Method and system for monitoring suspicious user of rubbish SMS
A technology of spam short message and monitoring system, applied in the field of short message system, can solve the problem of single strategy for capturing suspicious users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0028] For the convenience of description, first define a few nouns:
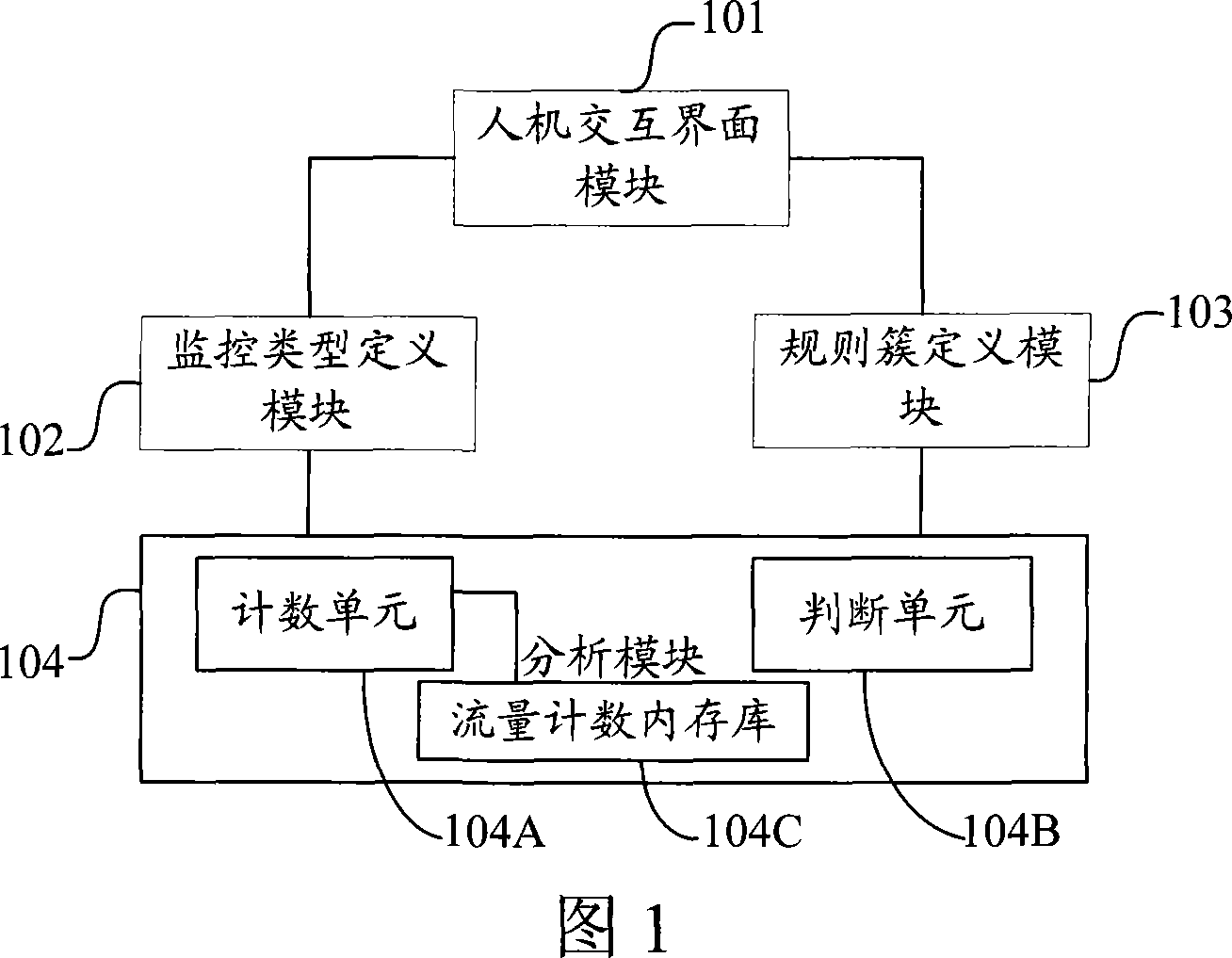
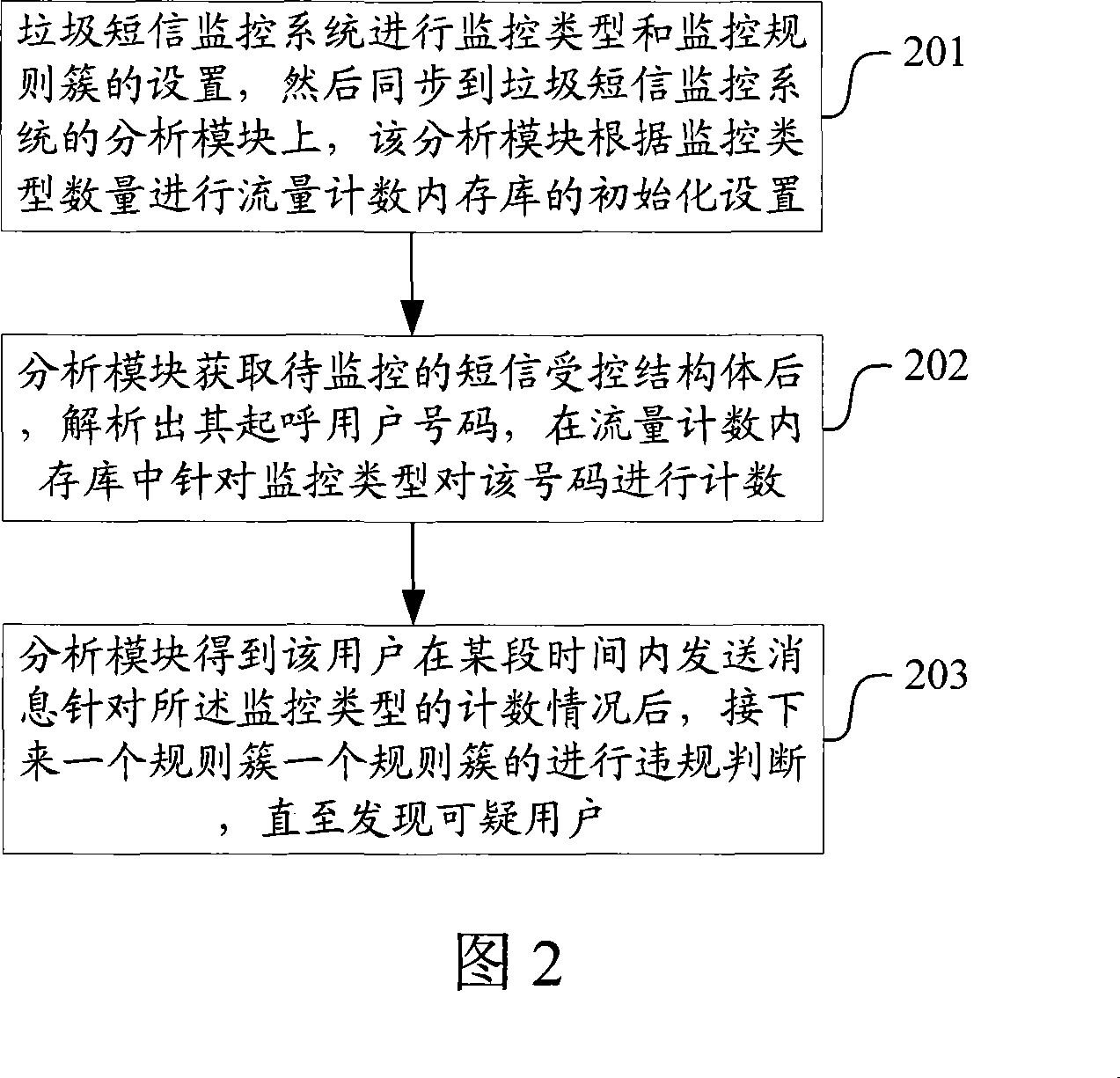
