Symmetric ciphering method having infinite cipher key space
A symmetric encryption, key space technology, applied in the field of information security, can solve the problem of increasing the difficulty of known plaintext analysis attacks, achieve high encryption and decryption efficiency, and protect security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be described in more detail below with reference to the accompanying drawings.
[0061] 1. Implementation of Encryption
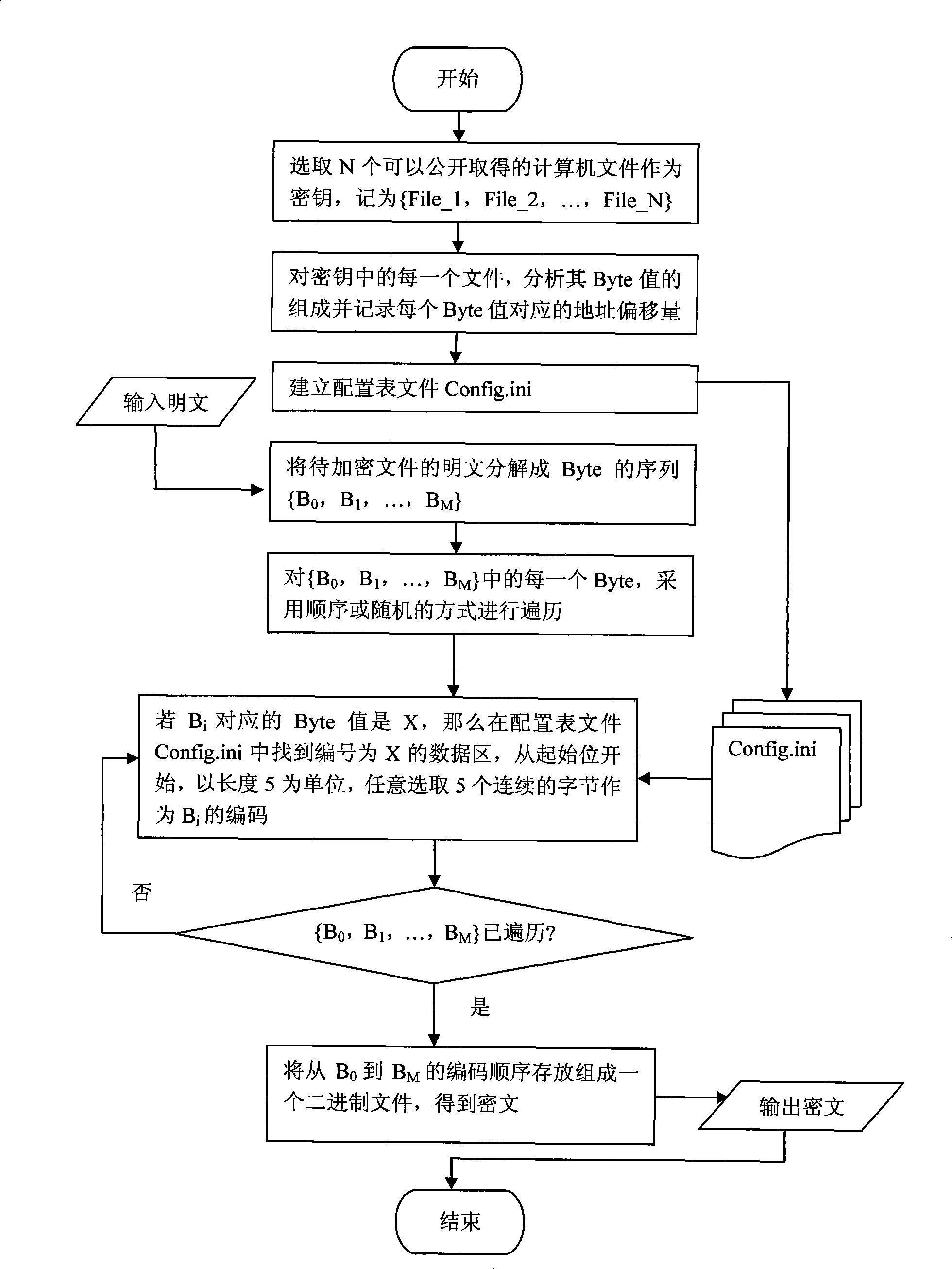
[0062] Such as figure 1 Shown, the operating steps of the present invention are as follows:
[0063] (1) Select N (N≥1, N is a natural number) publicly available computer files, and use the sequence {File_1, File_2, ..., File_N} as the key, where File_i represents the file name of the i-th file.
