State application blind identifying method
A blind identification and state technology, applied in the network field, can solve the problems of packet loss, lack of prior knowledge in new non-standard applications, loss of state synchronization tracking, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings.
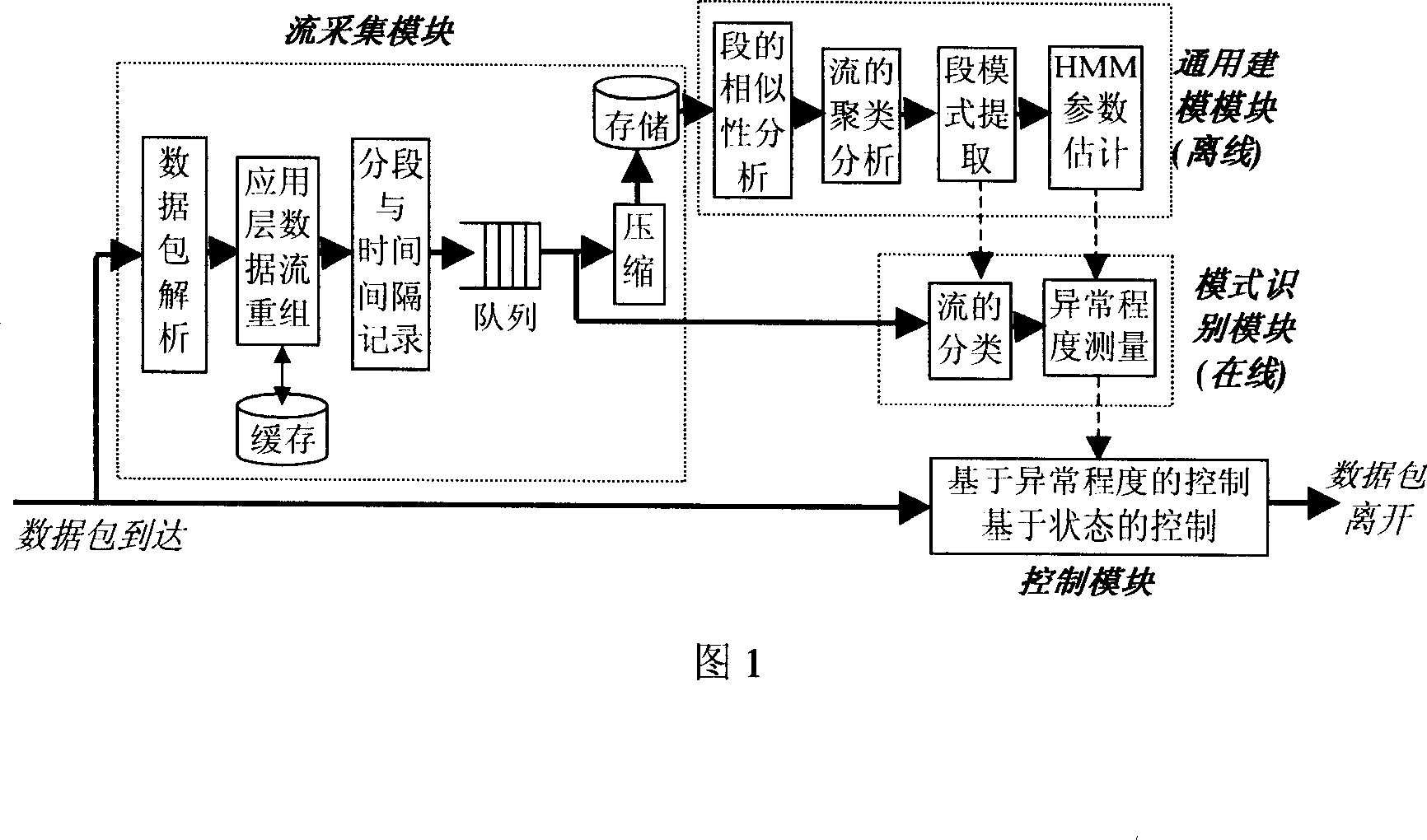
[0046] The system structure of the present invention is shown in Figure 1. Including: flow collection module, used to extract application layer data from data packets, and recombine application layer data flow; general modeling module, used to perform cluster analysis and modeling on collected application layer data flow samples, and provide model The identification module provides parameters; the pattern identification module is used to classify and measure the application layer data flow online, providing reference for the classification control of subsequent data packets; the control module is used to perform real-time classification control on the application layer data flow.
[0047] The stream acquisition module includes a data packet parsing sub-module, an application layer data stream recombination sub-module, a segmentation and time interval recording sub-modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com