Patents
Literature
117results about How to "Security service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
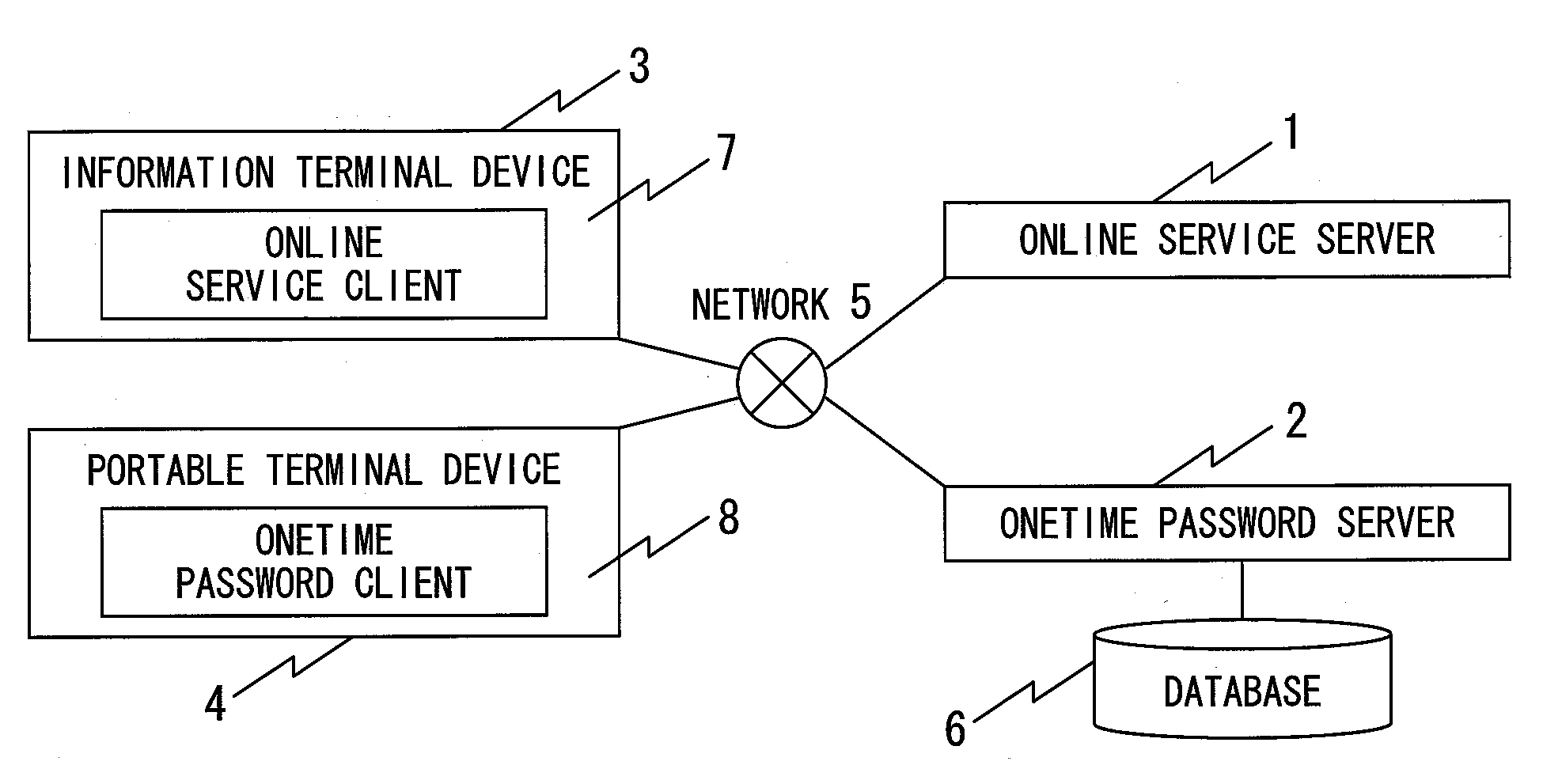
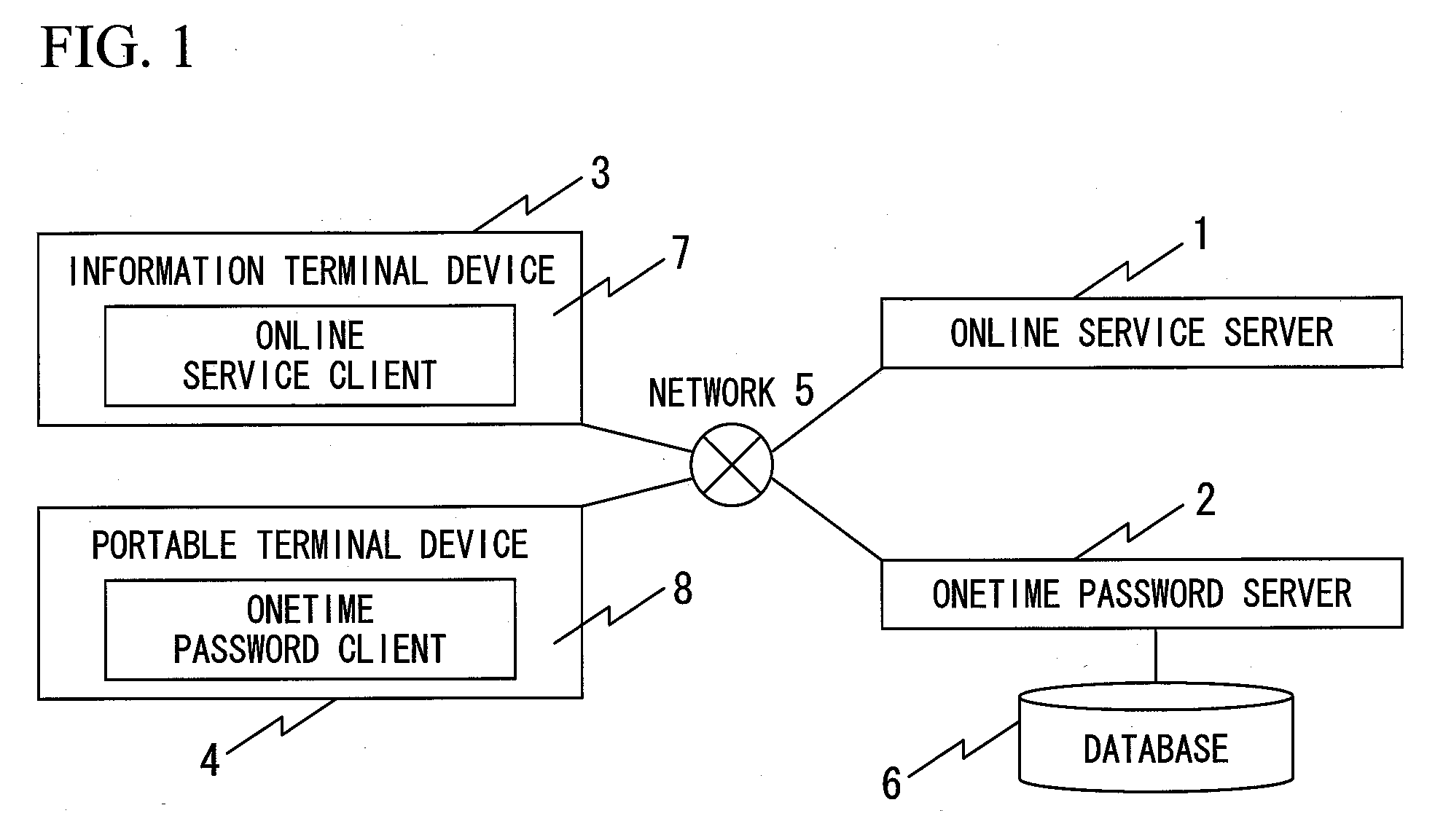
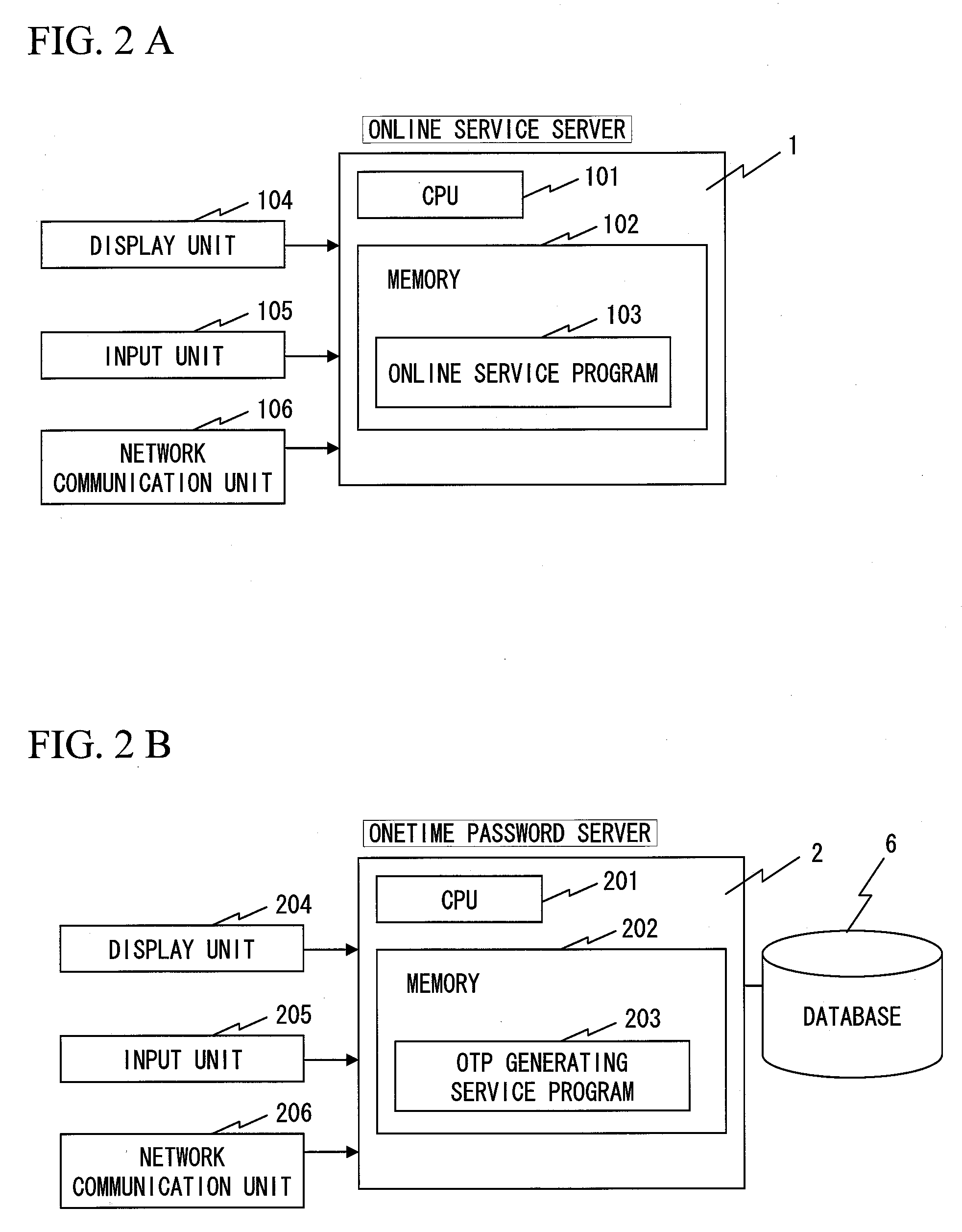
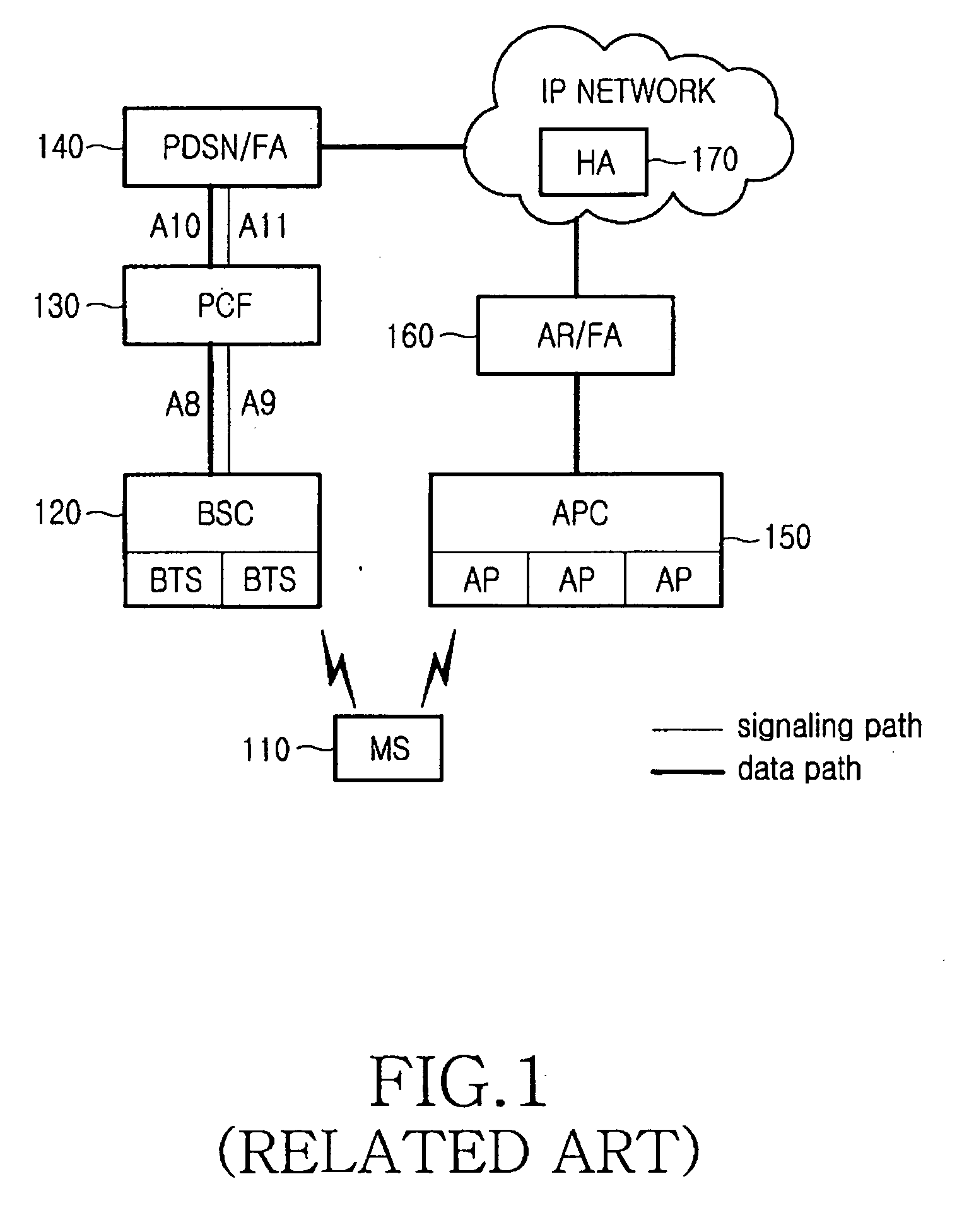
Verification system
InactiveUS20070220597A1Great strengthProvide service safelyDigital data processing detailsUser identity/authority verificationVerification systemTerminal equipment
A verification system in which a client terminal can safely receive online service from an online service server. The verification system includes an online service server, an information terminal device for receiving online service, an OTP server for performing a process involving login verification of the information terminal device and verification of online service transaction contents, and a portable terminal device that displays an OTP used for login verification and transaction contents verification. The portable terminal device includes means for transmitting, to the OTP server, separate acquisition requests for a login-verifying OTP and a transaction-contents-verifying OTP that the information terminal device requires when receiving online service from the online service server, receiving a login verifying OTP and a transaction contents verifying OTP from the OTP server, and displaying them.
Owner:HITACHI SOFTWARE ENG
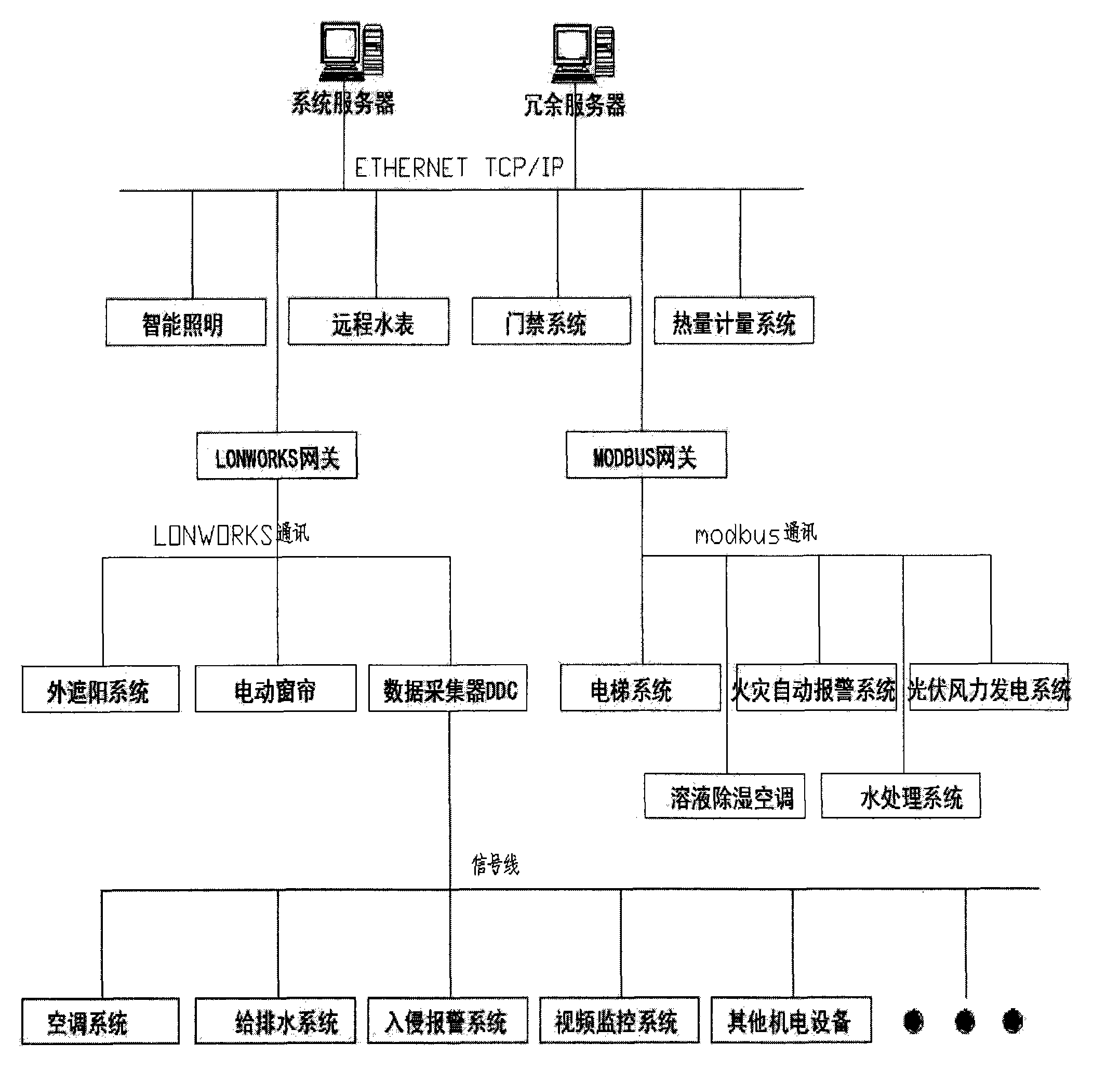
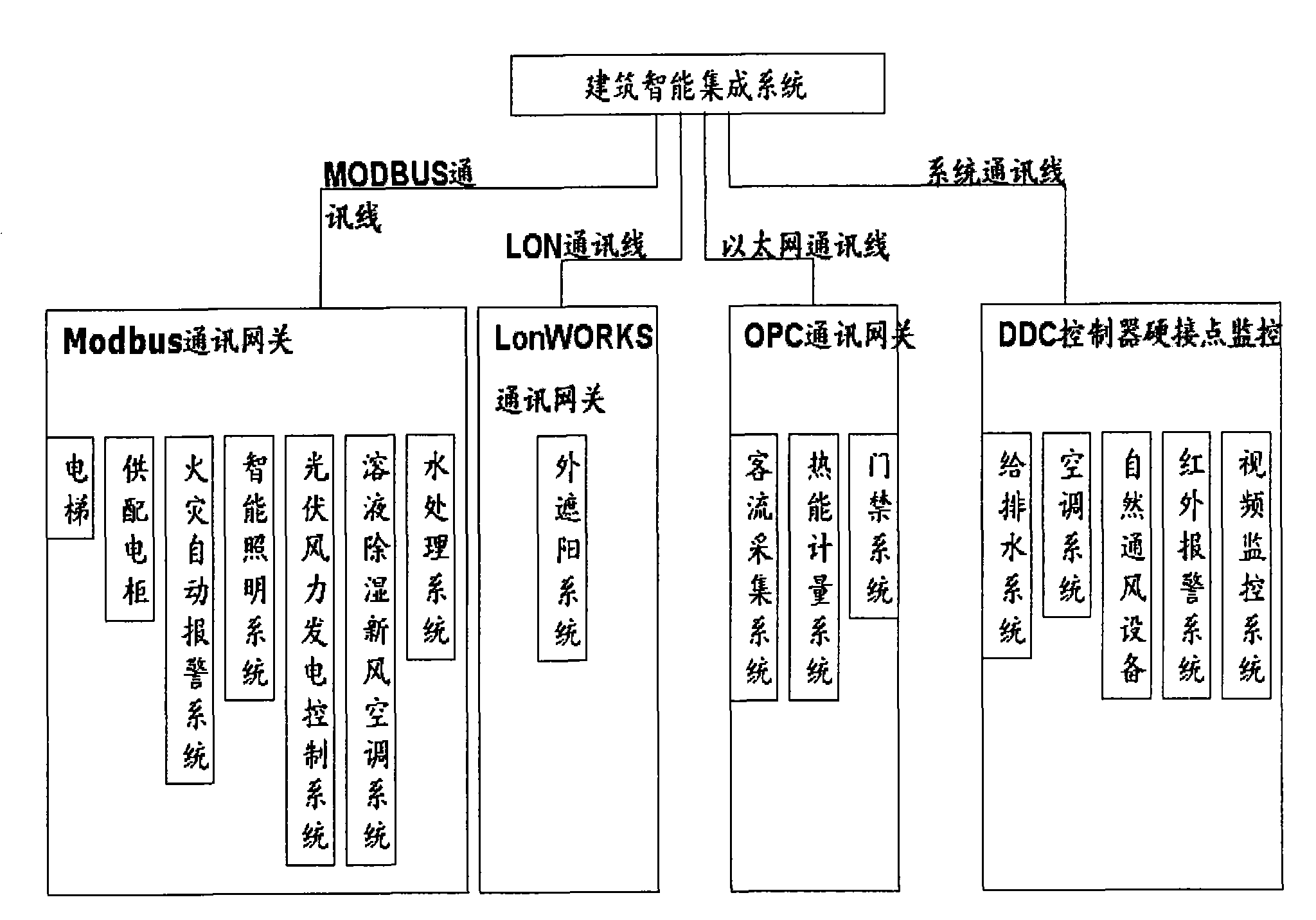
Intelligent building integrated system
ActiveCN101963803ASecurity serviceAchieve sharingTransmissionProgramme total factory controlIntelligent lightingLight equipment
The invention relates to an intelligent building integrated system. The system has a two-stage network structure, of which the first stage is a management layer network and the second layer is a monitoring layer network, wherein the management layer network comprises a control center; a central working station is arranged in the control center; a central working station system consists of a server, a working station, a display and a printer and is directly connected with Ethernet; the management layer network has a bus type network topological structure; the monitoring layer network comprises each protocol gateway, a direct digital controller, an I / O module, a sensor for acquiring a field signal, an executing mechanism and a valve; and the monitoring layer network is a field bus control network. The integrated system also comprises an intelligent lighting control system, an air conditioner, an air feeding and discharging system and a water supply, drainage and treatment system; and the intelligent lighting control system is used for intelligently controlling lighting equipment, to which the intelligent lighting control system belongs, in buildings. The system performs unified monitoring and management to realize necessary gang control so as to truly realize information and resource sharing of the entire building; and thus the best management level is achieved and environment-friendly, complete, high-quality, safe, comfortable and fast service is provided for users.
Owner:SHANGHAI DIGITAL INTELLIGENT SYST ENG
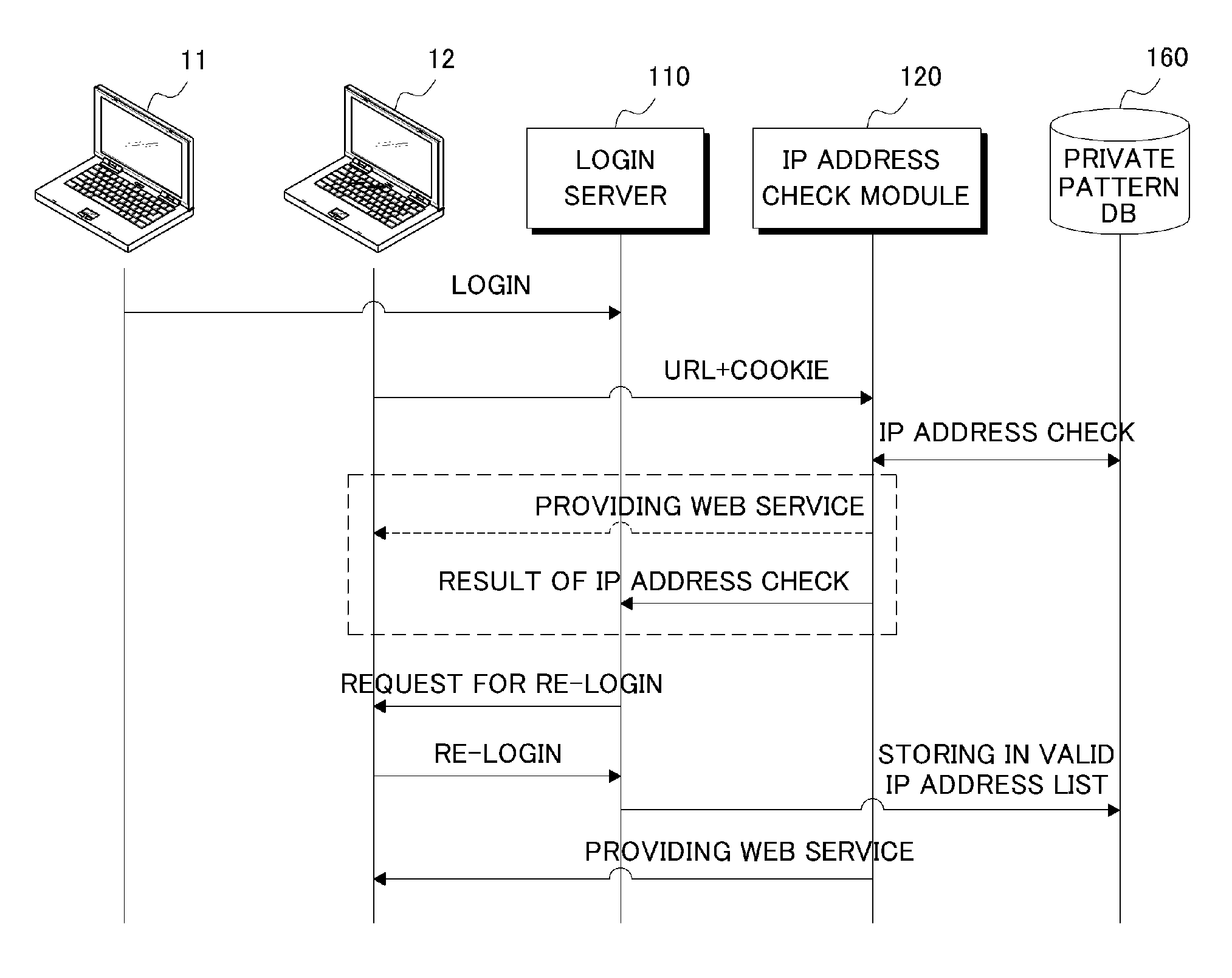
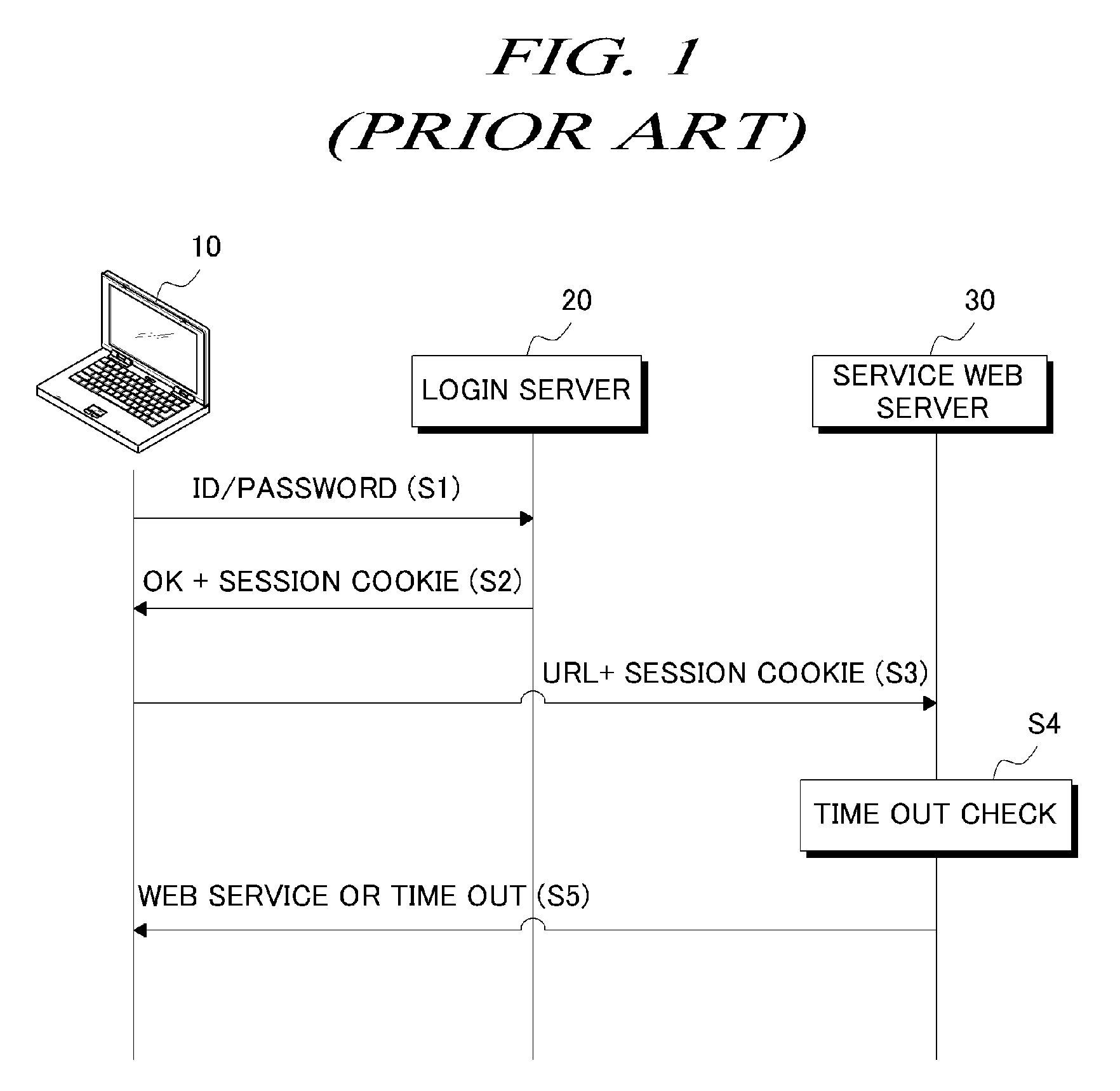
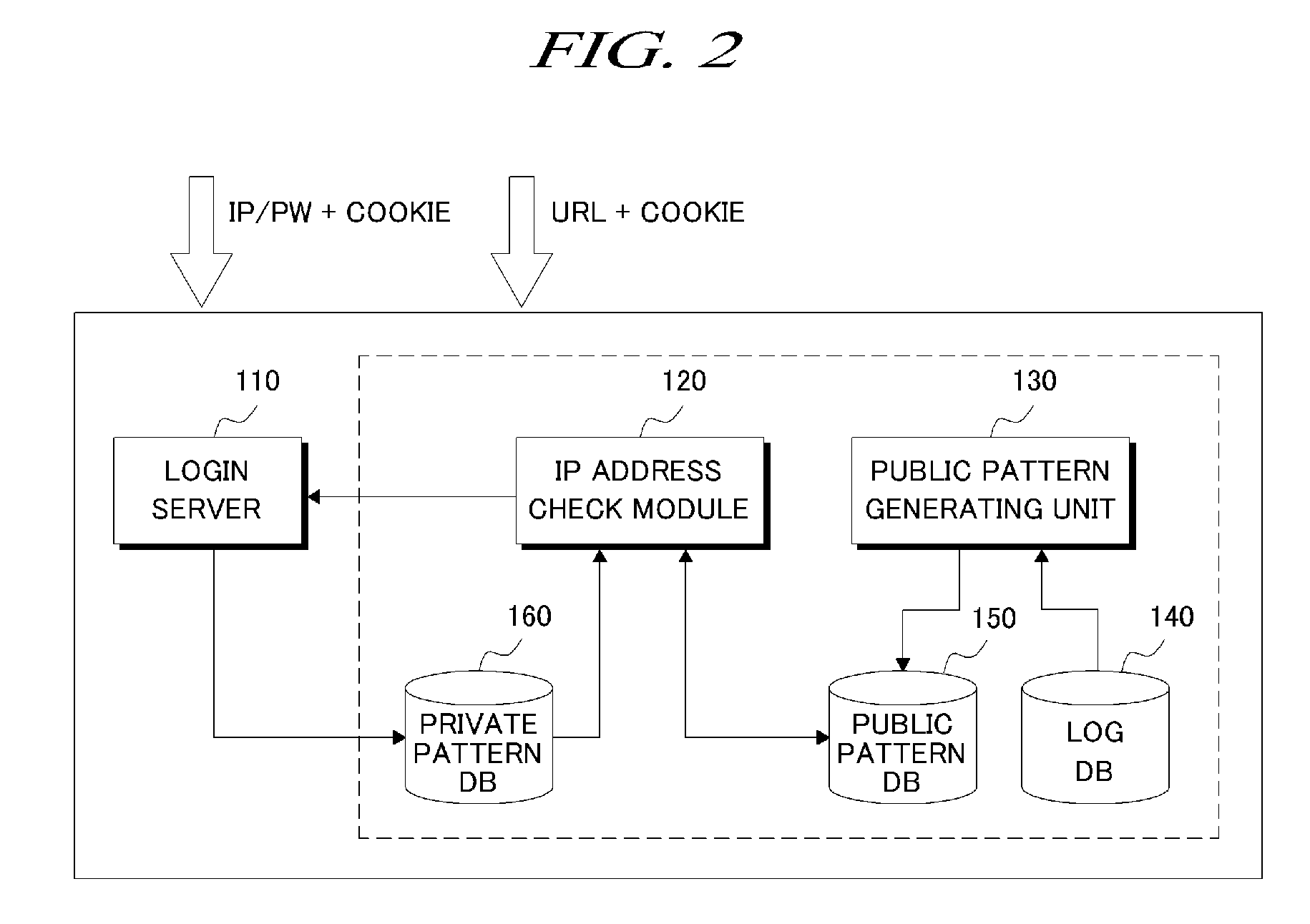
User authentication system using IP address and method thereof
ActiveUS20090055912A1Improve convenienceSecurity serviceDigital data processing detailsUser identity/authority verificationIp addressUser authentication
A method for authenticating a user by IP address check includes: receiving a URL and a session cookie from a client; determining whether or not an IP address of the client has been changed based on the session cookie; resetting the session cookie, if the IP address has been changed, by adding the changed IP address as a temporary IP address thereto; determining whether or not the URL is required to perform IP address check; requesting a re-login to the client if it is determined that the URL is required to perform IP address check; and adding the temporary IP address to a valid IP address list for the user if the re-login is successful.
