Method for household base station access control
A technology of access control and home base station, applied in access restriction, wireless communication, transmission system, etc., can solve problems such as no solution, user deletion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
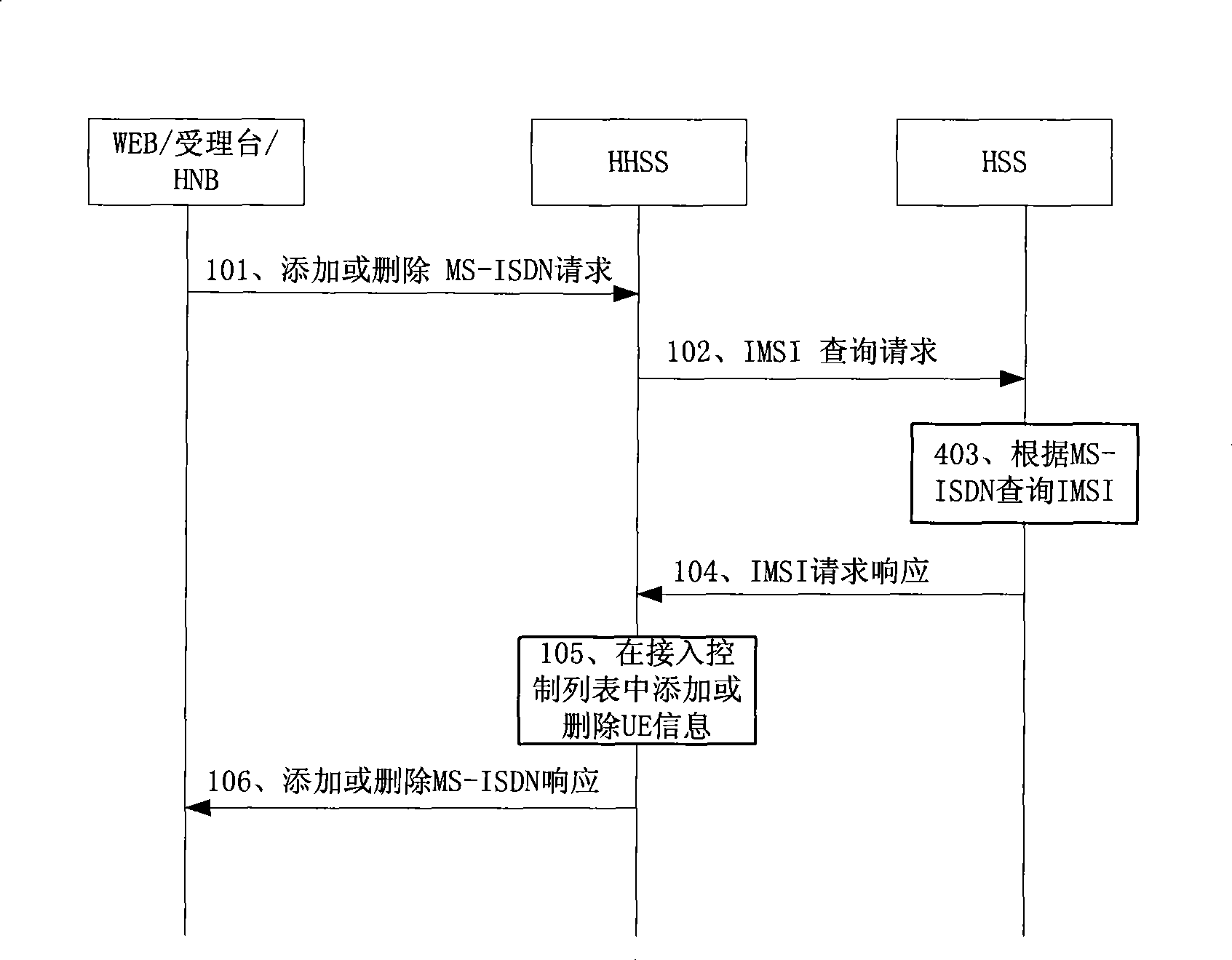
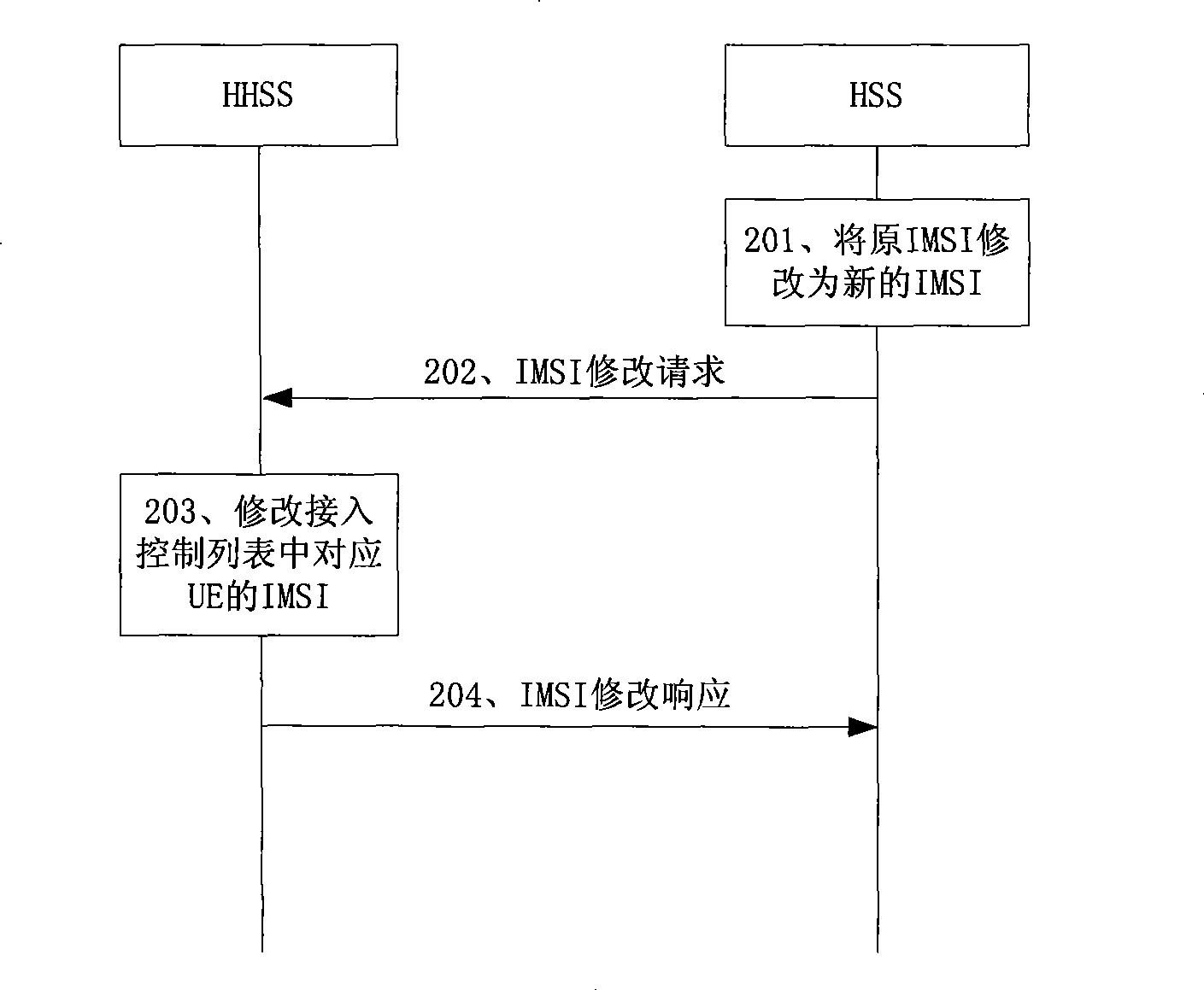
[0022] Embodiment 1 of the present invention provides a method for the HHSS or the HSS to update the access control list of the HNB.
[0023] The first case occurs when the user uses the UE's MS-ISDN to configure the access control list. The HHSS on the network side stores the subscription information of the HNB, including: security information, the identity of the HNB, the identity of the CSG to which the HNB belongs (CSG Identity, CSG ID), and the UE access control list related to each CSG.
[0024] The CSG may include one or more HNBs, and for multiple HNBs, their access control lists may be the same. Therefore, an access control list can be maintained for each CSG on the HHSS, that is, each access control list is identified by a different CSG ID. The HHSS does not need to maintain its access control list for all HNBs belonging to a CSG, it only needs to maintain the access control list of the CSG. Alternatively, an access control list can also be maintained for each HNB ...
