Fire wall/subnet penetration method based on intranet node forwarding technology
A technology of node forwarding and firewall, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of increasing wrong addressing, application program difficulty, host cannot be identified, etc., to achieve safe service and data transmission, reduce cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
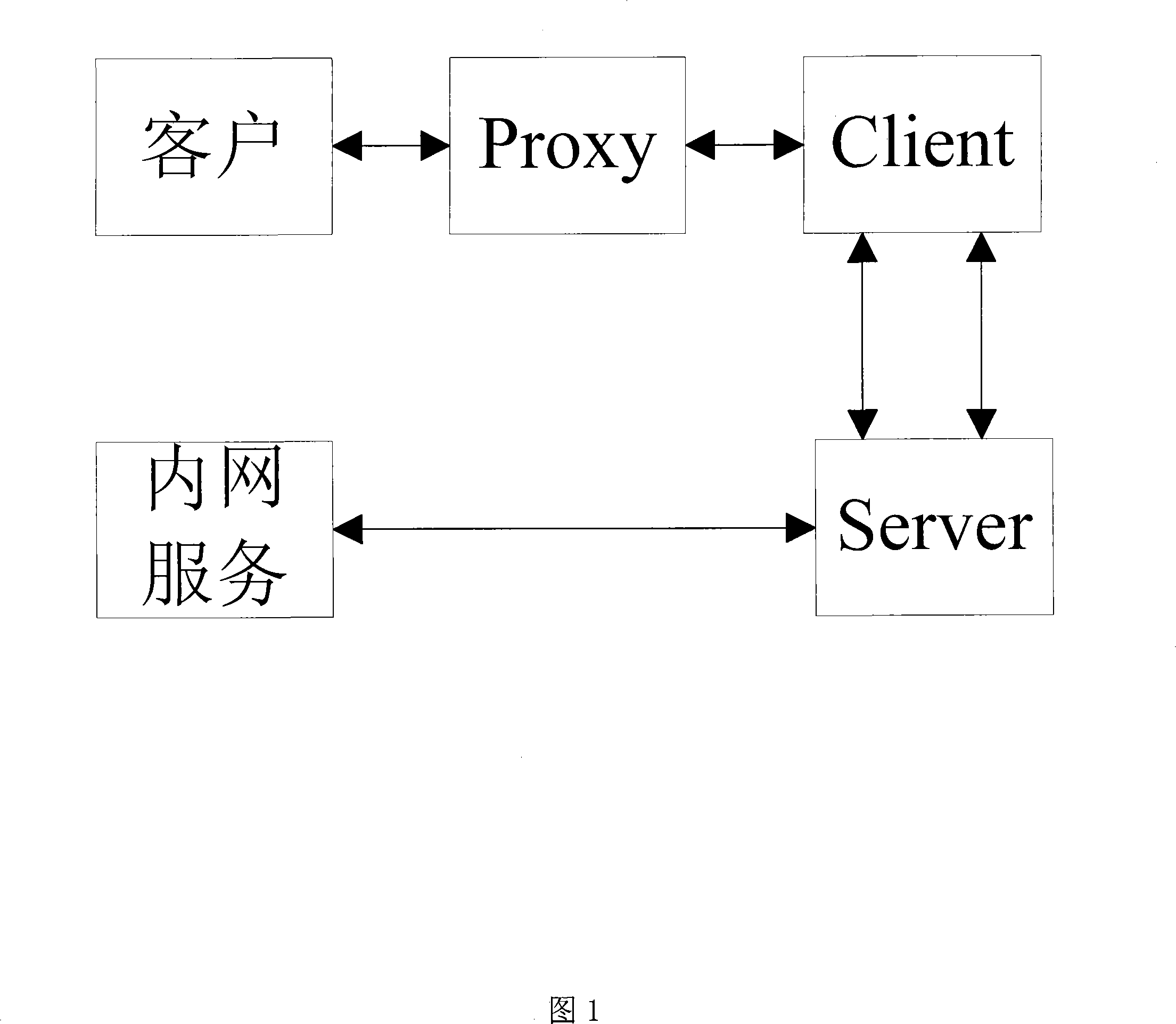
[0016] A kind of realization of the firewall / subnet penetration method of the present invention, comprising an embedded computer A as an intranet node data forwarding server, a computer C that opens HTTP (Hypertext Transfer Protocol) service in an intranet , and a user computer B that initiated the request in the external network. The Server module runs on the data forwarding server A, and the Client module and Proxy module run on the user computer B. Among them, the SBC 2410X (hereinafter referred to as ARM platform) embedded computer based on Samsung's ARM9 processor is used as the intranet data forwarding server A. In terms of software, the ARM platform uses the free embedded Arm-Linux operating system announced by Korea MIZI Company.