Owner:NAVER CLOUD CORP
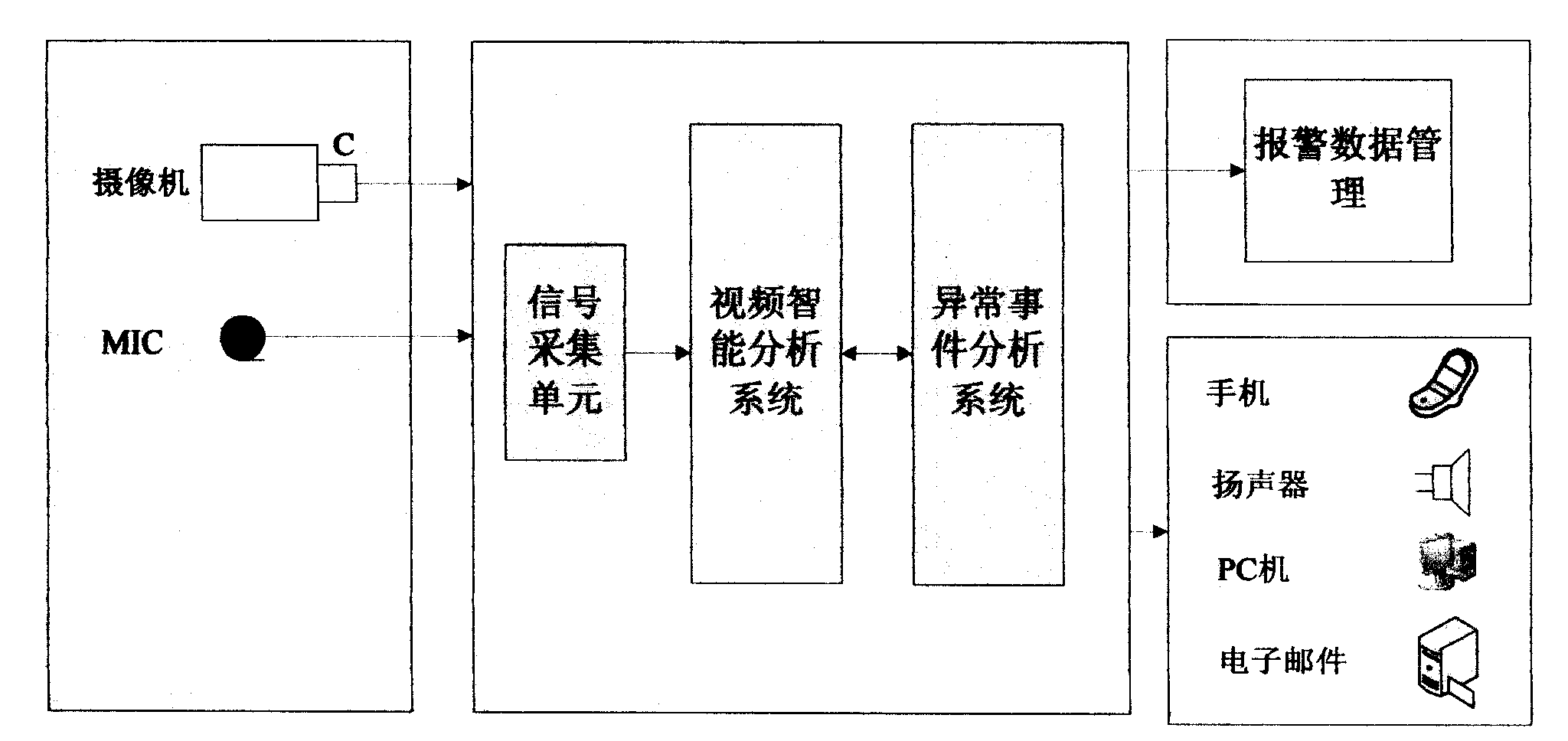
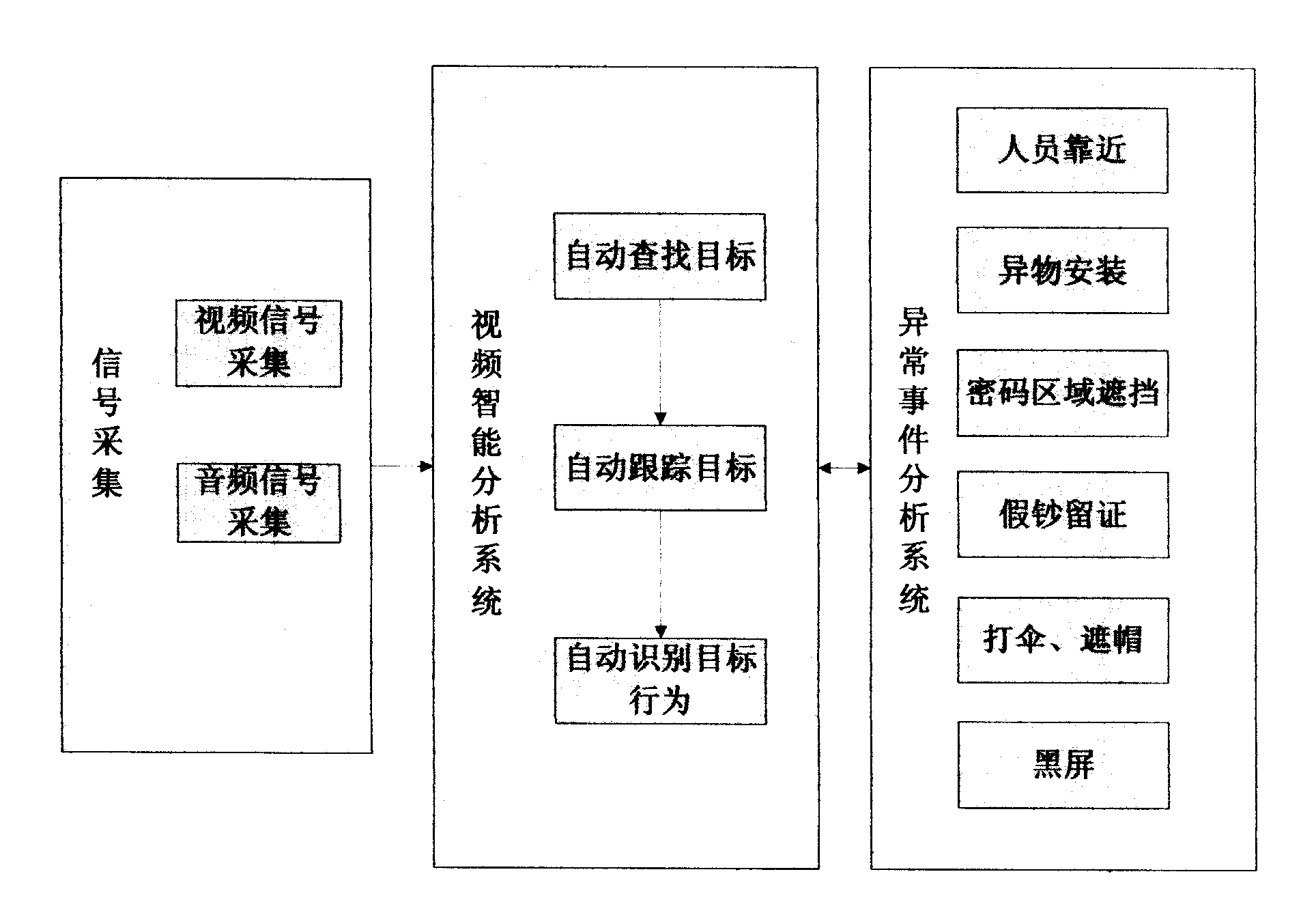
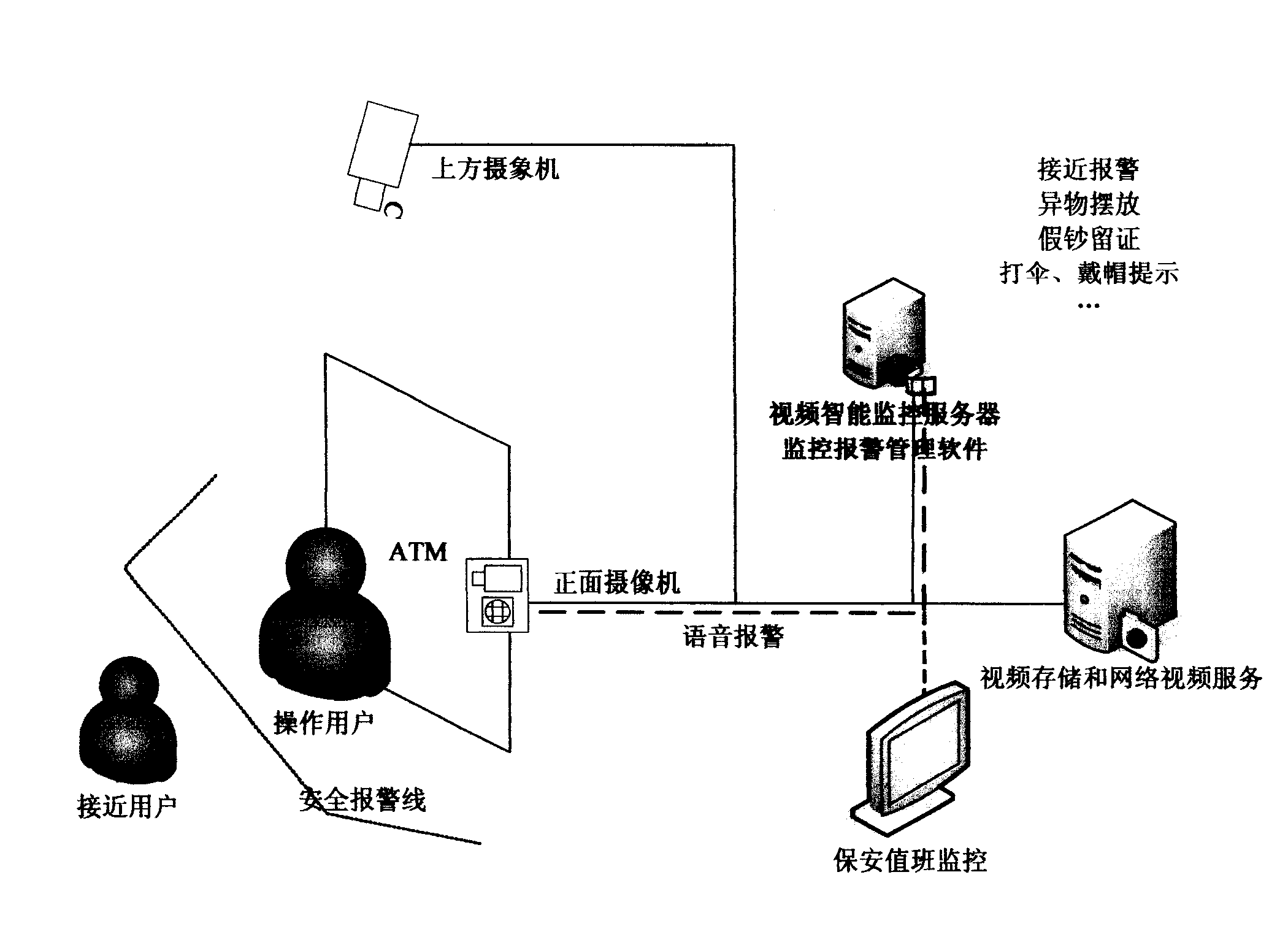
Anomalous video warning device for ATM
InactiveCN101609581APrevention and reduction of illegal activitiesGuaranteed safe operationComplete banking machinesBurglar alarmEvent analysisReal-time computing
The invention relates to the technical field of ATM intelligent monitoring systems. A module comprises an input module, a video intelligent monitoring server, a monitoring alarm management module and an output module. A video intelligent analysis system to which the video intelligent monitoring server is related particularly refers to the behaviors of automatically detecting an object, tracking the object, and recognizing and analyzing the object. The video intelligent monitoring server relates to an anomalous event analysis system which is combined with a front camera and an upside camera to monitor anomalous and dubious behaviors of objects round an ATM, and simultaneously obtain face information of a suspect and give an alarm in time when an anomalous situation happens.
Owner:YUNNAN ZHENGZHUO INFORMATION TECH
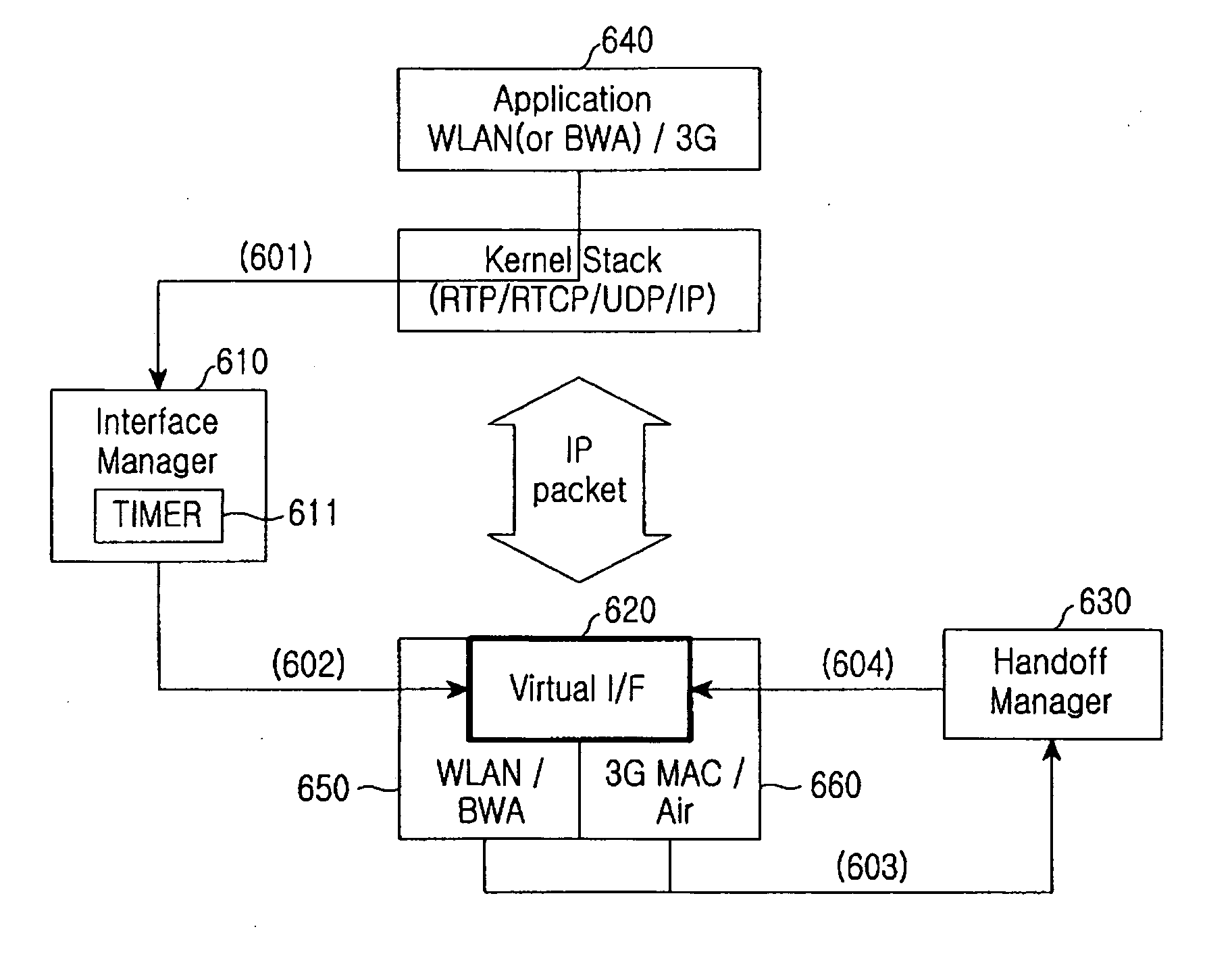
Apparatus and method for selecting network interface in mobile terminal supporting multiple wireless access scheme
InactiveUS20060209821A1Efficiently provideEfficient couplingSynchronisation arrangementConnection managementProtocol ApplicationNetwork interface
An apparatus and method are provided for selecting a network interface in a mobile terminal supporting a multiple wireless access scheme. Upon receiving a connection request to a particular network interface from an application layer, an interface manager maps the application layer to its associated network interface. Upon detecting handoff by receiving current air information, a handoff manager transmits information indicating a change to a new network interface, to a virtual interface. The virtual interface transmits an Internet protocol (IP) packet received from the application layer to the exterior via the network interface mapped to the application layer according to the handoff decision result of the handoff manager.
Owner:SAMSUNG ELECTRONICS CO LTD
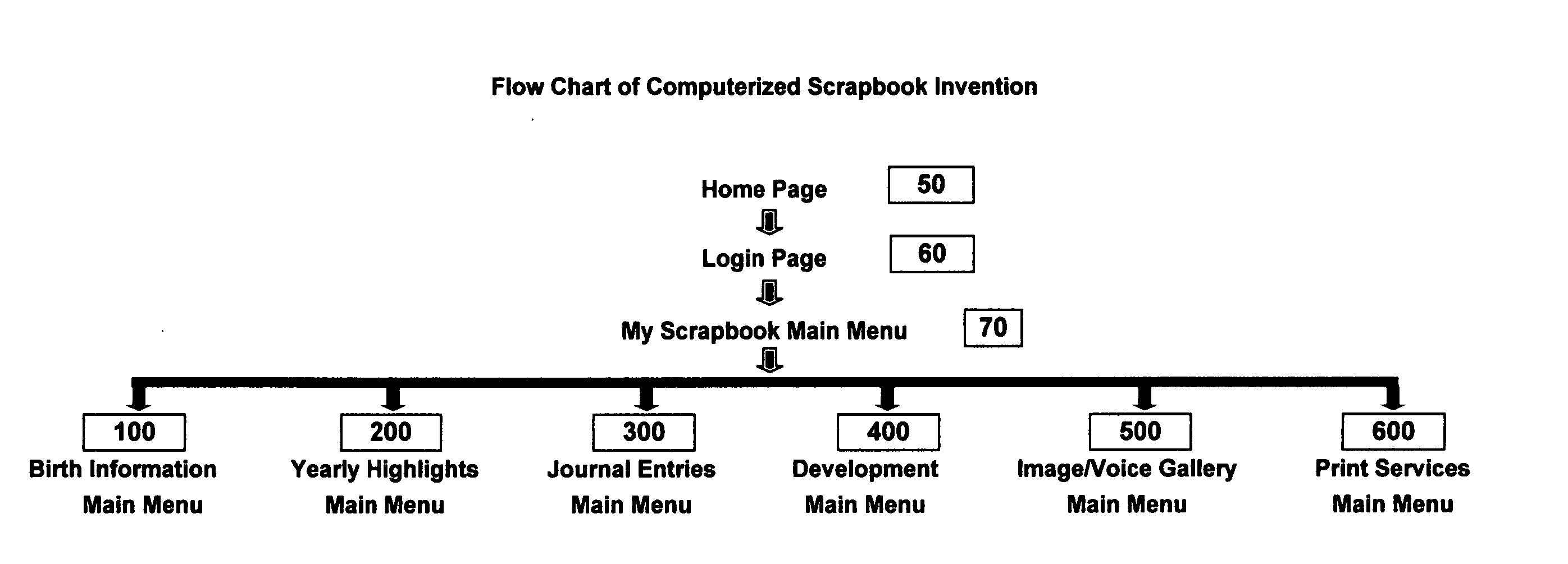
Computerized scrapbook system
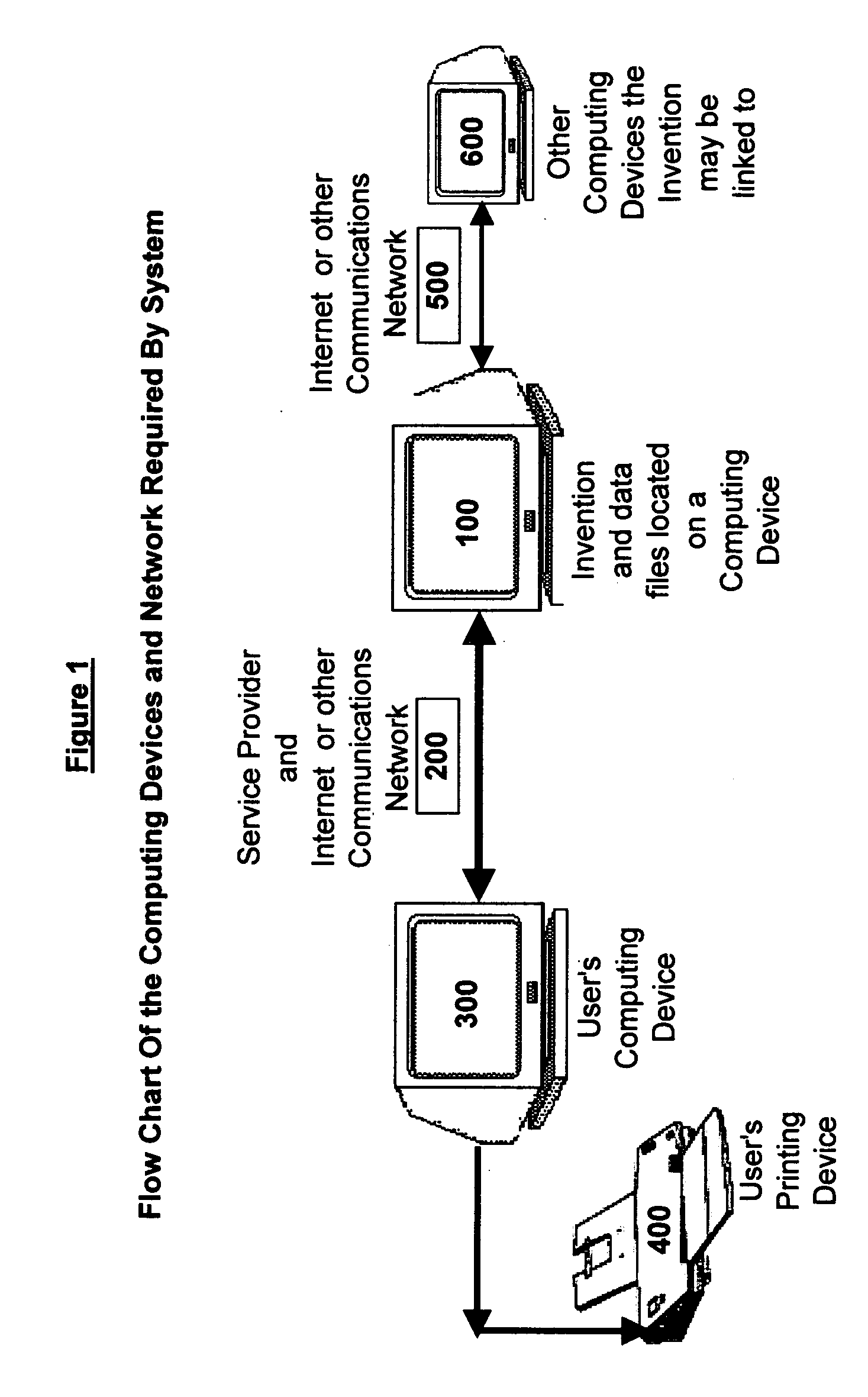
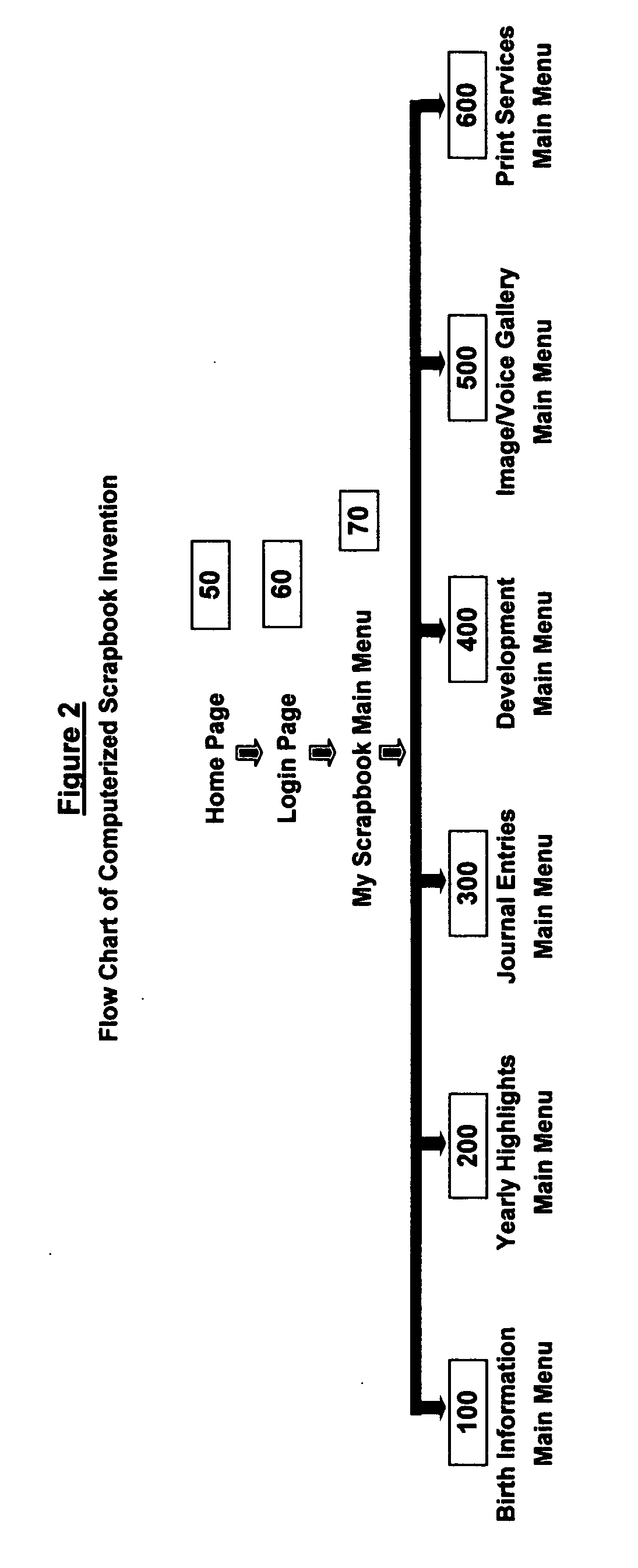
InactiveUS20040194034A1Efficient and cost-effective and convenientConvenience and securityNatural language data processingSpecial data processing applicationsThe InternetComputerized system
A method and system for users to create and maintain a scrapbook in a computerized system is disclosed and explained. From a single Internet or other communications network site provided according to the invention, a user can create, update, view, search and print a scrapbook. The system enables a user to import images, type notes, maintain a journal, and store memorable information. The user also can readily search and view their stored information. Most importantly, the invention automates the scrapbook process for users and provides users with a format to quickly and cost-effectively create duplicate copies of their scrapbook.
