Conversation cryptographic key generation method, system and communication equipment
A technology of session key and communication equipment, which is applied in the field of network communication, can solve the problems of insufficient security and no change of shared key for a long time, and achieve the effect of improving practicability and security and avoiding trust and dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
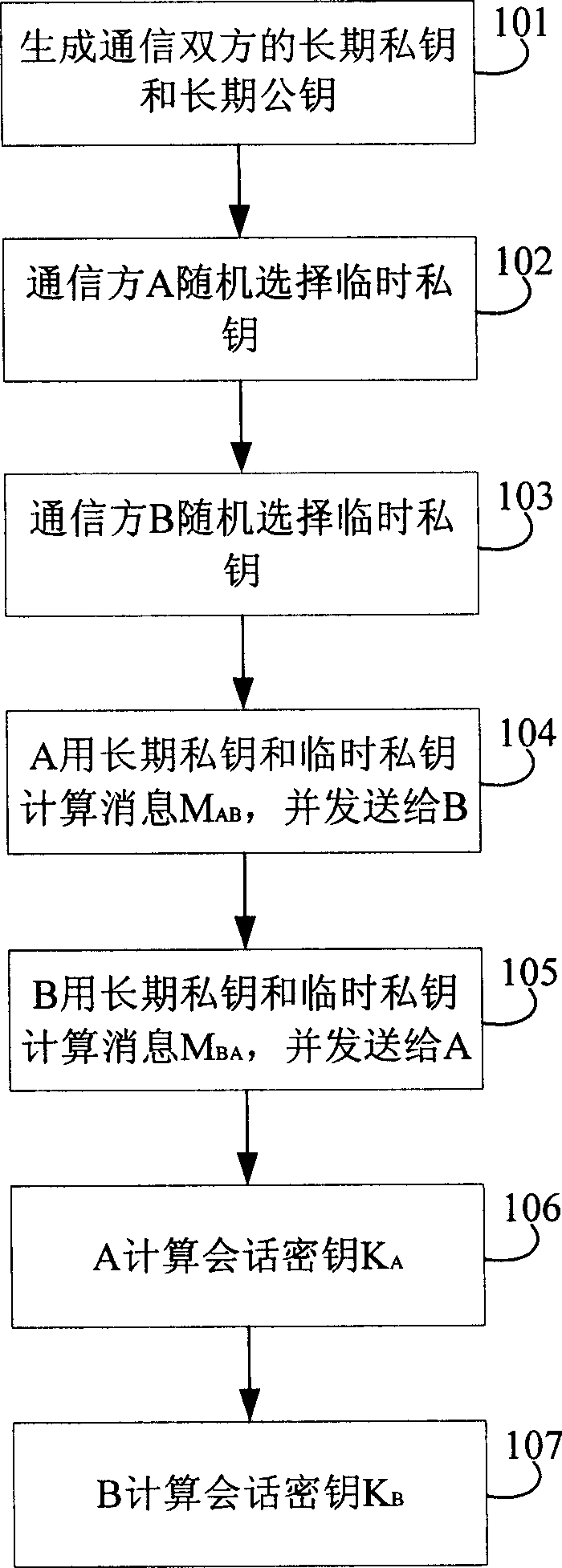
[0044] see figure 1 , is a flowchart of a method for generating a session key. This embodiment is based on the cryptographic system of discrete logarithm, system parameter T={g, p}, wherein p is a prime number, and g is a finite field F p Generator, and g is less than p;
[0045] The method for generating the session key between communication parties A and B specifically includes:
[0046] Step 101: The key management center generates A's long-term private key a, B's long-term private key b, and A's long-term public key: P A =g a mod p, B's long-term public key: P B =g b mod p; and send a and b to A and B respectively in a secure manner.
[0047] Step 102: A randomly selects a temporary private key x and keeps it secret.
[0048] Step 103: B randomly selects a temporary private key y and keeps it secret.
