Electric lock capable of proofing whether himself had been unlocked and implementation method therefor
An electronic lock and provable technology, applied in the field of electronic locks, can solve the problems of unprovable cracking and electronic locks that cannot prove cracking, etc., so as to prevent fraud incidents and improve the anti-cracking performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
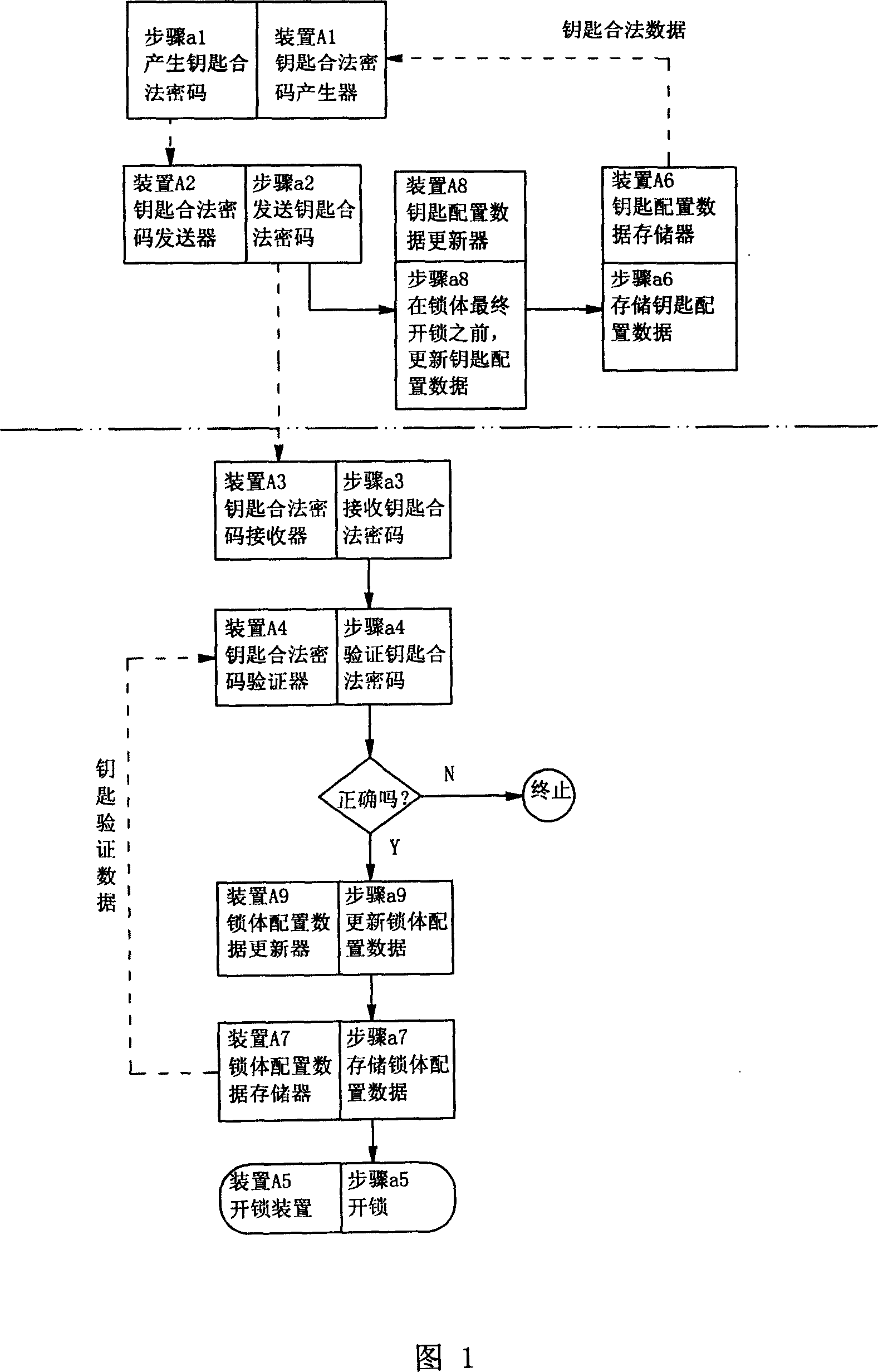
[0043]The implementation of this embodiment is the same as that described in the previous section, and will be described in detail below with reference to FIG. 1 . When unlocking, the legal key code generator A1 of the key uses the legal data of the key stored in the key configuration data memory A6 in advance as a calculation parameter, and calculates the legal code of the key with a certain algorithm, and then the legal code of the key is sent by the legal key code transmitter A2. Send to the lock body. Afterwards, the key configuration data updater A8 of key updates the legal data of the key in the key configuration data memory A6 before the lock body performs the final unlocking action, and prepares for unlocking next time. At the same time, after the key legal password receiver A3 of the lock body receives the key legal password, the key legal password verifier A4 of the lock body verifies the key legal password. The basis of verification is to use the key verification d...