Owner:VLAMIS MICHAEL STEVEN
Controlled take over of services by remaining nodes of clustered computing system
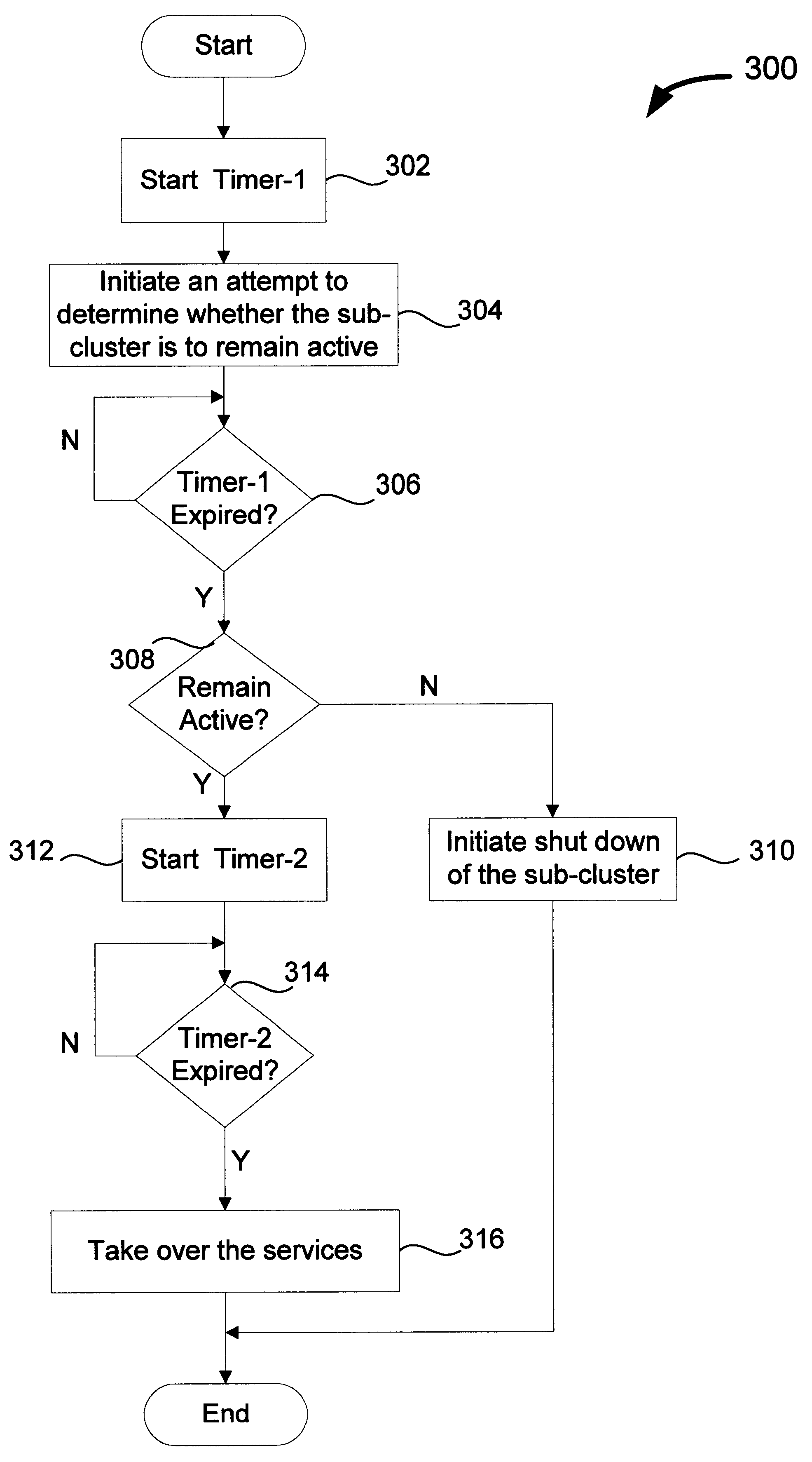
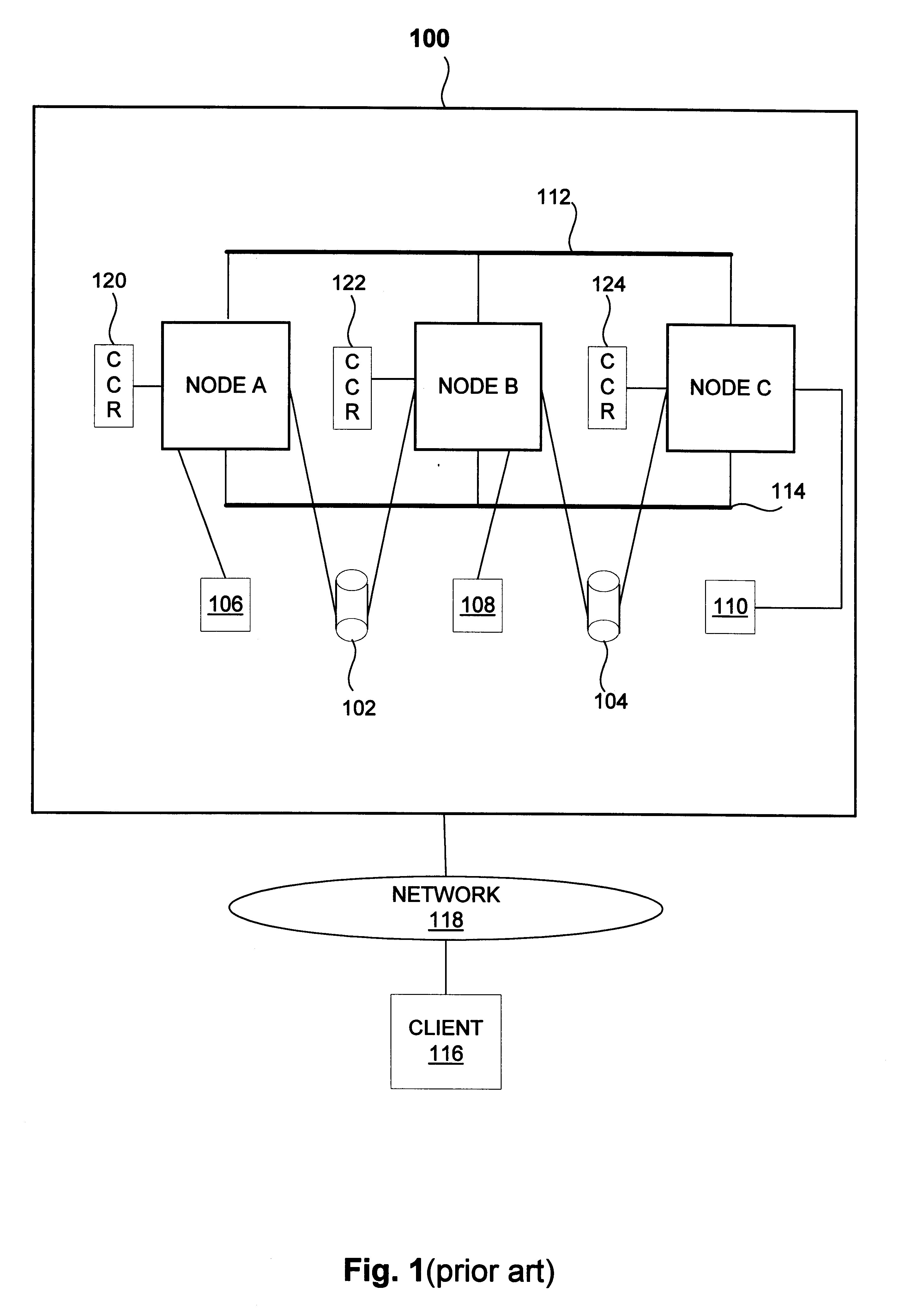
InactiveUS6789213B2Take over serviceSafely provide serviceError detection/correctionDigital computer detailsComputing systemsDistributed computing
Improved techniques for controlled take over of services for clustered computing systems are disclosed. The improved techniques can be implemented to allow one sub-cluster of the clustered computing system to safely take over services of one or more other sub-clusters in the clustered computing system. Accordingly, if the clustered computing system is fragmented into two or more disjointed sub-clusters, one sub-cluster can safely take over services of the one or more other sub-clusters after the one or more other sub-clusters have been shutdown. As a result, the clustered computing system can continue to safely provide services even when the clustered computing system has been fragmented into two or more disjointed sub-clusters due to an operational failure.
Owner:ORACLE INT CORP
Man-machine interface technique for fingerprint locker and method for managing same
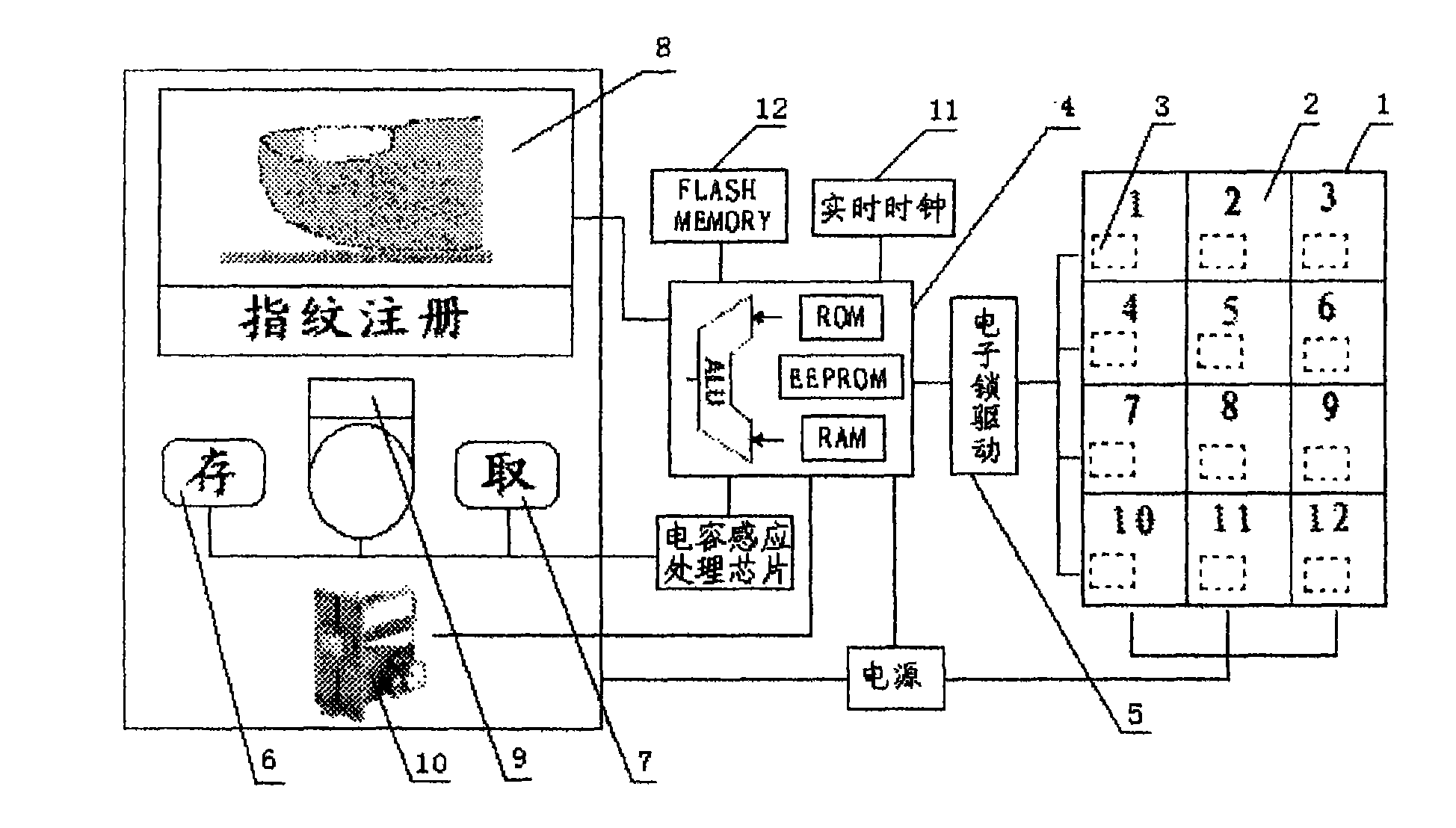
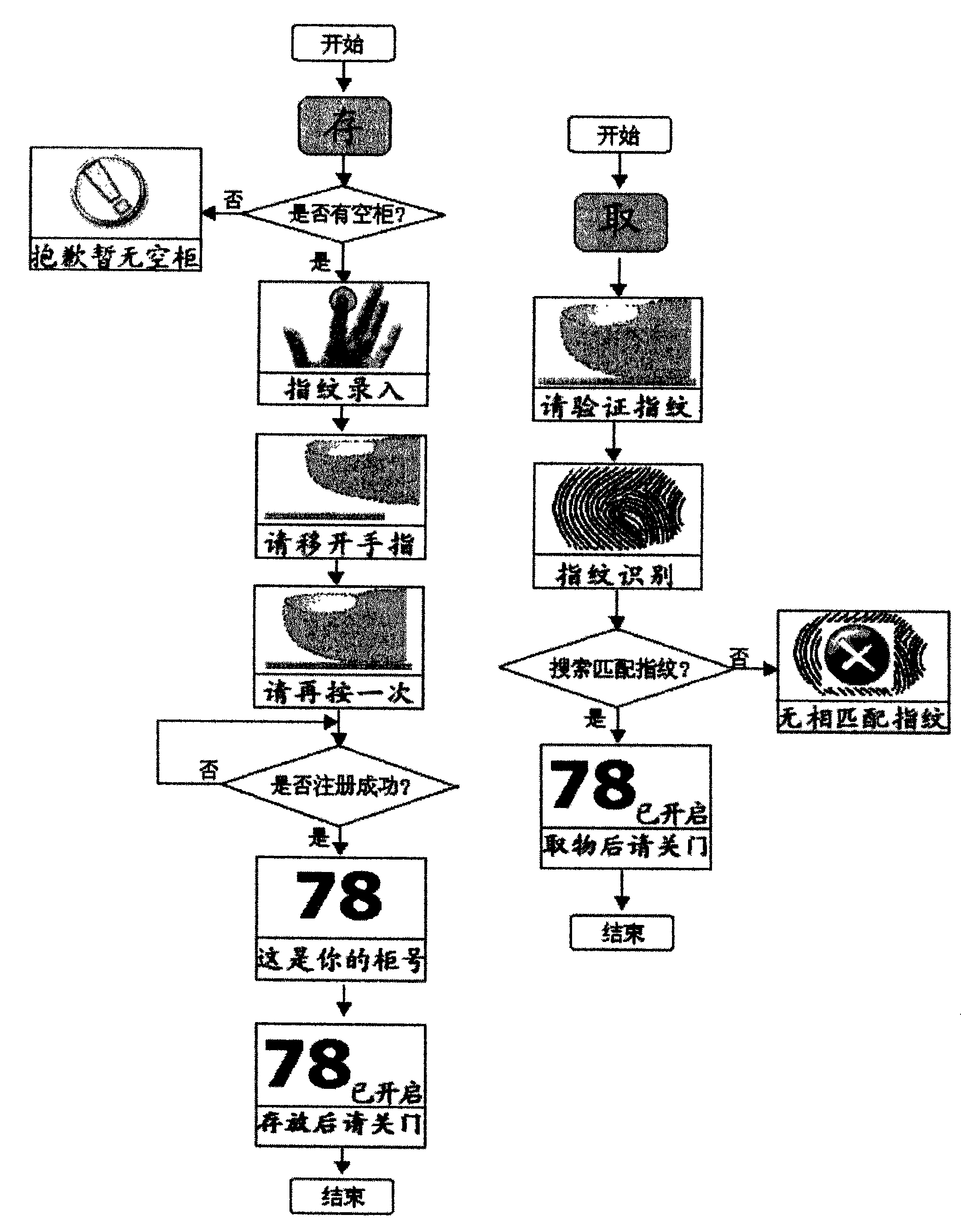
InactiveCN101625781AEasy to useQuality improvementApparatus for meter-controlled dispensingLiquid-crystal displayPublic place
The invention discloses a man-machine interface technique for a fingerprint locker and a method for managing the same. A system adopts the combination of the fingerprint identification technique in the biometric identification technology and the man-machine interface technique to complete the work for safe temporary storage of articles of people necessary in a public place. The technique is characterized in that: only 2 to 3 keys and display contents combining patterns and characters and displayed by an LCD form the interactive man-machine interface, and an intuition guide based mode is adopted to guide a user for routine access operation; and by the same man-machine interface, the equipment managing staff can quite conveniently complete the back-stage management operations of the equipment, such as time setting and correction, language setting of a user interface, fee rate setting, money withdrawing operation, locker opening treatment in an abnormal state, safety audit and the like, under a highly-safe safety restriction mechanism. The technique has the advantages of simple user interface and easy use of the same man-machine interface, easy management of the management interface,comprehensive management functions, and sound security mechanism.
Owner:黄涛
Distributed type security system
ActiveCN101211495ASecurity security serviceFast Security ServiceAlarmsManipulatorMoving speedEngineering
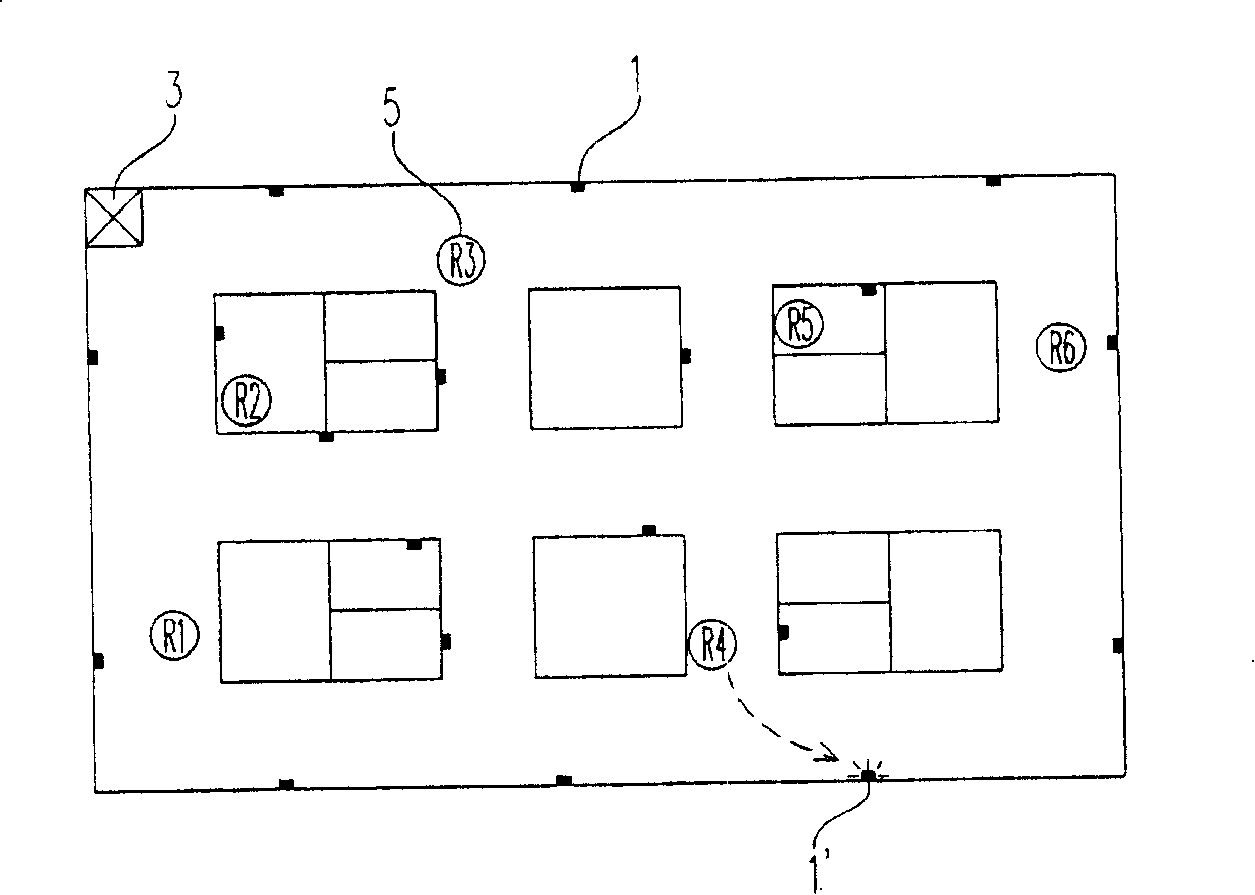
The invention provides a distributed preserving system, which comprises a plurality of sensing devices, a main system and a plurality of robots, wherein the sensing devices are arranged in the environment and send the measured environment information to the main system. The main system can assign the robot which can reach the occurring position of abnormality in the shortest time and monitor when the main system judges the occurrence of the abnormality based on the environment information. The shortest time is computed out according to the relevant displacement distance of the robot and the sensed position and the highest moving speed of the robot. By adopting the distributed preserving system, when a plurality of sensing devices are abnormal, the main system commands a plurality of robots to move there and process so as to achieve the effects of providing more rapid and safer preserving service and further reducing occurrence of danger.
Owner:IND TECH RES INST
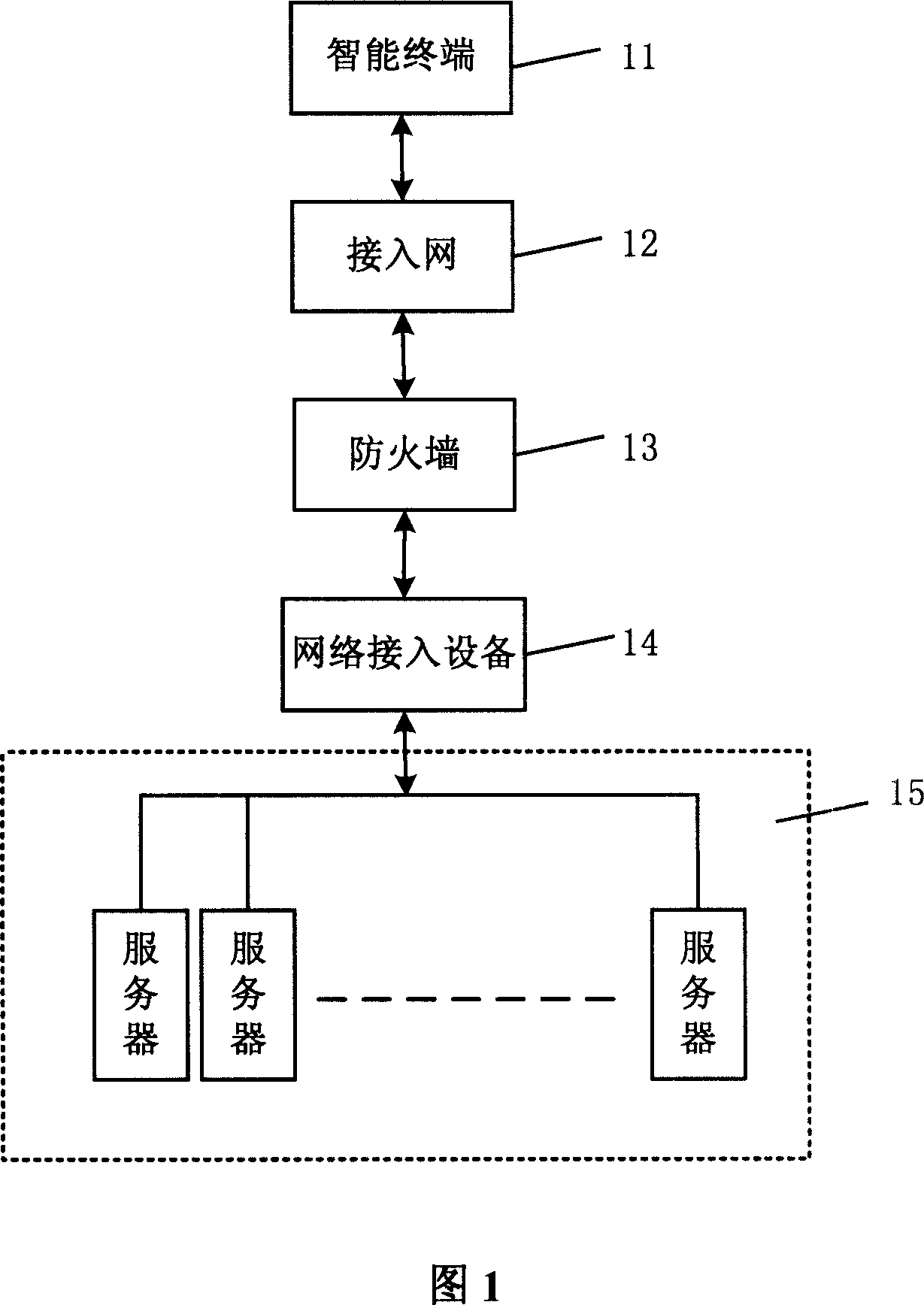
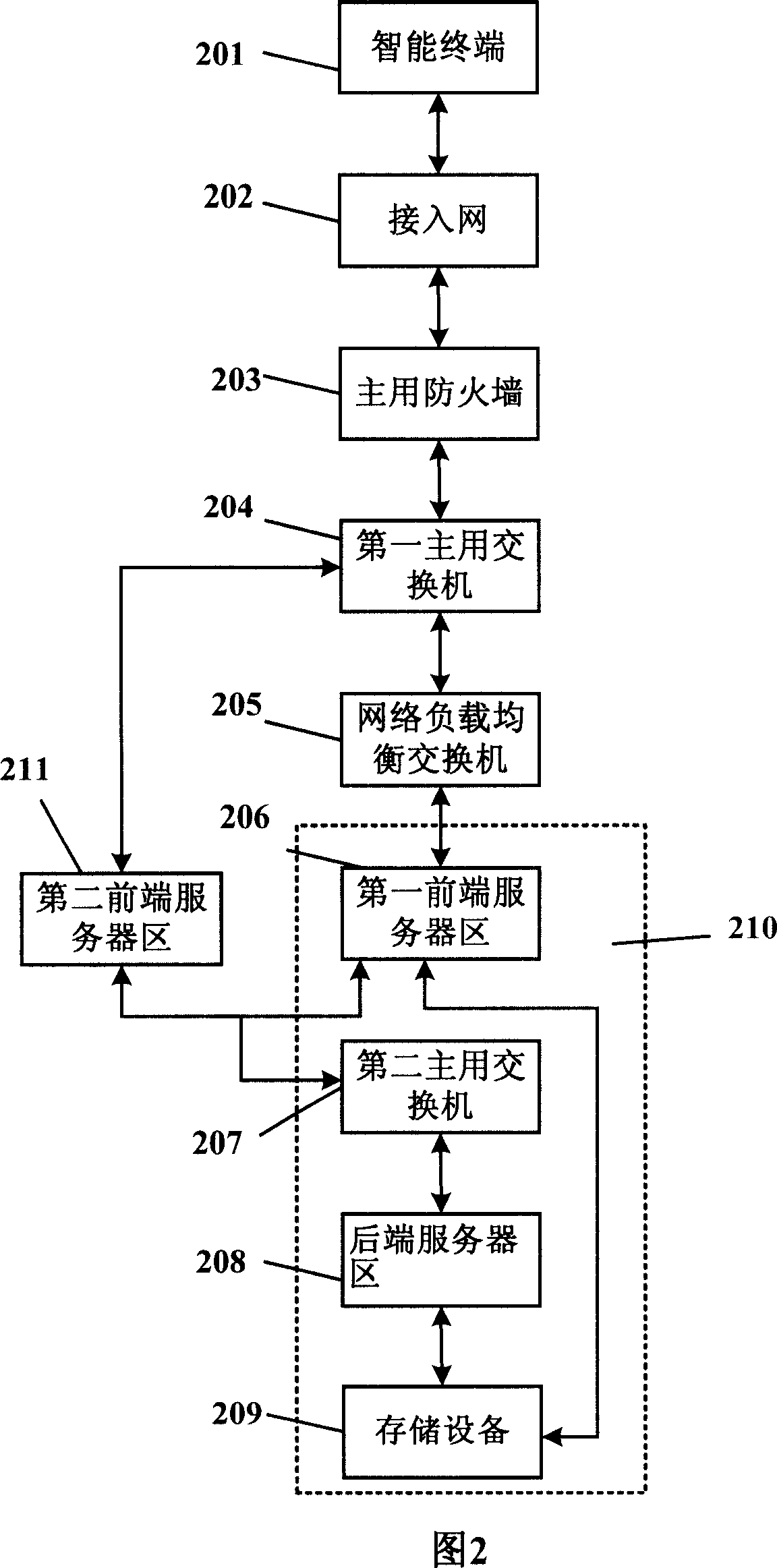
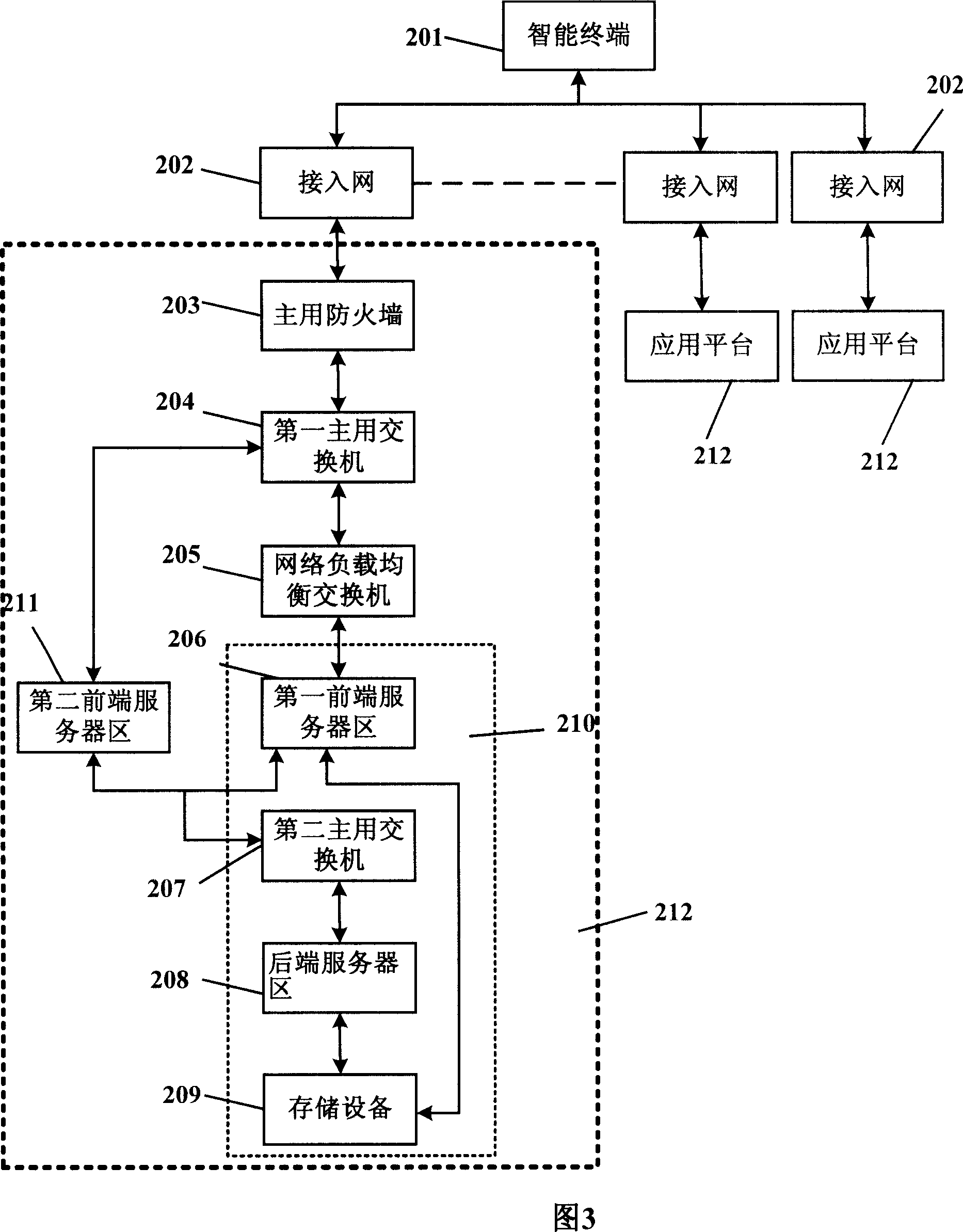
Network structure-based intelligent terminal application system
InactiveCN1968166AAvoid Traffic BottlenecksProvide overall performanceData switching by path configurationAuthorizationDomain analysis
The invention relates to an intelligent terminal application system based on network structure, which at least comprises one local network with intelligent terminal, access network, and fireproof wall; the first server area with several different server groups while each group has at least one server with different functions, and the first server area has authorization domain analysis server; network load balancer connected to the fireproof wall and the first server area, to select one of minimum-load server to connect the intelligent terminal, according to the requested server group and the load of server.
