Internally-control safety method for information gateway-service support system
A business support and information network technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as the difficulty in supervising the information access behavior of support personnel, and the inability to implement the SQL log audit mechanism due to huge system overhead. , to ensure accuracy and completeness, strengthen access management, and reduce security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
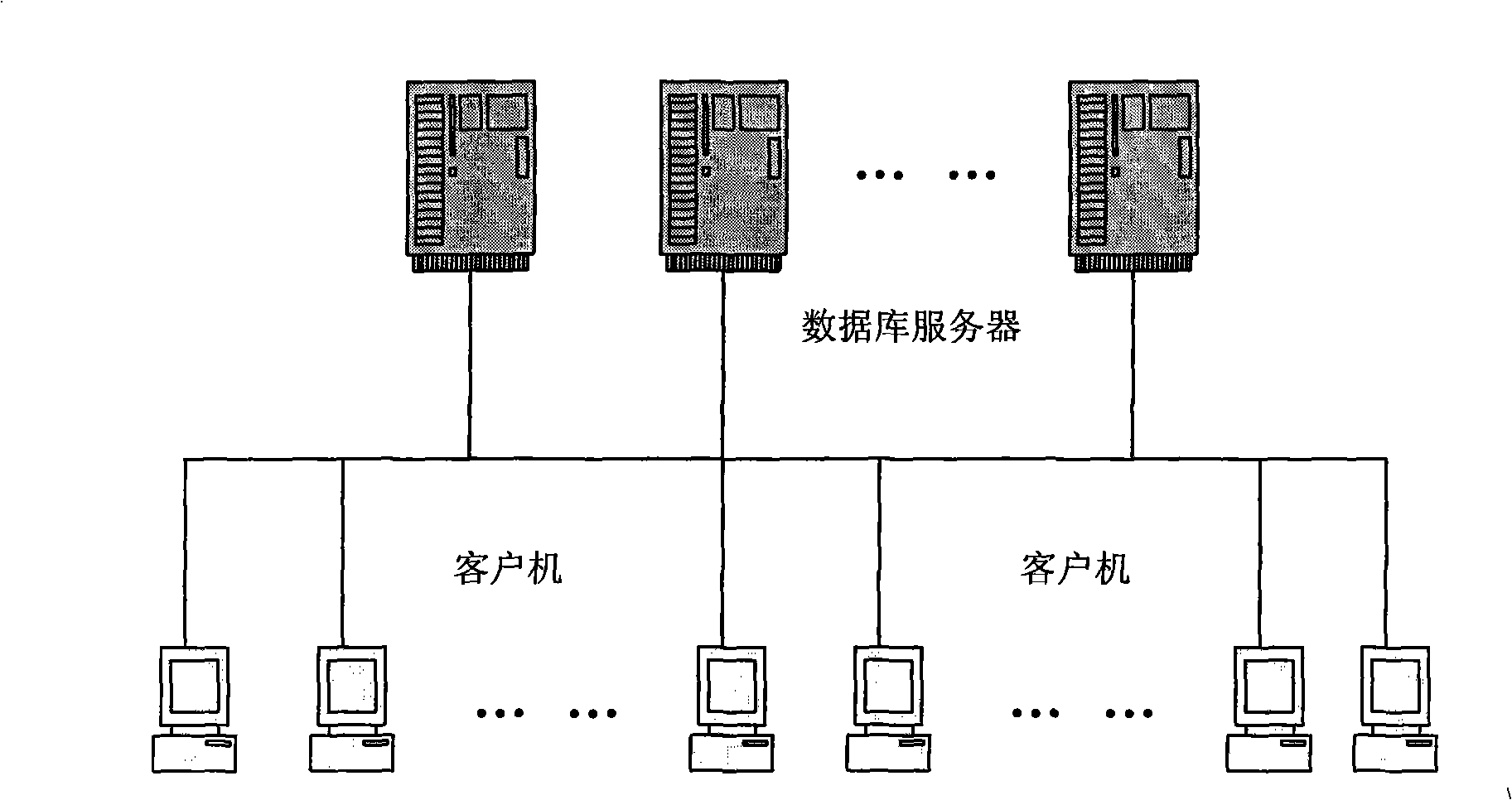
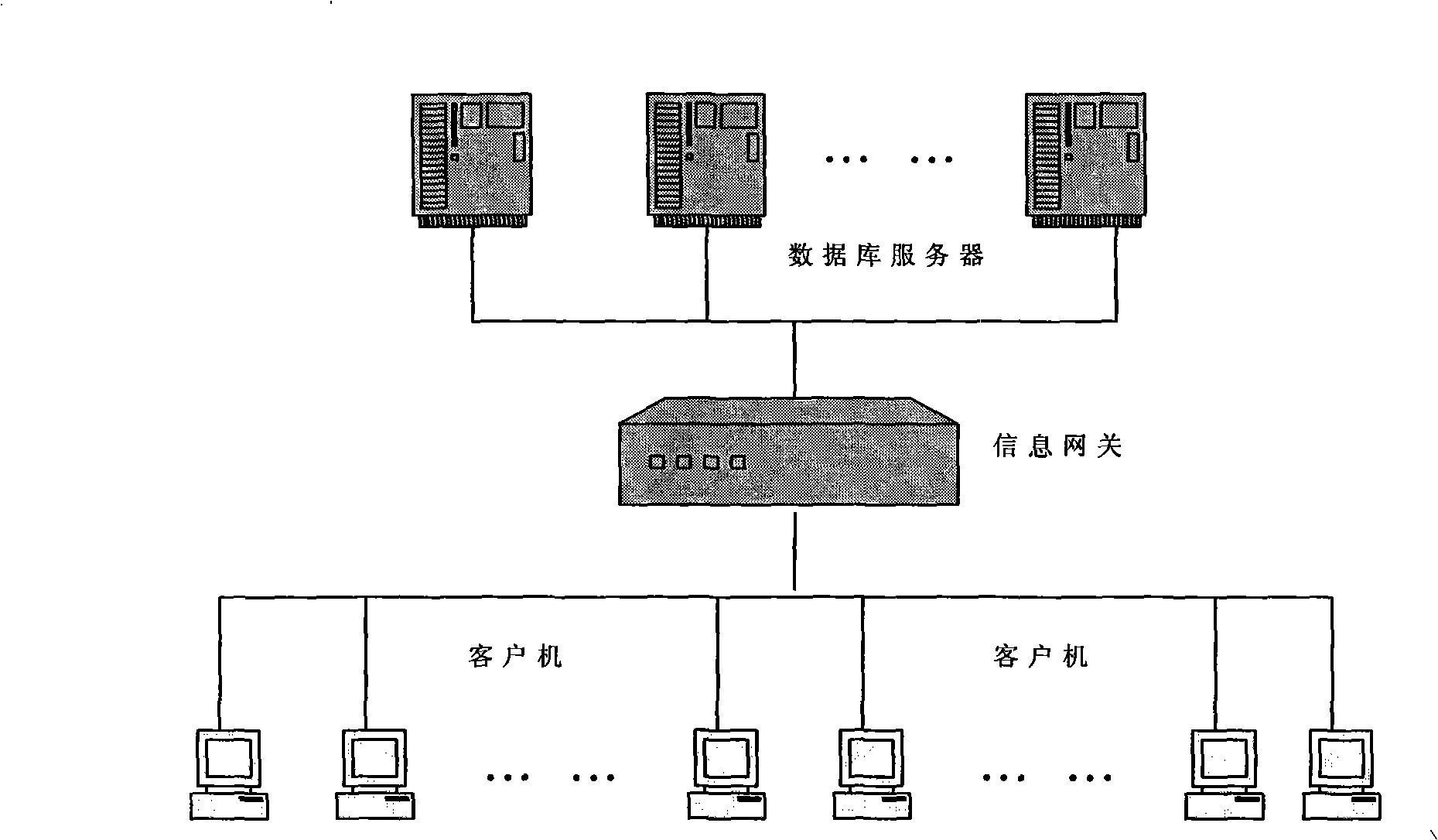
[0039] The information gateway of the embodiment of the present invention--the internal control security method of the business support system, comprises the following steps:
[0040] Step 1. Network segment isolation: blocking the communication between the client and the database at the network layer;
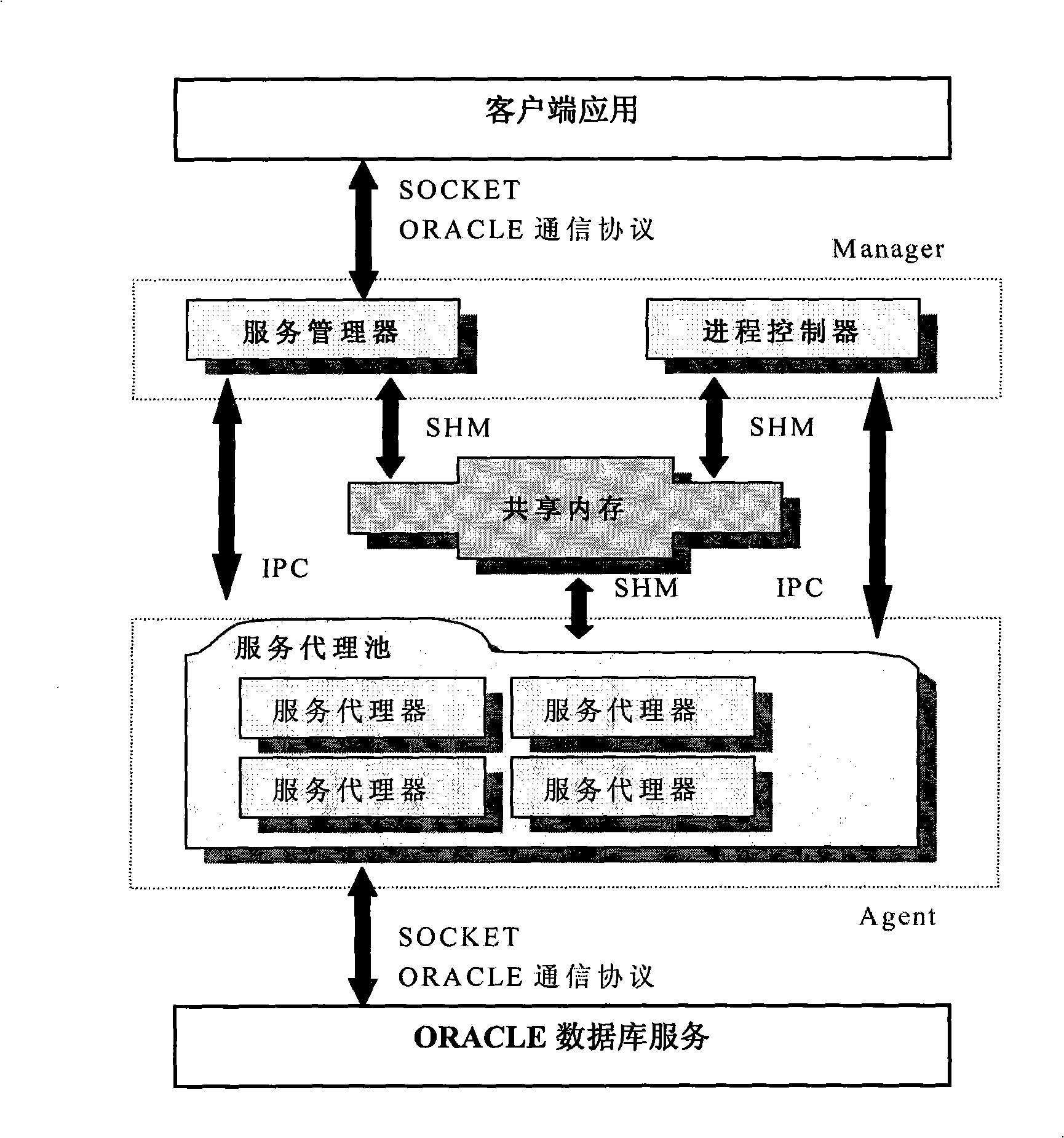
[0041] Step 2, setting up the information gateway agent system;
[0042] Step 3, client authentication and authentication;
[0043] Step 4, agent database connection and information forwarding;
[0044] Step 5. Intercept the communication packet, record the database connection behavior and information access behavior;
[0045] Step 6. Regularly conduct post-event security checks according to the security log, and take relevant security measures in a timely manner;
[0046] The technical features of the above-mentioned "Information Gateway-Internal C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com