MAC secure network communication method and network device
A technology of network equipment and communication methods, which is applied in secure communication devices, data exchange networks, digital transmission systems, etc., can solve the problems of terminal A and terminal B being unable to communicate, communication is blocked, difficult, etc., so as to save network resource waste and speed up The effect of MAC communication speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
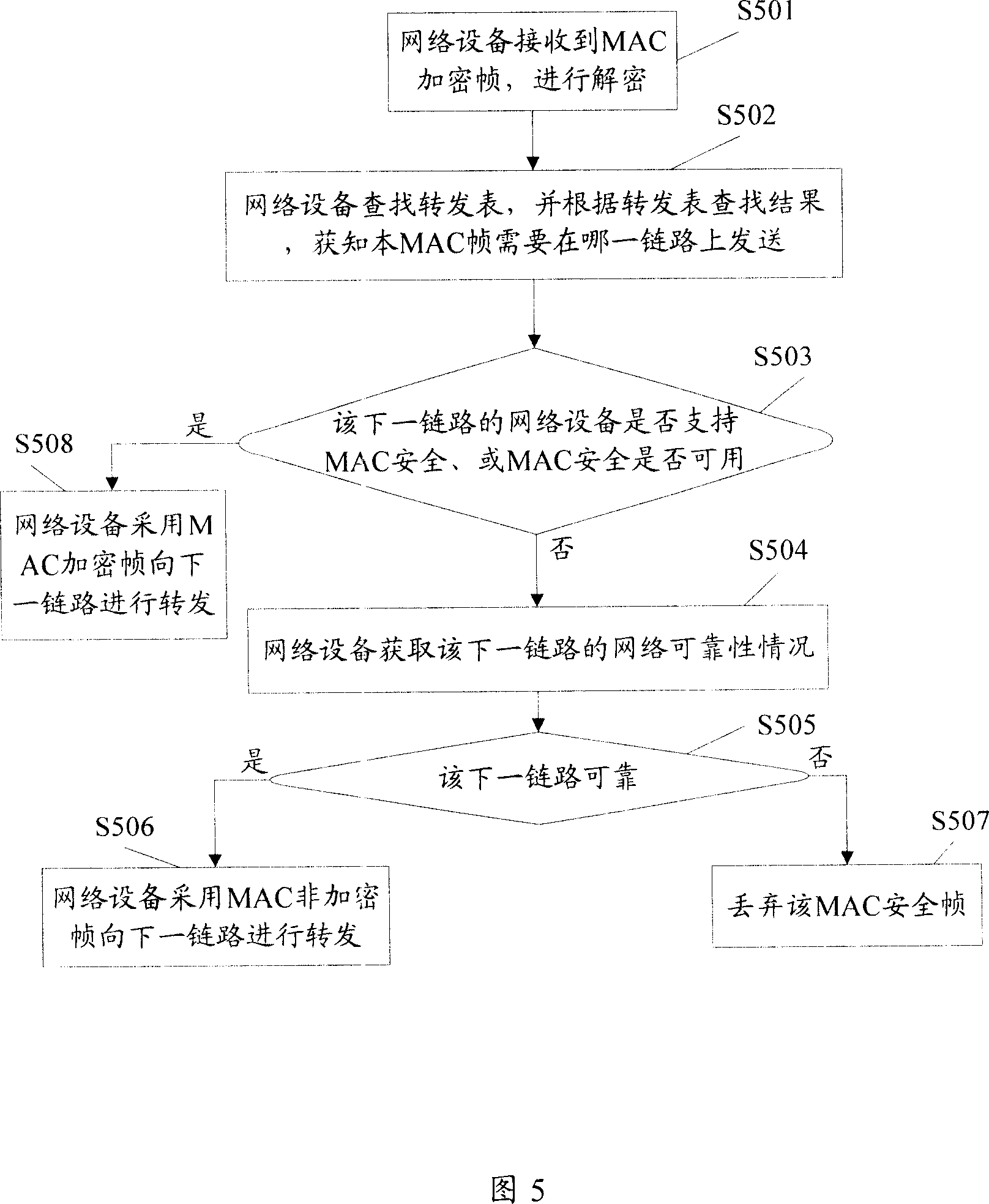
[0065] In this embodiment, according to the reliability of the link, it is decided whether to discard the MAC encrypted frame forwarded to the network device of the next link that does not support MAC security or the MAC security is not available, or continue to use non-encrypted frames for forwarding, Describe in detail.
[0066] Fig. 5 is the schematic flow chart of the method of this embodiment, as shown in the figure, this method comprises the following steps:
[0067] Step S501: The network device receives the MAC encrypted frame and decrypts it.
[0068] The network device receives the MAC encrypted frame sent to the network device by the previous link, and the network device transmits the MAC encrypted frame to the control port for decryption. The network device described in the present invention may be any network device in the communication network that supports MAC security and is available except the terminal, such as each network bridge in CBN, PBN, and PBBN.
[...
Embodiment 2
[0085] This embodiment is further aimed at the situation that the user carries the user's requirement for the MAC security confidentiality level in the MAC frame, whether to discard the MAC frame forwarded to the next link where the MAC security is unavailable at the network device decision, or continue to use non-encrypted frame forwarding When further combining the user's requirements on the MAC security confidentiality level, the confidentiality and communicability of the MAC communication are better coordinated and balanced, making the method of the present invention more practical.
[0086] First, how the user carries the information required by the user for the MAC security confidentiality level in the MAC encrypted frame is described.
[0087] According to IEEE 802.1ae, the composition of the MAC security label field of the MAC frame is shown in Table 1, wherein the MAC security label field contains an 8-bit Short Length (Short Length, called SL in IEEE802.1ae) field , ...
Embodiment 3
[0119] In this embodiment, when the network device receives a MAC non-encrypted frame, the processing of the MAC non-encrypted frame to realize network security communication is specifically described.
[0120] As shown in Figure 7, it is a schematic flow chart of the method of this embodiment. As shown in the figure, the present invention includes the following steps:
[0121] Step S701: The network device receives a MAC unencrypted frame.
[0122] The MAC unencrypted frame can be a MAC frame sent by a network device that supports MAC security and that MAC security is available; it can also be a MAC unencrypted frame sent by a network device that does not support MAC security or is unavailable MAC security, or MAC non-encrypted frames sent by network devices that are not available for MAC security, are more practical to implement MAC security communication on subsequent links.
[0123] Step S702: If the network device on the next link supports MAC security and MAC security i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com