Owner:UNICOM NEW SPACE
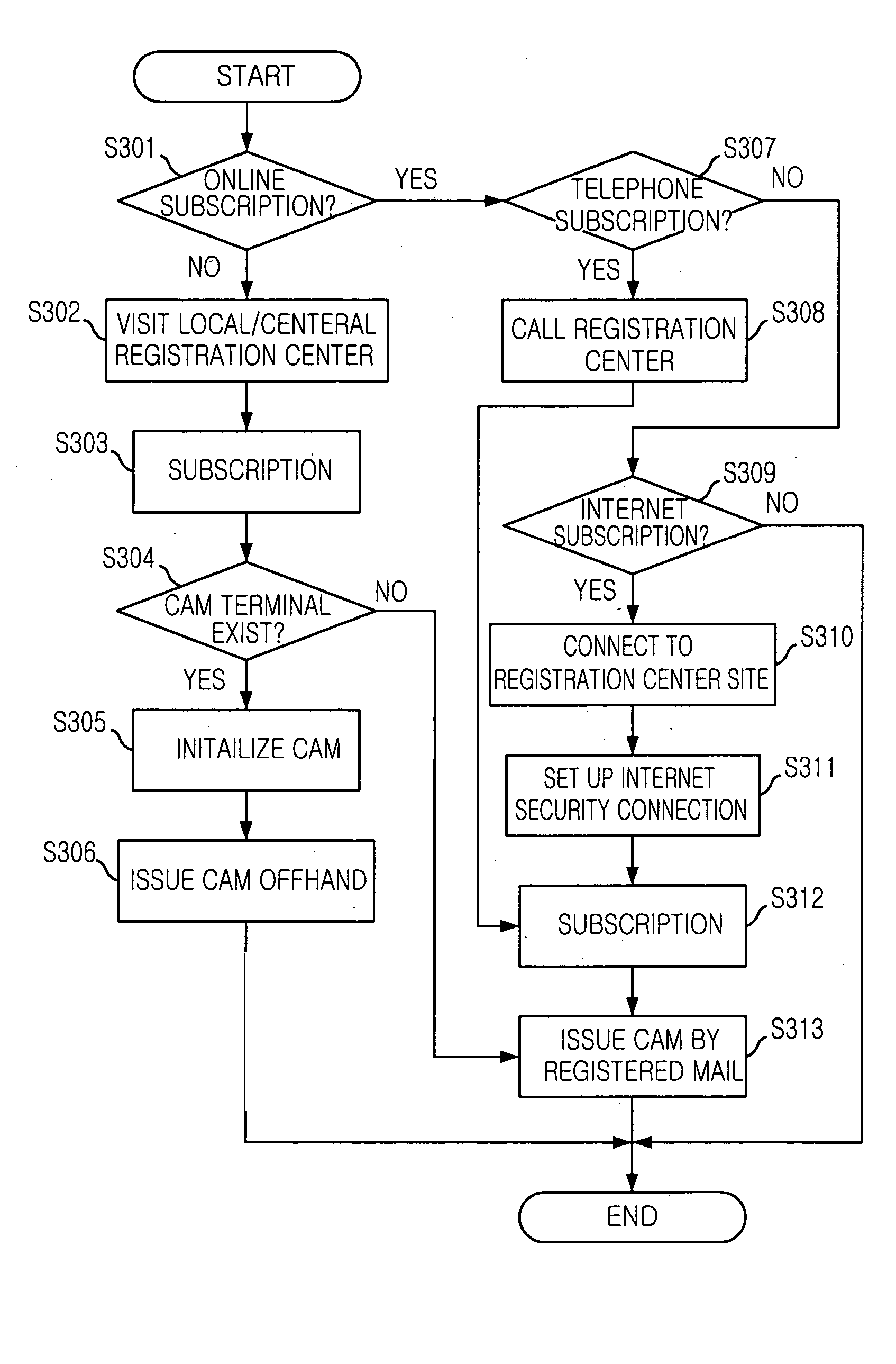
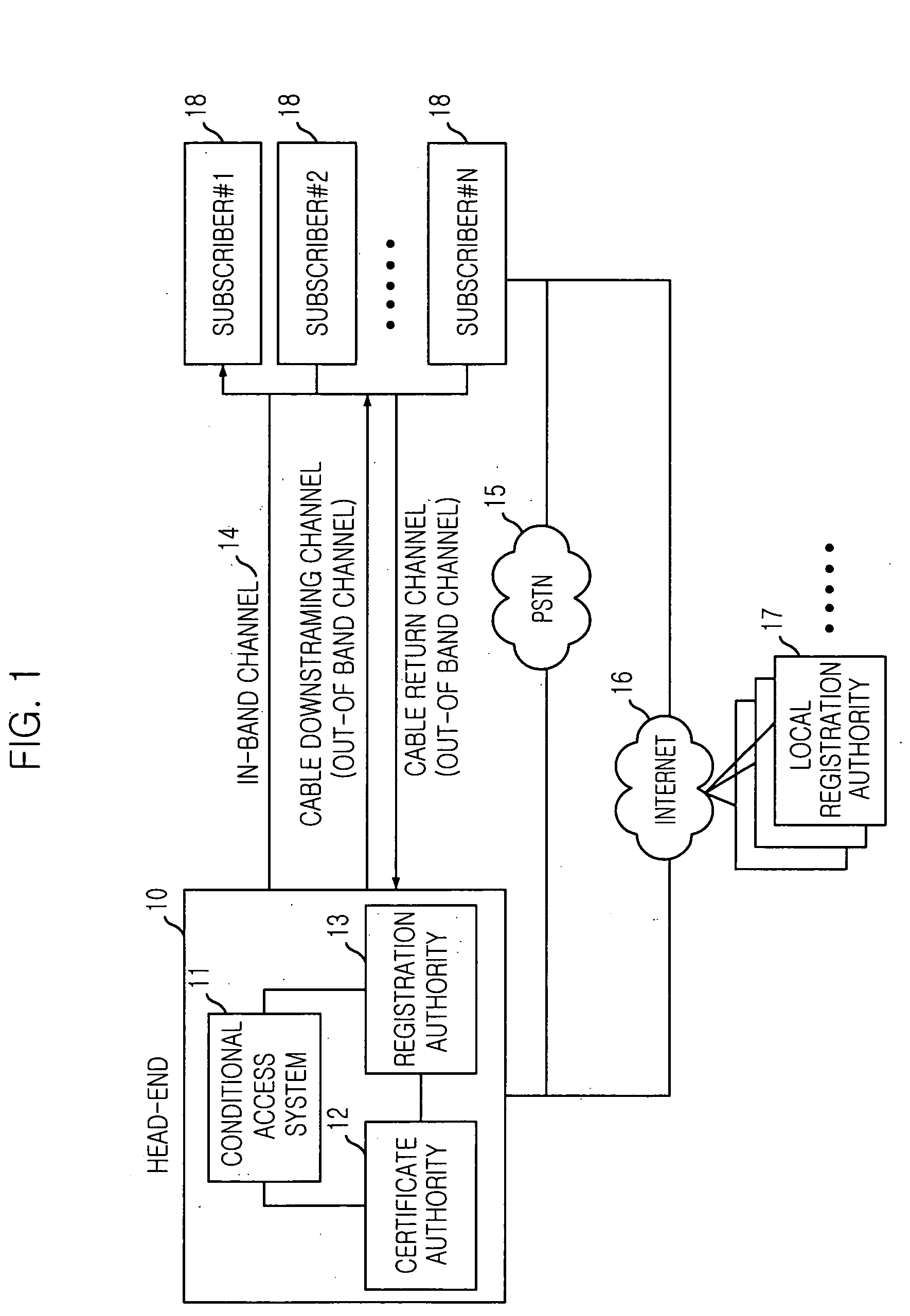
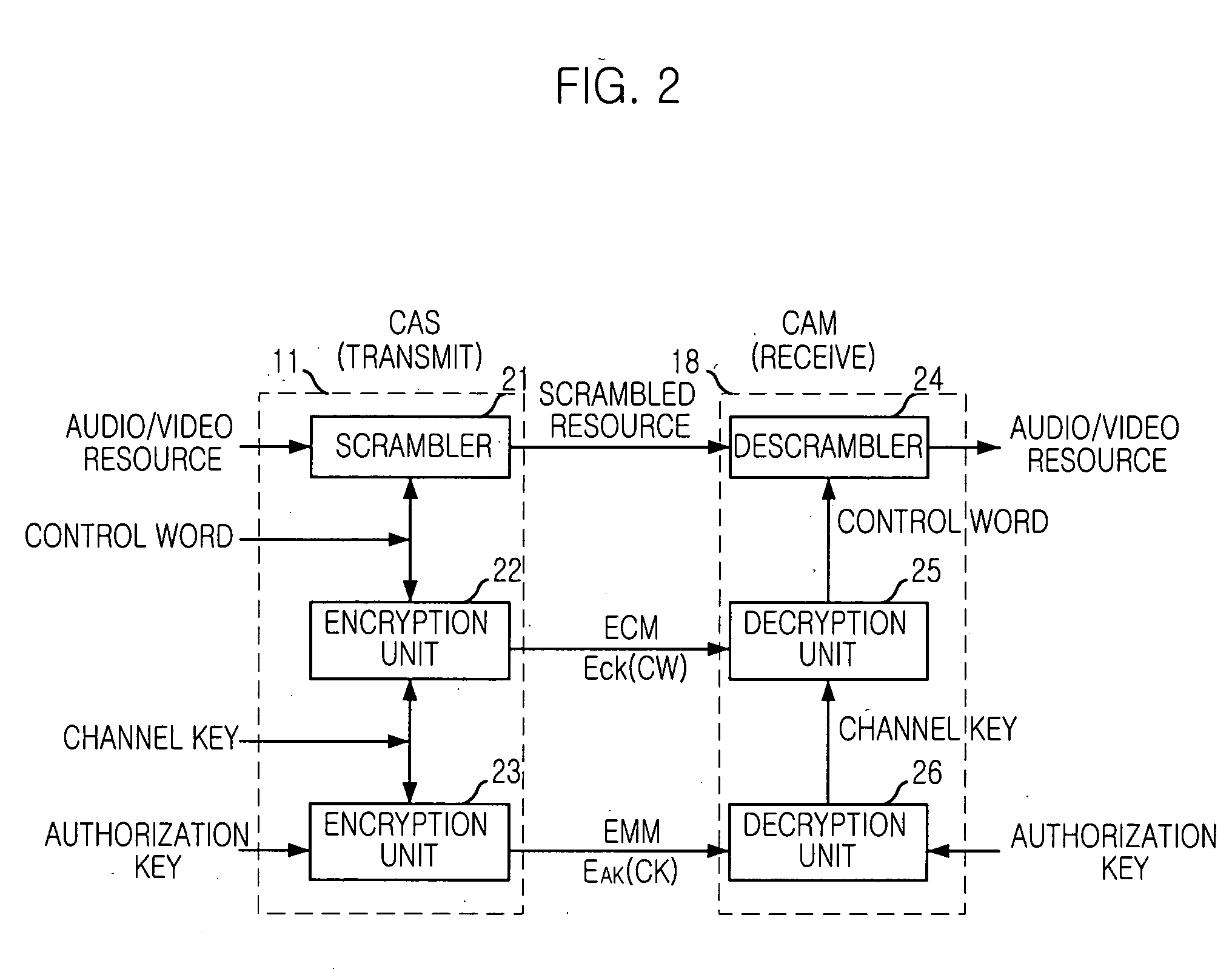
Method for subscribing service and distributing encryption key based on public-key encryption algorithm in digital CATV system
ActiveUS20050141712A1Improve securitySecurity serviceComplete banking machinesFinanceTelevision systemDigital signature
A method for subscribing a service and distributing encryption key based on public-key encryption algorithm in a digital CATV system are disclosed. In accordance with an aspect of the present invention, there is provided a method including the steps of: a) generating a charged service application message; b) generating a session connection request message, signing based on a digital signature scheme with appendix on the session connection request message and transmitting to the head-end; c) generating a symmetric-based session key, signing a digital signature on the key, encrypting based on a public-key of the subscriber, transmitting the session key to the subscriber; decrypting the session key message, verifying the digital signature, extracting the session key from the session key message and storing at a Condition Access Module; and d) signing a digital signature on the charged service request message, encrypting using the extracted session key and transmitting to the head-end.
Owner:ELECTRONICS & TELECOMM RES INST
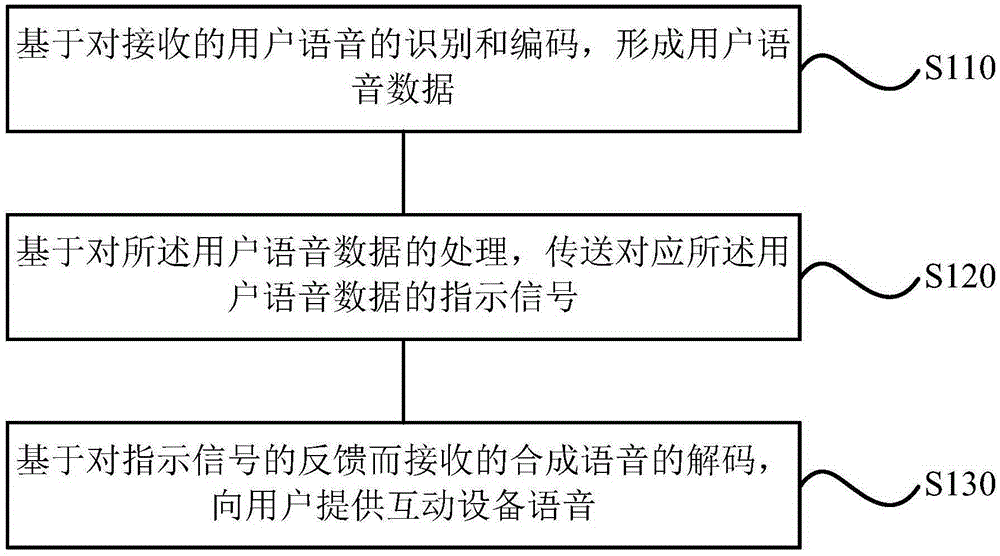
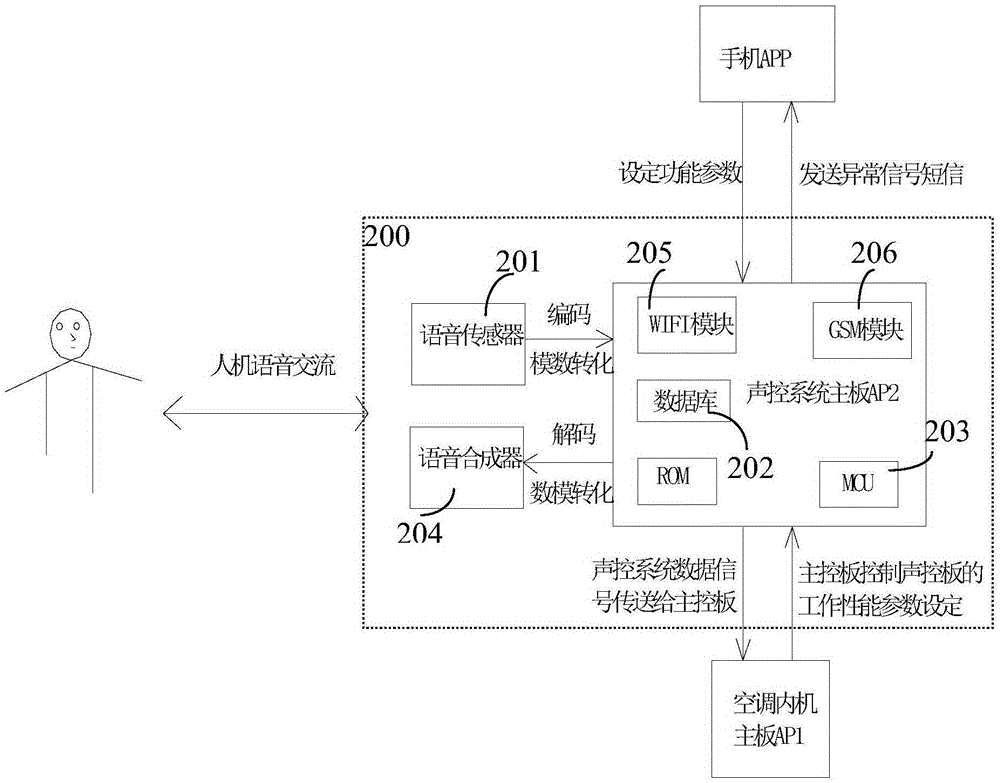
Voice control method, voice control system and voice-controlled air-conditioner
InactiveCN105185378AImprove convenienceProcess intelligenceSpace heating and ventilation safety systemsLighting and heating apparatusControl systemAir conditioning
The invention provides a voice control method, a voice control system and a voice-controlled air-conditioner. The method comprises the following steps: forming user voice data based on recognition and coding of received user voice; transmitting an indicating signal corresponding to the user voice data based on processing for the user voice data to complete control of a user by voice. Therefore, the problem that the voice control system, constructed by voice sensing, synthesizing and analyzing processing, of air-conditioning equipment is used for implementing human-machine information transfer and communication by human voice can be solved, human-machine information communication is conveniently realized, and more air-conditioning equipment control modes and various equipment interaction experience and humanized service can be provided.
Owner:GREE ELECTRIC APPLIANCES INC
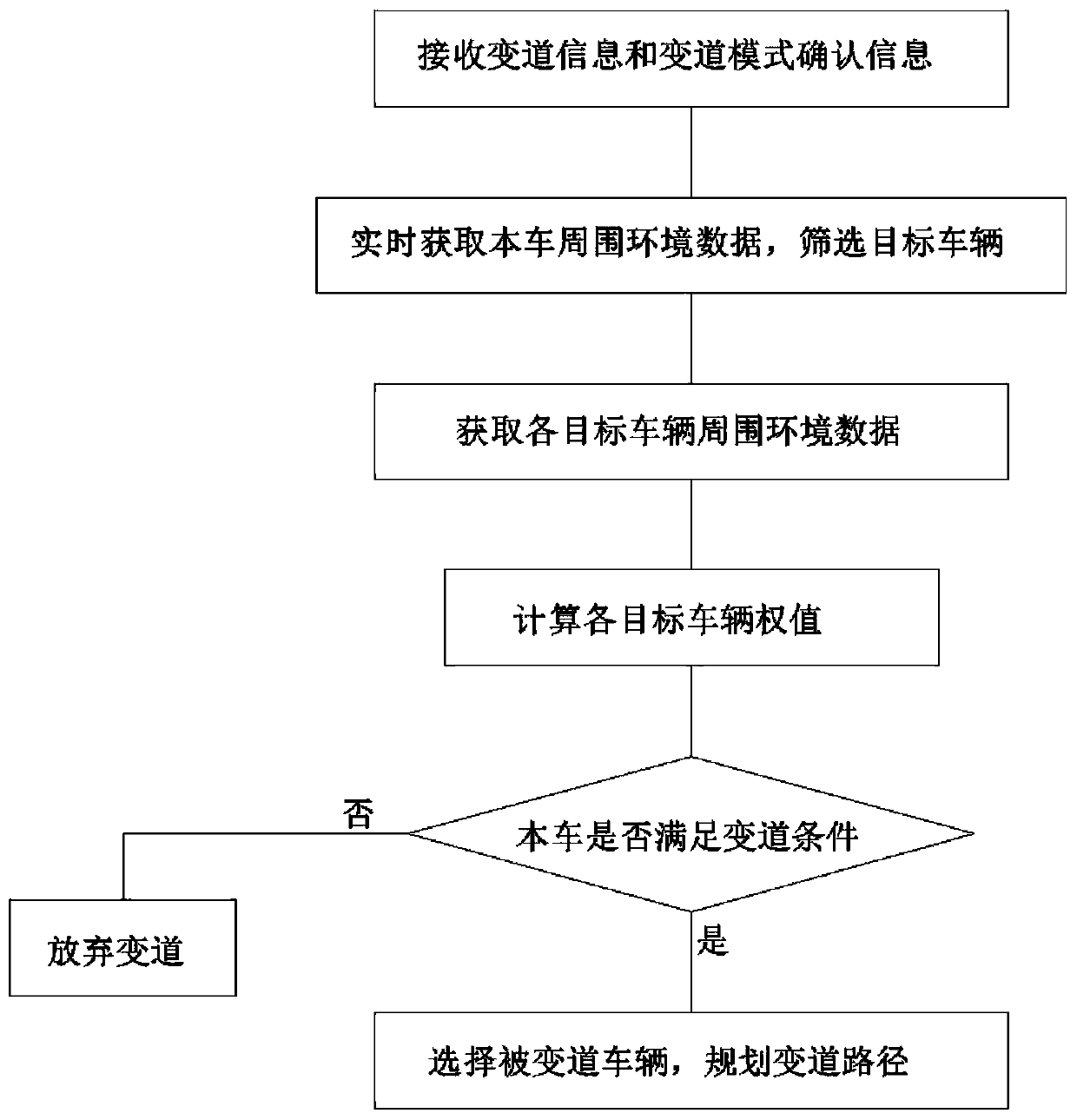
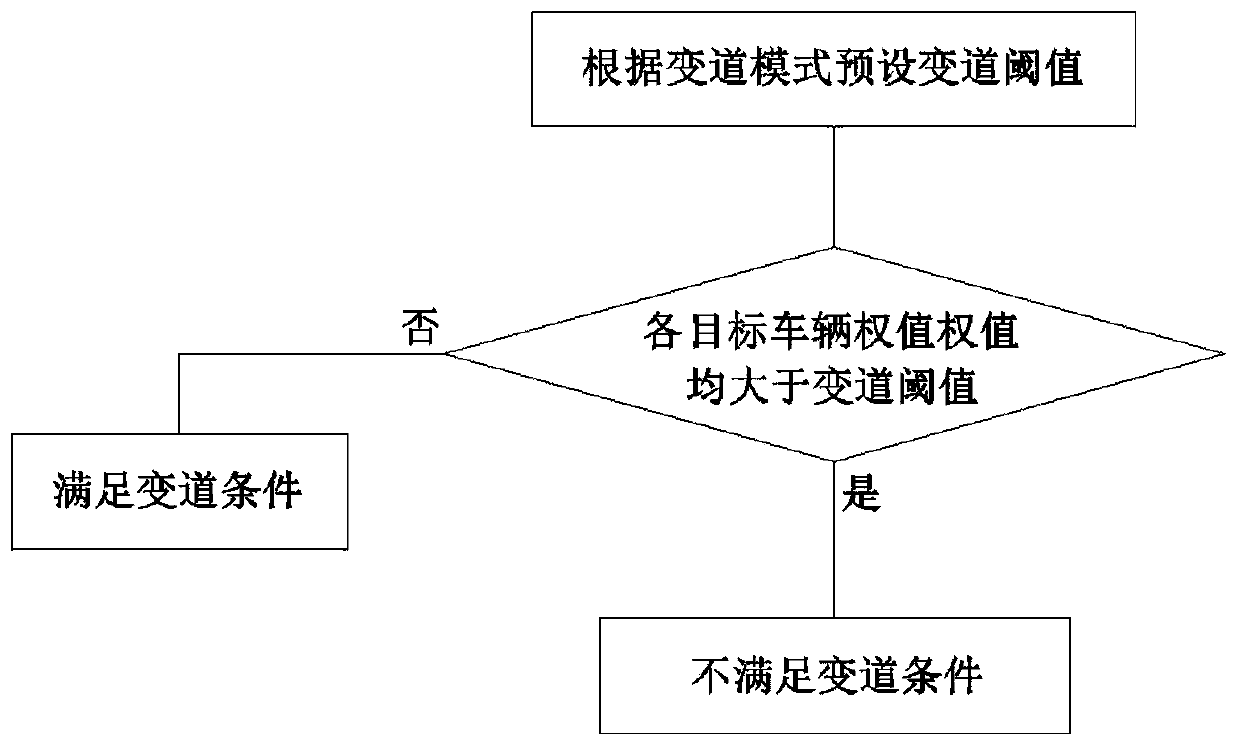
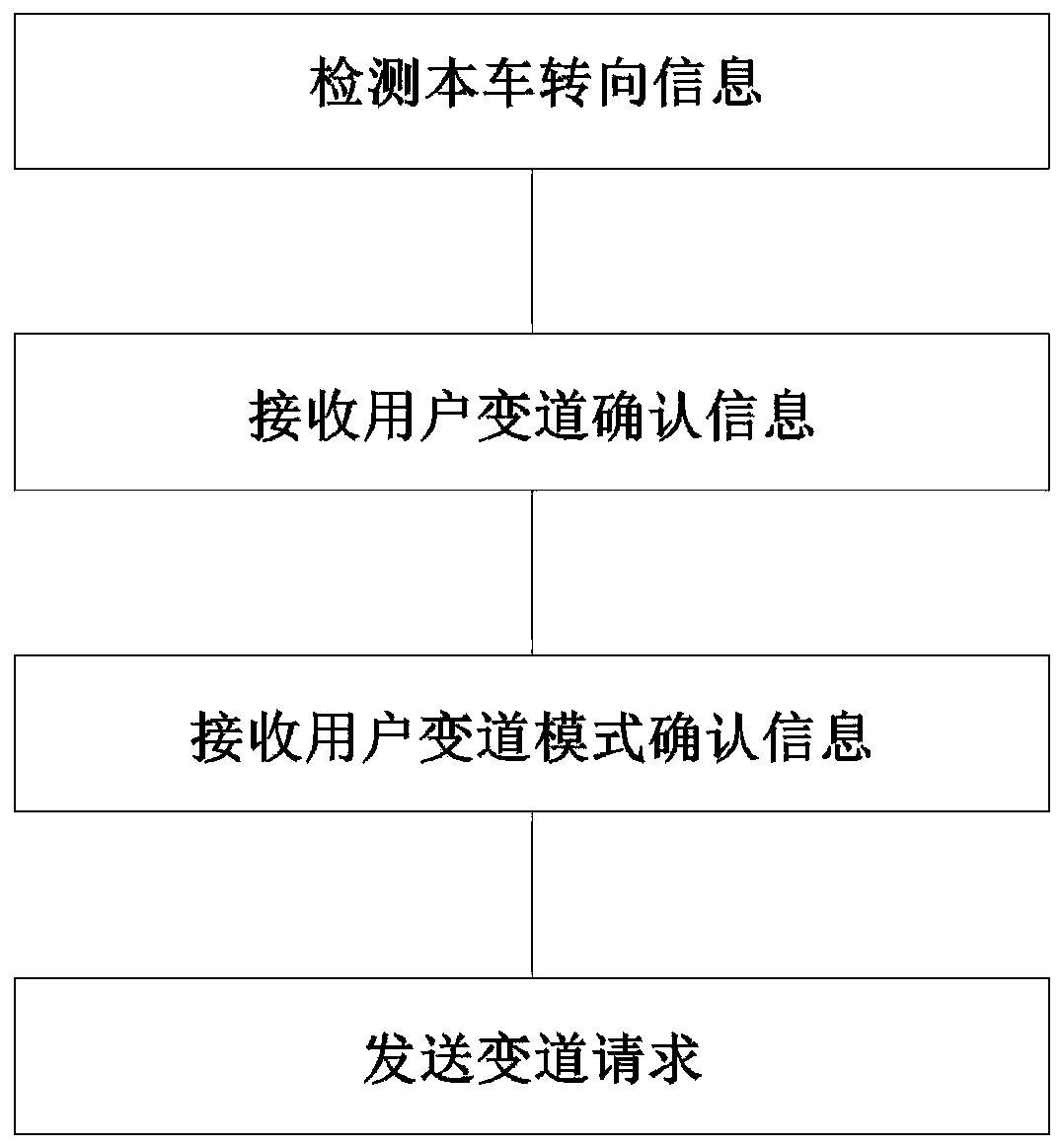
Automatic vehicle lane changing method
ActiveCN110239550AImprove securityImprove driving experienceControl devicesFault toleranceEngineering
The invention discloses an automatic vehicle lane changing method. The automatic vehicle lane changing method includes the steps that user lane change information and lane changing mode confirmation information are received; a preset area of a vehicle is monitored, environmental data around the vehicle is acquired in real time and target vehicles are screened, and environmental data around each target vehicle is acquired; the weight of each target vehicle is calculated to determine whether the vehicle meets the lane changing condition or not; if the lane changing condition is not met, the vehicle is fed back to abandon lane changing; and if the lane changing condition is met, the target vehicle with the smallest weight is selected as a lane changing vehicle, the lane changing path is planned, and the automatic lane change of the vehicle is executed. The automatic vehicle lane changing method can not only screen the lane changed vehicle, complete the lane changing path planning and execute the automatic lane changing, but also can monitor the lane changed vehicle in real time and alert the collision risk and assist the coordinated lane changing of the lane changed vehicle, and the safety of the vehicle lane changing is increased; and the fault tolerance is increased, the risk caused by human error operation is reduced, and the driving experience of a user is improved.
