Device for classifying and recognizing network application flow quantity and method thereof
A traffic classification and network application technology, applied in the field of network application traffic classification and identification devices, can solve the problems of no public protocol specification for private protocols, difficulty in extracting protocol feature codes, limited number, etc., and achieve real-time high-precision application perception and classification control. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
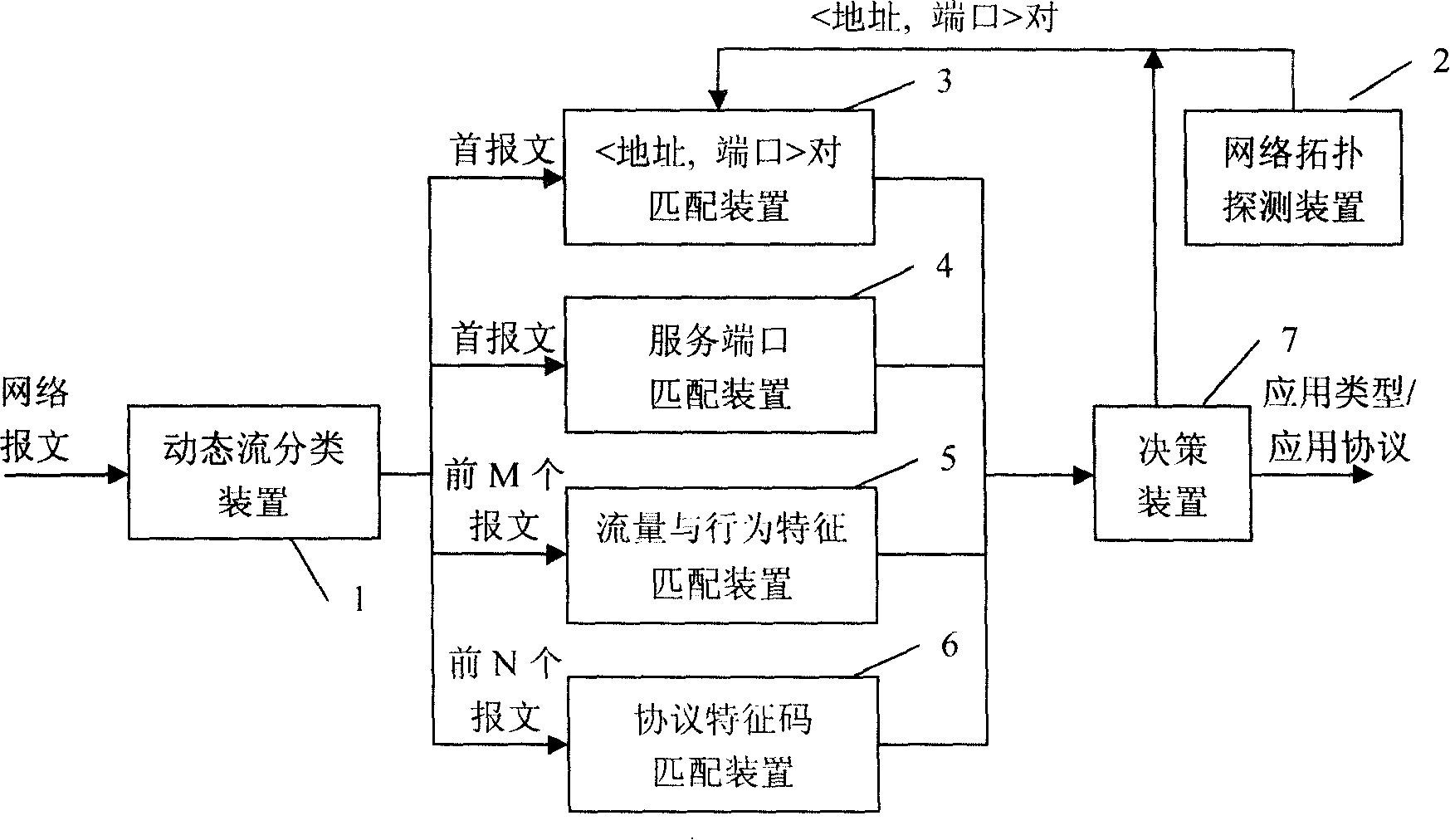
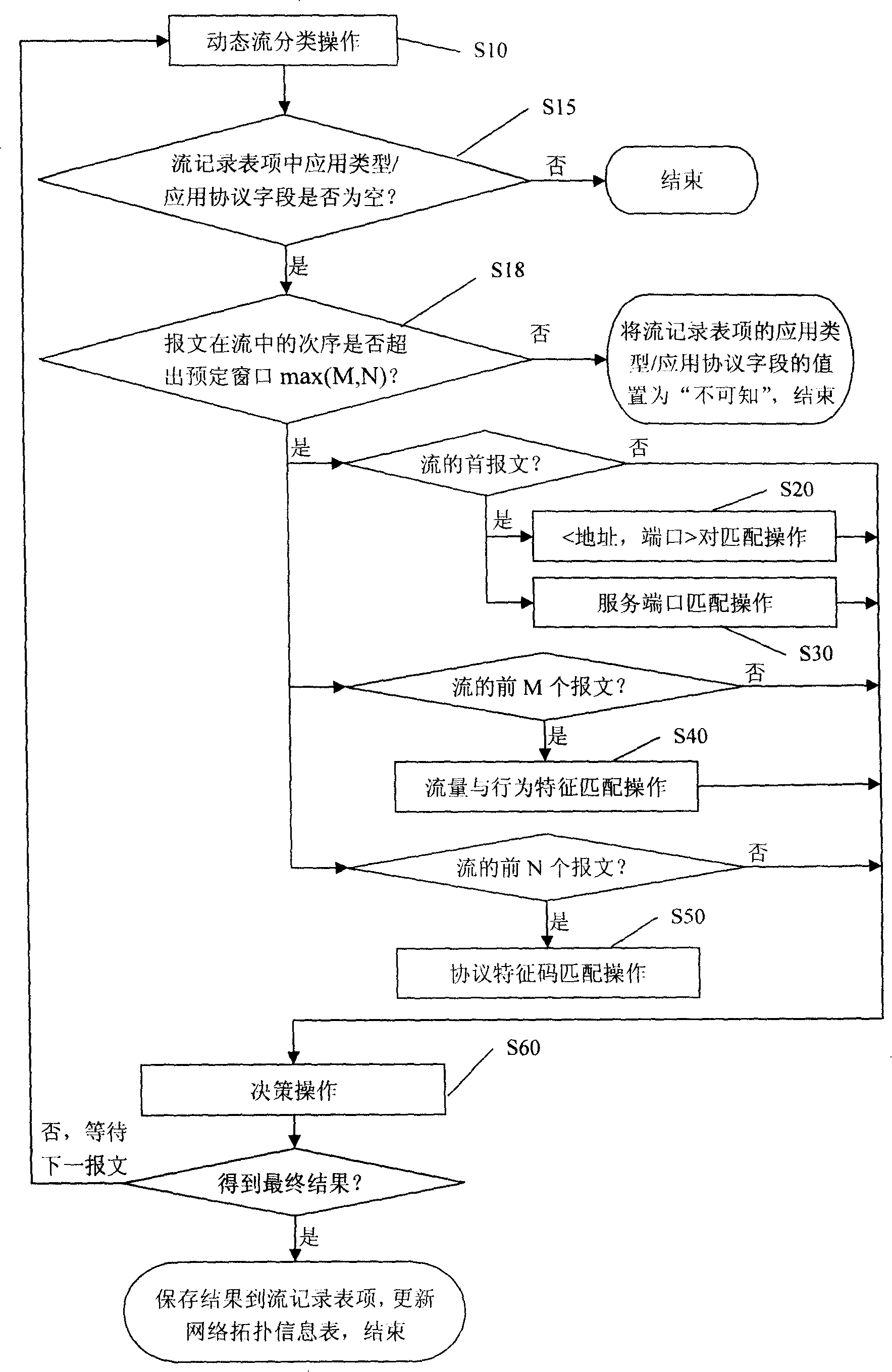
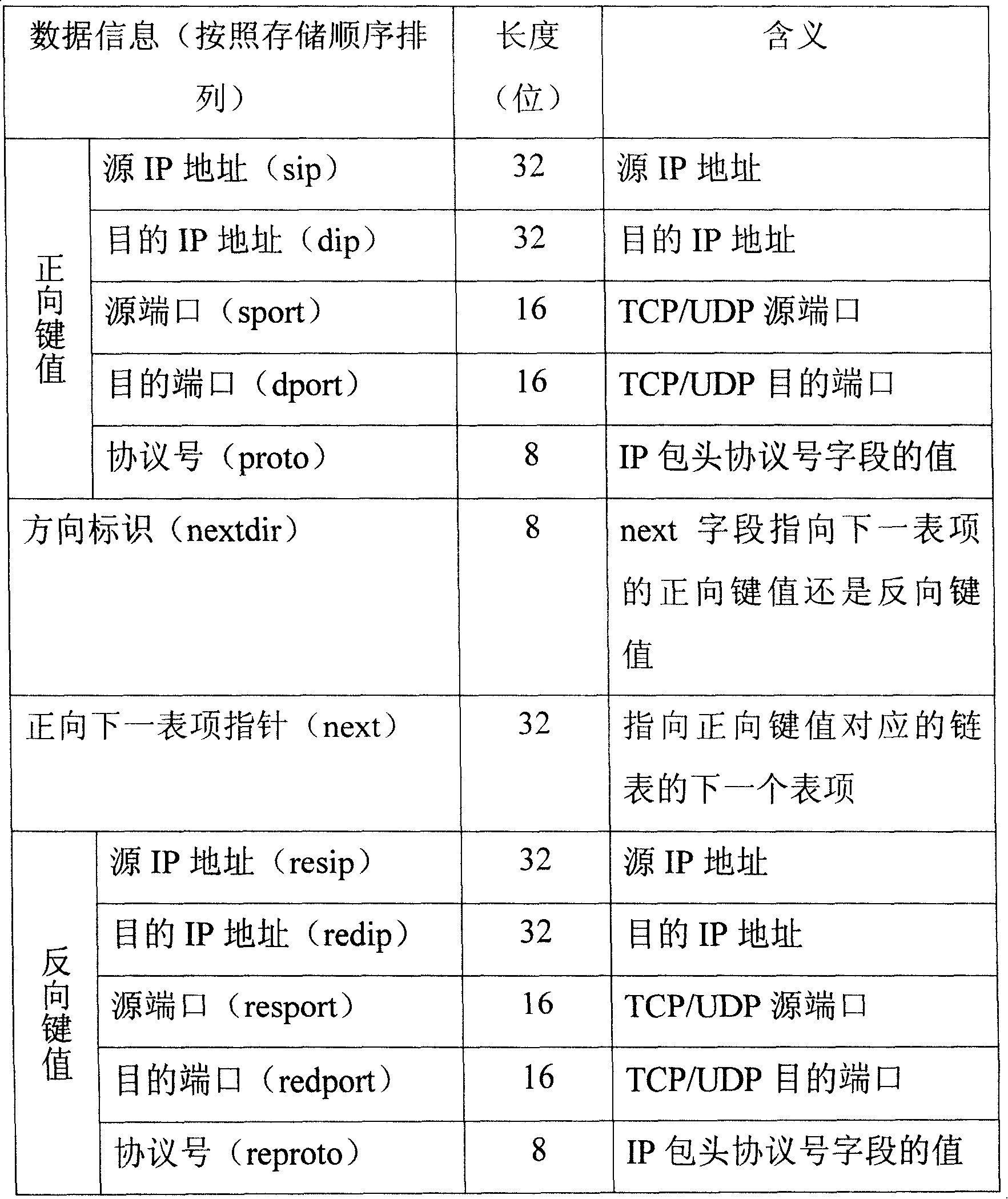
[0025] The network flow table 11 is organized in the form of a hash table, and uses a linked list to solve hash collisions. The structure of the flow record entry is shown in the following table:
[0026]
[0027]
[0028] The network topology information table 21 is used to record pair and its corresponding application type / application protocol, matching degree and other information. It adopts hash table to organize, and uses linked list to solve hash collision, where entry is shown in the following table:
[0029] Data information (arranged in order of storage
length
the meaning
[0030] List)
(bit)
pair (ipport)
64
IP address, TCP / UDP port
Application Type / Application Protocol Information
(appinfo)
32
Application Type / Application Protocol
Matching degree (weight)
32
suitability
[0031] The service port table 41 is used to record information such as t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com