A method for access terminal and operator binding
A technology for access terminals and operators, applied in network connection, data exchange through path configuration, digital transmission system, etc., to achieve the effect of simple implementation scheme and avoid vicious competition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] Embodiment 1: Identify the operator's domain name as an identifier
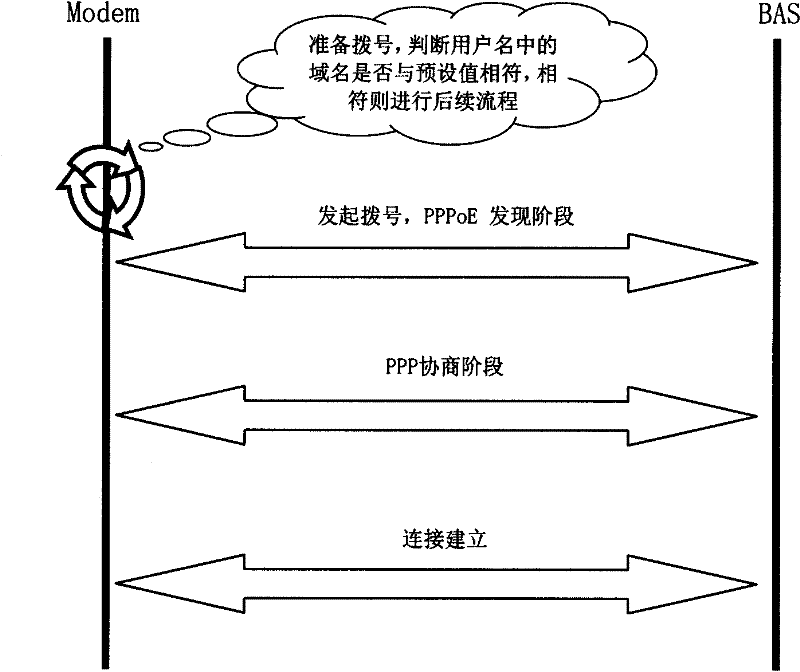
[0046] First of all, the operator pre-stores its domain name in its access terminal, which can be fixed in the code or written in flash in a certain way, and ordinary users cannot modify it.
[0047] During the PPPoE dial-up process, the Modem extracts the domain name field in the user name and compares it with the pre-stored operator domain name, and only allows dialing if the two are consistent.
[0048] In routing mode, the dial-up process is initiated by the Modem. The user name will be configured on the Modem, such as usernamexxx.xx. The Modem needs to obtain the user name dialing from the configuration. Some rules can be set in the program to extract the domain name after the characters are extracted from the user name. The Modem directly judges whether the extracted domain name is the same as the operator's preset domain name during the PPPoE dial-up process.
[0049] Such as figure 1 As shown...
Embodiment 2
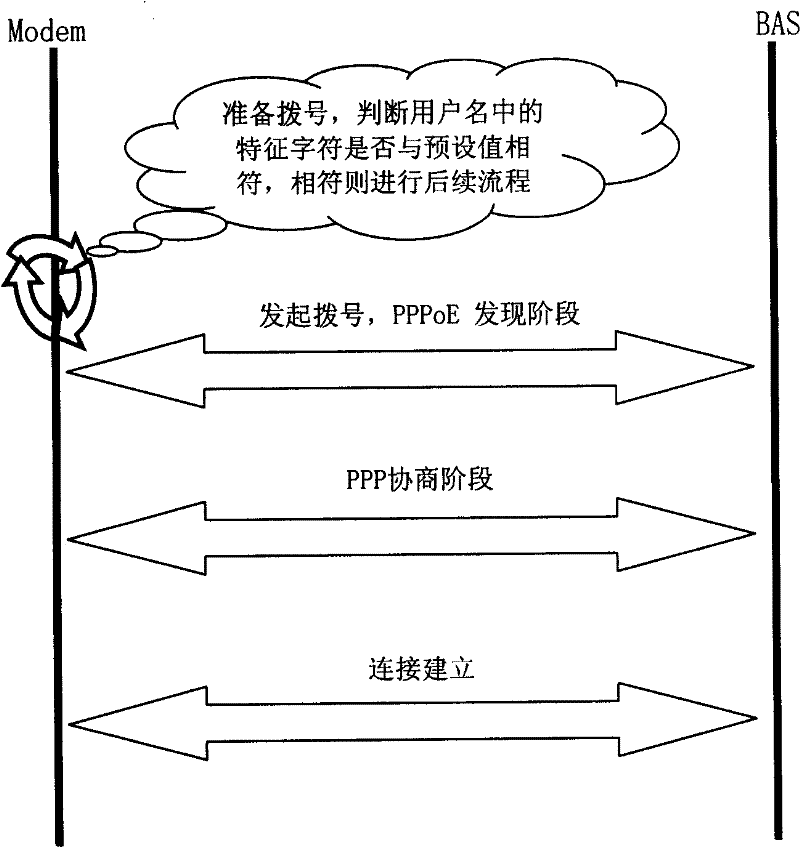
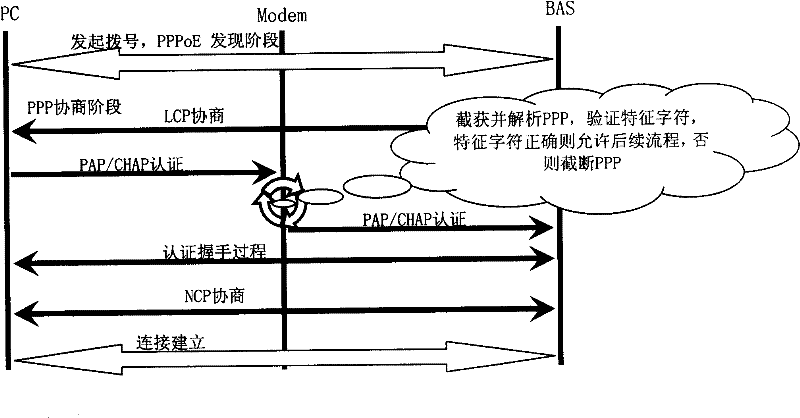
[0059] Embodiment 2: The operator superimposes its trademark or other representative character strings with the user name applied for by the user when issuing services, and the operator pre-stores the characteristic character as an identifier in its access terminal, and the user uses this When the access terminal accesses the network, the access terminal extracts the characteristic characters in the user name and compares them with the characteristic characters stored therein, and only when the two are consistent, the subsequent dialing process is allowed.
[0060] First of all, operators pre-store characteristic characters in their access terminals, which can be fixedly written in the code or written in flash in a certain way, and ordinary users cannot modify them.
[0061] The operator superimposes this characteristic character with the user name applied by the user when issuing services, such as username_XXX, where XXX is the characteristic character of the operator.
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com