Owner:ZHEJIANG GEELY HOLDING (GROUP) CO LTD +1
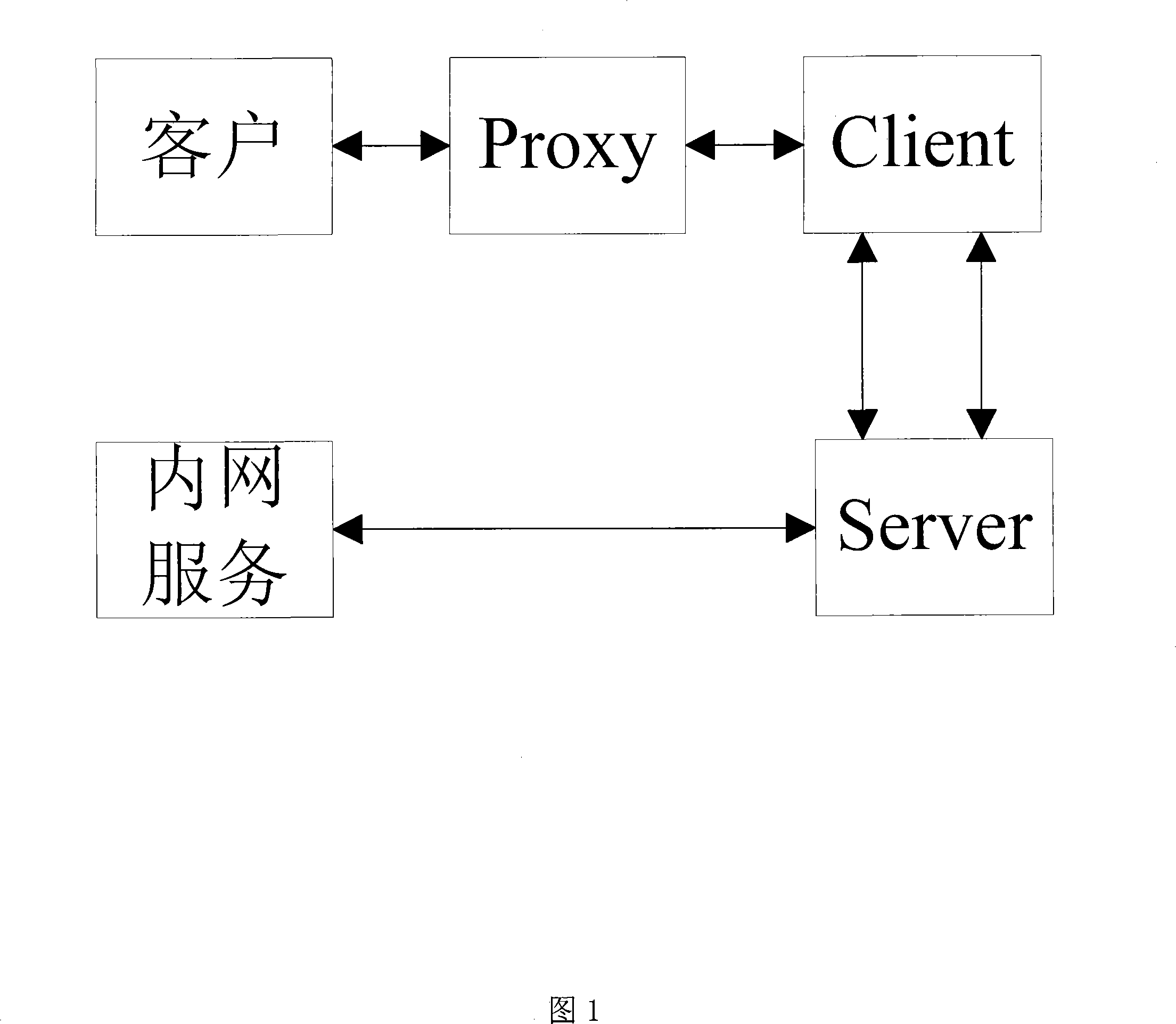
Fire wall/subnet penetration method based on intranet node forwarding technology
InactiveCN101175036ALow costSecurity Services and Data TransmissionData switching networksData transmissionIntranet
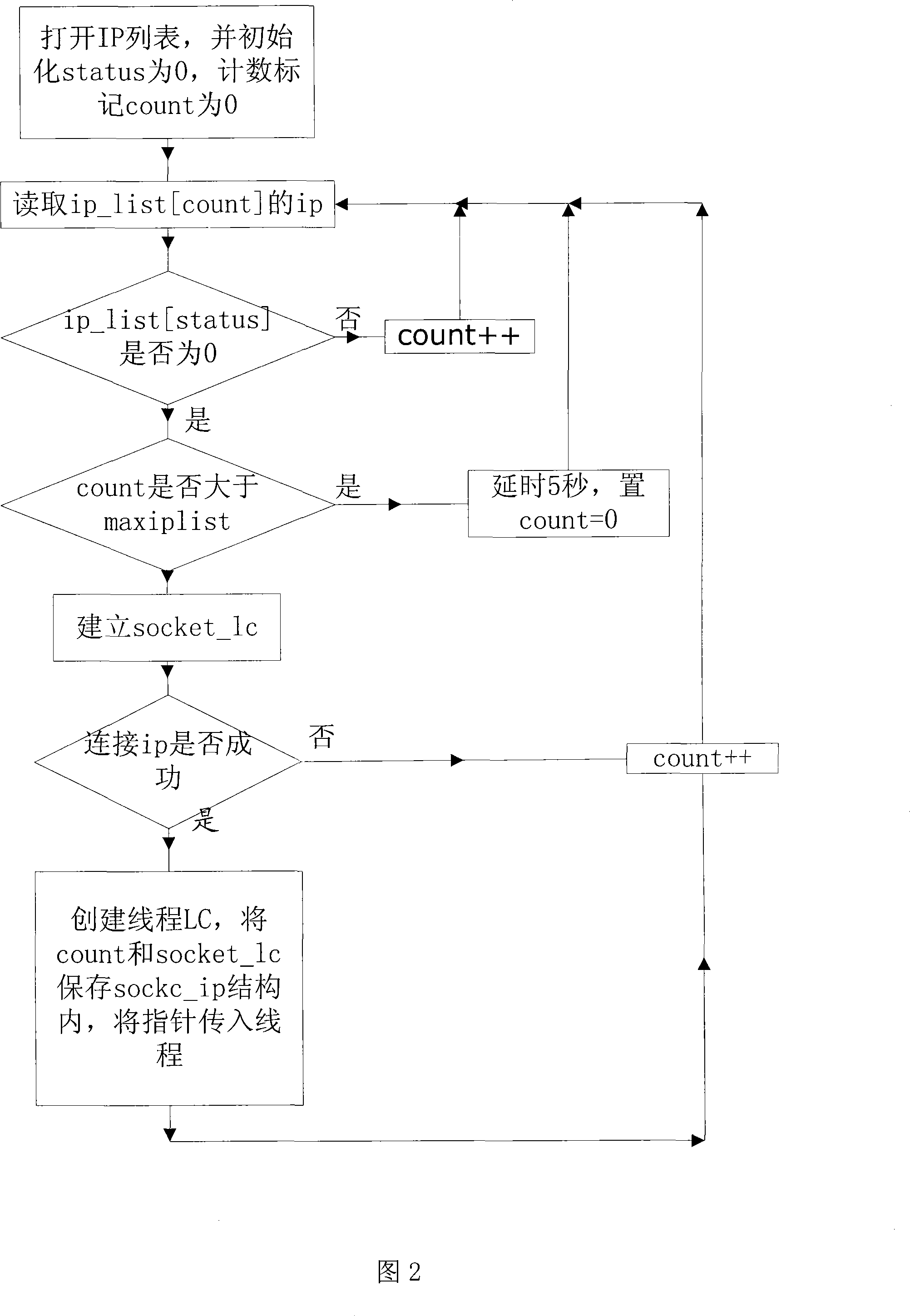
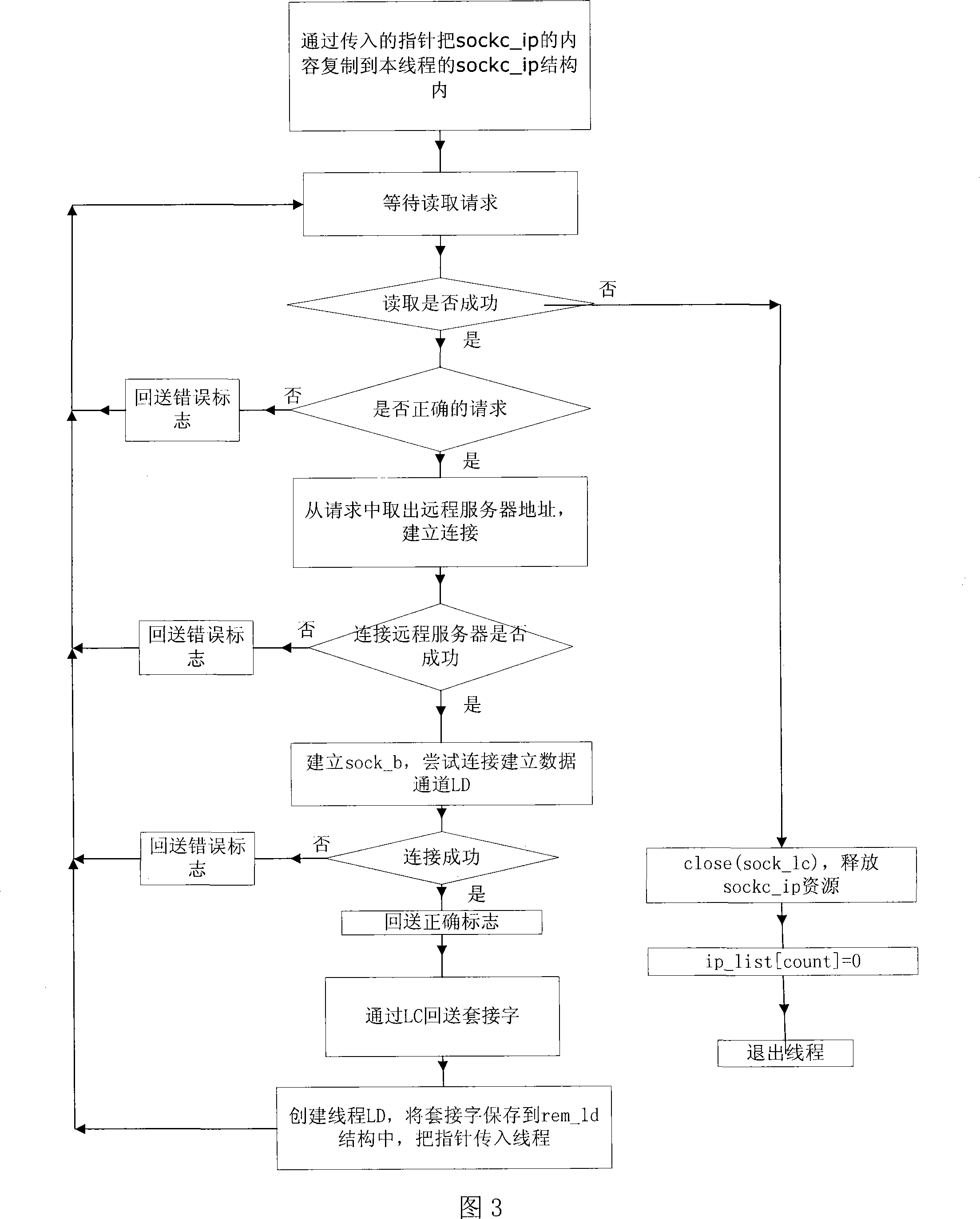
The invention discloses a firewall / subnet penetration method based on intranet node forwarding technology, which includes three modules: Proxy (agent) module, Client (user) module, and Server (server) module. The Proxy module is mainly responsible for collecting user requests and forwarding them to the Client module; the Client module is mainly responsible for establishing a connection with the Server module and forwarding requests from the Proxy module; the Server module is mainly responsible for actively establishing a connection with the Client module, and the processing is performed by The request forwarded by the Client module obtains the corresponding resource and forwards it. The present invention utilizes existing protocols and platforms to effectively reduce the cost of firewall / subnet penetration and can achieve relatively safe service and data transmission.
Owner:NANJING UNIV
Pushing method for express distribution
InactiveCN103995850ASecurity serviceFast and accurate serviceData processing applicationsSpecial data processing applicationsUser needsLogistics management
The invention relates to a pushing method for express distribution. A remote server is arranged, and an express delivery person sends express information of expresses to the remote server, wherein the express information at least comprises express IDs and the locality of the expresses; the remote server counts and processes the information comprising different express companies, express localities and the like according to the received express information; when a user inquires from the remote server, the remote server searches express companies of the localities comprising a receiver address and / or a shipping address in an inquiring request, and the logistics speed of different logistics modes of the express companies within the set date period, comprehensively judges out a rapidest express company meeting the user requirement within the set date period, and pushes the rapidest express company to the user. On the condition of not destroying the current express market pattern and mode, express schemes suitable for specific users can be pushed and sent out through a cloud platform, and the express logistics can provide services for the users more safely, reliably, rapidly and accurately.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
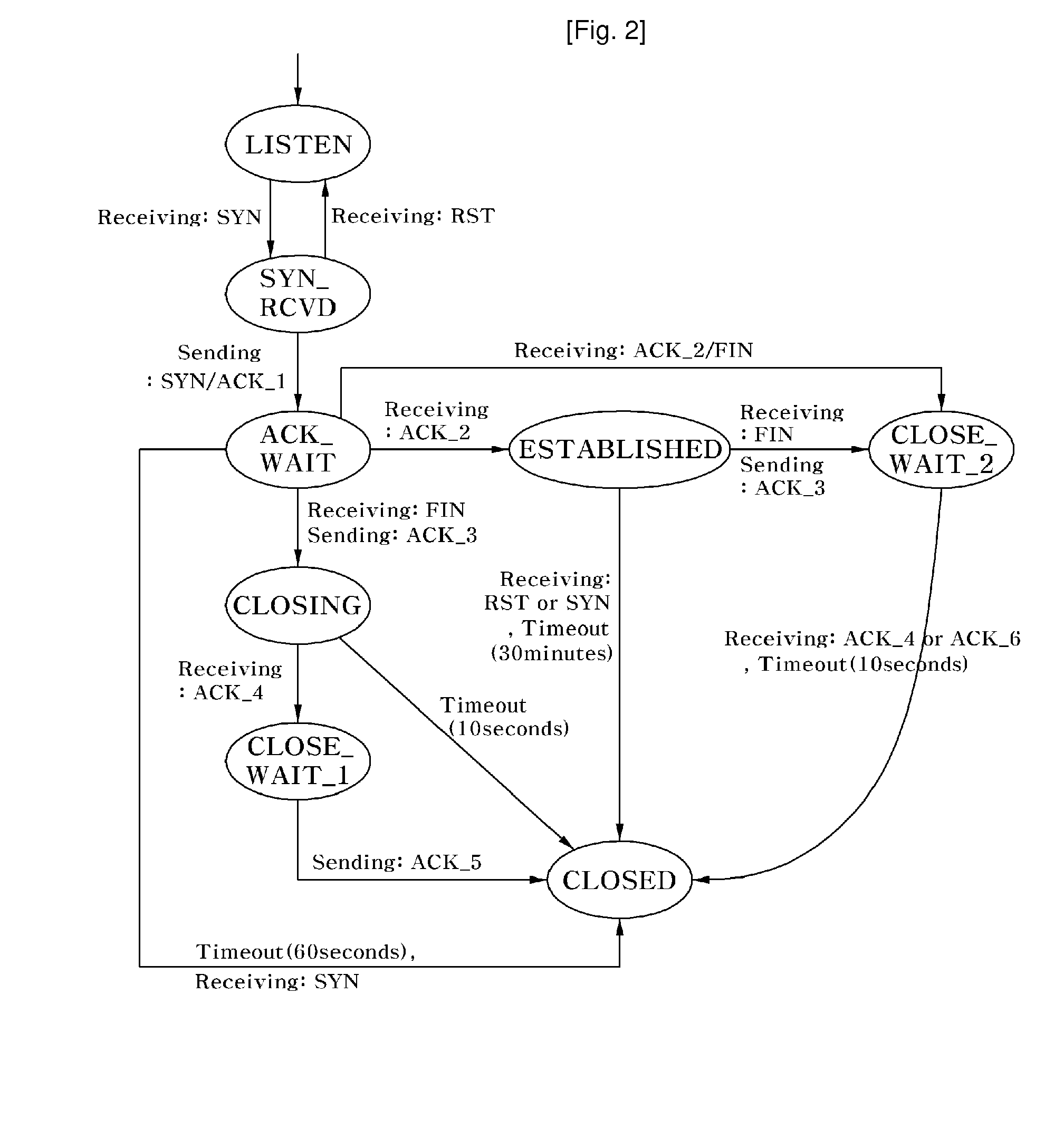
Method for Preventing Denial of Service Attacks Using Transmission Control Protocol State Transition
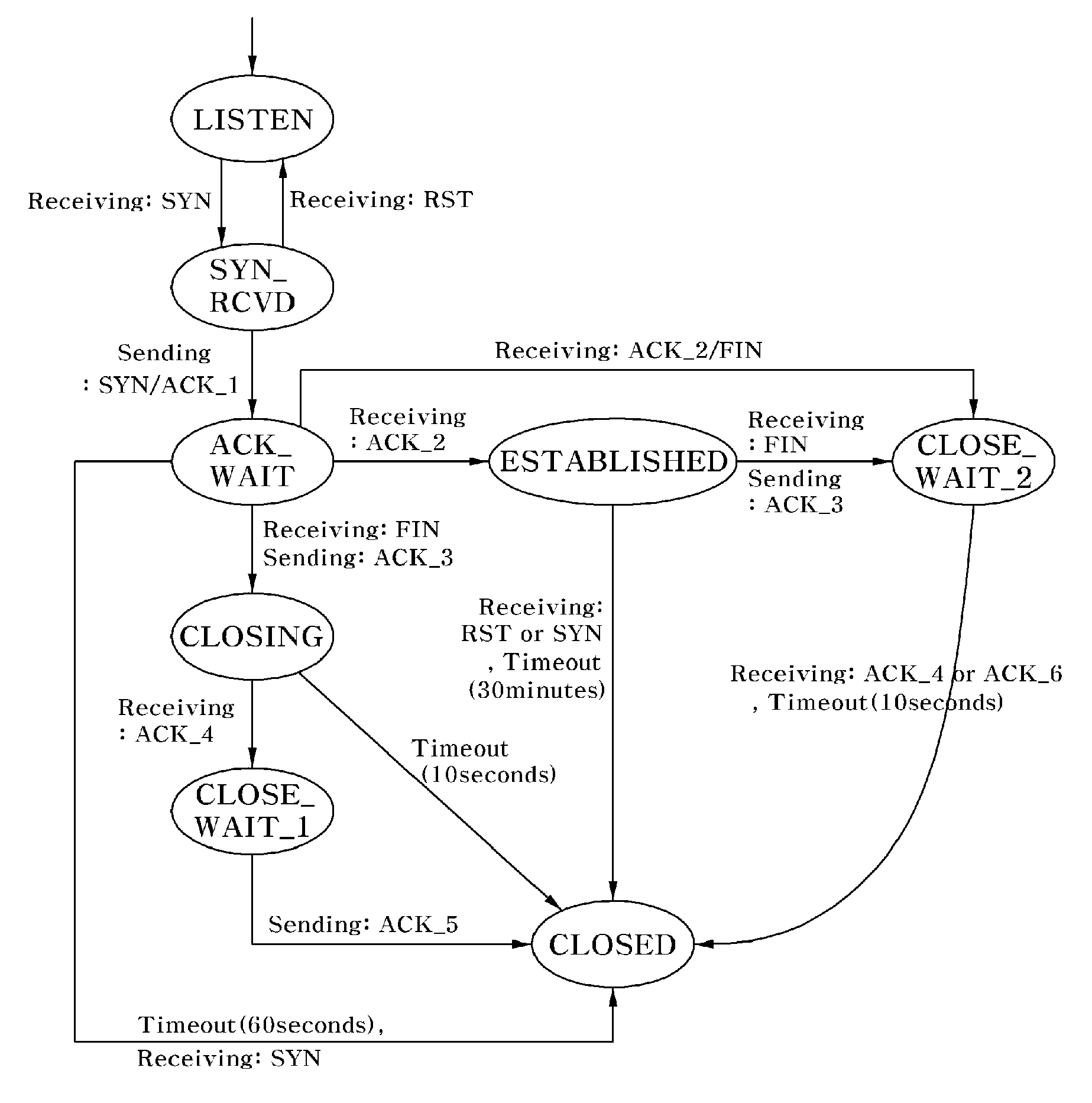
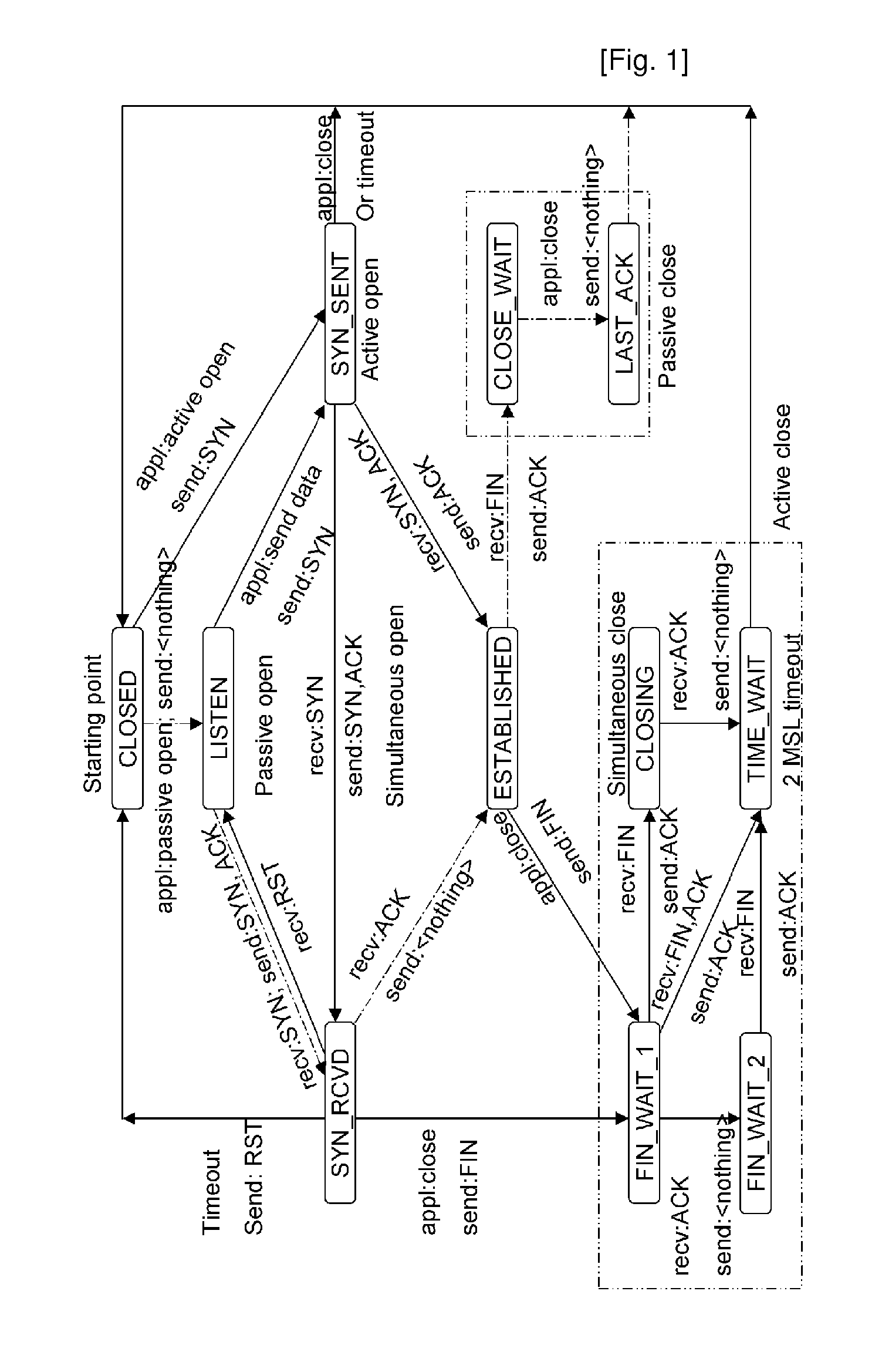
InactiveUS20100088763A1Reduce loadSecurity serviceMemory loss protectionData taking preventionState switchingClient-side
Disclosed is a method of preventing a denial of service (DoS) attack using transmission control protocol (TCP) state transition. Flow of packets transmitted between a client and a server using TCP is monitored to prevent the DoS attack, e.g., SYN flooding, and to efficiently reduce the load on the server and provide mor secure service. By applying the method to a firewall, a proxy server, an intrusion detection system, etc., of a server, it is possible to make up for vulnerabilities regarding a DoS attack without disturbing a conventional TCP state transition operation and detect, verify and block DoS attacks abusing the vulnerabilities, thereby providing more secure service.
