Attack protection method and device
A legal, source address technology, applied in the field of network security, can solve the problems of maintaining a large amount of data, complex implementation, server impact, etc., to achieve the effect of ensuring normal operation, significant prevention effect, and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
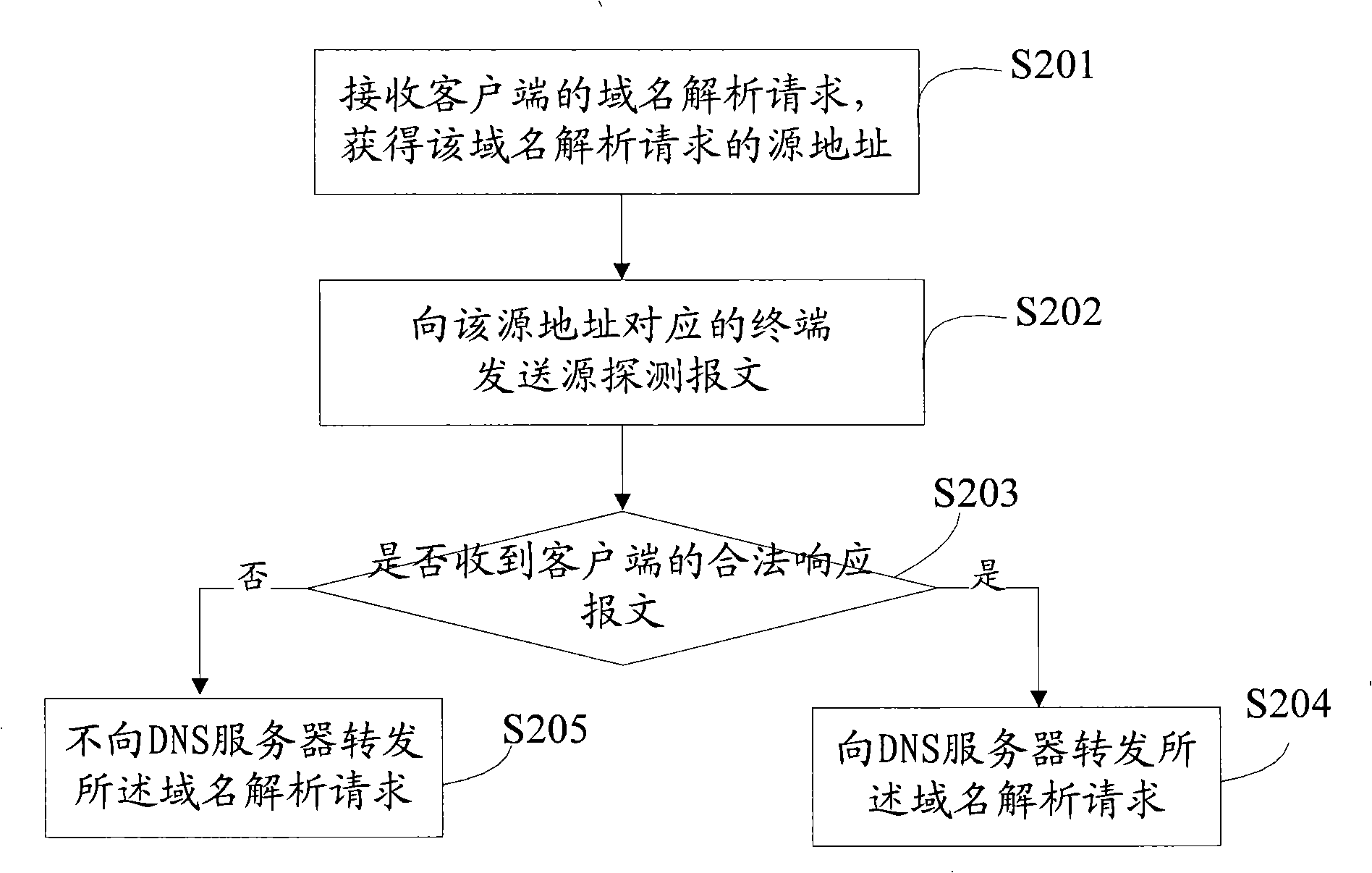
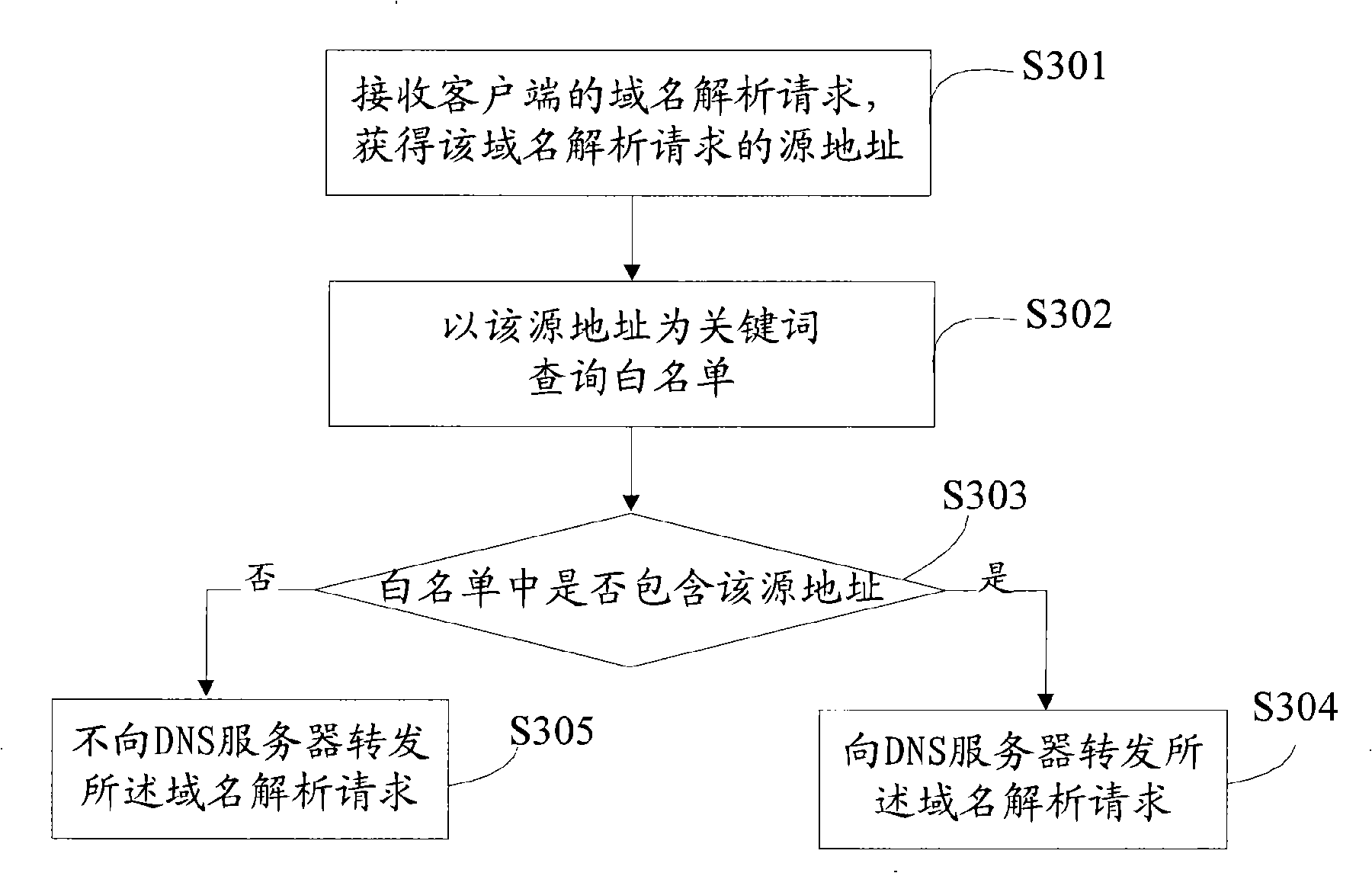
[0037] In an embodiment of the attack prevention method of the present invention, when the detection device detects a DNS flood attack, it enters the prevention process: for the domain name resolution request sent by the client, first verify that the domain name resolution request comes from a real source, and then send the domain name resolution request to the DNS server Forward the domain name resolution request and respond to the terminal. The detection device may be a special detection device or the firewall itself, depending on the networking.