[0049] Step 104: A calculates M AB =(P B ) ax mod p=g abx mod p, send message M to B AB .
[0050] Step 105: B calculates M BA =(P A ) by mod p=g aby ...
Embodiment 2
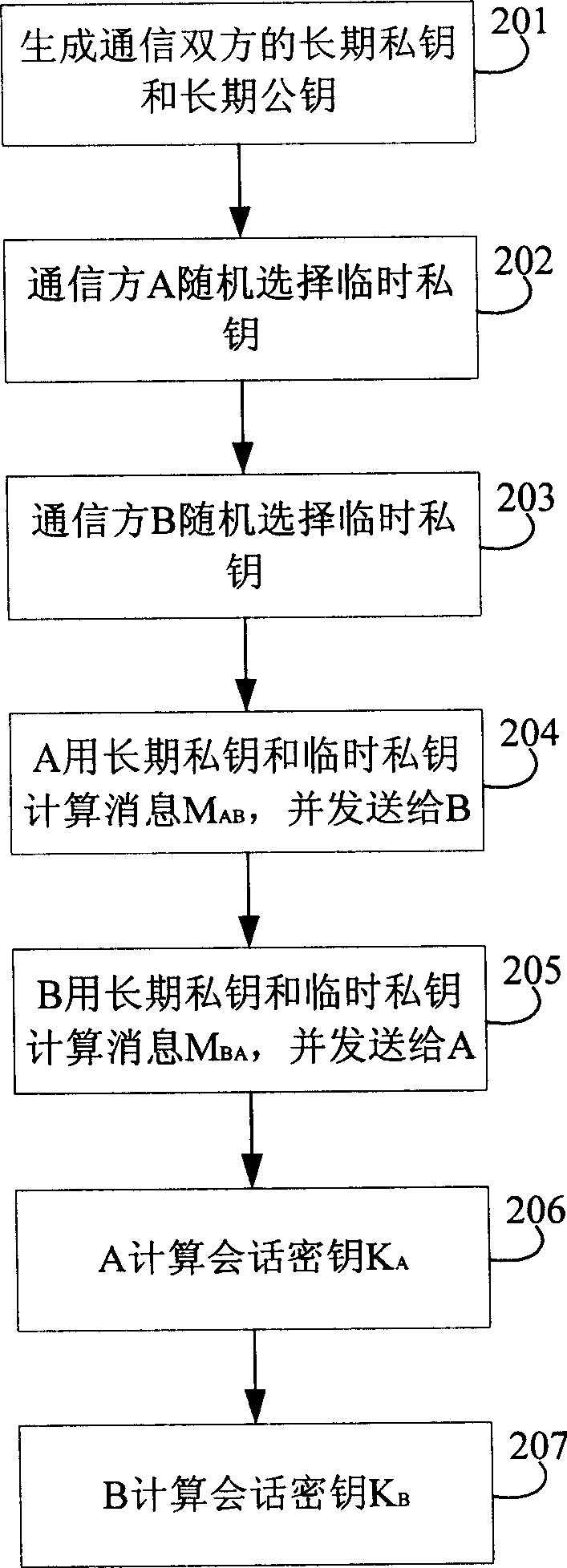
[0058] see figure 2 , is a flowchart of a method for generating a session key. This embodiment is based on the elliptic curve cryptosystem, and the system parameter is T: (u, v, G, n, p), wherein p is a positive integer, Fp is a finite field, u, v are positive integers on Fp, and G is an elliptic curve The base point on E(Fp), n is a prime number, which is the order of the base point G;
[0059] The method for generating the session key between communication parties A and B specifically includes:
[0060] Step 201: The key management center generates A's long-term private key a, B's long-term private key b, and A's long-term public key: P A =a*G mod p, B's long-term public key: P B =b*G mod p. And send a and b to A and B respectively in a safe way.
[0061] Step 202: A randomly selects a temporary private key x and keeps it secret.
[0062] Step 203: B randomly selects the temporary private key y, and keeps it secretly.