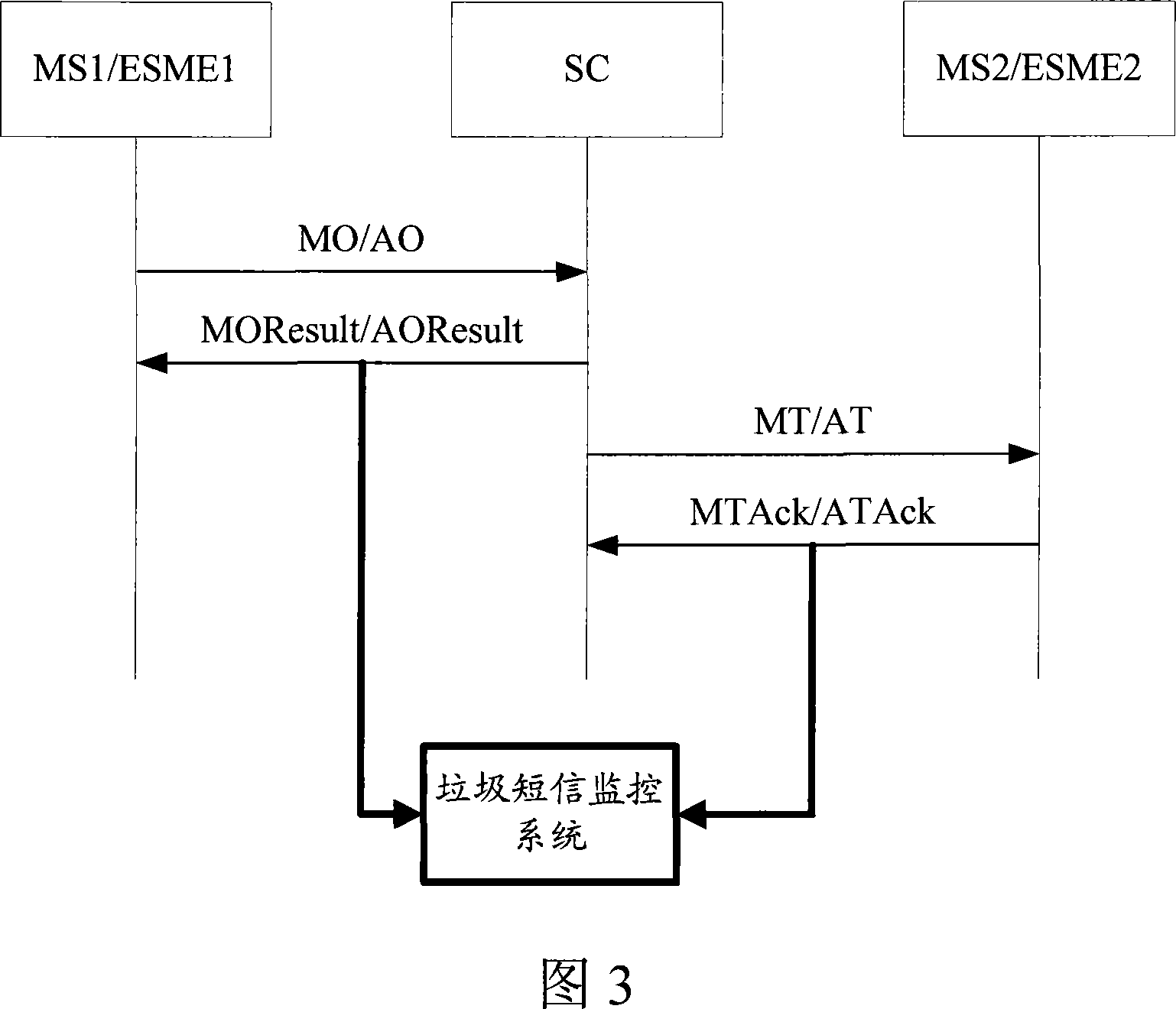
[0029] 1) Monitoring type: one of the necessary attributes in each rule, indicating which type the rule is based on, and the monitoring type is divided into two categories: initial call and final call, respectively for initial call response and final call The reason for the success or failure of the call response.
[0030] 2) Monitoring by frequency: monitor the amount of messages per unit time, which is directly obtained through the count value of a certain monitoring type.
[0031] 3) Monitor by ratio: monitor a certain ratio (for example, call success rate), which is obtained by dividing the count values of two monitoring types.
[0032] 4) Rule cluster: a set of rules with "and" relationship.
[0033] 5) First rule: the initial rule of a rule cluster.
[0034] 6)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com