Owner:SAMSUNG SDS CO LTD
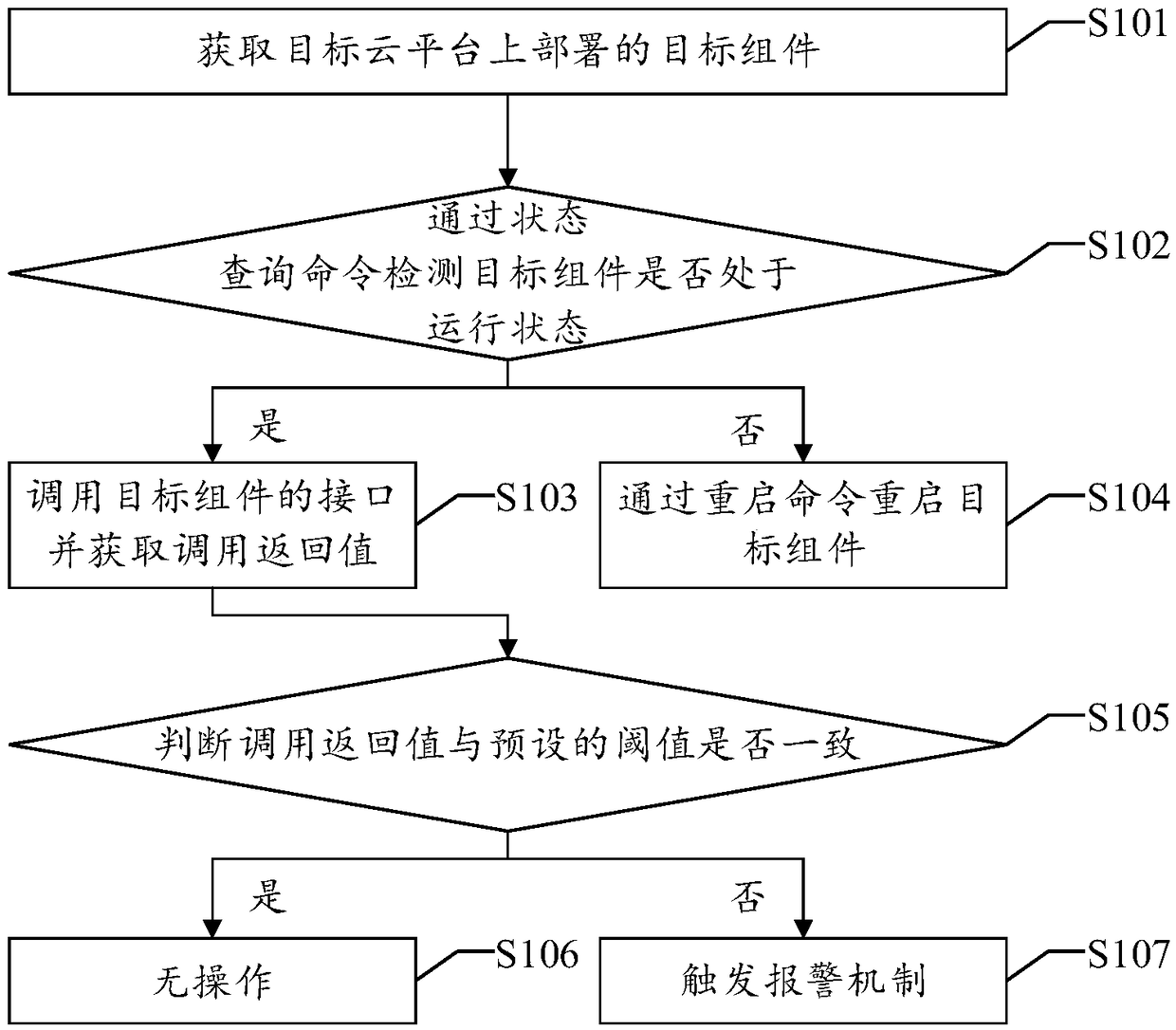
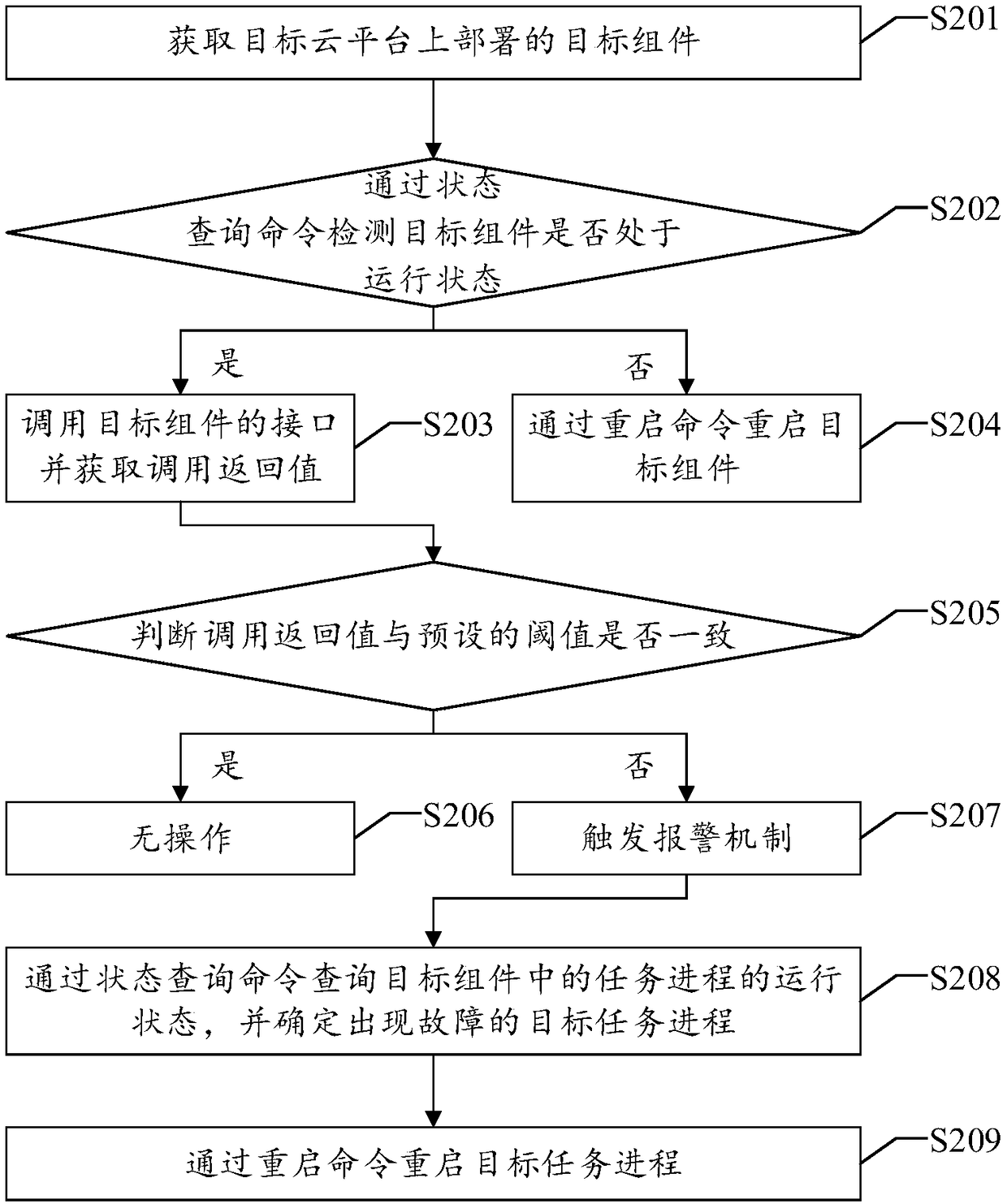
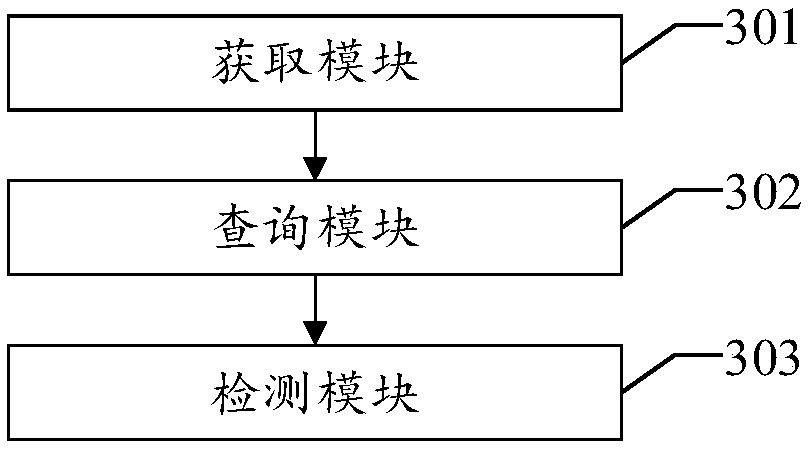
A fault detection method and a device of a cloud platform
The invention discloses a fault detection method of a cloud platform, which comprises the following steps: acquiring target components deployed on a target cloud platform; detecting whether a target component is in a running state by a status query command; if yes, the interface of the target component is called and the call return value is obtained;. when the call return value is inconsistent with the preset threshold value, trigging the alarm mechanism, so that the failure of the cloud platform can be repaired in time. At the same time, since the method monitors all components deployed on the cloud platform, the burden of the cloud platform and the workload of the developers can be reduced, and the influence of the monitoring process on the cloud platform services can be reduced, so thatthe method can provide safe and stable cloud services for users and improve the user experience. Accordingly, the invention discloses a fault detection device, a device and a computer-readable storage medium of a cloud platform, which also have the technical effects mentioned above.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Distributed file transmission service method
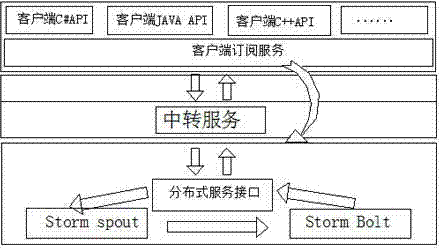
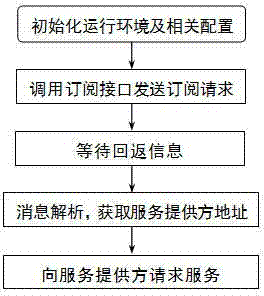
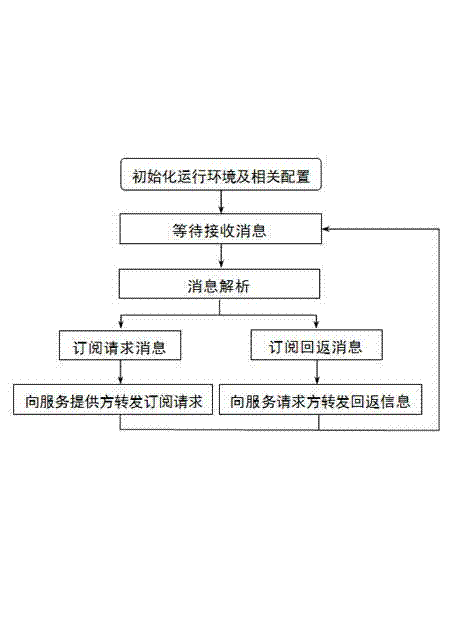
ActiveCN104243610ASolve simultaneous uploadSolve efficiency problemsTransmissionSERCOS interfaceFile transmission
The invention provides a distributed file transmission service method which is used for single or batch uploading and downloading services and aims to solve the bottlenecks of file transmission services in terms of concurrent transmission and transmission efficiency. The method includes: (1) a client application interface; (2), a server transfer service; (3) a server distributed file processing service. The method has the advantages that the concurrent quantity and service efficiency bottlenecks during simultaneous uploading and downloading of large-batch files can be effectively solved; the subscribing service interface and a unified transfer service interface are used, the defect of file transmission service failure due to the fact that communication port number cannot be displayed and acquired under some special application environments is overcome, and services can be performed safely and effectively.
Owner:INSPUR SOFTWARE CO LTD
Wireless humiture sensor network structure based on zigbee
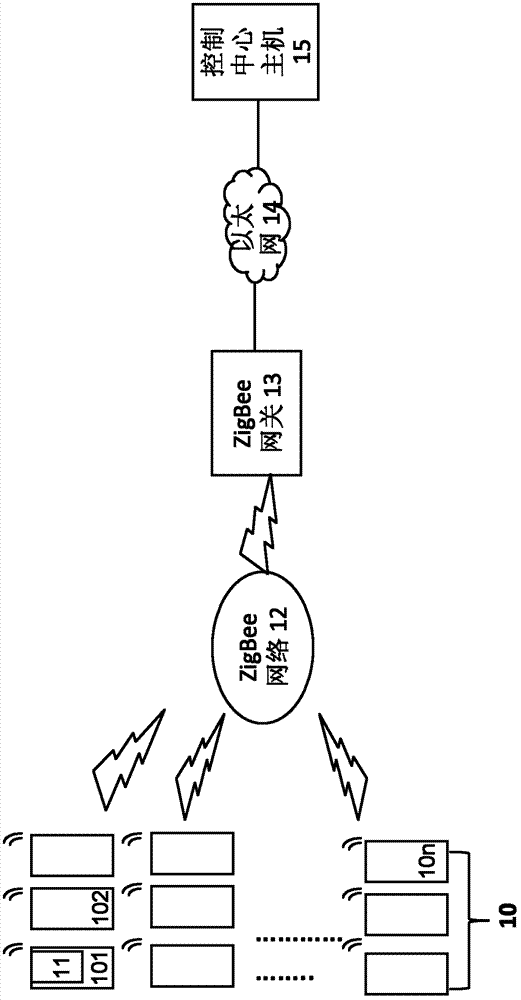
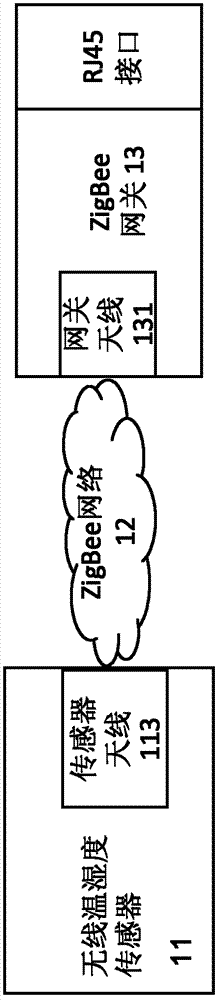
InactiveCN103369719ASecurity serviceGuaranteed safe operationNetwork topologiesEthernet protocolNetwork structure
The invention provides a wireless humiture sensor network structure based on a zigbee, relates to the wireless humiture sensor technology, and solves the problem that the security of running devices in a cabinet of a machine room is not guaranteed. The structure comprises a plurality of wireless humiture sensors based on the zigbee which are distributed in each cabinet of the machine room, a ZigBee wireless gateway, and a control center host. The wireless humiture sensors collect a humiture signal in the cabinet, preprocess the signal into humiture data in a ZigBee protocol format, and transmit the humiture data; the ZigBee wireless gateway receives, through a ZigBee network, the humiture data in the ZigBee protocol format transmitted by the wireless humiture sensors, and transforms the humiture data in the ZigBee protocol format into the humiture data in an Ethernet protocol format; and the control center host, through an Ethernet telecommunication transmission, receives the humiture data in the Ethernet protocol format transmitted by the ZigBee gateway, and displays the humiture data in a real time manner. The sensor network structure can display the humiture in the cabinet in the control center host in the real time manner, so as to ensure the safe operation of devices in the cabinet.
Owner:上海宽岱电讯科技发展有限公司
Software authorization permission method and device and electronic device
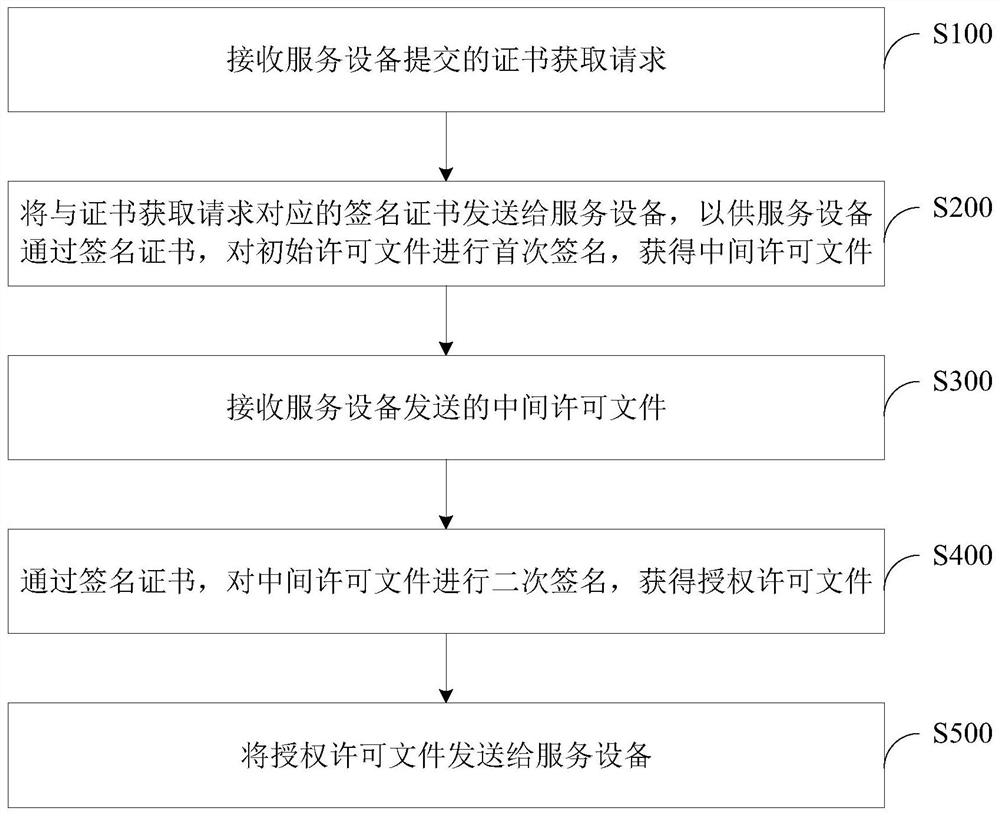
PendingCN112115425AImprove securitySecurity serviceProgram/content distribution protectionEngineeringComputer software
The invention relates to the technical field of computer software, in particular to a software authorization permission method and device and an electronic device. The software authorization permission method provided by the embodiment of the invention is applied to authorization management equipment, and comprises the following steps: receiving a certificate acquisition request submitted by service equipment; sending a signature certificate corresponding to the certificate acquisition request to the service equipment, so that the service equipment signs the initial permission file for the first time through the signature certificate to obtain an intermediate permission file; receiving an intermediate permission file sent by the service equipment; performing secondary signature on the intermediate license file through the signature certificate to obtain an authorization license file; and sending the authorization permission file to the service equipment. According to the software authorization permission method and device and the electronic device provided by the embodiment of the invention, safe and reliable software service can be realized.
Owner:北京指掌易科技有限公司
Method and system for implementing internet of things service
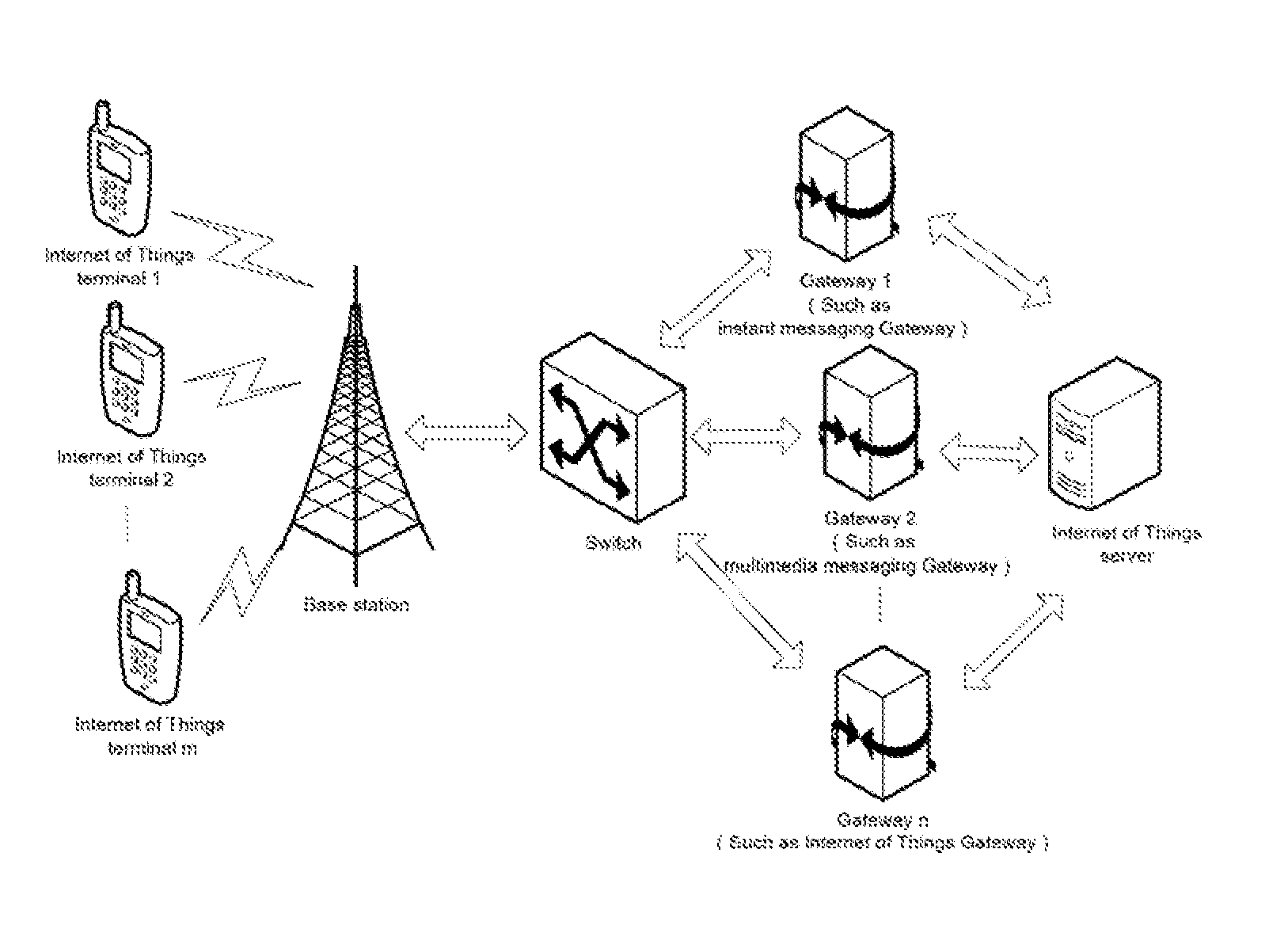
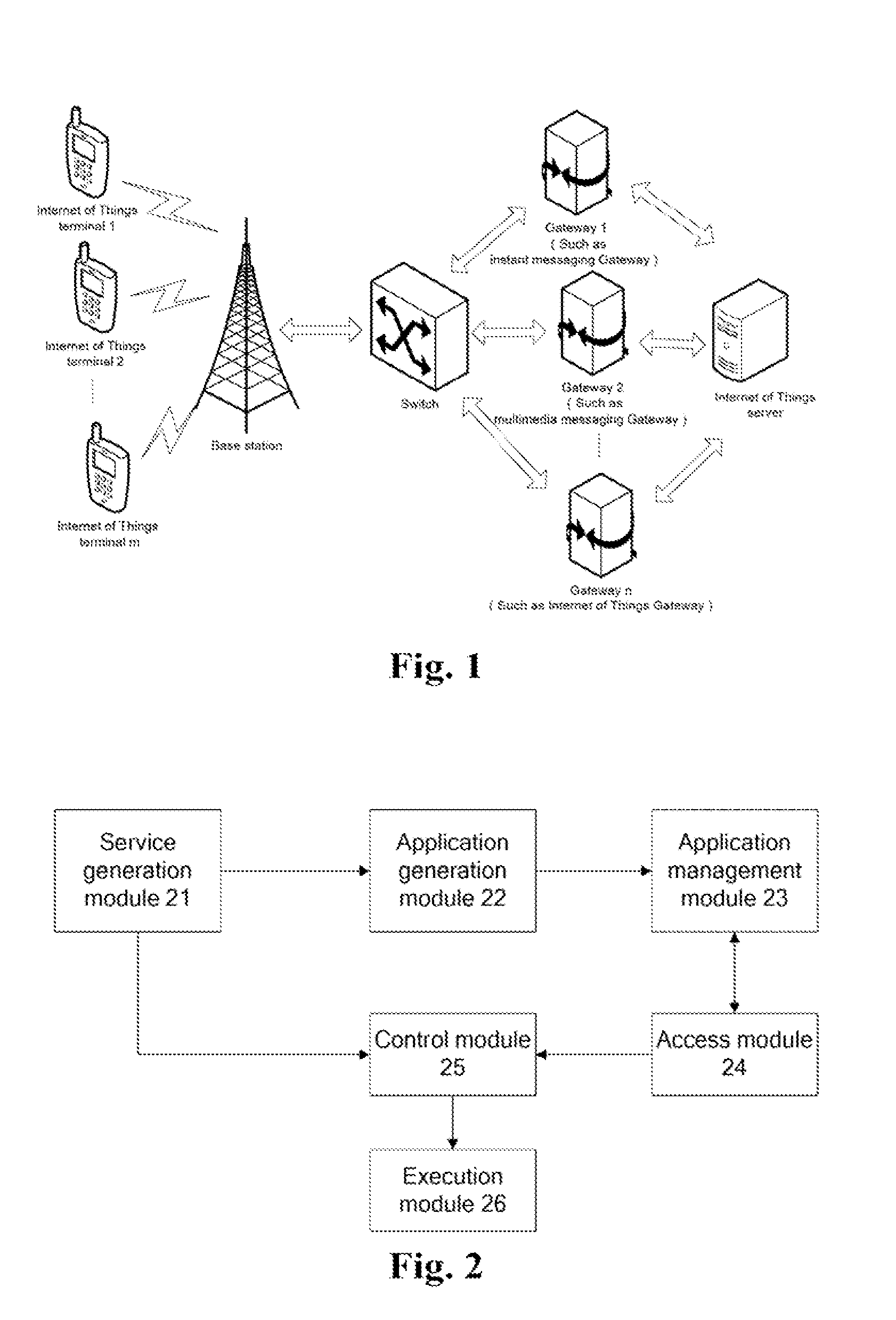
ActiveUS9071657B2Comprehensive Internet of Things serviceSecurity serviceService provisioningMultiple digital computer combinationsThe InternetComputer terminal
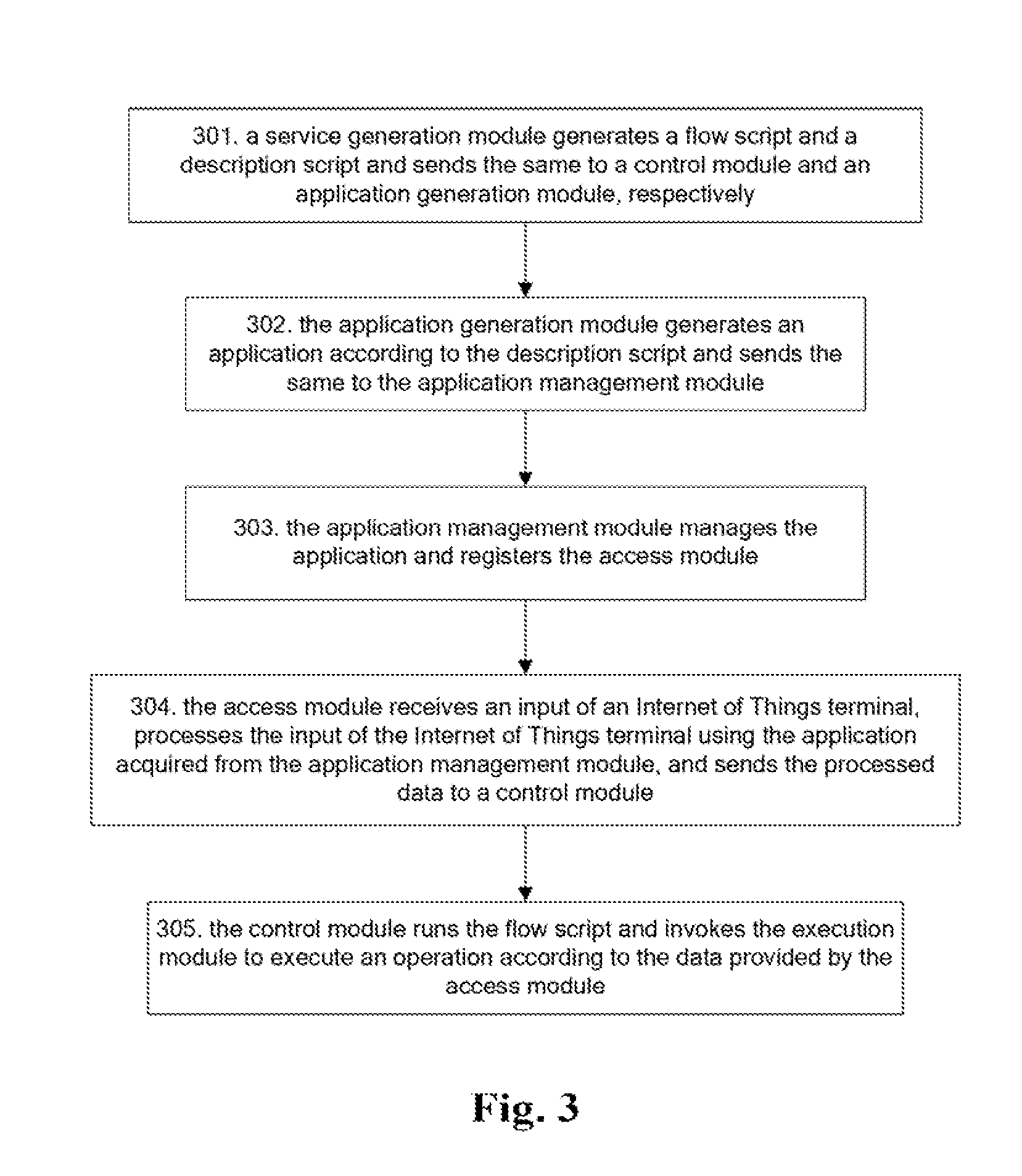
Disclosed in the present invention are a method and system for implementing an Internet of Things service. In the present invention: a service generation module generates a description script and a flow script according to a required service, sends the description script and the flow script to an application generation module and a control module, respectively; the application generation module generates an application according to the description script and sends the same to an access module; the access module receives an input of an Internet of Things terminal, processes the input of the Internet of Things terminal using the application, and sends the processed data to a control module; the control module runs the flow script and invokes an execution module to execute an operation according to the data sent by an access module; and the execution module executes an operation according to the invocation of the control module.
