Method for improving identification authentication security based on password card
A technology of identity authentication and password card, which is applied in the field of information security, can solve the problems of legitimate user losses, illegal transactions, hidden safety hazards, etc., and achieve the effect of increasing the difficulty of cracking and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
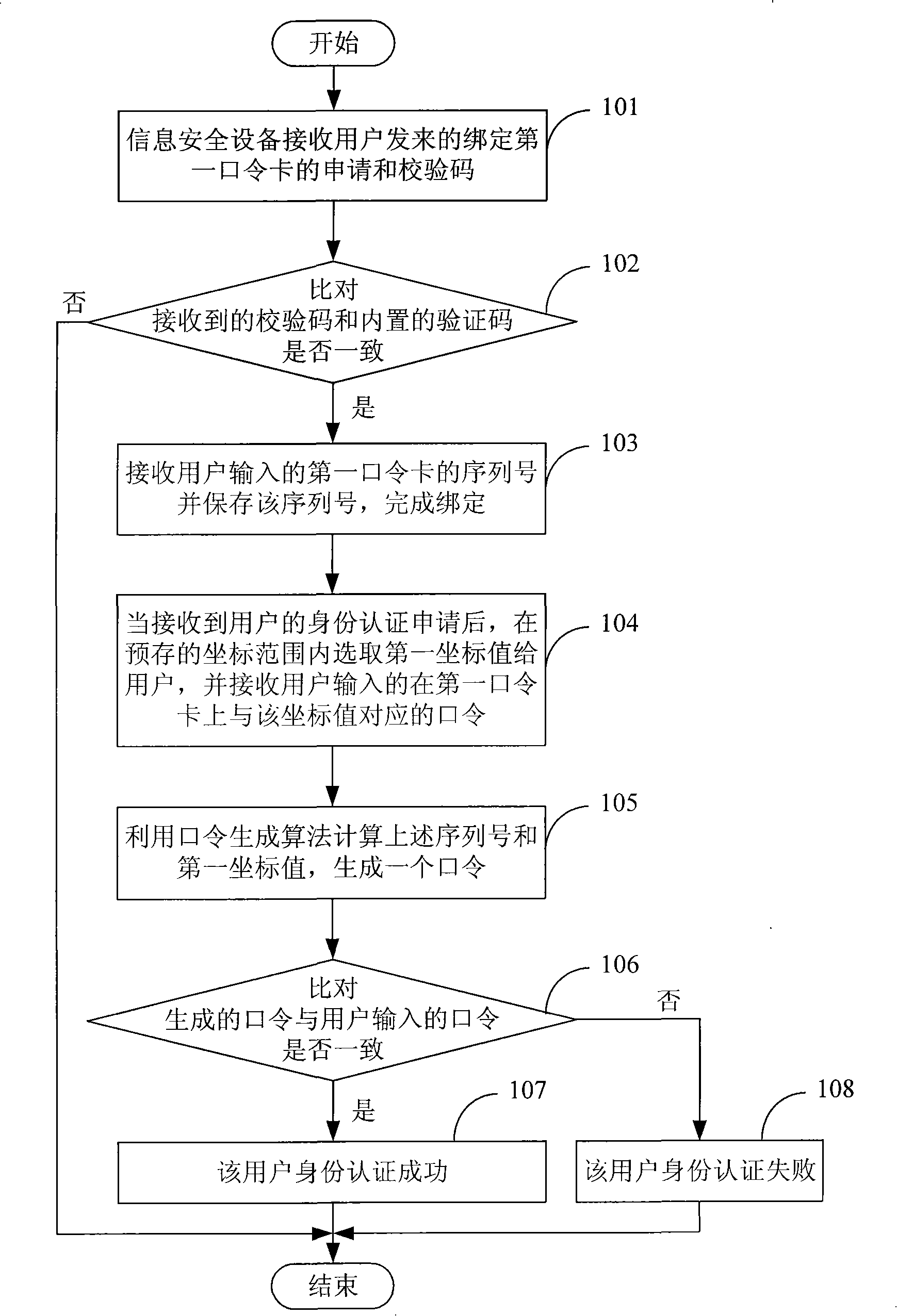
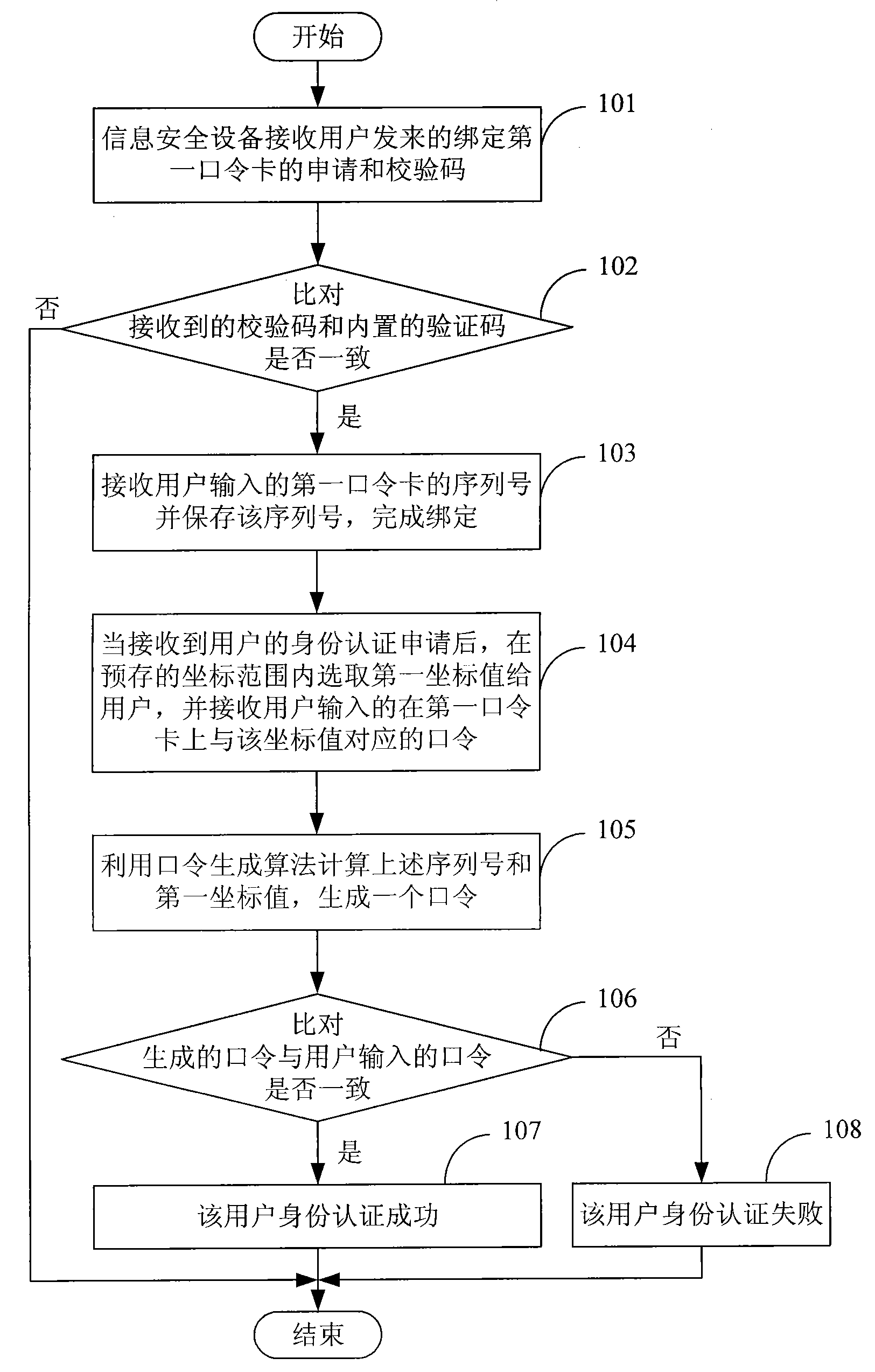
[0032] see figure 1 , the embodiment of the present invention provides a method for improving identity authentication security based on a password card, the method specifically includes:
[0033] Step 101: The information security device receives the application for binding the first password card and the verification code sent by the user.
[0034] Step 102: The information security device checks whether the received verification code is consistent with the built-in verification code, and if they are consistent, execute step 103; otherwise, the binding of the information security device and the first passcard fails, and ends.
[0035] Step 103: The information security device receives the serial number of the first password card input by the user, saves the serial number, and completes the binding with the first password card.
[0036] Step 104: After receiving the user's identity authentication application, the information security device selects the first coordinate value ...