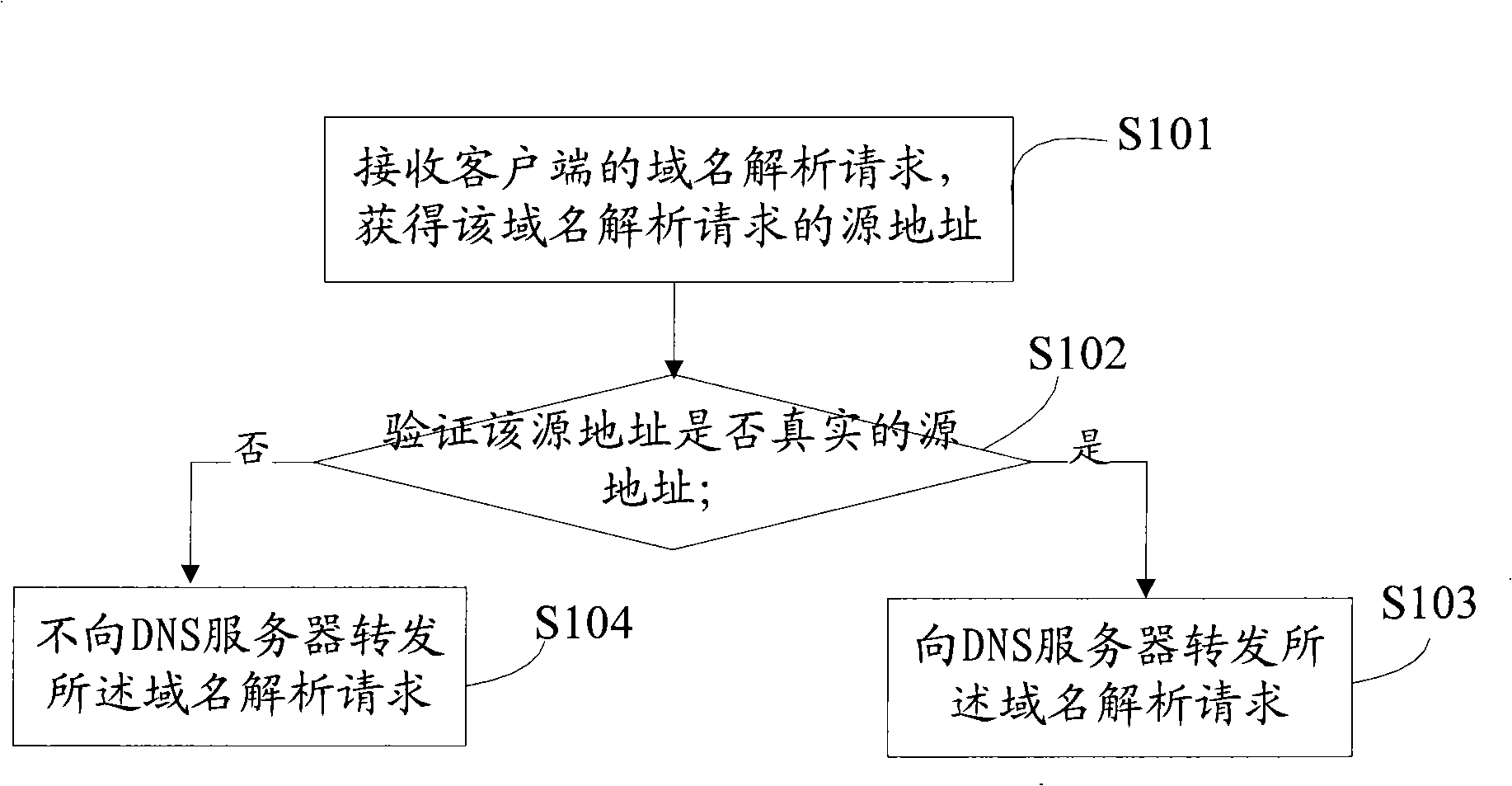
[0038] refer to figure 1 , an embodiment of the attack defense method of the present invention mainly includes the following steps:
[0039] S101: Receive a domain name resolution request from the client, and obtain the source address of the domain name resolution request;
[0040] S10...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com