Embodiment 2
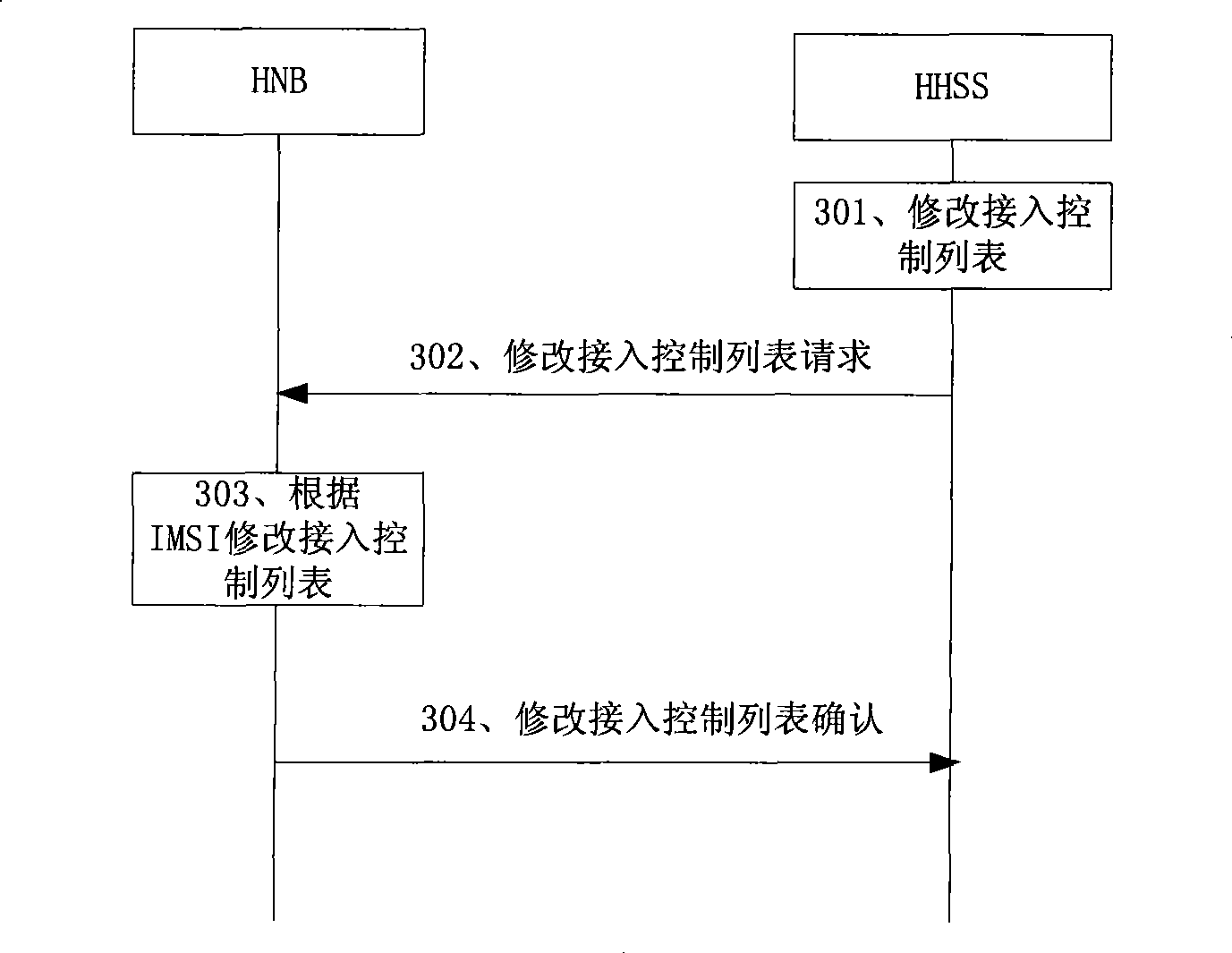
[0066] Embodiment 2 of the present invention provides a method for performing access control on a UE by using the IMSI or TMSI of the UE and the access control list, including:
[0067] When the UE is in the idle (Idle) state, the access control on the HNB is performed after the radio resource control (Radio Resource Control, RRC) connection is successfully established; when the UE is in the active (Active) state, the access control on the HNB is Followed by a switch request. The HNB acquires UE identity (IMSI or TMSI, etc.) information from the UE, compares it with the access control list stored in the HNB, and judges whether the UE is allowed to access, thereby realizing access control on the UE.
[0068] The IMSI will be used only when the UE performs an initial network attachment (Attach) after the UE is turned on, and the TMSI will be used for communication in the subsequent communication process for the sake of security. Every time the UE is powered off or its location ...
Embodiment 3
[0082] The embodiment of the present invention also provides an HNB for performing access control on the UE, the HNB includes a message sending and receiving module 501, an information storage module 502, and an access control module 503, wherein,
[0083] The message transceiving module 501 is used for receiving the request for modifying the access control list sent by the HHSS or the HSS or the SGSN.
[0084] The request for modifying the access control list above carries the information of the UE required to modify the list, and the information may carry the IMSI and TMSI of the UE, or a new identifier defined by the HHSS for the UE.
[0085] Information storage module 502: for storing access control information, and for updating the information of the information storage module.
[0086] The access control module 503 is configured to perform access control on the UE according to the access control information stored in the information storage module 502 .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com