Method and system for P-CSCF to identify forbidden calling subscriber
A P-CSCF, calling user technology, which is applied in the field of proxy call session control function entity identification and prohibition of calling users, can solve the problems of refusal to logout, unable to prohibit calls, unable to identify the public identity of barred, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
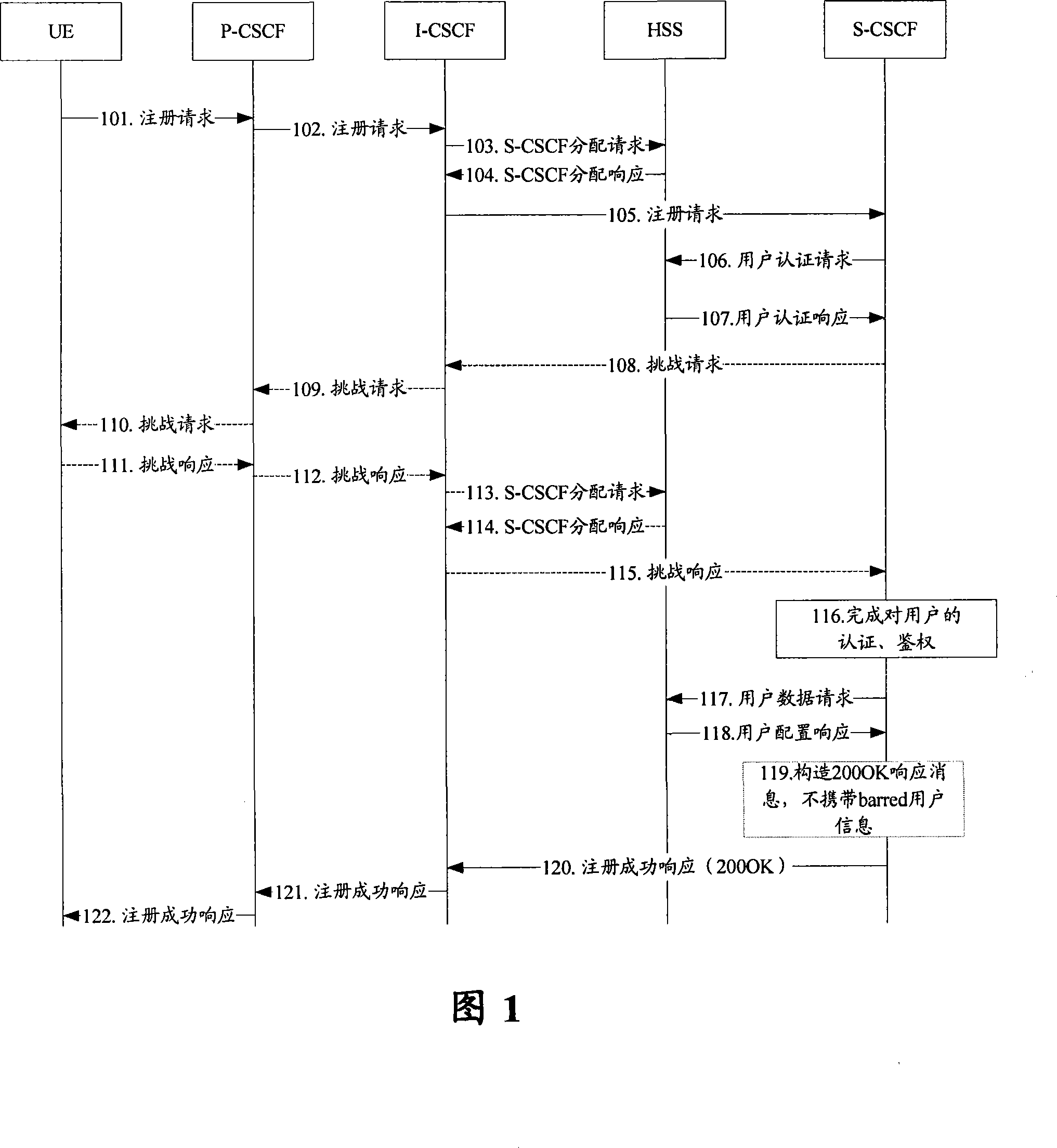
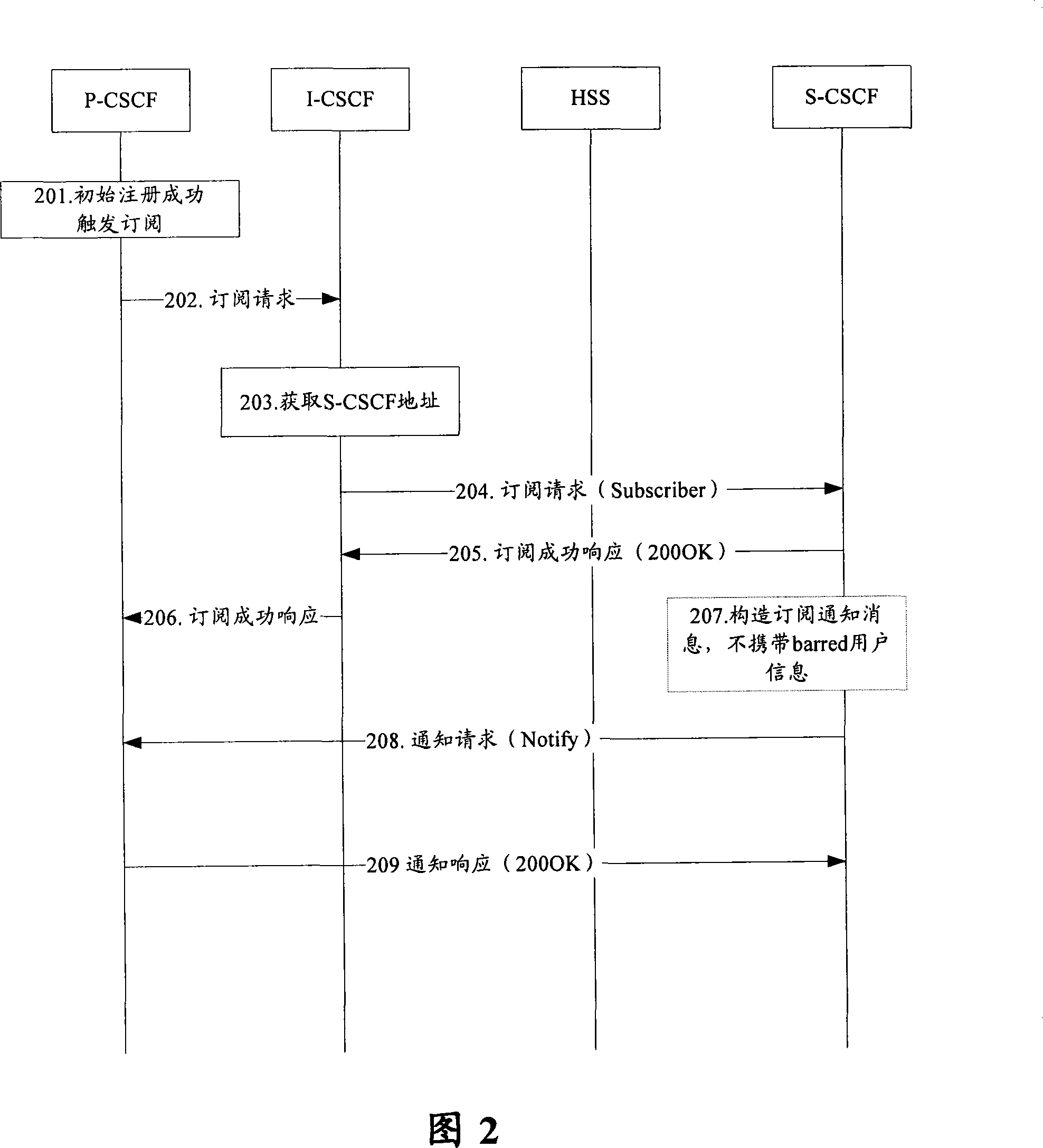
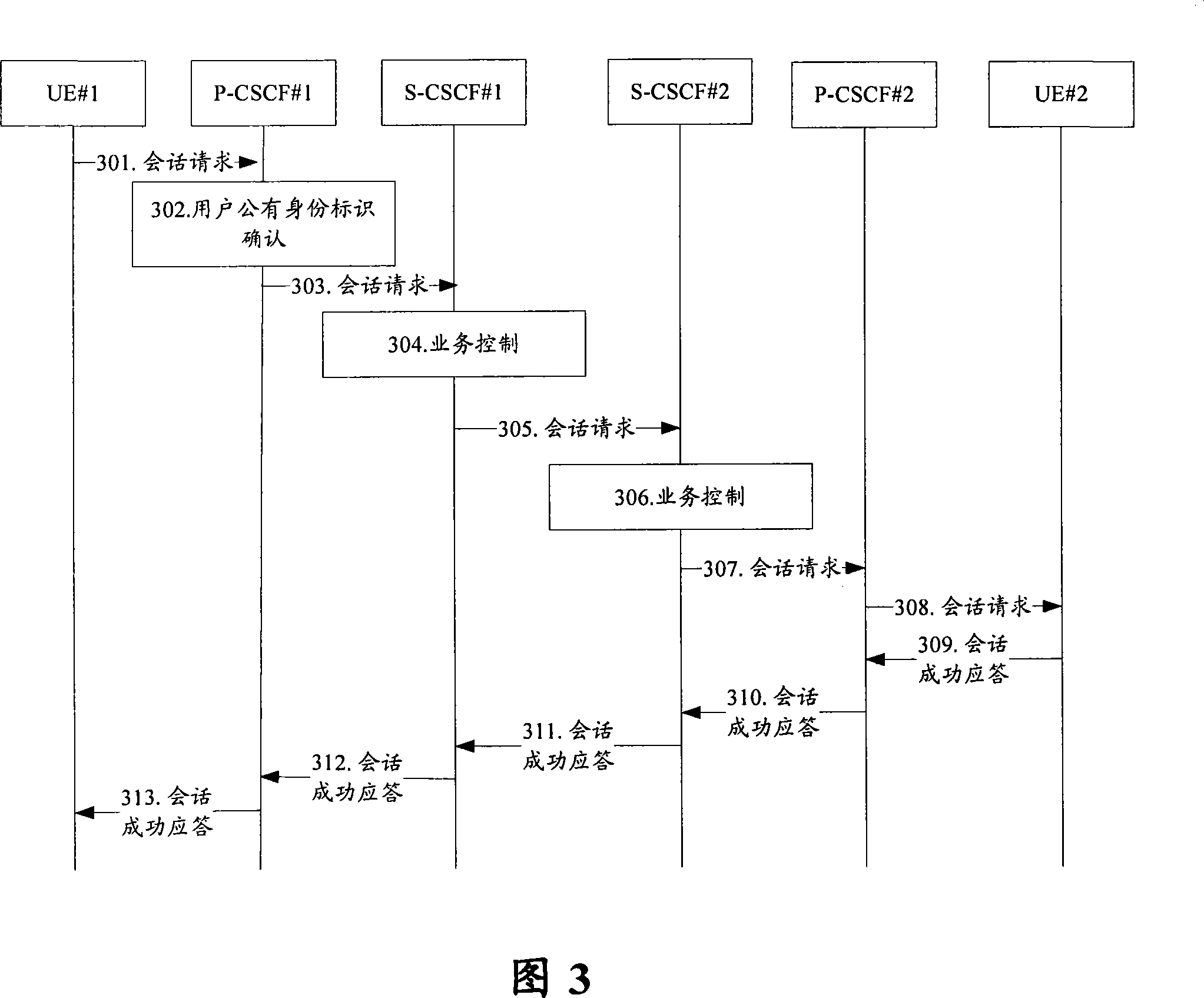
[0063] In related technologies, the P-CSCF cannot accurately perceive whether the user information is barred, and the S-CSCF needs to inform the P-CSCF through various mechanisms. However, in the embodiment of the present invention, the S-CSCF carries additional indications in the successful registration response Bring the information to the P-CSCF to inform the barred user information. After receiving the barred user information, the P-CSCF saves it locally; after the registration is successful, the P-CSCF then subscribes the user. When the subsequent user information is modified after the PPR occurs in the HSS When the user is barred, the S-CSCF constructs a subscr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com