Owner:ZTE CORP
Trip manifold
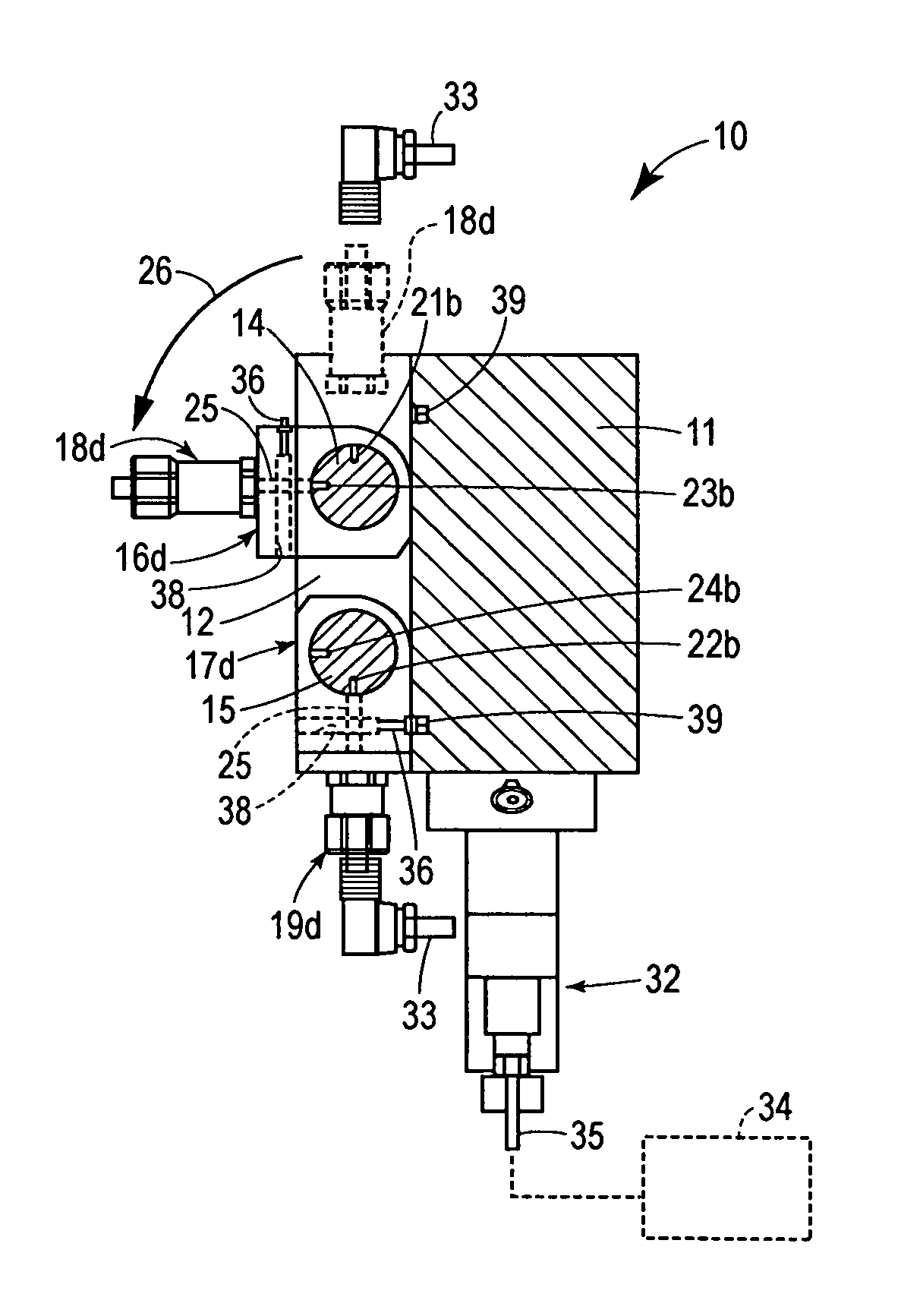
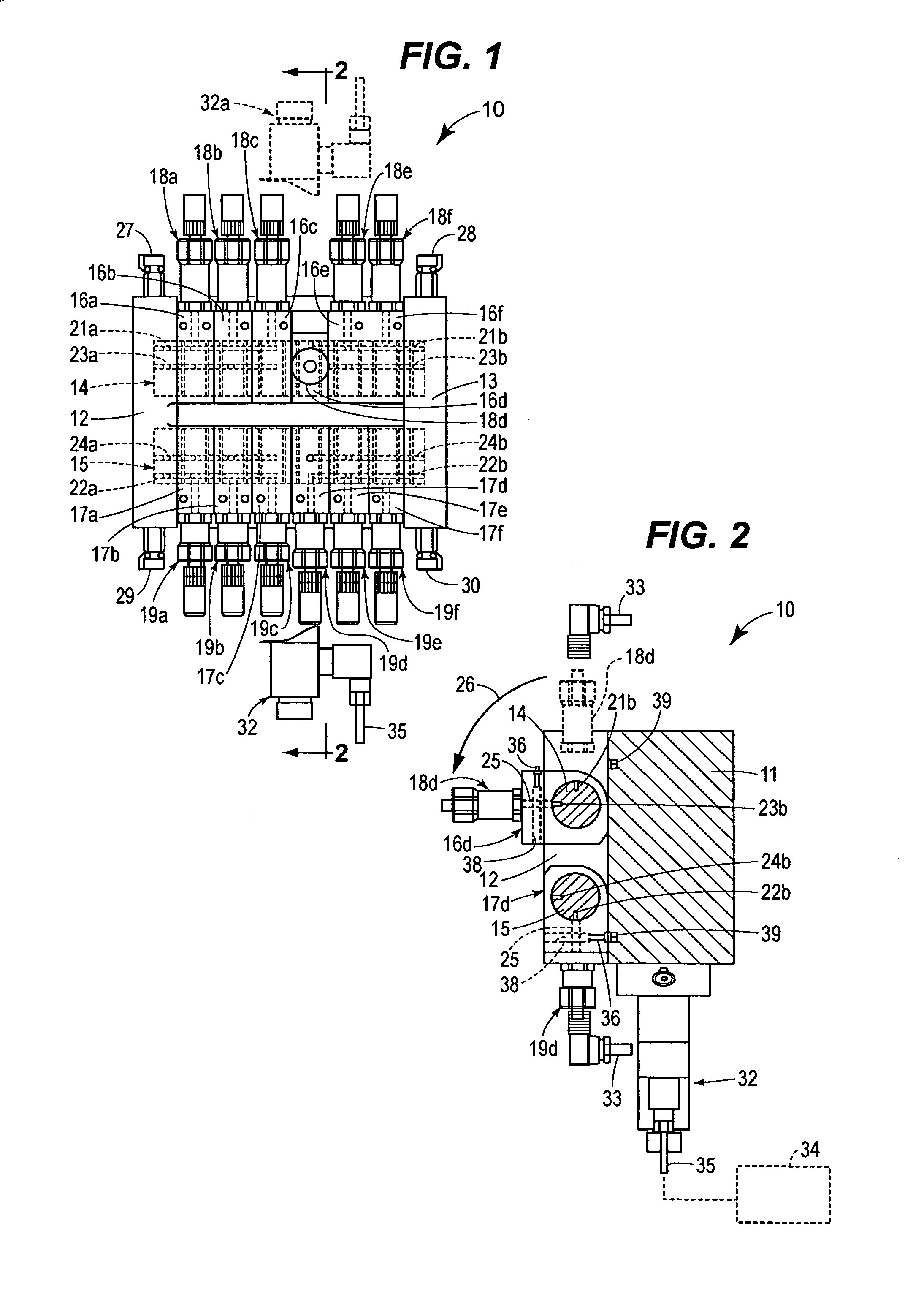
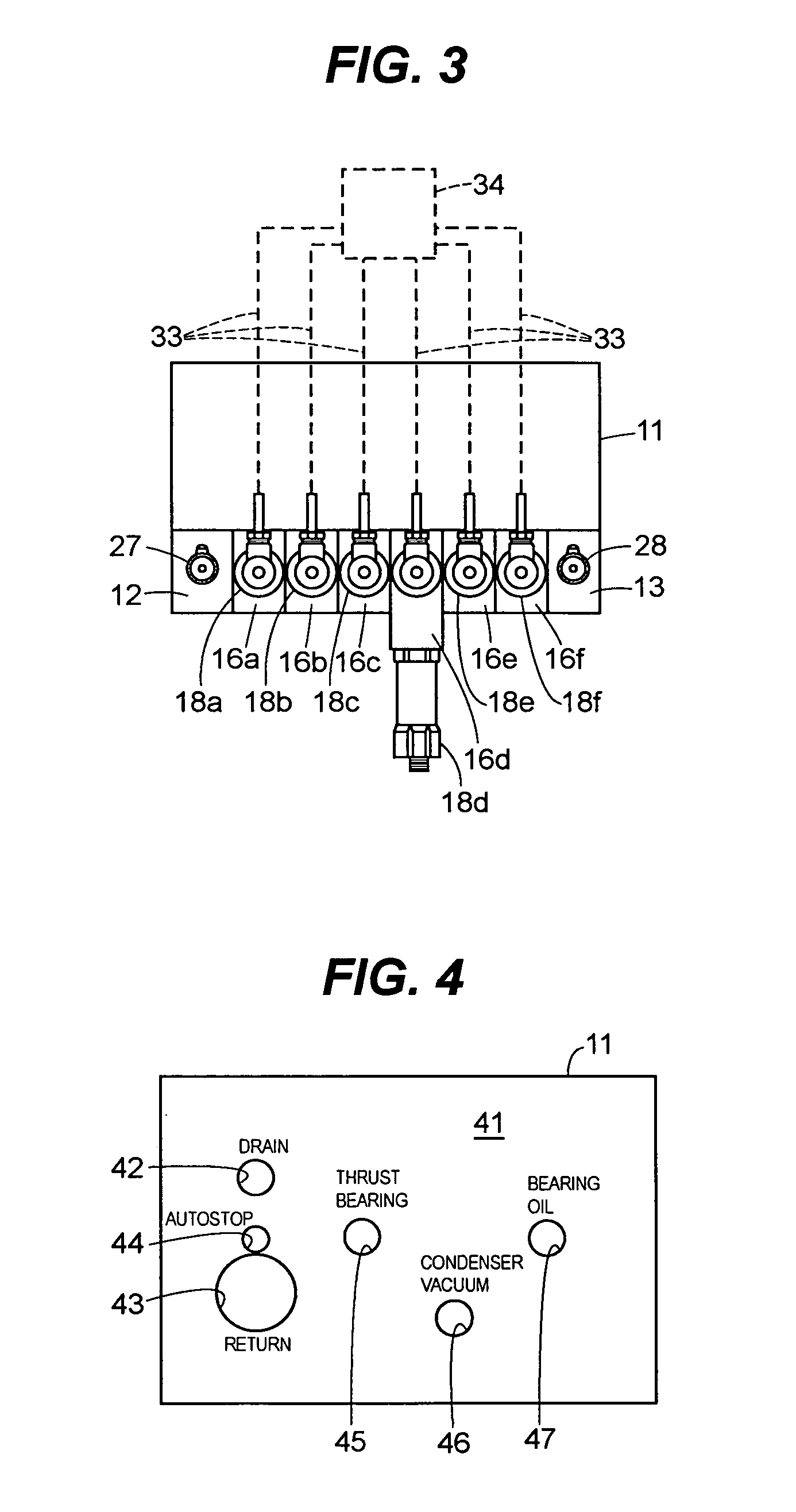
ActiveUS7137407B2Maintenance safetySafe removalWind motor controlServomotor componentsRotary valveEngineering
A trip manifold assembly is disclosed which includes a manifold body connected to a header shaft. The header shaft passes through a plurality of rotary valves. Each rotary valve is connected to a pressure transmitter. The header shaft comprises two passages including a transmitter input passage and a drain passage. The rotary valves each comprise a through passage. A manifold body provides fluid communication between an input source and the transmitter input passage of the header shaft. The manifold also provides communication between the drain passage of the header shaft and a drain vent. The rotary valves are each independently rotatable between two positions including a transmit position where the through passage of each valve provides communication between the transmitter input passage of the header shaft and their respective pressure transmitters. Each rotary valve is also independent rotatable to a drain position where the through passage of each valve is in communication with the drain passage of the header shaft. Multiple header shafts may be provided in a single manifold assembly and each header shaft can handle more than one input that needs to be monitored.
Owner:EMERSON PROCESS MANAGEMENT POWER & WATER SOLUTIONS
Intelligent guide method and device for movie theater audiences
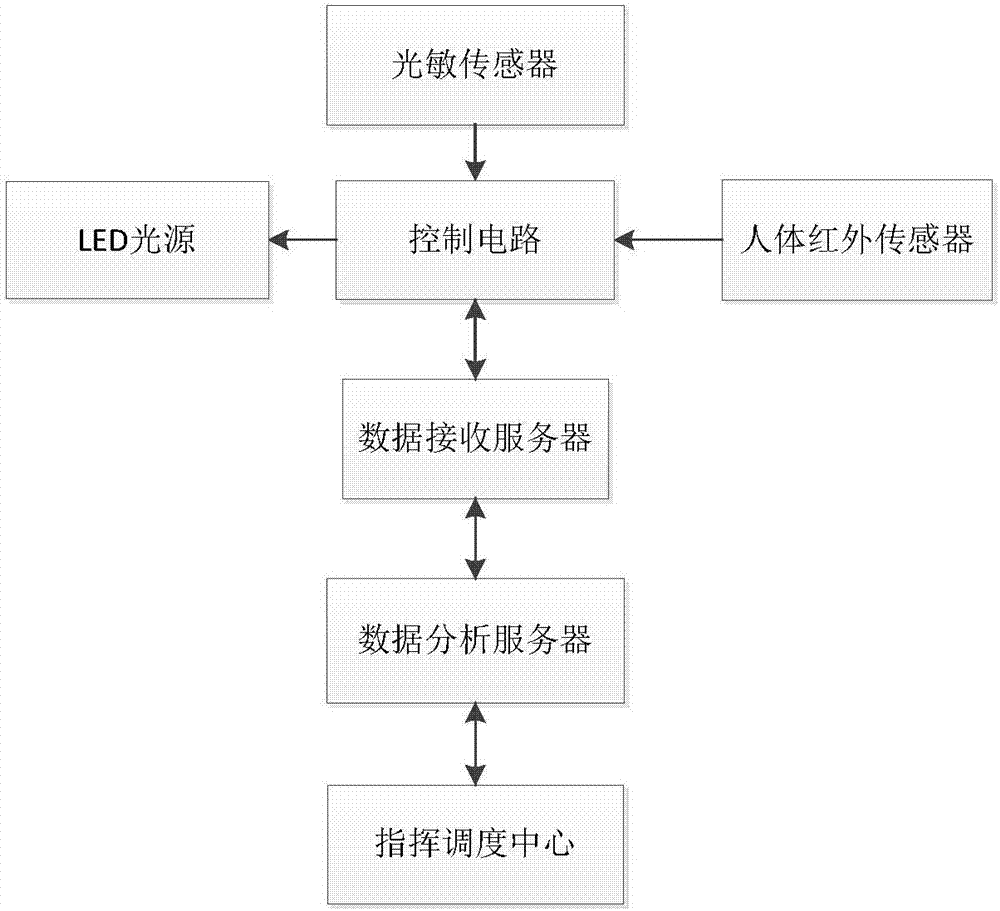
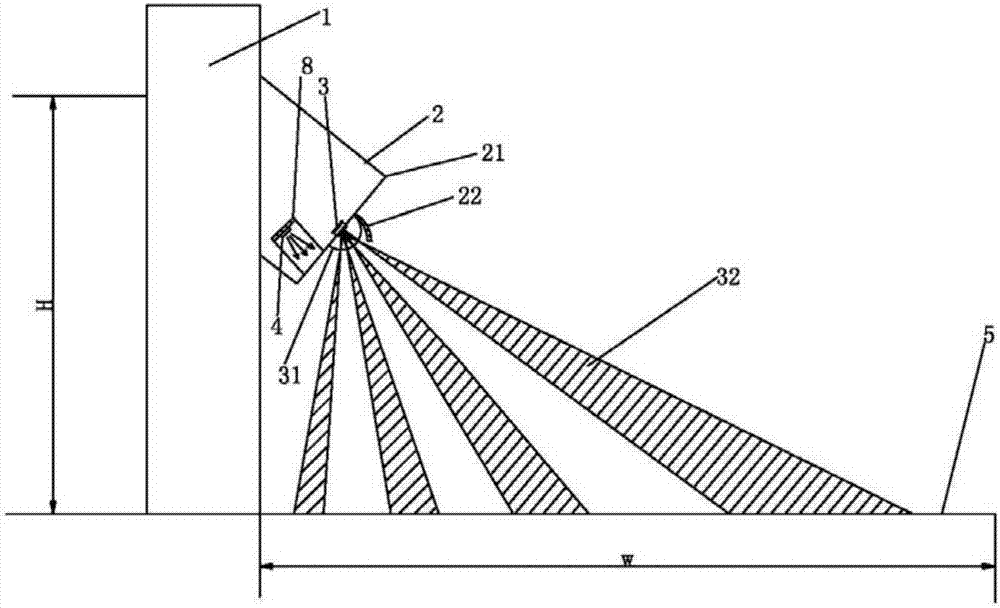
PendingCN106931363APrevent steppingAvoid panicElectrical apparatusElectric circuit arrangementsElectricityEngineering
The invention discloses an intelligent guide method for movie theater audiences. The method comprises the following steps that 1, an LED floor lamp is arranged; 2, the floor lamp is arranged on a seat on one side of a longitudinal channel of a movie theater studio; 3, LED light sources and pyroelectric human infrared sensors are obliquely arranged towards the channel ground, and light rays emitted by the LED light sources irradiate into the channel; 4, when audiences pass through sensing areas of the pyroelectric human infrared sensors, the sensors are triggered to give electric pulse signals and carry out counting, the LED light sources are turned on through control circuits to project light rays to the faced channel ground, audiences can see channel ground conditions, characters or marks, step missing, fettering and crowding are avoided, and audients are guided to accurately and rapidly find specific seats; and 5, after audients leave the sensing areas, the LED light sources are gradually turned off. The invention further provides an intelligent guide device implementing the intelligent guide method for movie theater audiences. The intelligent guide method and device can be widely applied to intelligent management of movie theaters.
Owner:广州尚牛设计有限公司
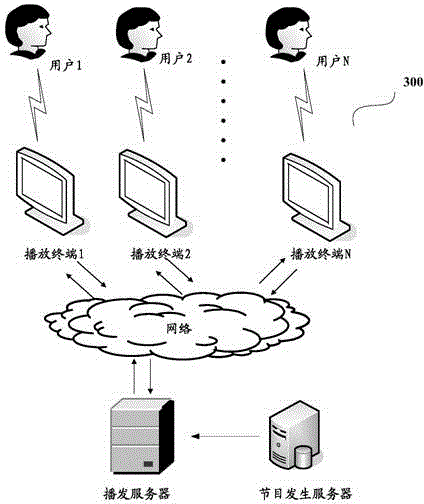
Program play method and related device and system
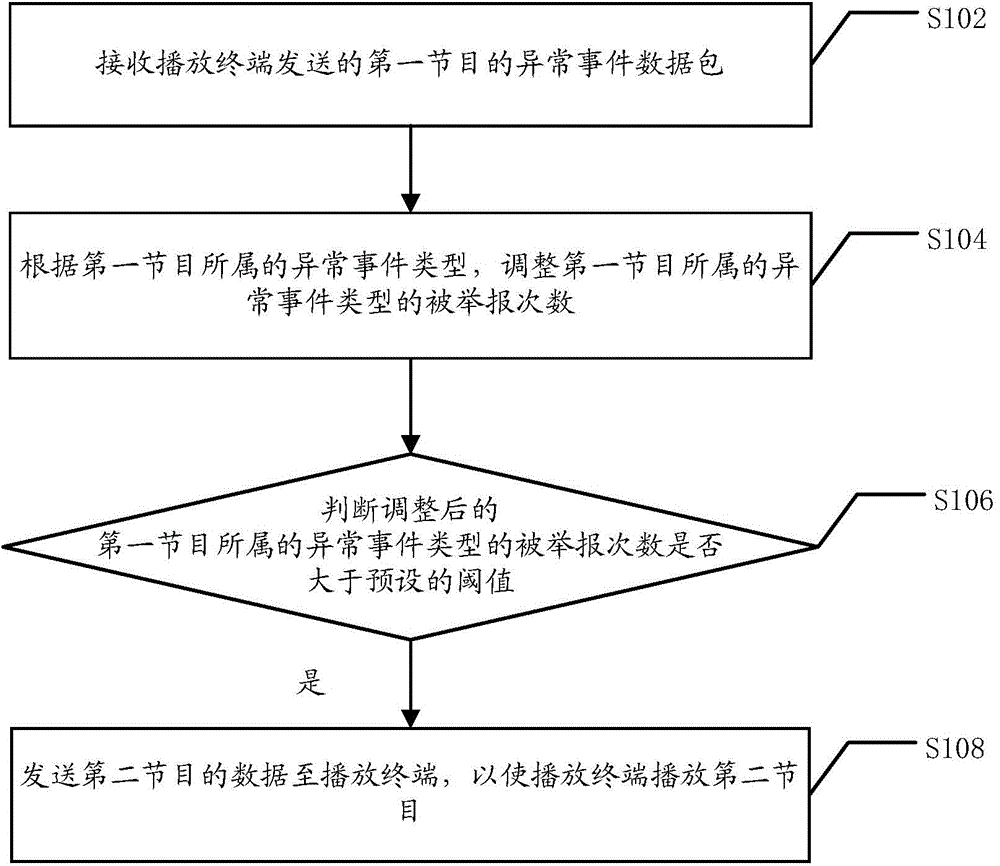
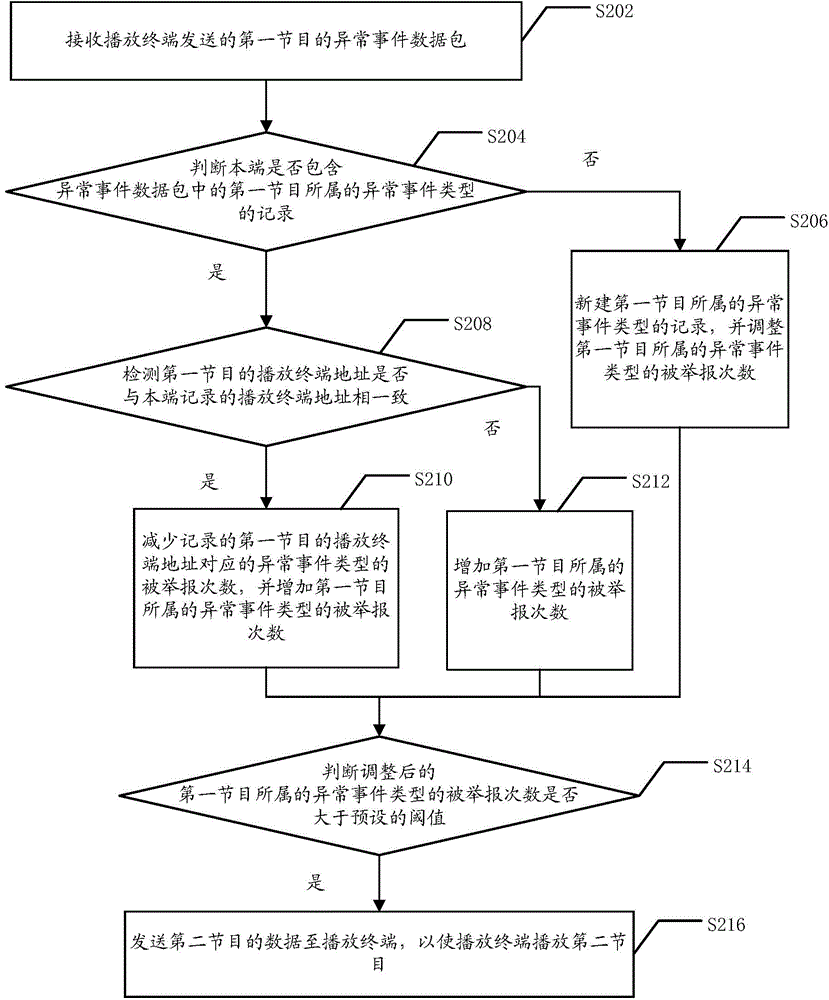
InactiveCN104618787AImplement playback controlImprove experienceSelective content distributionEvent typeNetwork packet
The invention discloses a program play method and a related device and system. The program play method provided by the embodiment of the invention comprises the following steps: receiving an abnormal event data packet of a first program transmitted by a playing terminal, wherein the abnormal event data packet comprises information on abnormal event type, to which the first program belongs, reported when a user watches the first program played by the playing terminal; adjusting the report frequency of the abnormal event type, to which the first program belongs, according to the abnormal event type to which the first program belongs; judging whether the adjusted report frequency of the abnormal event type, to which the first program belongs, is greater than a preset threshold value; when the judgment result is yes, transmitting data of a second program to the playing terminal to play the second program by the playing terminal. By using the method and the system, the user judges and reports abnormal programs according to the played programs, the information on the abnormal programs reported by the user is transmitted to a play server by the playing terminal, and play control over the programs is realized by the play server according to the preset threshold value of the report frequency.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
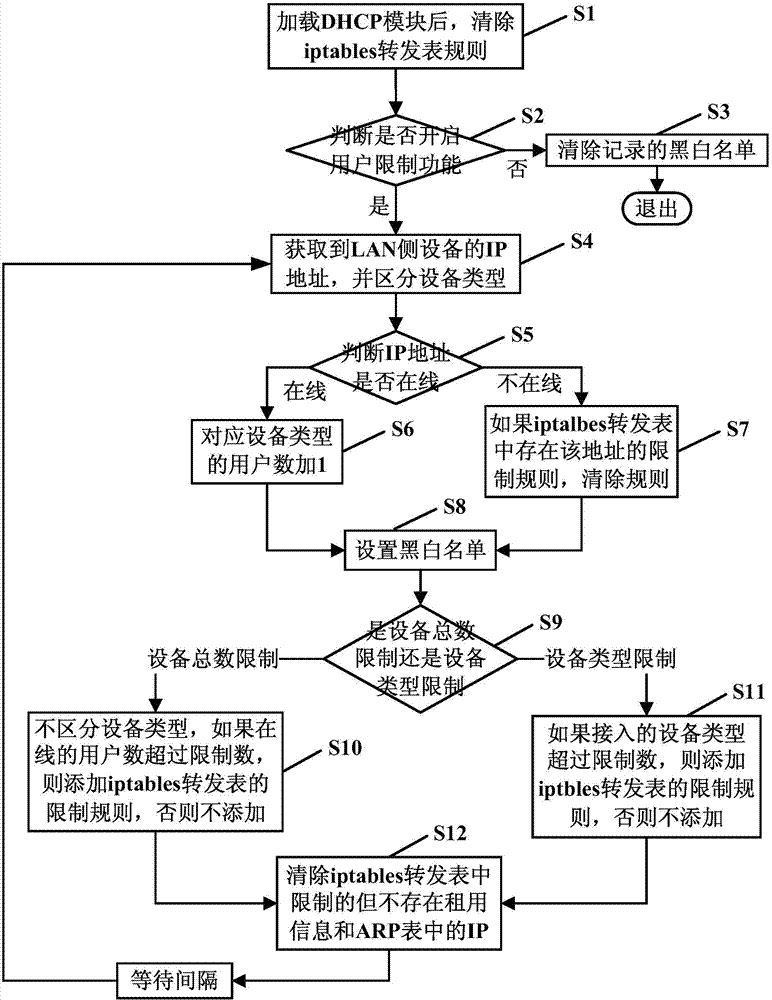
System and method of implementing limitation of public network access user number based on Linux for CPE (Customer Premise Equipment)
ActiveCN104270325AA large amountSatisfy the requirements of simultaneous access to the public networkData switching networksDevice typeGNU/Linux
The invention discloses a system and a method of implementing limitation of a public network access user number based on a Linux for CPE (Customer Premise Equipment), relating to the field of CPE equipment. The system comprises a DHCP (Dynamic Host Configuration Protocol) module and a public network user access number limiting module, wherein when the DHCP module checks status information of equipment at a LAN (Local Area Network) side at each time, an iptables forwarding table rule is eliminated, and the previous check information is eliminated, so that the current result is taken as a standard at each check; the public network user access number limiting module is used for eliminating recorded blacklist and whitelist and un-limiting the public network user access number if a public network user access number limiting function is closed, and obtaining an IP (Internet Protocol) address of the equipment at the LAN side, carrying out terminal identification through DHCP Option60 and distinguishing the equipment type if the public network user access number limiting function is opened. According to the system and the method, the maximum quantity for synchronous access of the public network can be limited, individual limitation of the public network access number can be carried out on each terminal type, and a function of individual limitation of the public network access number is enriched.
Owner:FENGHUO COMM SCI & TECH CO LTD
Automatically switched optical network evolution system and method
InactiveCN104113791ASimple serviceEfficient serviceMultiplex system selection arrangementsTransmissionAutomatically switched optical networkSoftware define network
The invention discloses an automatically switched optical network evolution system and method and belongs to the automatically switched optical network field. The method includes the following steps that: a thin client end arranged in a network element initiates an application request to an application end arranged in a software defined network (SDN); the application end performs computation on the application request, and sends a processing result to the thin client end; and the thin client end translates the processing result into an instruction which can be executed by the network element, so that corresponding operation can be performed. The invention also discloses the automatically switched optical network evolution system. The automatically switched optical network evolution system and method of the invention can provide simple, efficient and safe services for users by means of an SDN architecture and a cloud computing platform.