Embodiment 2
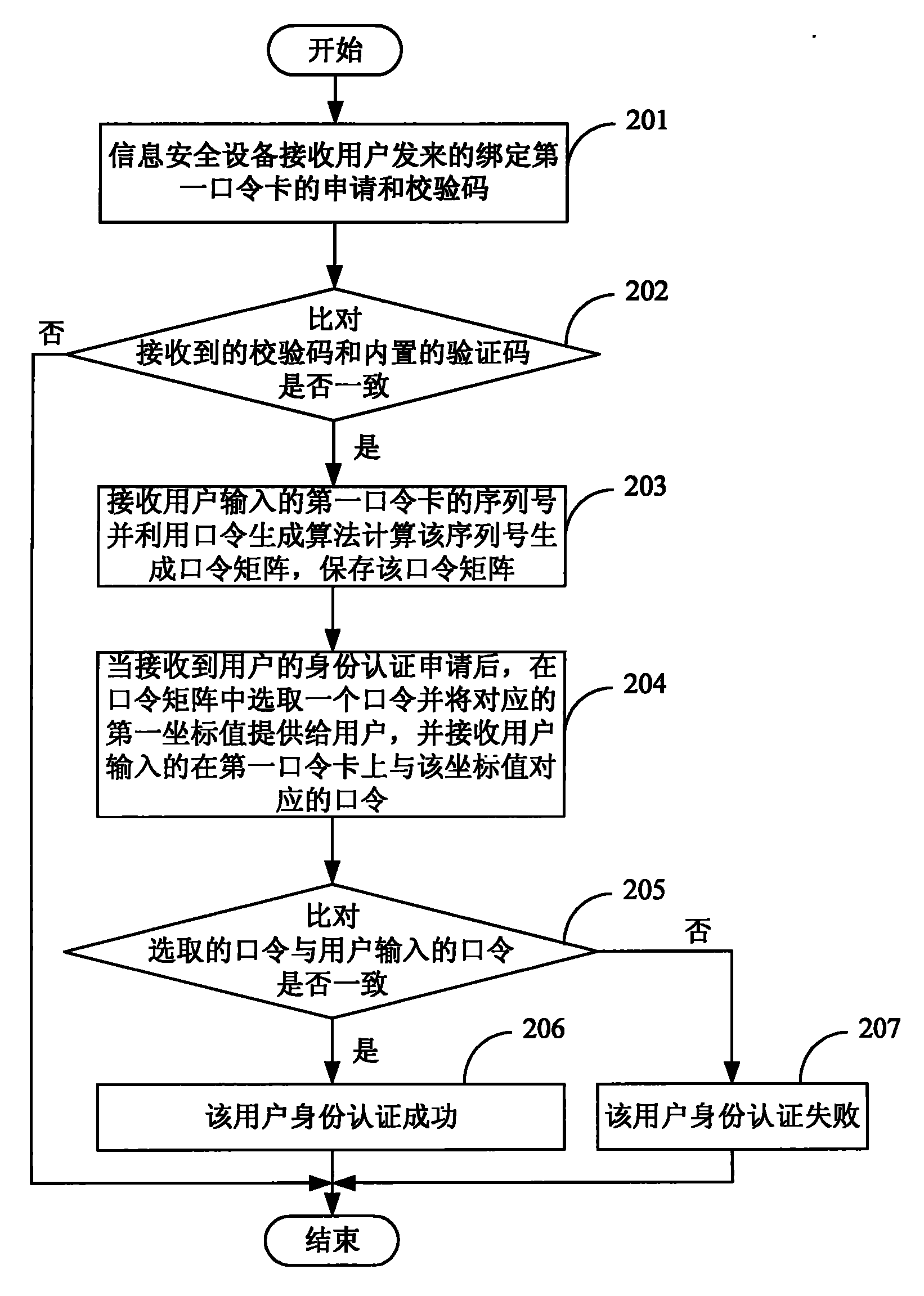
[0049] see figure 2 , the embodiment of the present invention also provides a method for improving identity authentication security based on a password card, which specifically includes:
[0050] Step 201: The information security device receives the application for binding the first password card and the verification code sent by the user.
[0051] Step 202: The information security device compares whether the verification code is consistent with the built-in verification code, and if they are consistent, execute step 203; otherwise, the binding between the information security device and the first passcard fails, and ends.
[0052] Step 203: The information security device receives the serial number of the first password card input by the user, uses the password generation algorithm to calculate the serial number to generate a password matrix, and saves the password matrix to complete the binding with the first password card.
[0053] Step 204: After receiving the user's i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com