Embodiment 2
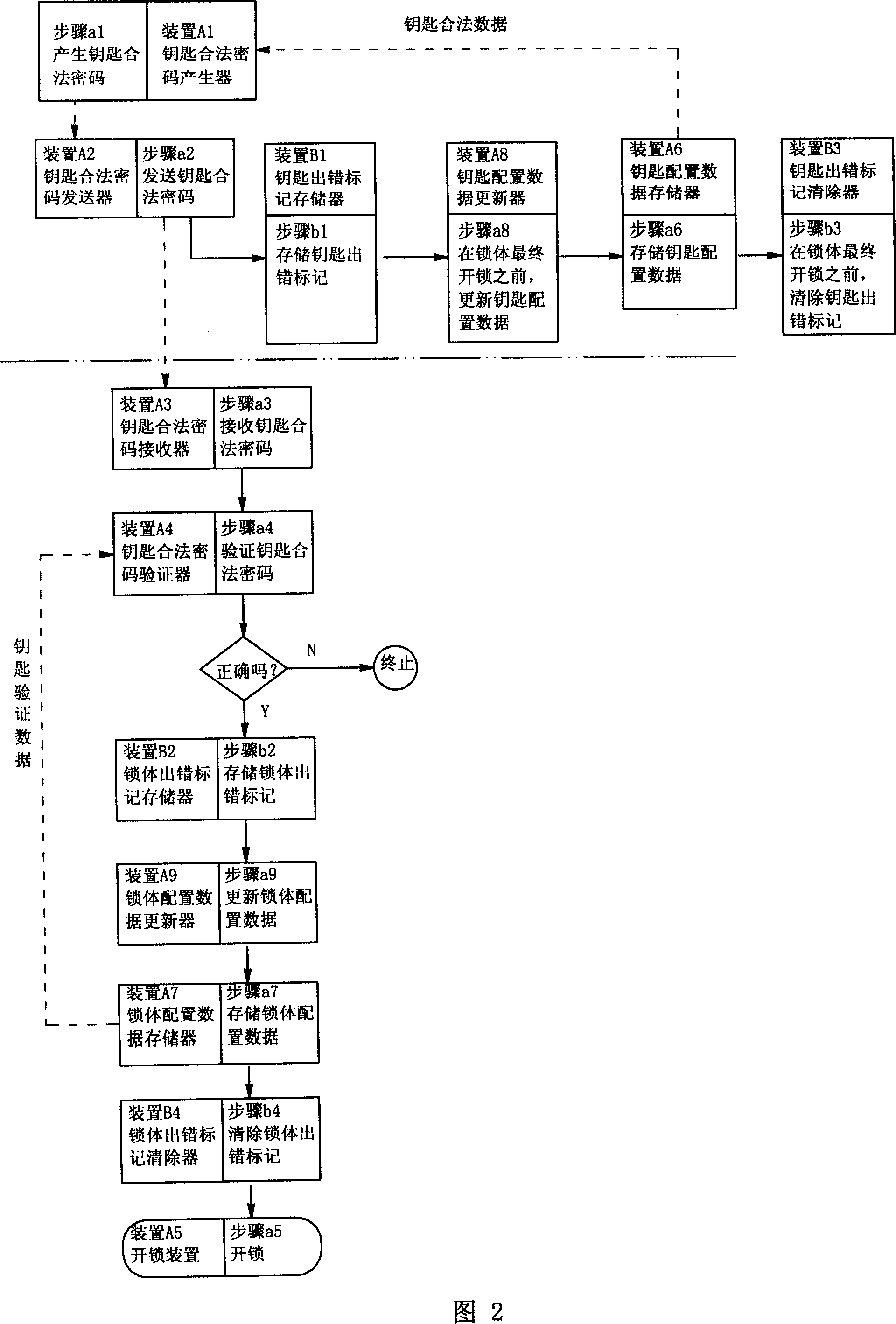
[0045] This embodiment is proposed to improve Embodiment 1. In embodiment 1, assuming that in the key configuration data update step a8 shown in Figure 1, or in the lock body configuration data update step a9, an abnormal power failure occurs and the update process cannot be completed normally, so the key configuration data cannot be guaranteed. The legal data of the key stored in the memory A6 maintains a matching relationship with the key verification data stored in the lock body configuration data memory A7, so that the key cannot be unlocked. This embodiment is improved on the basis of Embodiment 1 in order to distinguish whether it is due to abnormal power failure, or the key cannot unlock the lock because the lock body has been cracked. Referring to Fig. 2, in the unlocking procedure of the key, before the key configuration data update step a8, the key error flag storage step b1 is added, and the key error flag storage B1 is correspondingly added in the key, and the key ...