Owner:ZTE CORP
Ethernet paying business hall system
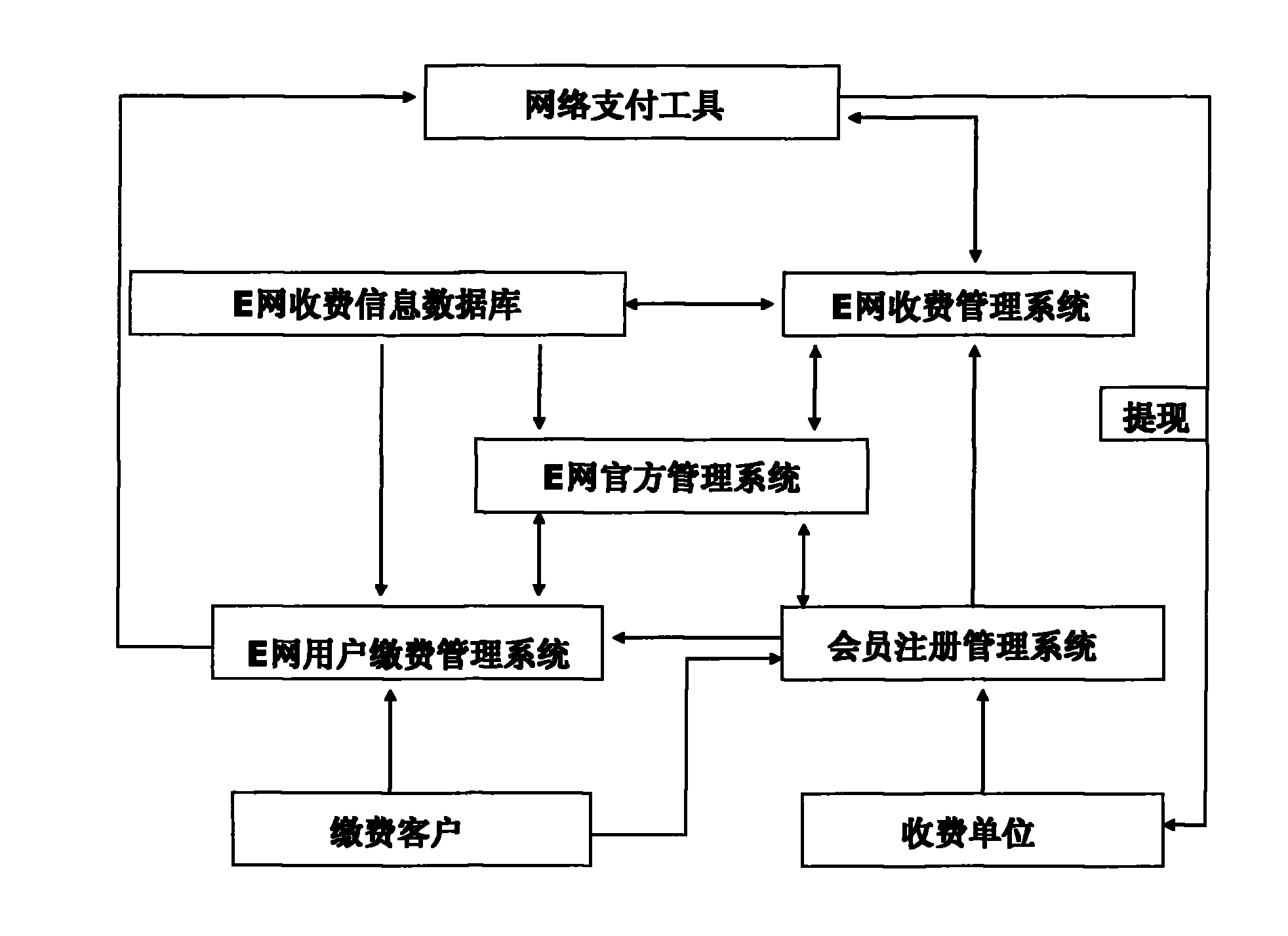
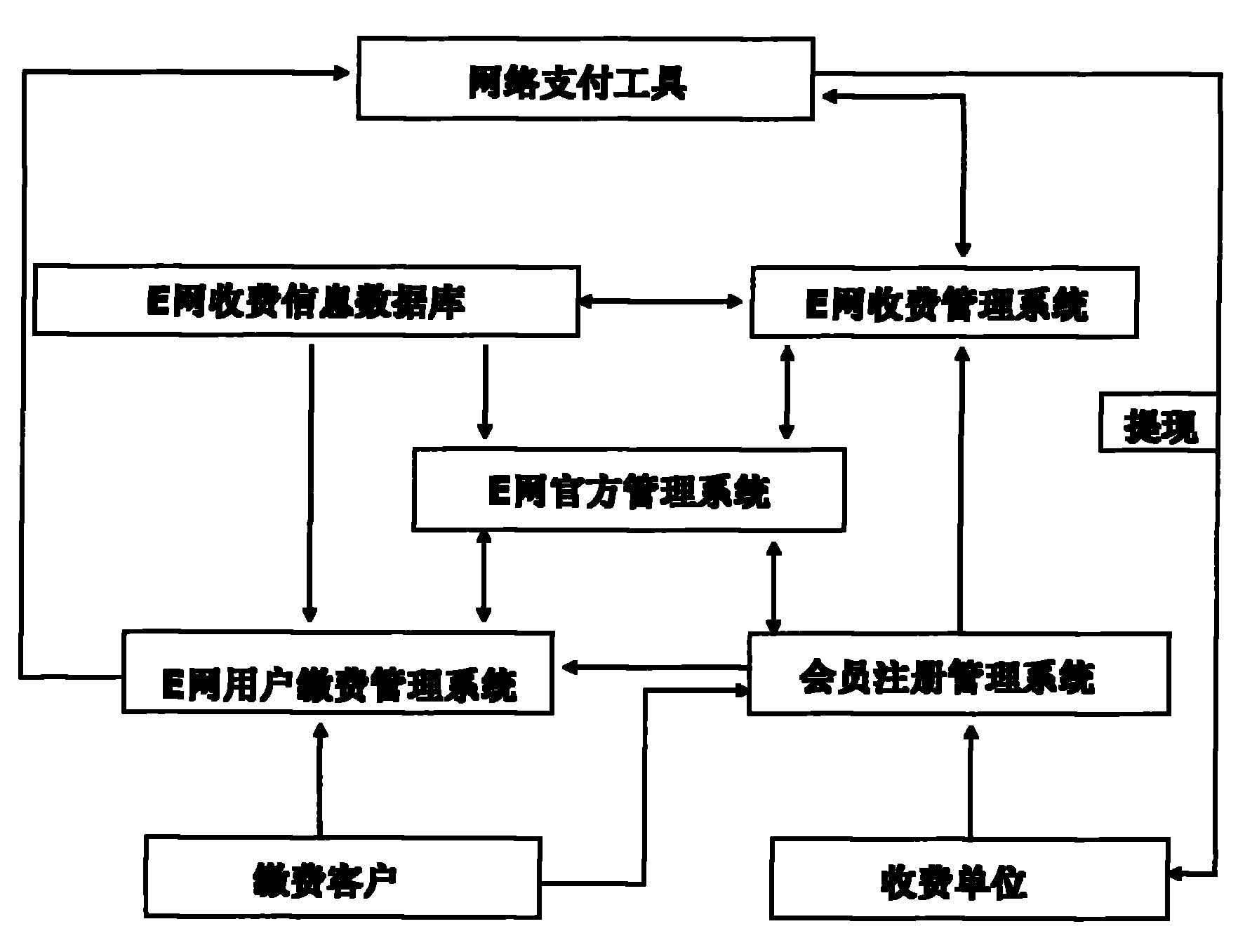
InactiveCN101930642ASecurity serviceGood serviceComplete banking machinesFinanceApplication softwareEthernet
The invention discloses an Ethernet paying business hall system comprising a member registering and managing system, an Ethernet official managing system, an Ethernet user paying and managing system, an Ethernet charging information database, a network paying tool and an Ethernet charging and managing system; wherein the charging information database is in a standard format that various charging information data at the present stage are extracted according to the universality of charging elements and can be edited by conventional application software comprising EXCEL and the like; the Ethernet charging and managing system and the Ethernet user paying and managing system can both realize that multiple users share, manage and process all kinds of charging and paying information data; and the network paying tool comprises Alipay, tenpay or other guaranteed network payment measures. The Ethernet paying business hall system can overcome the defects of respective paying way, complicated category and the like in the prior art to realize centralized charging and paying way and simplification, fully utilizes network resources to realize a new pattern of centralized, unified and standard on-line payment, and has the characteristic of safe, rapid and flexible use.
Owner:王开全
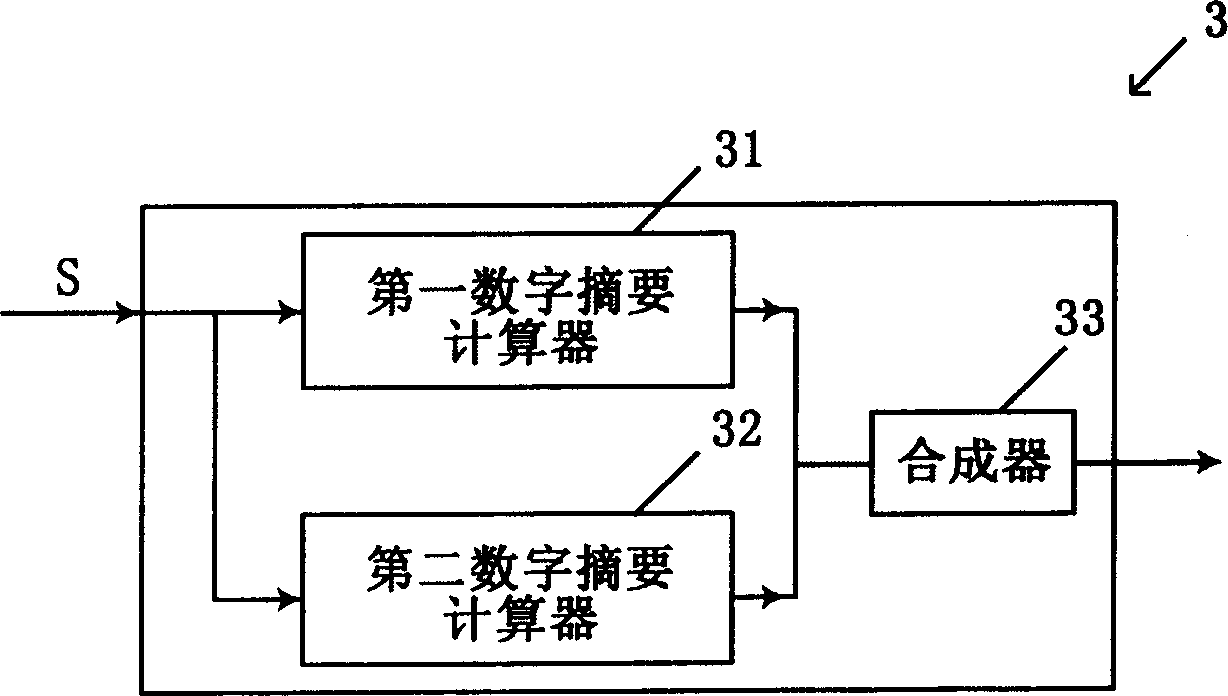
Digital abstract forming device and method, and CA signing system and method
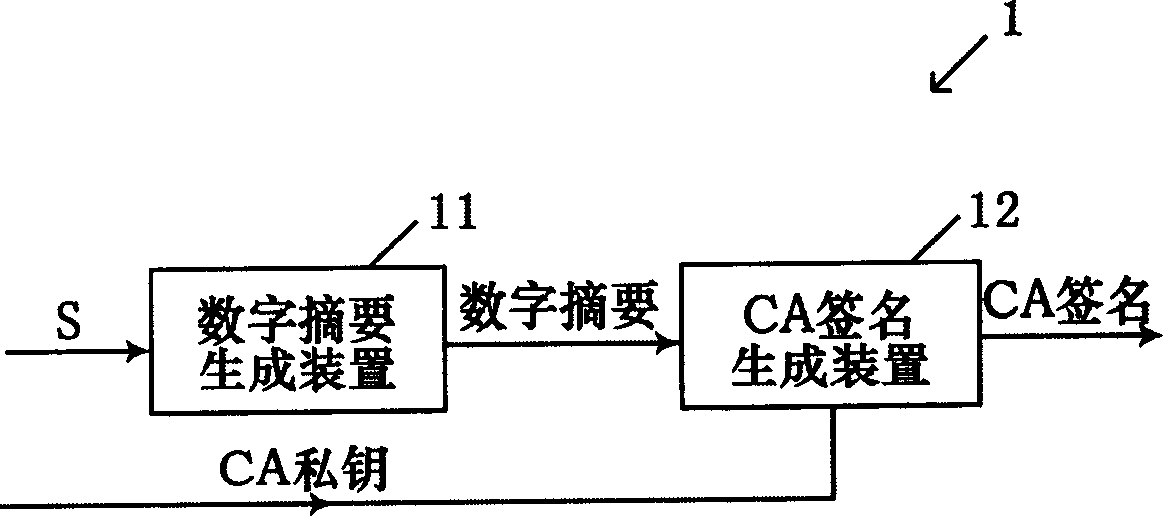
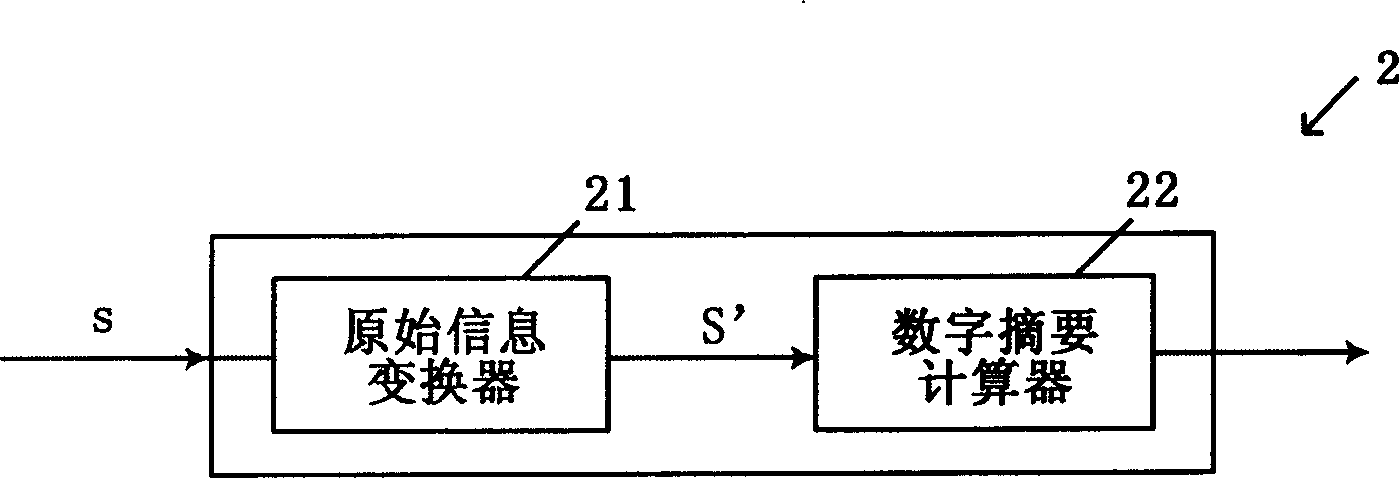
ActiveCN1885769AModify complexityIncrease the lengthUser identity/authority verificationComputer scienceCalculator
The provided generator for digital abstract comprises: a converter for original information to take function transformation, and calculator for digital abstract with discrete algorithm. This invention can improve CA signature security.
Owner:BEIJING SURSEN INT TECH CO LTD
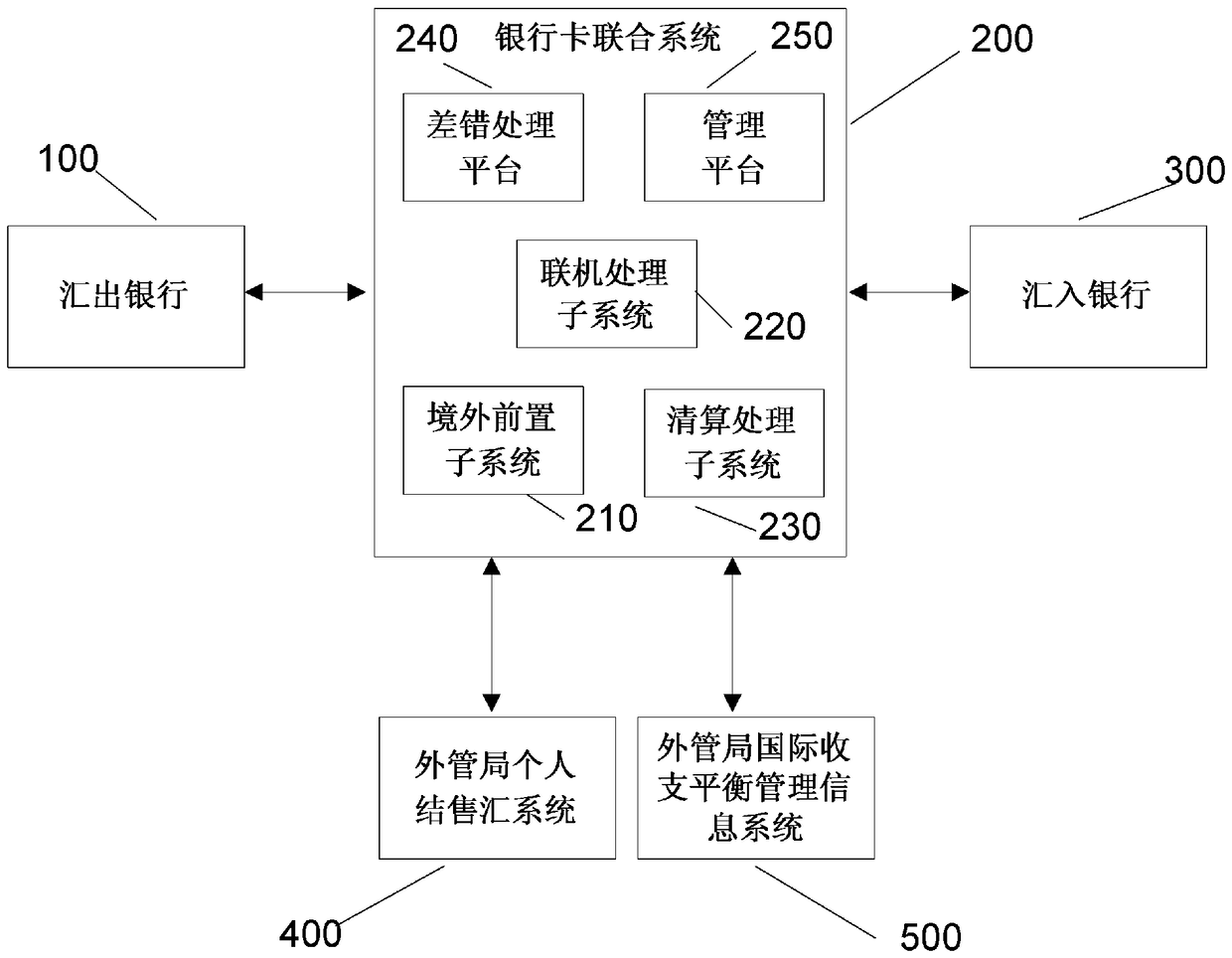
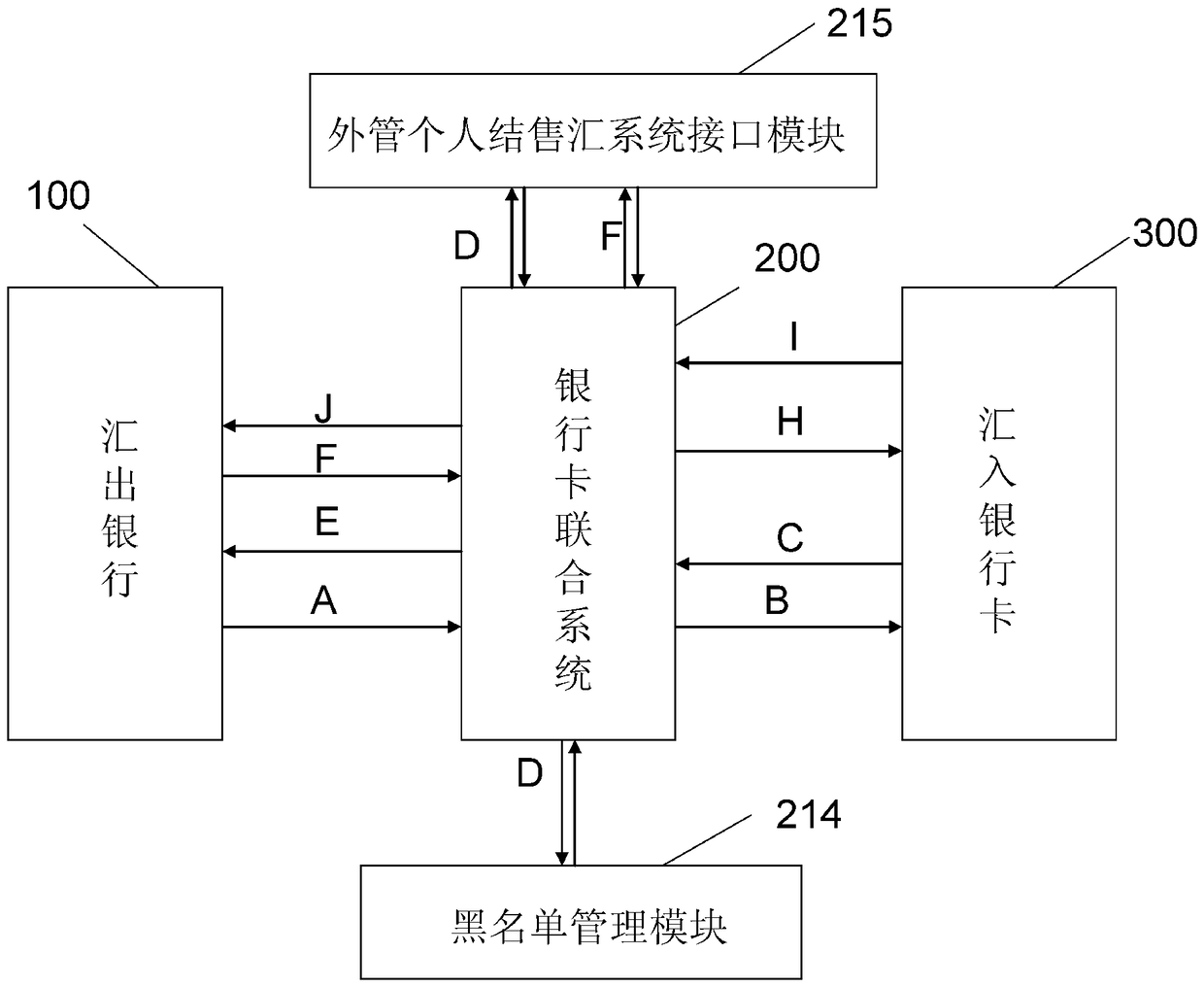
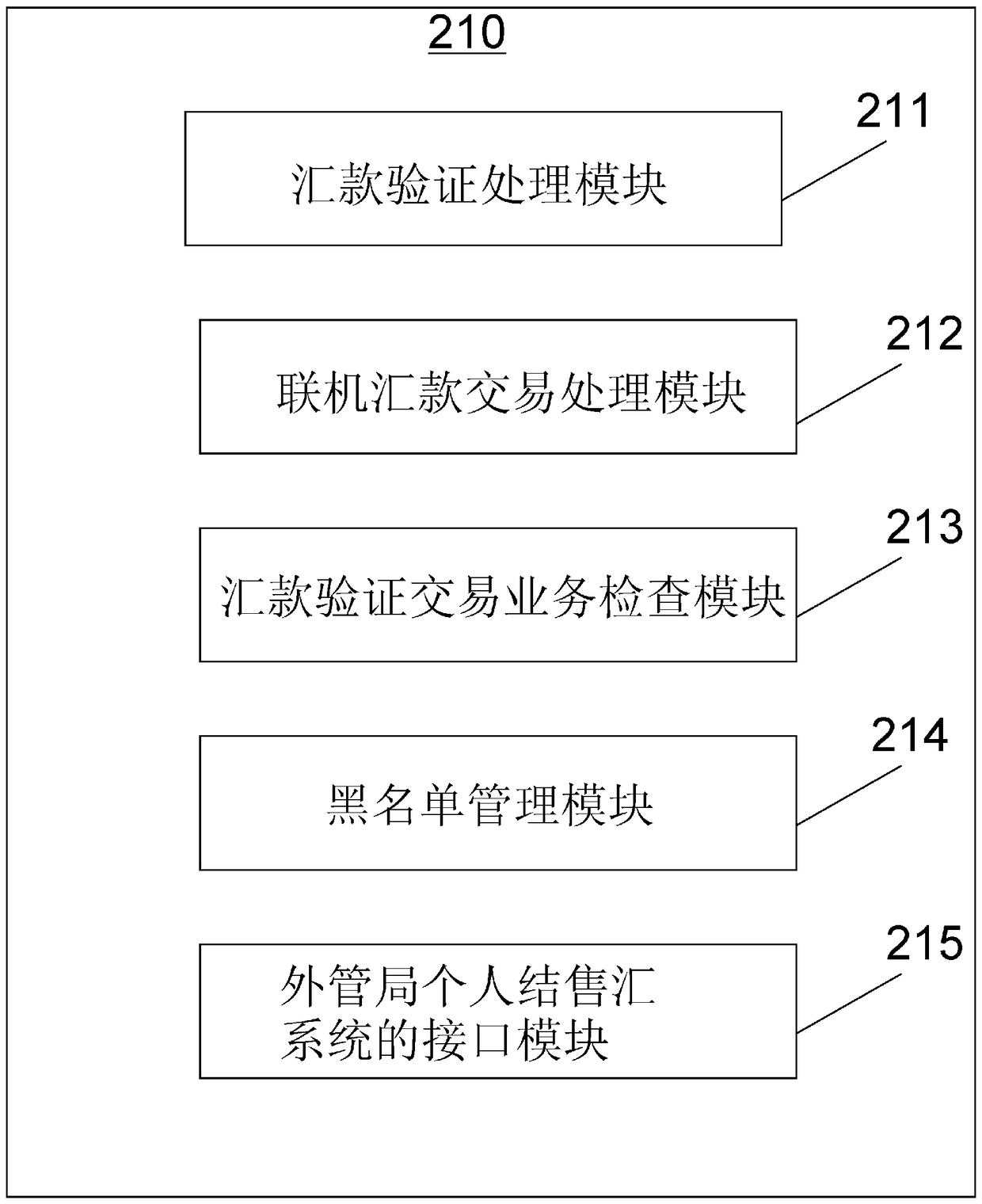
Financial data processing system and global quick money transfer system and method
ActiveCN108090753ARealize direct foreign exchange settlementRealize real-time reportingFinanceProtocol authorisationData processing systemFinancial data processing
The invention relates to a financial data processing system. The financial data processing system is equipped with a first data processing system, a data intermediate processing system, a second dataprocessing system, a first data monitoring system and a second data monitoring system. According to the financial data processing system and a global quick money transfer system and method of the invention, financial data can be monitored and processed in real time. In particular, the global quick money transfer system and method support multi-currency transaction and real-time transfer of fund toaccounts, and support the transfer of fund in original currency or RMB to accounts. Foreign exchange funds can be settled directly. The statistical information of international balance of payment canbe declared in real time. Blacklist management and suspicious split transaction monitoring can be realized. More convenient, safer and more efficient service can be provided for remitters. More timely, accurate and standardized data can be provided for the supervision department.
Owner:UNIONPAY INT CO LTD
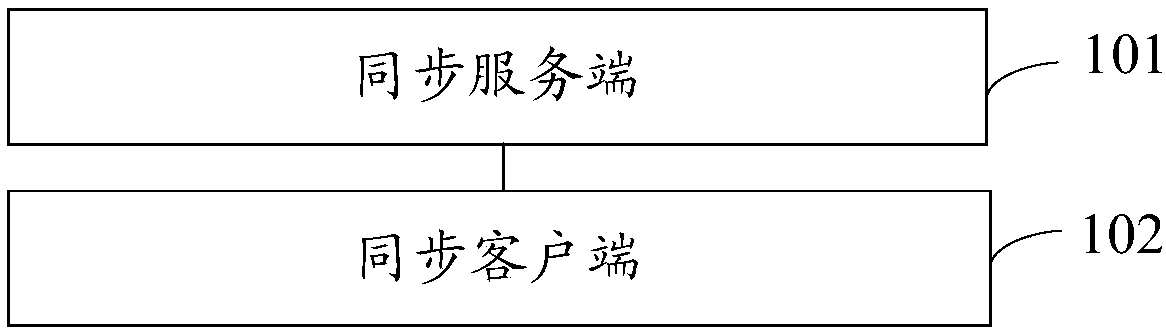
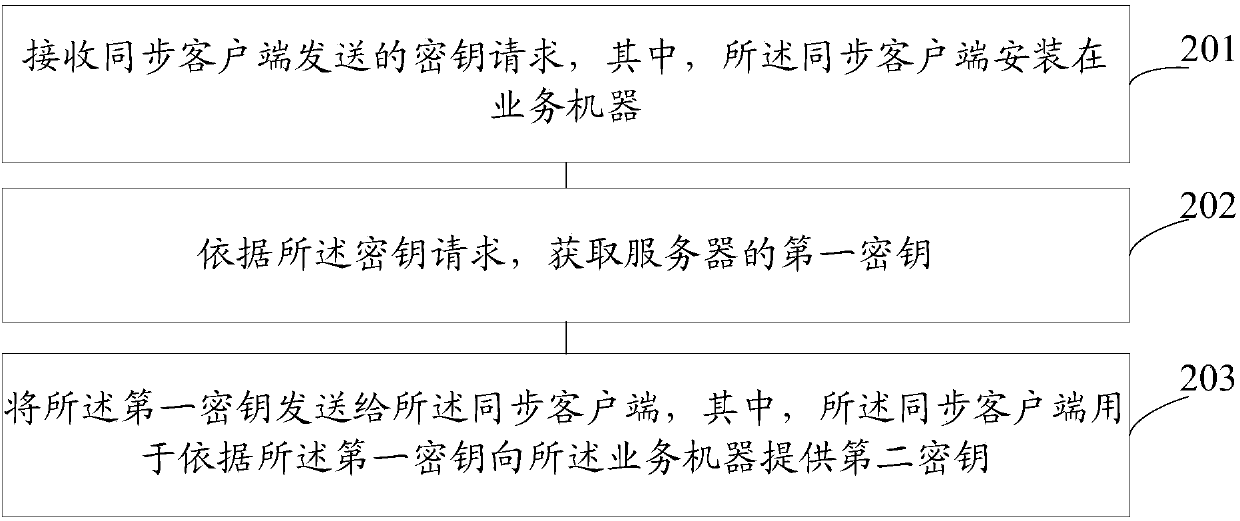
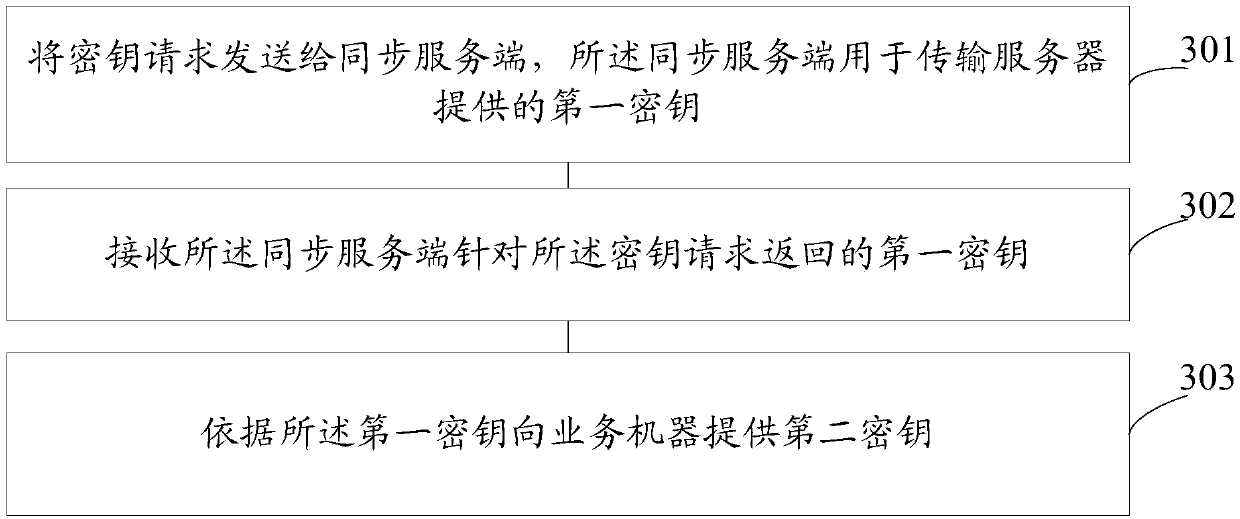
Data synchronization method and system
ActiveCN107592199AGuaranteed reliabilityAvoid the problem of key inconsistencyKey distribution for secure communicationSynchronising transmission/receiving encryption devicesData synchronizationClient-side
The embodiment of the invention provides a data synchronization method and system, and relates to the technical field of computer. The data synchronization method is applied to a synchronization client running in a server, and includes the steps: receiving a key request sent from the synchronization client which is arranged in a service machine; according to the key request, acquiring a first keyof the server; and sending the first key to the synchronization client, wherein the synchronization client is used for providing a second key for the service machine according to the first key. For the data synchronization method, after the synchronization client is started, the latest key in the server can be actively obtained from the synchronization service terminal, so that the data synchronization method solves the problem that the key of the server is not consistent with the key of the service machine because the server fails to actively push the key, and can guarantee the reliability ofsynchronous updating of the key.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com