Cipher key updating method of universal leading frame
An update method and general guidance technology, applied in key distribution, can solve the problem of inconsistent key identifiers, and achieve the effect of a simple and effective generation method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
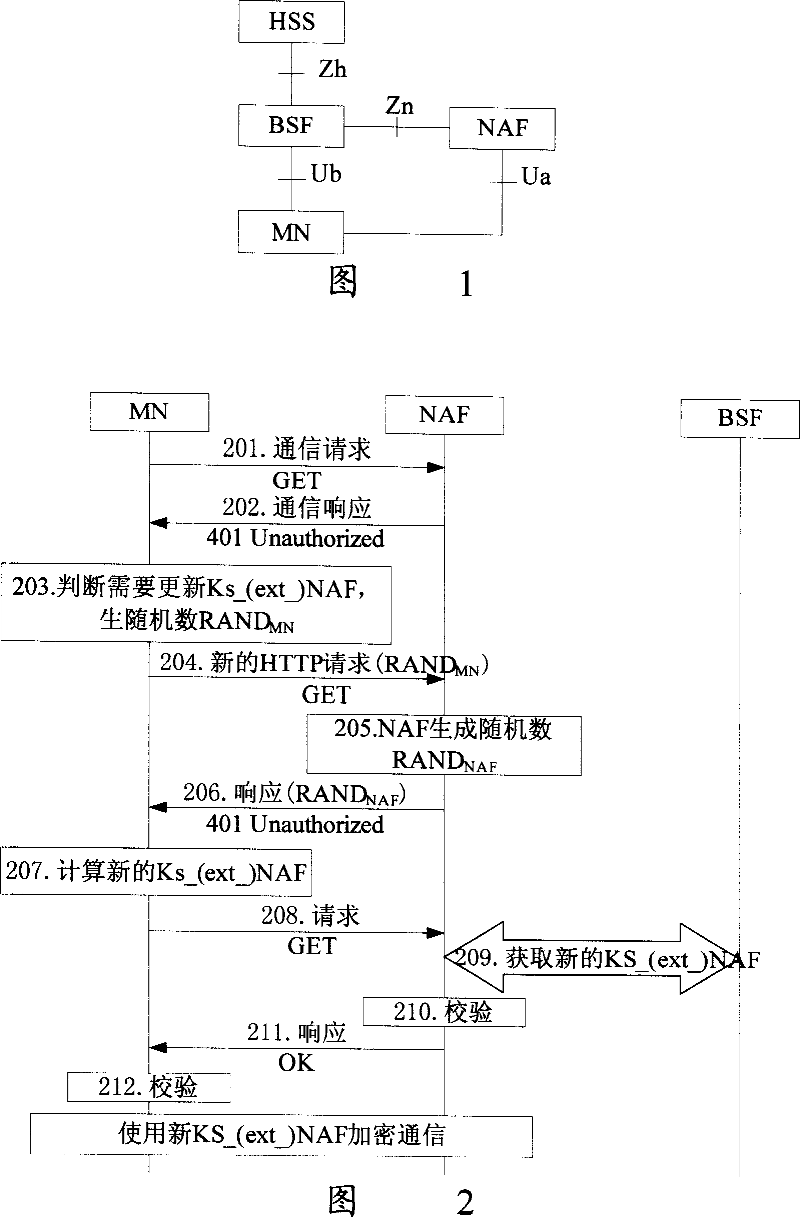
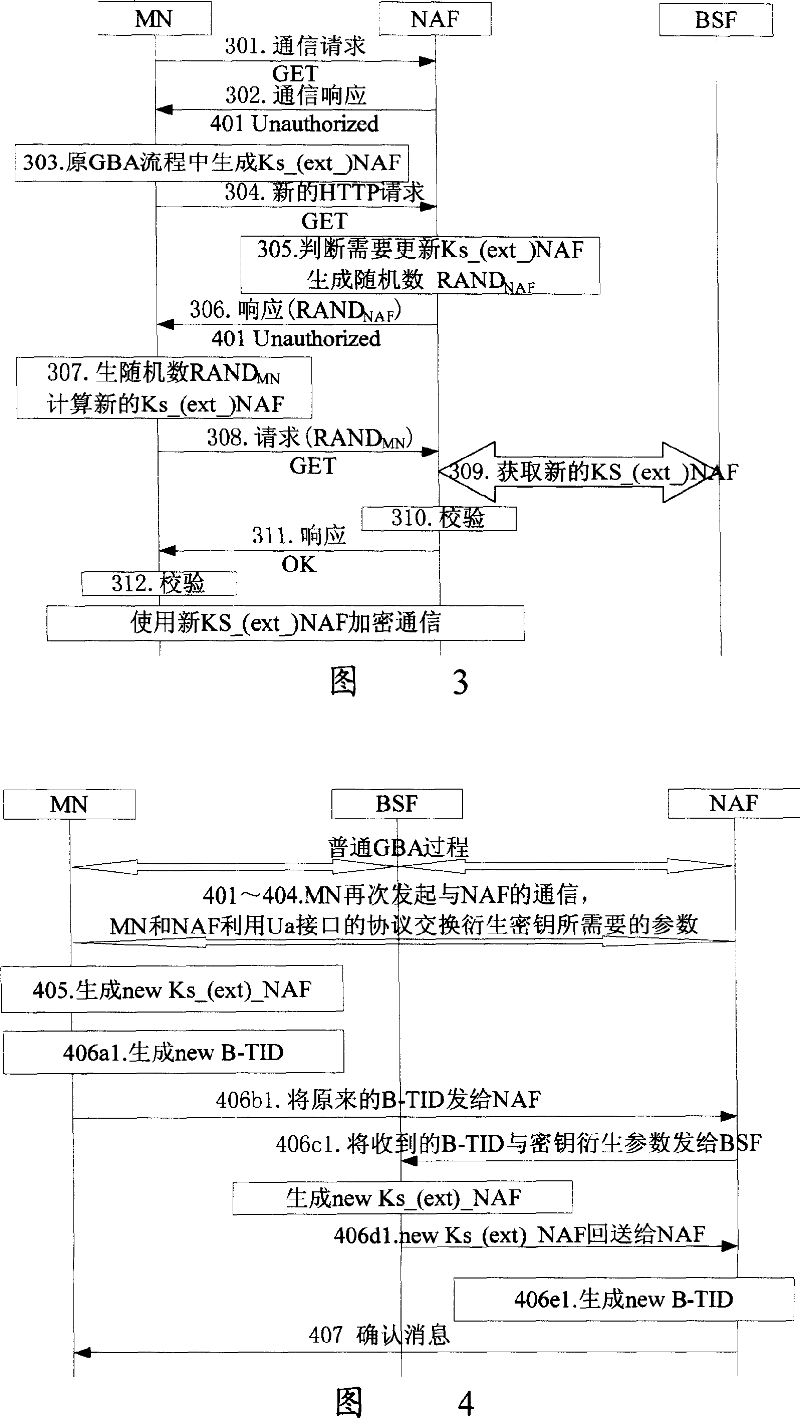
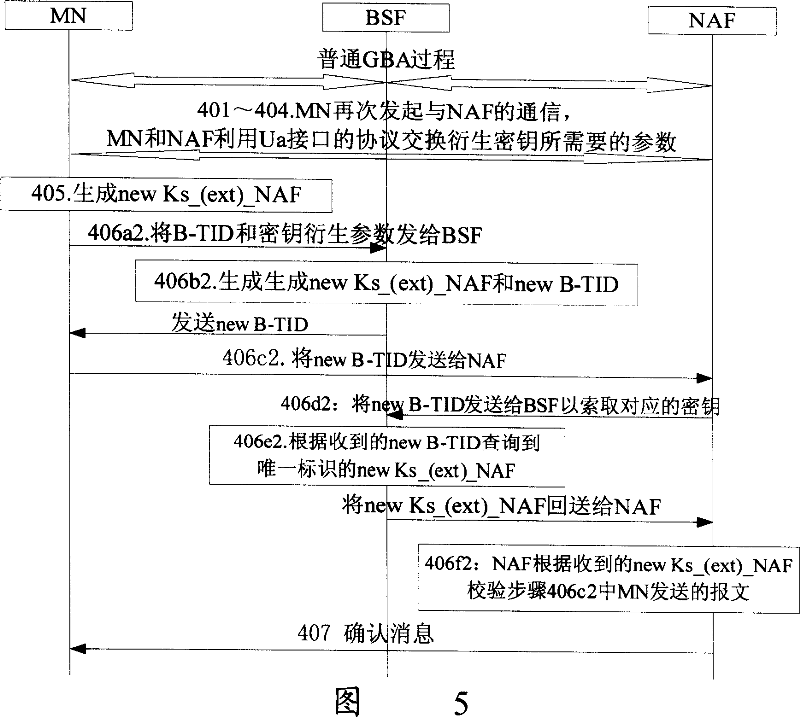
[0063] In the GBA specification, B-TID is generated by BSF. B-TID generation includes the following two forms, base64encode(AKA_Challenge)@BSF_servers_domain_name and base64encode(RAND)@BSF_servers_domain_name, where AKA_Challenge is a random number generated by BSF, and RAND is AKA Random number in the authentication vector generated by HSS in (Authentication and Key Agreement, authentication and key agreement). The above-mentioned first form is used for a flow based on CAVE (Cellular Authentication and Voice Encryption, cellular authentication and voice encryption protocol) or MN-AAA, and the second is used for a flow based on AKA. Although there are some differences, they are all composed of "base64 encoded random number" concatenated with "@" concatenated with "BSF domain name".
[0064] The generation method in the prior art of B-TID has been analyzed above. In the present invention, when generating a new Ks_(ext)_NAF, a new B-TID is generated at the same time, so that th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com