Optimization method for acquiring authentication cryptographic key during position updating process
An authentication key and update process technology, applied in security devices, electrical components, wireless communications, etc., can solve the problem of low processing efficiency, achieve the effects of optimizing the process, simplifying the message process, and improving network processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
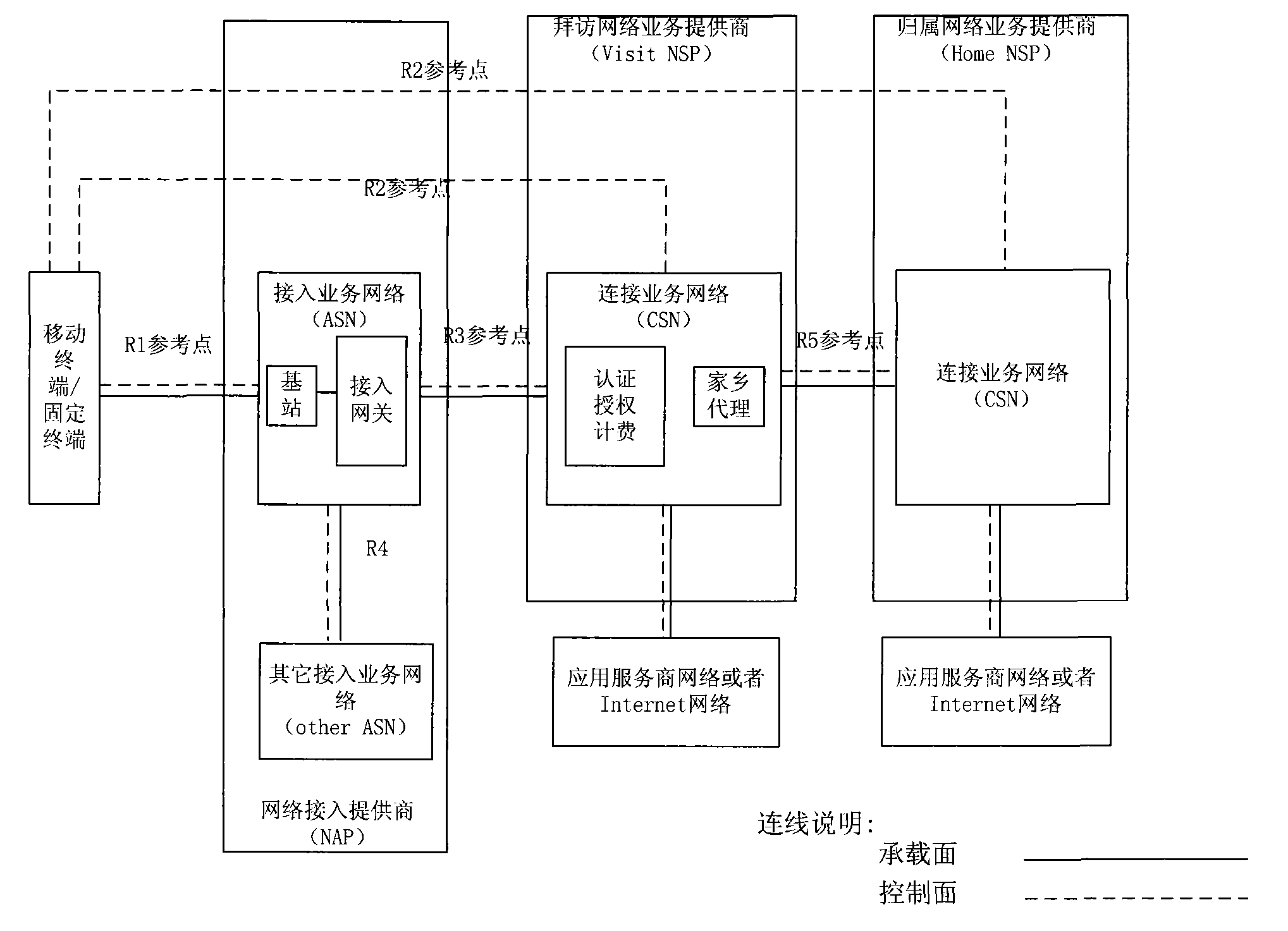
[0048] The present invention is based on the release1.0.0 related protocol specifications (including Stage2 and Stage3) released by NWG.