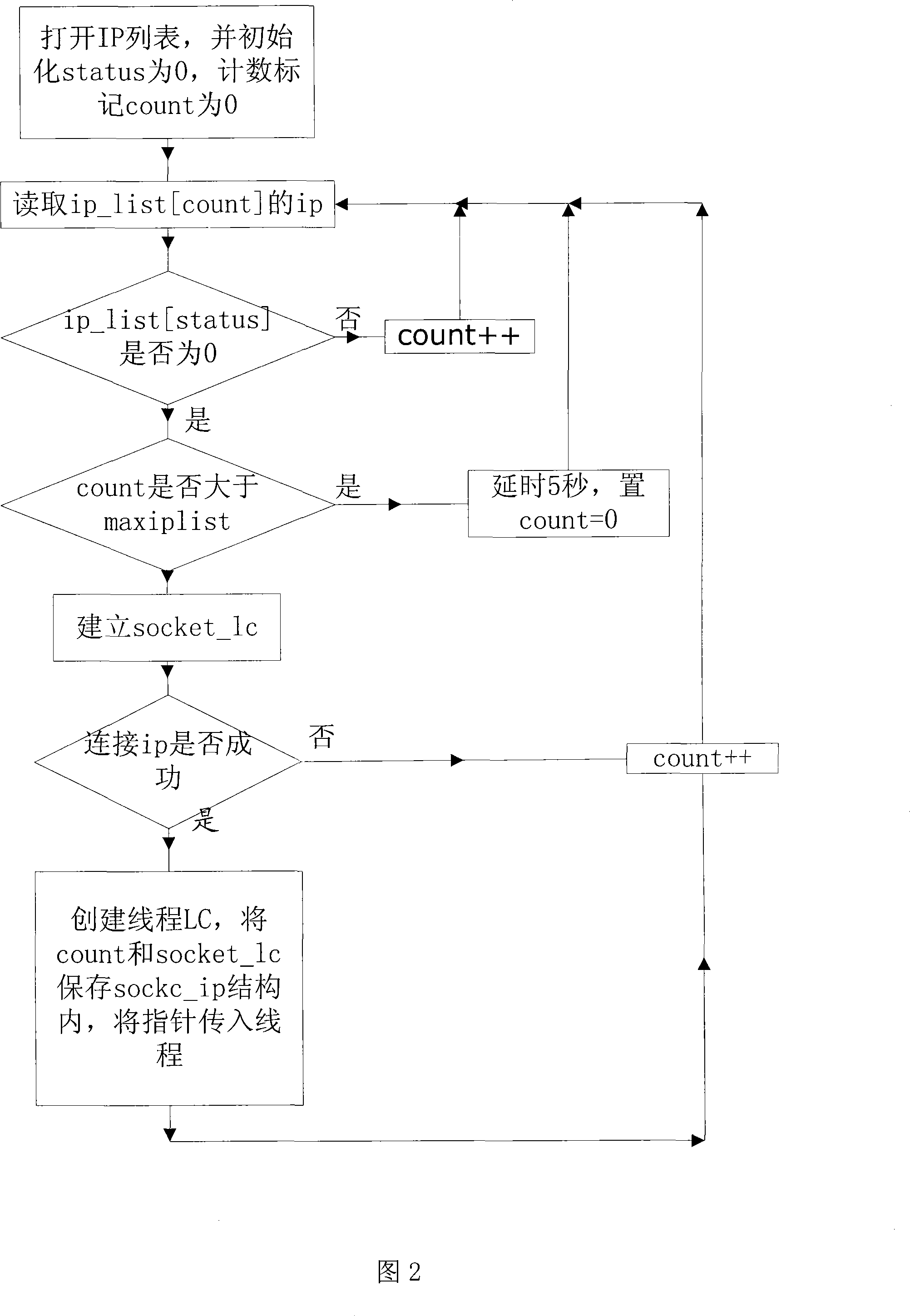
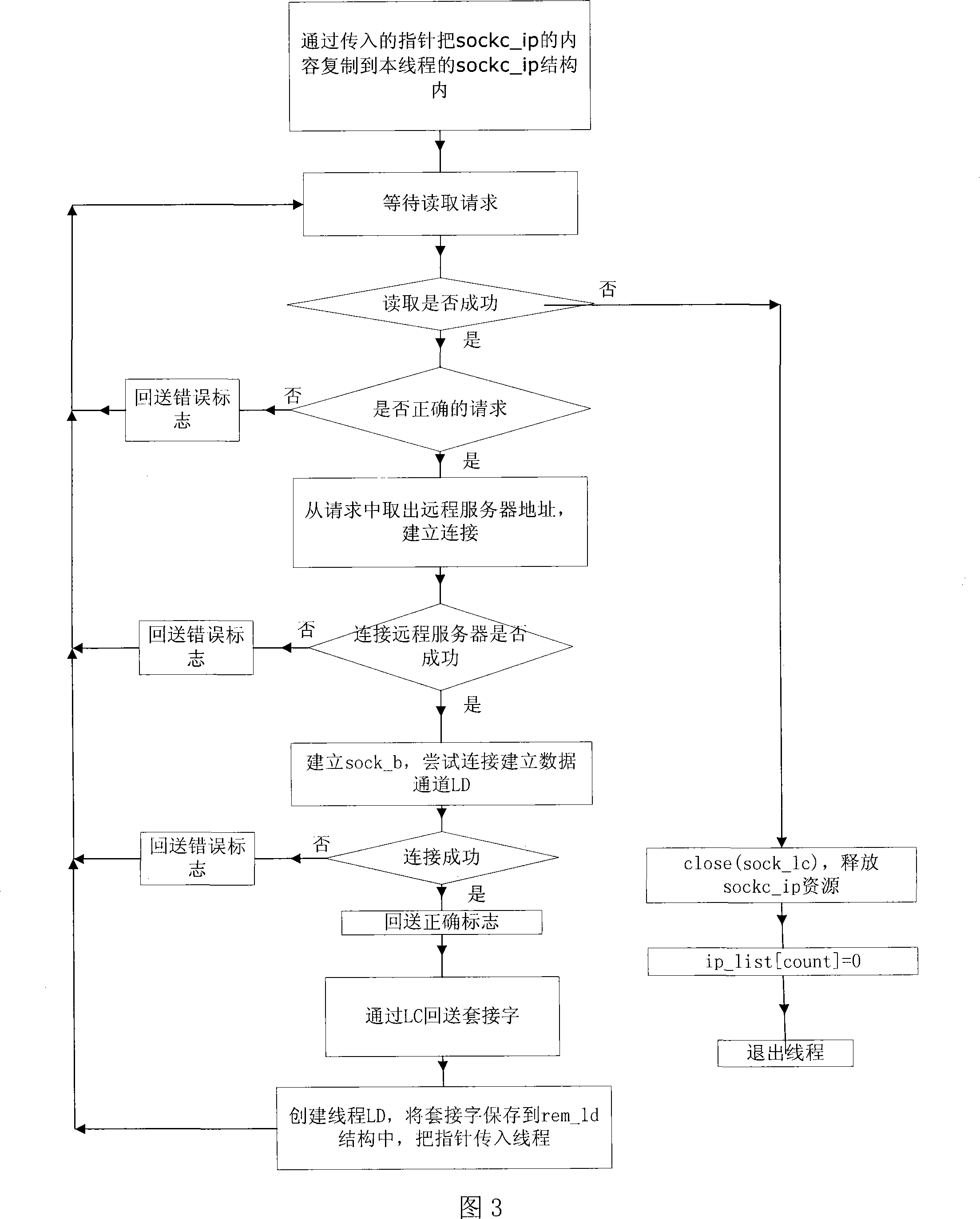
[0017] In this method, the ARM platform A is in the intranet and is a node that actively initiates communication. The basic process is: A initiates a connection to establish an LC channel with external network user B; A reads the request o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com