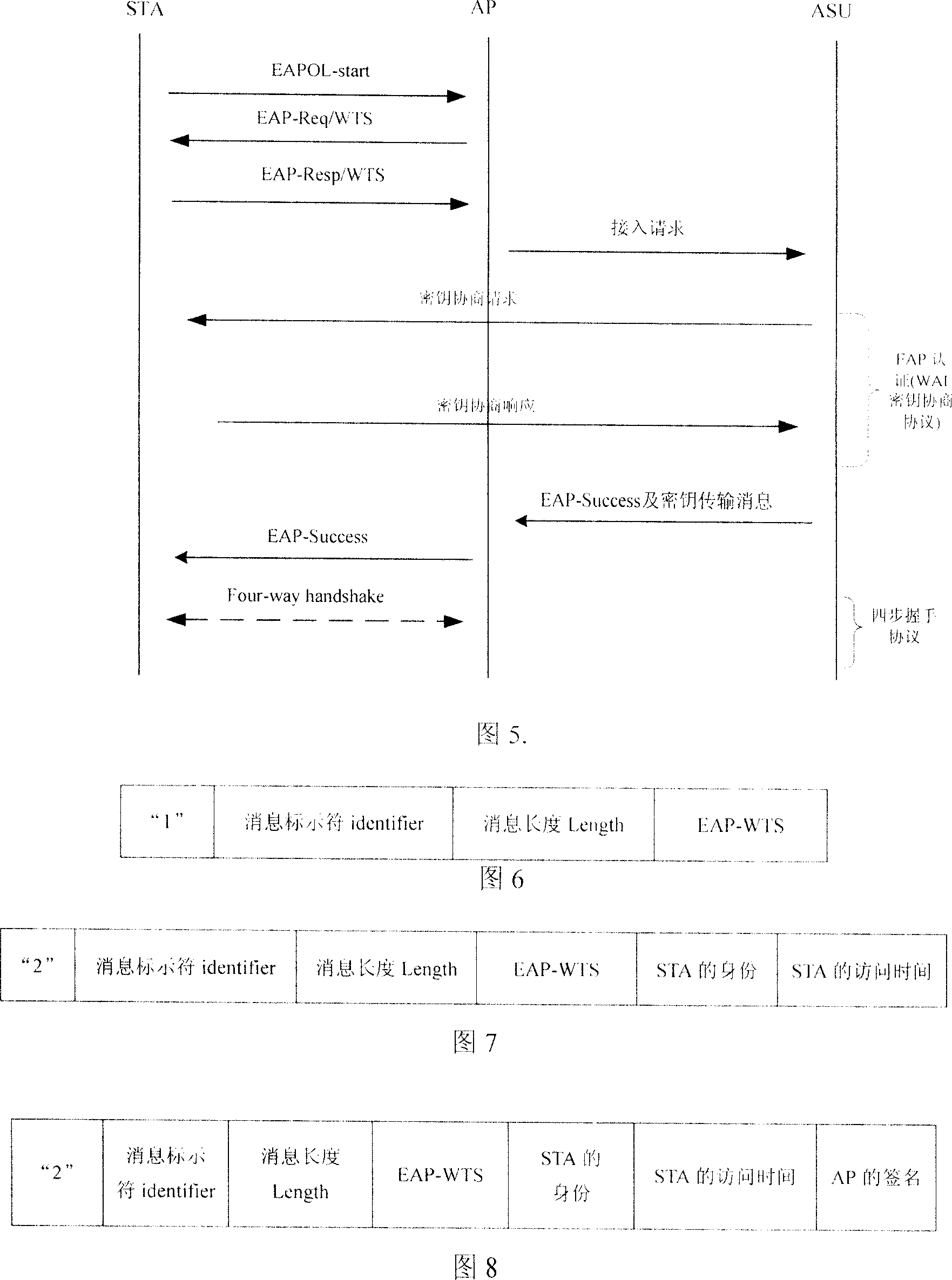Identity authentication method compatible 802.11i with WAPI
An identity authentication and identity technology, applied in the direction of user identity/authority verification, radio/induction link selection and arrangement, selection of devices, etc., can solve the problems of incompatibility between 802.11i and WAPI, and achieve the effect of reducing changes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
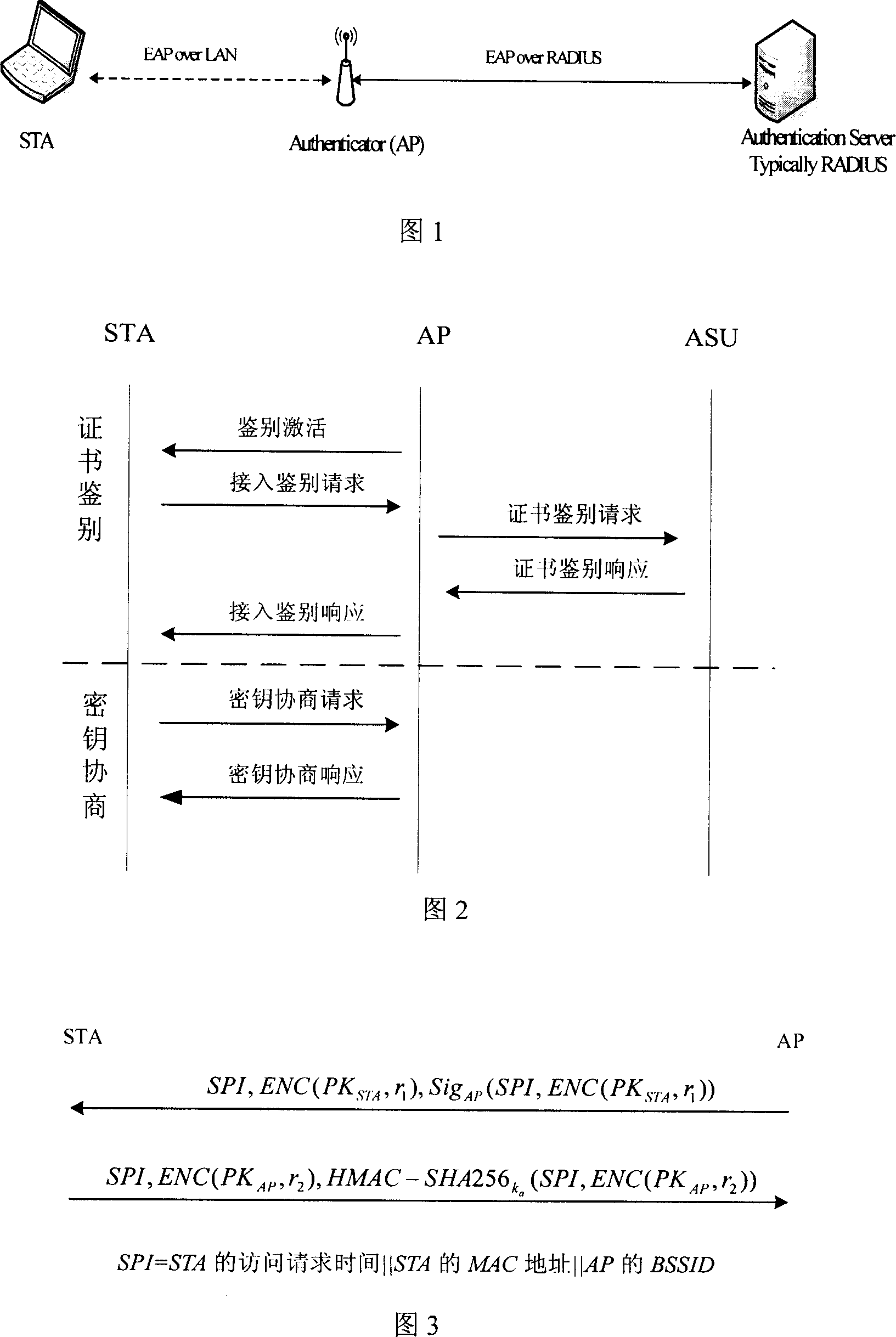
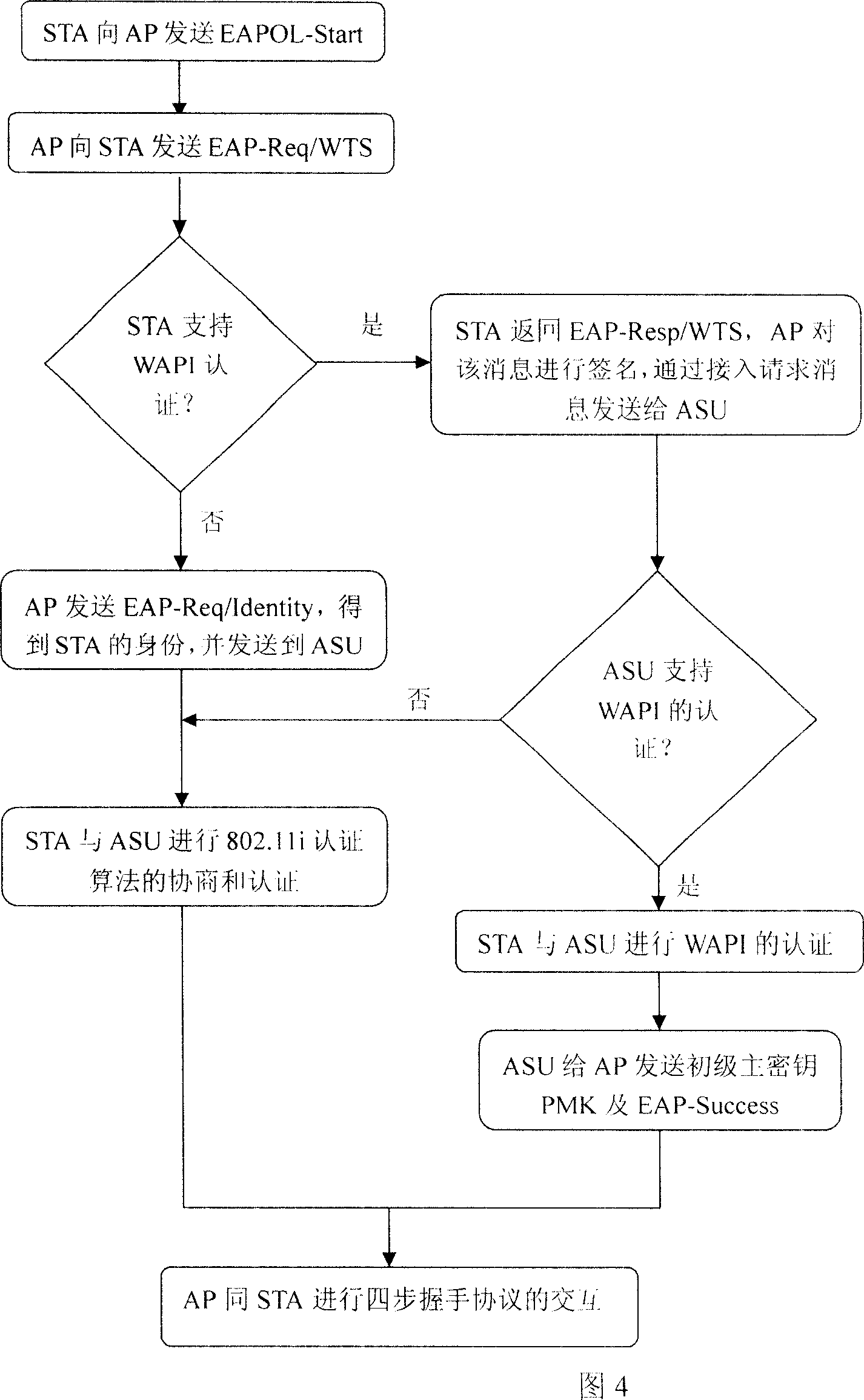
[0063] The following is a detailed description of the method of the present invention in conjunction with the flow chart 4 of compatible scheme execution and the protocol interaction process 5 of executing WAPI:
[0064] 1. The mobile station STA sends an EAP start message EAPOL-Start to the access point AP.
[0065] This message indicates that the mobile station STA requests EAP identity authentication, and its specific message format adopts the definition of EAPOL-Start in 802.11i.
[0066] 2. The access point AP sends a timestamp request message EAP-Req / WTS to the mobile station STA.
[0067] Through the time stamp request message EAP-Req / WTS, the access point AP requests the mobile station STA to send its identity and current access time. Since there is no such message type in the current EAP message, a new message type type: WAPI-WTS needs to be added to the EAP message. The format of this message is shown in Figure 6.
[0068] The message format shown in Fig. 6 is def...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com