Embodiment 3
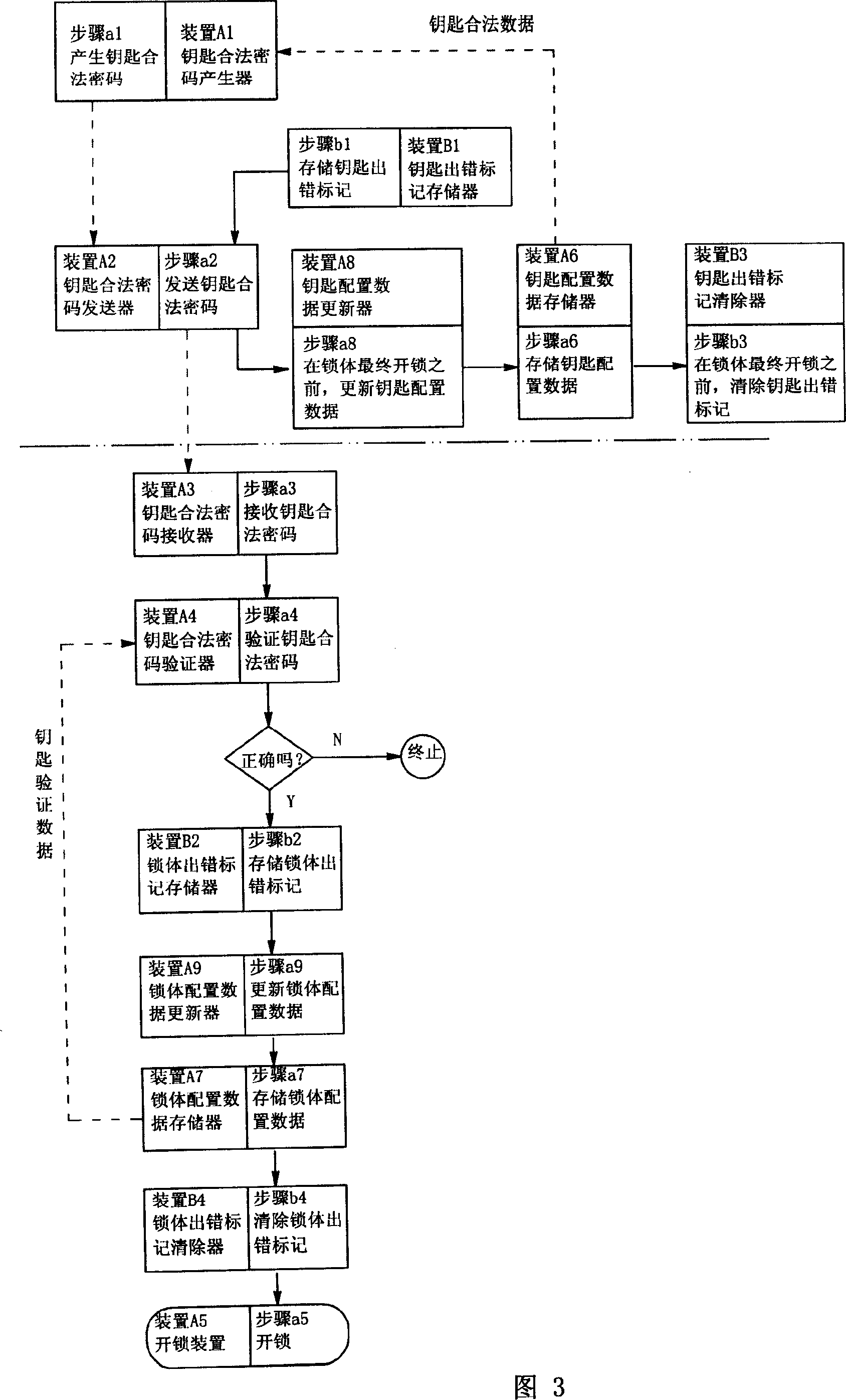
[0049] Although embodiment 2 has been further improved than embodiment 1, some loopholes still exist. Assuming that a user of an electronic lock with advanced technology wants to defraud the manufacturer, the user is likely to carry out the fraud in this way: first create a fake lock body, and then use the real key to open the fake lock body, so that the real key goes through a complete cycle. Then according to the key unlocking program described in embodiment 2, the legal data of the key of the real key will be changed in step a8, and the key error mark will also be removed in step b3, and the real lock body does not have Participate in the opening process, that is, the key verification data of the real lock body has not changed and there is no error mark. When the manufacturer verifies whether the lock body has been cracked, the real key will not be able to open the real lock body, and the real key and the real lock body are both There is no error flag, and the manufacturer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com