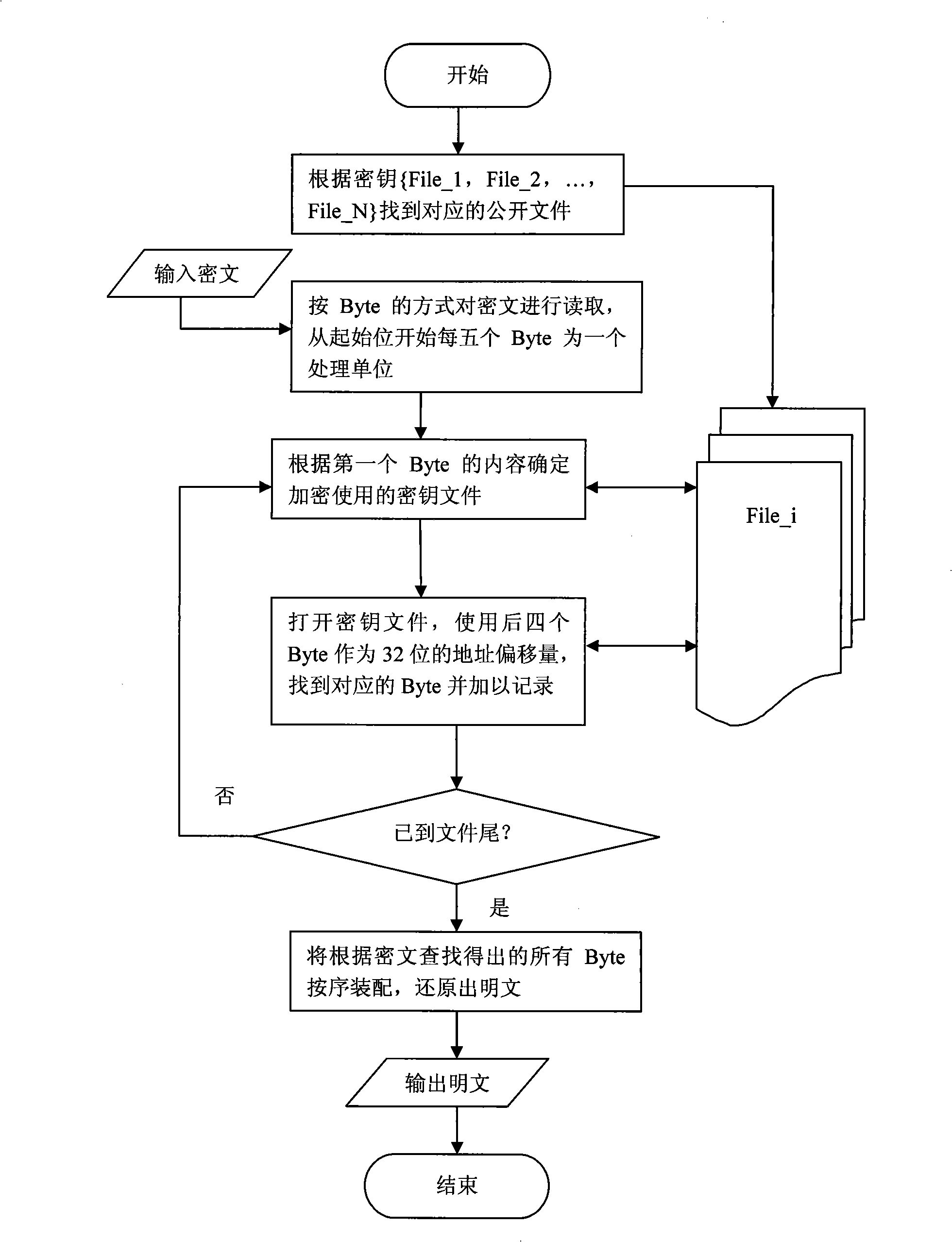
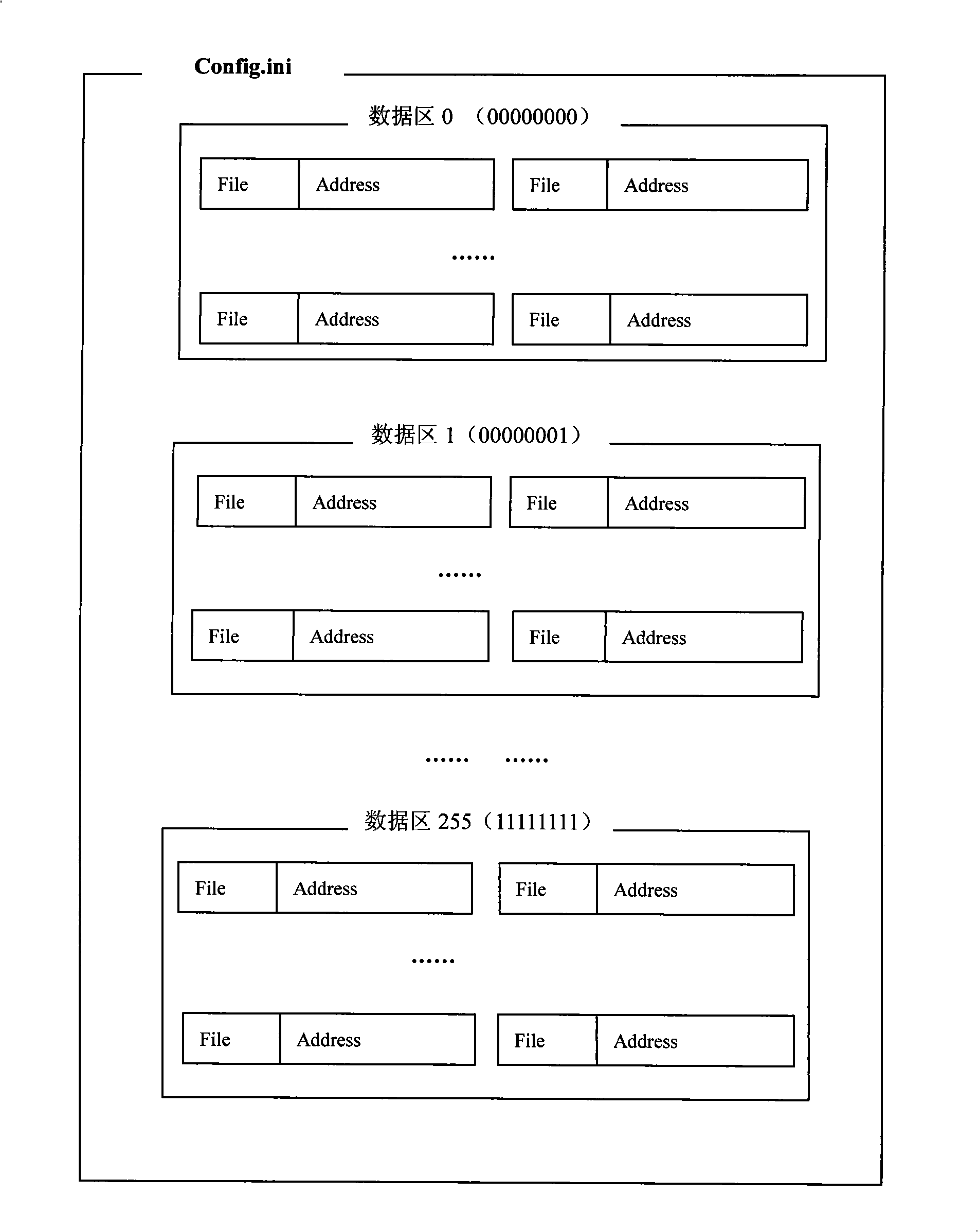
[0064] (2) For each file in the key, use program automation to count the value of each Byte and record its address offset. Then create a configuration table file Config.ini, which contains 256 data areas numbered from 0 to 255, and each data area stores 256 different Byte values from 0 to 255 according to its number. Starting from the start bit of any data area, the meaning of every five consecutive Bytes is: the first Byte represents the file used for encryption, and the next four Bytes represent the 32-bit address offset. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com