Service gateway and method for realizing message safe process
A security processing and service gateway technology, applied in the field of message security processing, can solve problems such as failure of grid service access points, insufficient computing and storage capabilities of mobile terminals, and difficulty in execution, so as to shorten the average response time, support security protection, The effect of improving service performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
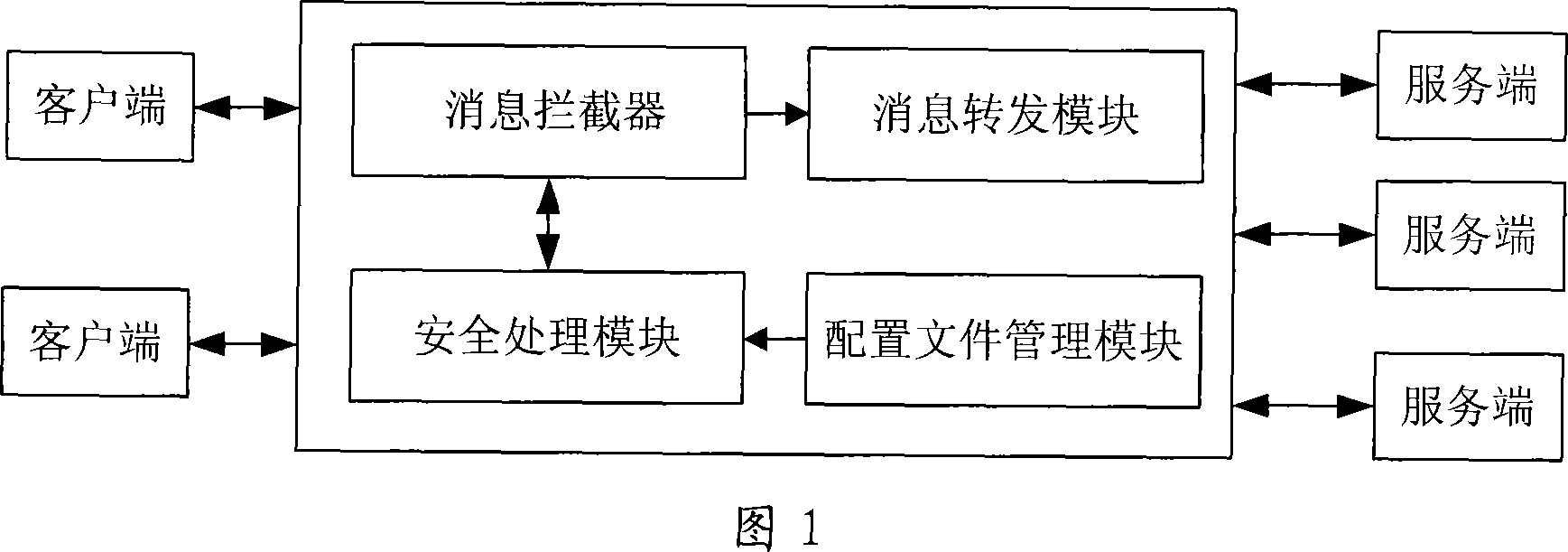
[0027] As shown in Figure 1, the service gateway includes a message interceptor, a security processing module, and a message forwarding module. The message interceptor is used to forward the intercepted user request message and / or service response message to the security processing module, and send the securely processed message returned by the security processing module to the message forwarding module; the message interceptor forwards the intercepted message Together with relevant information, it is encapsulated in the message context and sent to the security processing module. After the chain security processing is completed, the processing result is received, and according to the final processing result, it is decided whether to allow the service gateway to continue its normal message processing; the security processing module and the message The interceptor connection is used to securely process the message forwarded by the message interceptor, and return the securely proc...
