Method and system for user authentication based on DHCP
A technology for user authentication and DHCP messages, applied in the field of user authentication based on DHCP, which can solve the problems of inability to realize security authentication, inability to meet the requirements of operability and management of communication networks, and inability to implement session authentication in IP-Session.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0068] In this embodiment, specifically, the association relationship between the subscriber identity identifier Subscriber-ID and the DHCP-Key (DHCP key) is statically established and configured in the entity on the network side, and then, the association relationship can be used to implement DHCP-based Authentication for users.
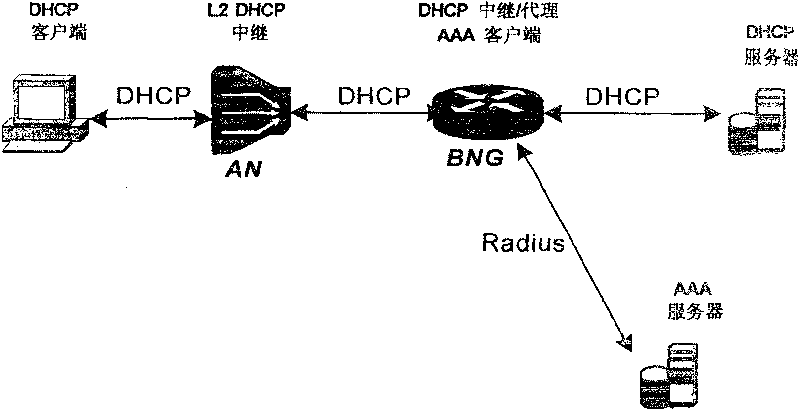
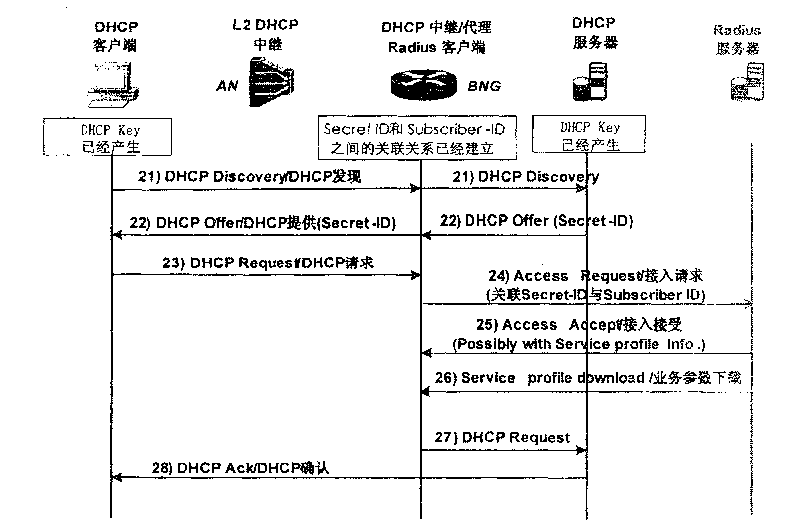
[0069] The specific implementation process of this embodiment is as follows: figure 2 shown, including:
[0070] Step 21: The DHCP client sends a DHCP discovery message to the DHCP Relay / Proxy, and the DHCP discovery message is sent to the DHCP server by the DHCP Relay / Proxy;
[0071] Step 22: After the DHCP server receives the DHCP discovery message, it will return a DHCP offer message to the DHCP Relay / Proxy, and the DHCP Relay / Proxy will continue to forward the message to the DHCP client;
[0072] In the DHCP provisioning message, it is necessary to transmit the DHCP-Key identification number Secret-ID (DHCP-Key identification) information, so...
Embodiment 2
[0079] In this embodiment, the association relationship between the subscriber identity identifier Subscriber-ID and the DHCP-Key is dynamically established and configured, that is, by dynamically establishing the association relationship in the DHCP process, after that, the association relationship established dynamically can be used The relationship realizes the association between the DHCP process and the authentication process for the user identity information of the logical user, that is, realizes the user identity authentication processing operation for the logical user based on DHCP.
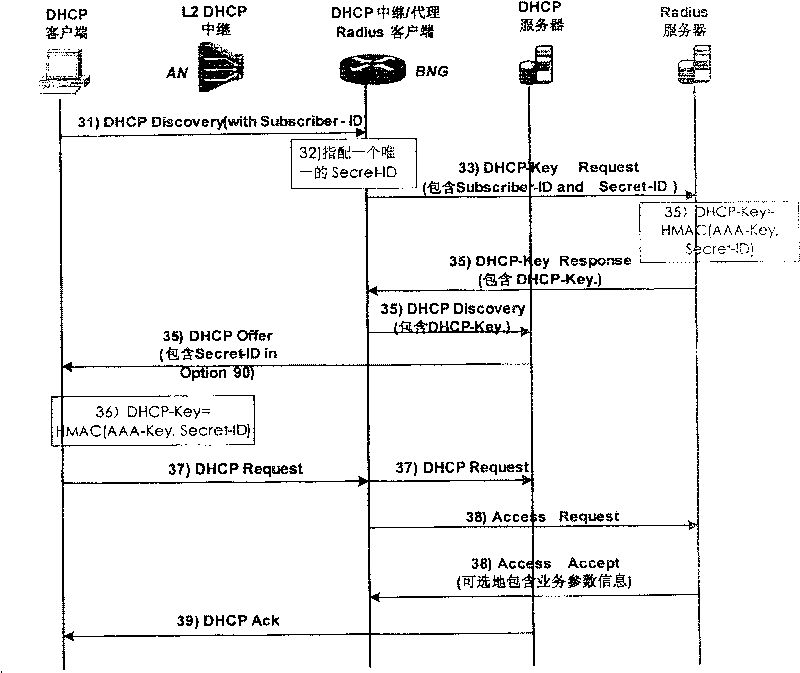
[0080] The specific realization scheme of this embodiment is as image 3 As shown, it specifically includes the following steps:
[0081] Step 31: The DHCP client sends a DHCP discovery message to the DHCP Relay / Proxy, and carries the Subscriber-ID information of the user;
[0082] Step 32: After the DHCP Relay / Proxy receives the DHCP discovery message, it obtains the Subscriber-ID infor...
Embodiment 3
[0096]In this embodiment, the DHCP message is specifically extended so that the encrypted user identity authentication information, such as a challenge word and a challenge word response for identity authentication, is transmitted through the DHCP message, so as to implement authentication processing for the user based on DHCP.
[0097] The specific implementation process of this embodiment is as follows: Figure 4 As shown, it specifically includes the following processing procedures:
[0098] Step 41: The DHCP client sends a DHCP discovery message to the DHCP Relay / Proxy, and the message carries the Subscriber-ID information of the user;
[0099] Step 42: The DHCP Relay / Proxy of BNG obtains the Subscriber-ID information of the user from the forwarded DHCP message, and forwards the DHCP message to the DHCP server;
[0100] Step 43: The authentication client in the BNG obtains the Subscriber-ID from the DHCP Relay / Proxy, and sends an access request to the authentication serve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com