Communication system and communication method of chaos safety information internet transmission
A technology of secure information and communication methods, which is applied in the field of communication systems for Internet transmission of chaotic security information, can solve problems such as potential information security risks, public and open information transmission security independence, etc., to ensure anti-attack capabilities and enhance information The effect of anti-theft ability and enhanced security independence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in further detail below with reference to the drawings and embodiments, but the embodiments of the present invention are not limited thereto.
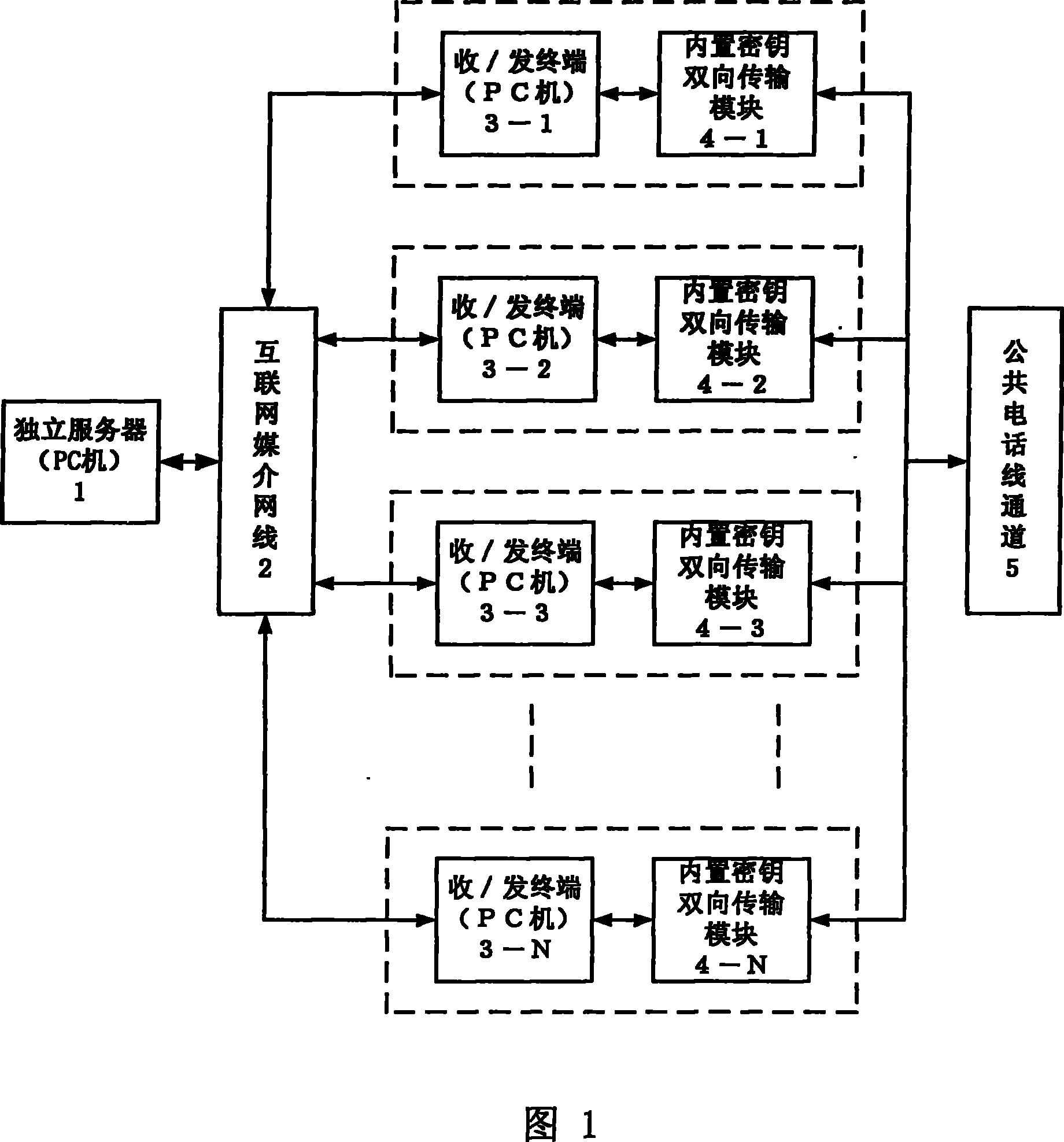
[0021] Such as figure 1 As shown, the communication system of a kind of chaos safety information Internet transmission described in the present invention comprises independent server 1, receiving / sending terminal (PC machine) 3-1, 3-2, 3-3 and to 3-N (N≤256, The same below), the built-in key two-way transmission module 4-1, 4-2, 4-3 and to 4-N jointly constitute, each receiving / sending terminal (PC machine) 3-1, 3-2, 3-3 and to 3 -N are electrically connected to the independent server 1 through the Internet media network cable 2, and are electrically connected to the respective built-in key bidirectional transmission modules 4-1, 4-2, 4-3 and 4-N through signal lines, each built-in The key bidirectional transmission modules 4-1, 4-2, 4-3 and 4-N are electrically connected to corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com