[0063] Step 204: A calculates M AB =a*x*(P B ...
Embodiment 3
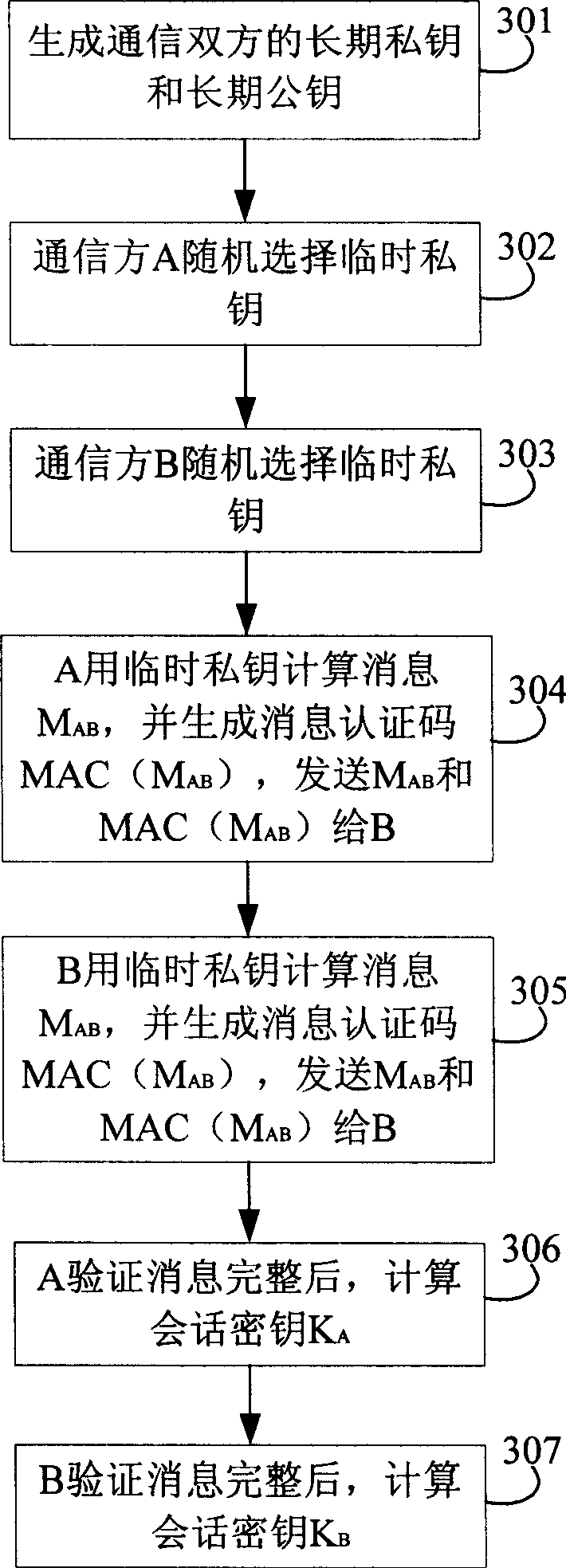
[0072] see image 3 , is a flowchart of a method for generating a session key. This embodiment is based on the cryptographic system of discrete logarithm, system parameter T={g, p}, wherein p is a prime number, and g is a finite field F p Generator, and g is less than p;
[0073] The method for generating the session key between communication parties A and B specifically includes:
[0074] Step 301: The key management center generates A's long-term private key a, B's long-term private key b, and A's long-term public key: P A =g a mod p, B's long-term public key P B =g b mod p, and send a and b to A and B respectively in a secure manner.
[0075] Step 302: A randomly selects a temporary private key x and keeps it secret.
[0076] Step 303: B randomly selects the temporary private key y, and keeps it secretly.
[0077] Step 304: A calculates M AB =g x mod p, s=(P B ) a mod p=g ab mod p, use s to generate message M AB Message Authentication Code (MAC, Message A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com