Embodiment 2
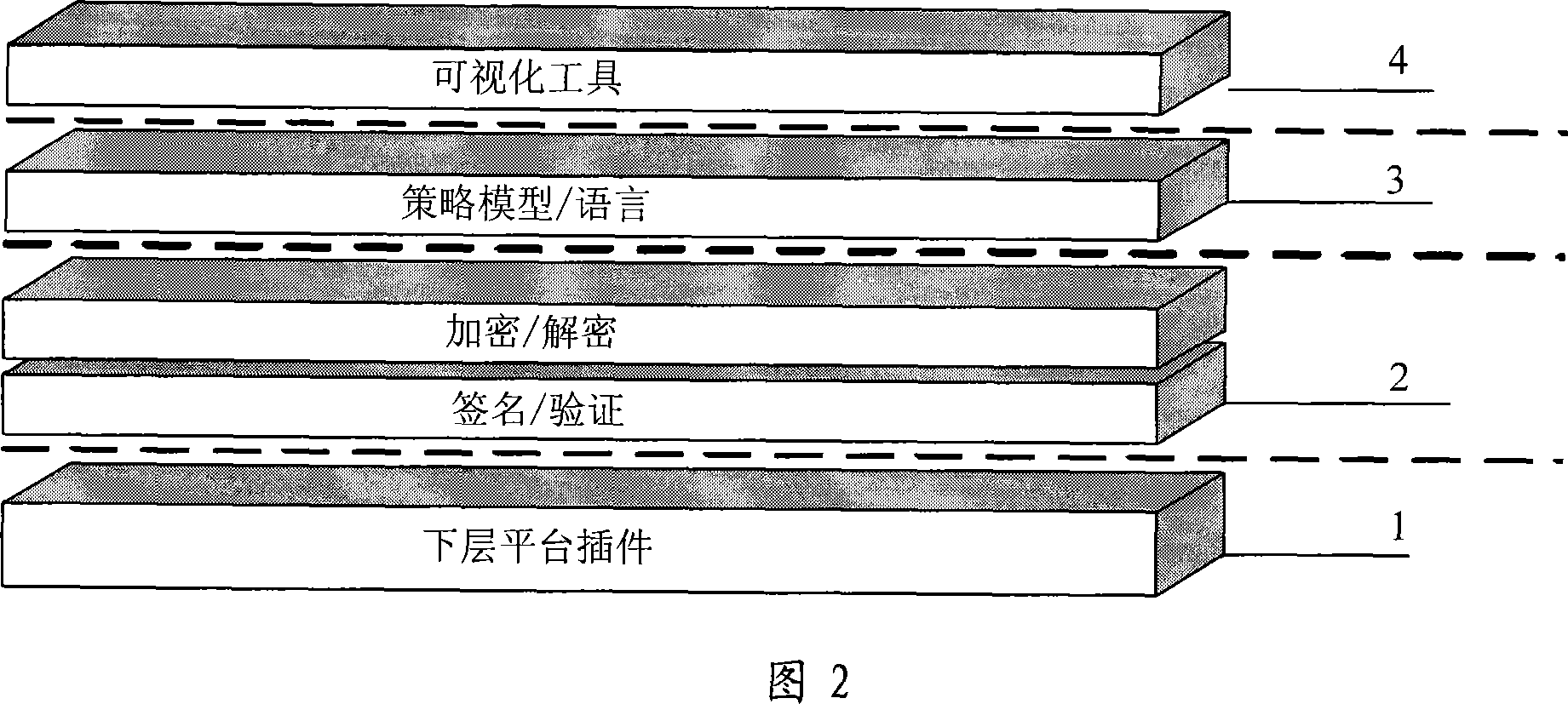
[0031] Based on Embodiment 1, the security processing module is divided into four levels from the technical architecture level, which are respectively from bottom to top: plug-in layer 1, control layer 2, policy layer 3 and management layer 4, as shown in FIG. 2 .
[0032] The responsibilities of each layer are as follows:
[0033] 1. Plug-in layer, where plug-ins are placed in the service gateway to intercept user requests and service response messages, and realize security control of service access.
[0034] 2. The control layer implements specific security control. The security control supported by the security processing module is mainly communication security. Since the security requirements of the application are diverse, the security processing module adopts an open and configurable chain structure to provide further flexibility in the organization of the security module at runtime.
[0035] 3. Policy layer, customize various communication security policies according ...
Embodiment 3
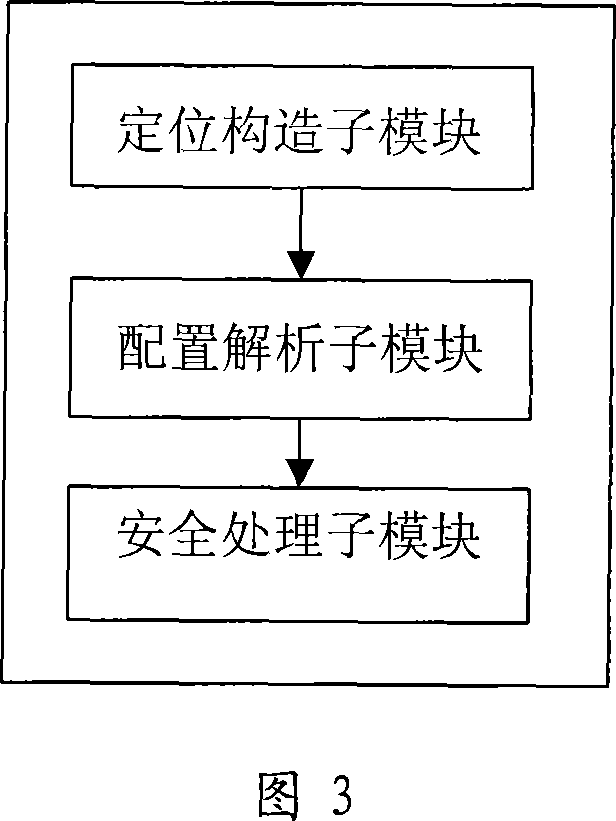
[0040] Based on the second embodiment, the SOAP specification stipulates how to sign the message. Signed arbitrary digital content is called a data object. The signature result of the data object plus the digital signature information is stored in the document in the form of an extensible markup language (eXtensible Markup Language; hereinafter referred to as: XML) element, which is called a signature element. The signature element is represented by the XML element "Signature". The SOAP specification also specifies how to encrypt messages. The encrypted data content is also referred to as a data object. The encrypted result and encrypted information of the encrypted data object are stored in the document in the form of XML elements, which are called encrypted elements. If an ordinary data object is encrypted, the encrypted element is "EncryptedData", and if the key is encrypted, the encrypted element is "EncryptedData". EncryptedKey". Referring to the relevant provisions o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com