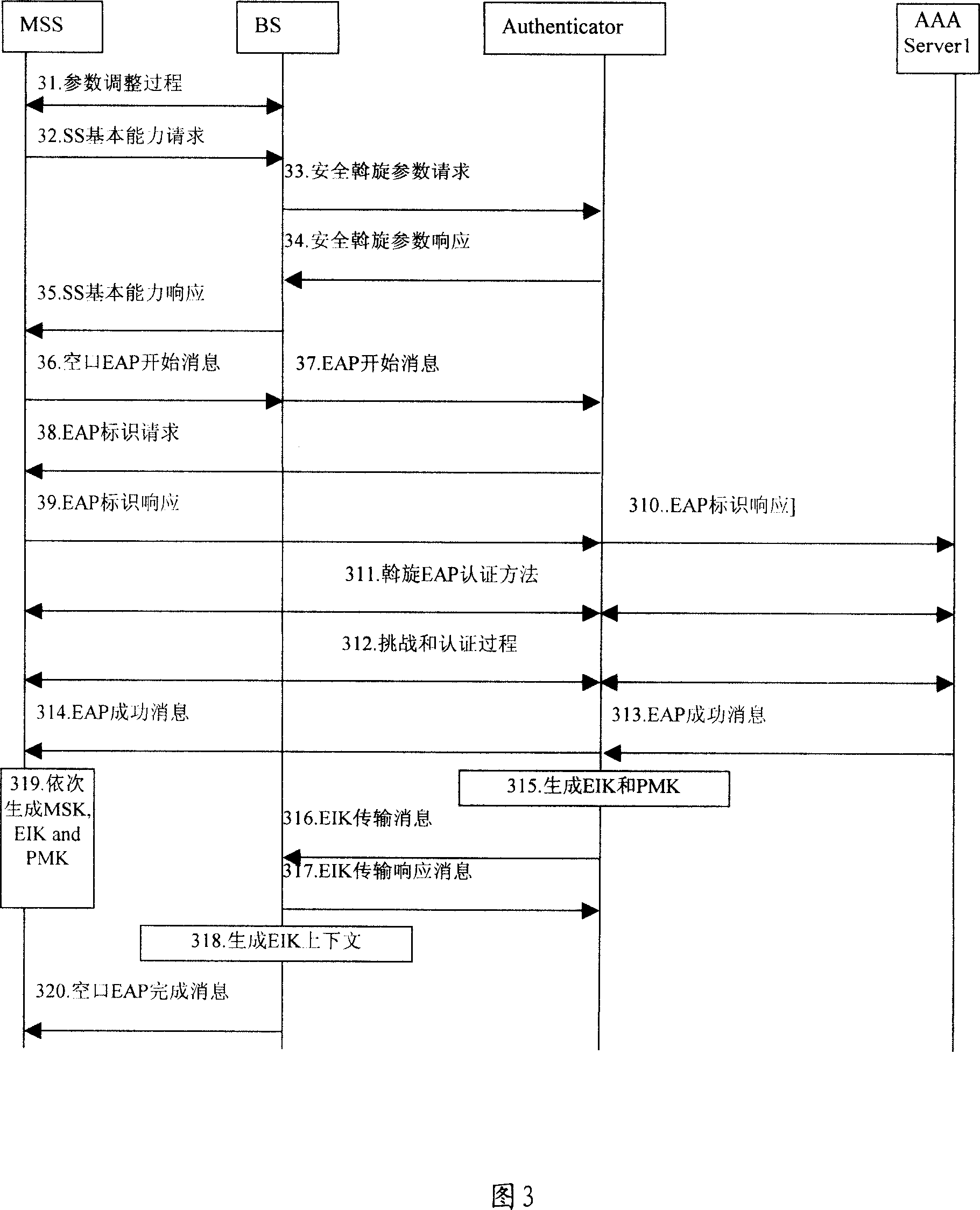
[0100] In the method for implementing Extended Authentication Protocol authentication in a wireless network provided by the present invention, in order to enable the BS to know when the first EAP process is completed, an AUTHRELAY EIK-Transfer message is defined, so that the BS knows the first EAP process through this message. The process is completed, and the PKMv2 PKM-RSP / EAP-Complete message is sent on the air interface, indicating that the MSS has completed the first EAP process.
[0101] Specifically, an EIK-Transfer message is defined between the BS and the authenticator, and the message has two functions: the first aspect is used to transmit the EIK to the BS, and the second aspect is used to instruct the BS to perform the first EAP authentication process After successful completion, the BS is stimulated to initiate the second EAP authentication process.
[0102] In the specific implementation process of the present invention, in order to meet the needs of the EAP authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com