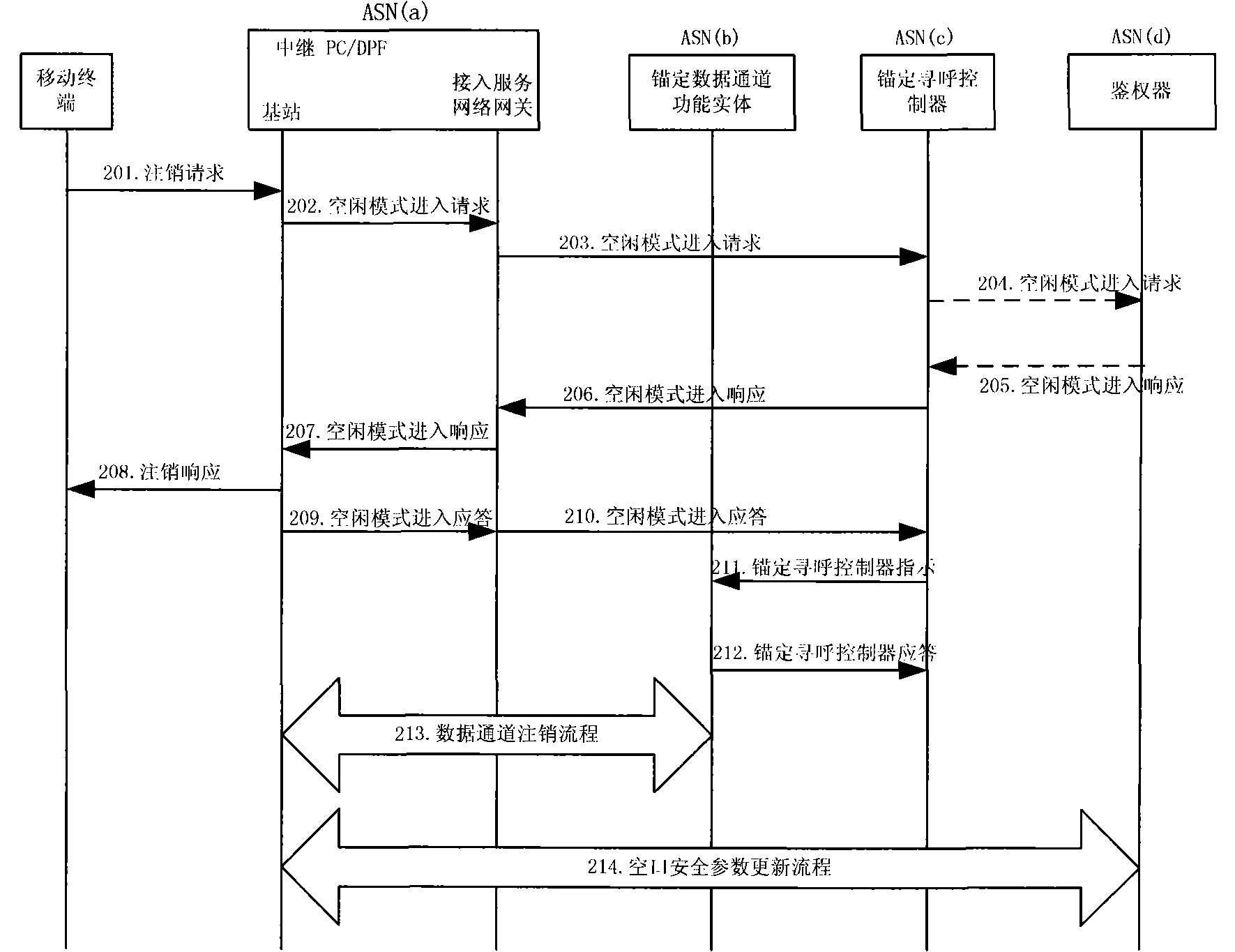
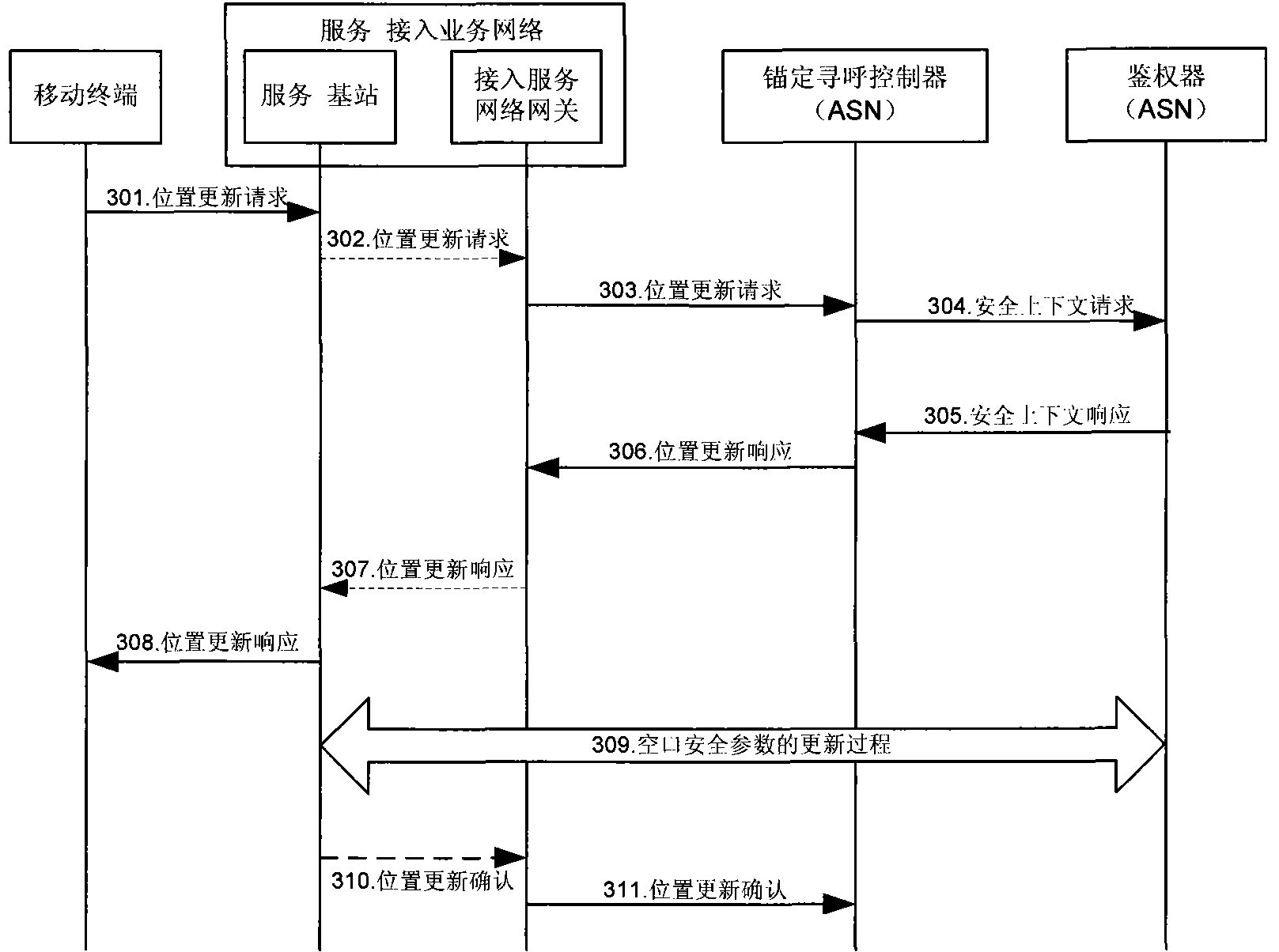
[0049] For the MS that enters the idle mode, the anchor PC saves its relevant information, so the anchor PC can store the AK context, and through appropriate judgment processing, to ensure that the correct AK context is provided to the BS, and it is not necessary to obtain it from the Authenticator.
[0050] The main idea of the present invention is that when the MS enters the idle mode, the anchor PC saves the AK context of the serving BS, and when the MS performs location update, the anchor PC decides whether to initiate the acquisition of the AK context through corresponding judgment. The method specifically includes the following steps:
[0051] (a) An optional field AK context (AK Context) is added to the idle mode entry response (IM_Entry_State_Change_Rsp) message;
[0052] (b) When the MS enters the idle mode, the tracking local p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com