Secure device and reader/writer
A security device and reader technology, applied in computer security devices, internal/peripheral computer component protection, record carriers used by machines, etc., to achieve the effect of reducing the storage area
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
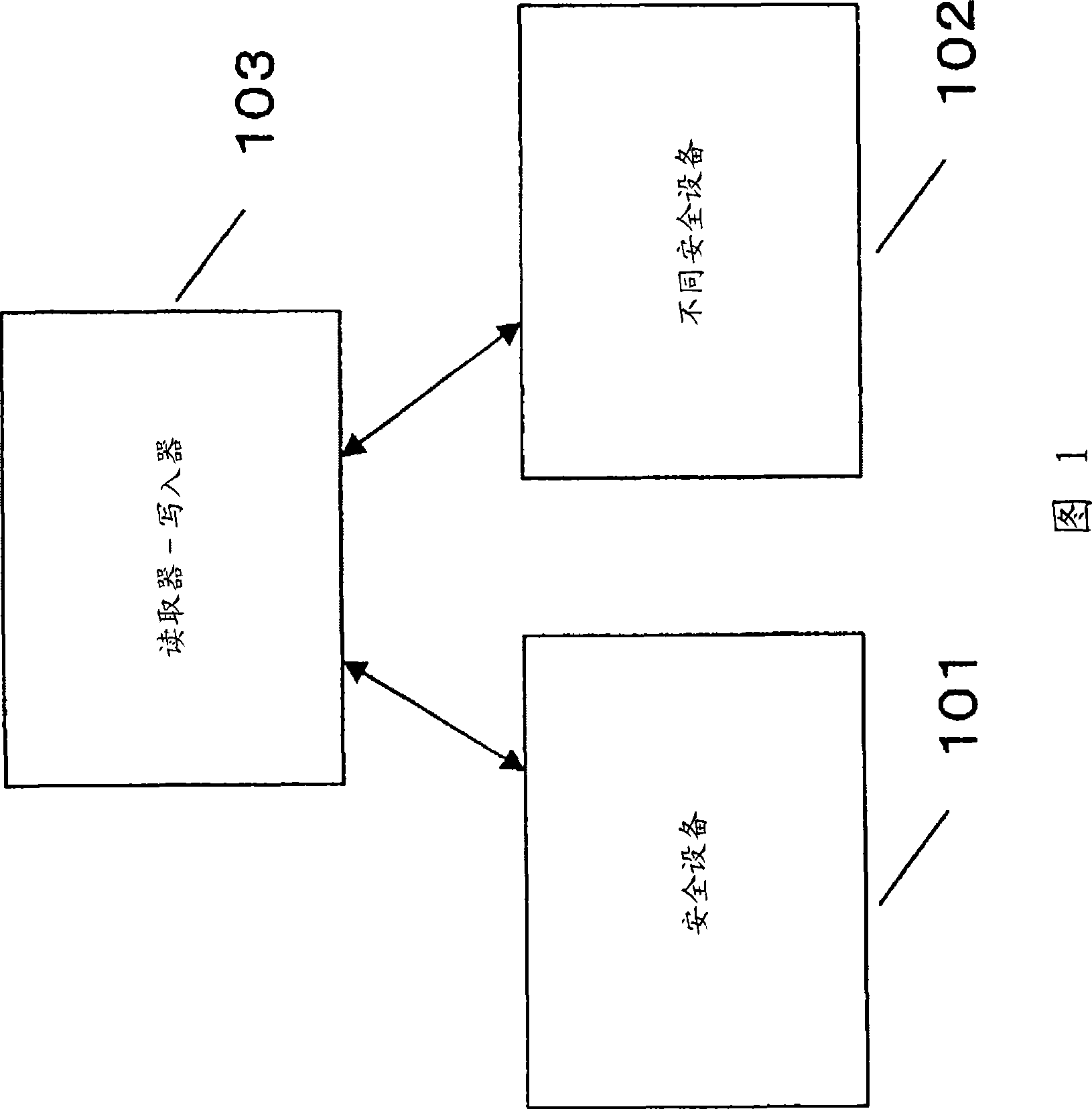
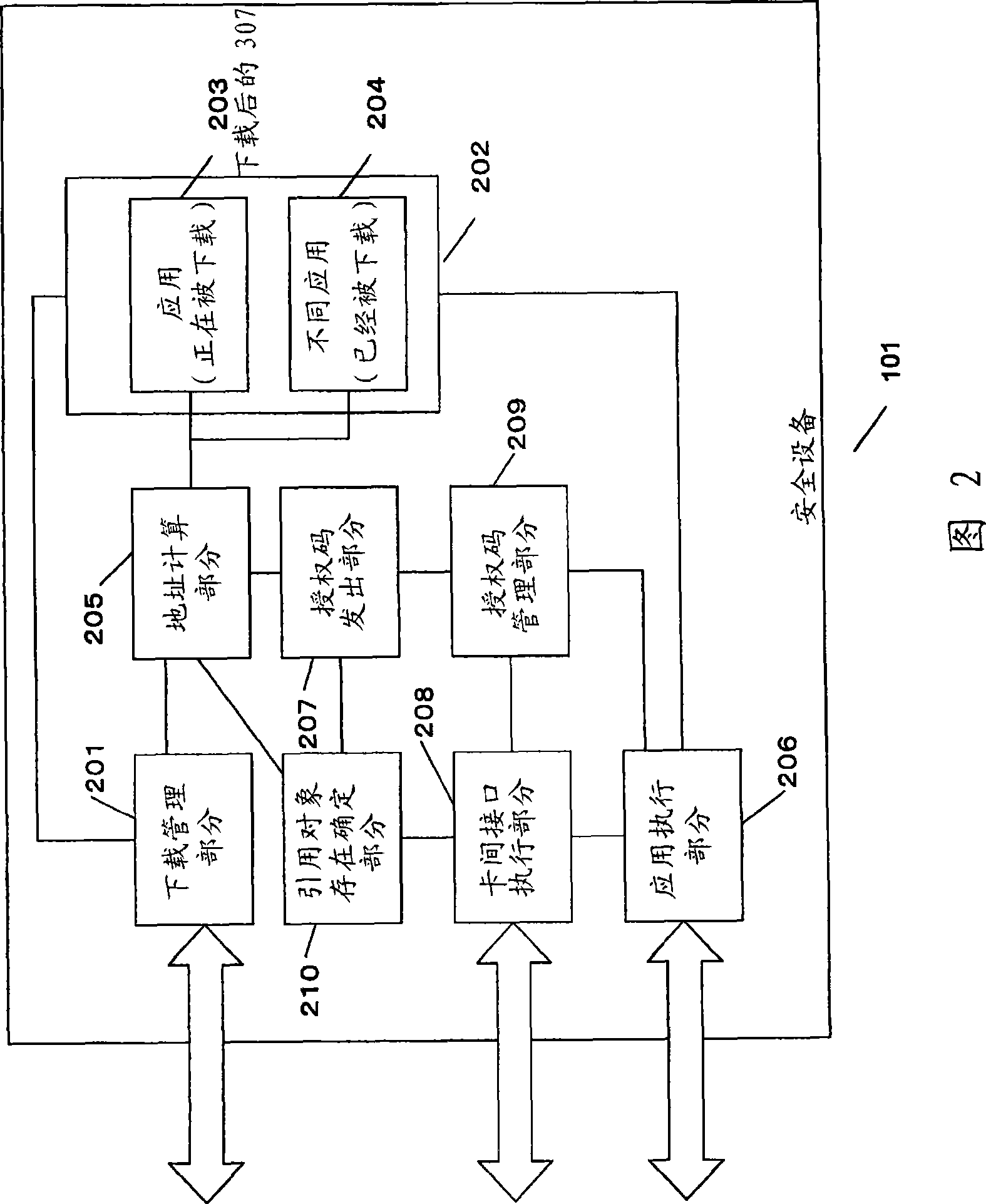
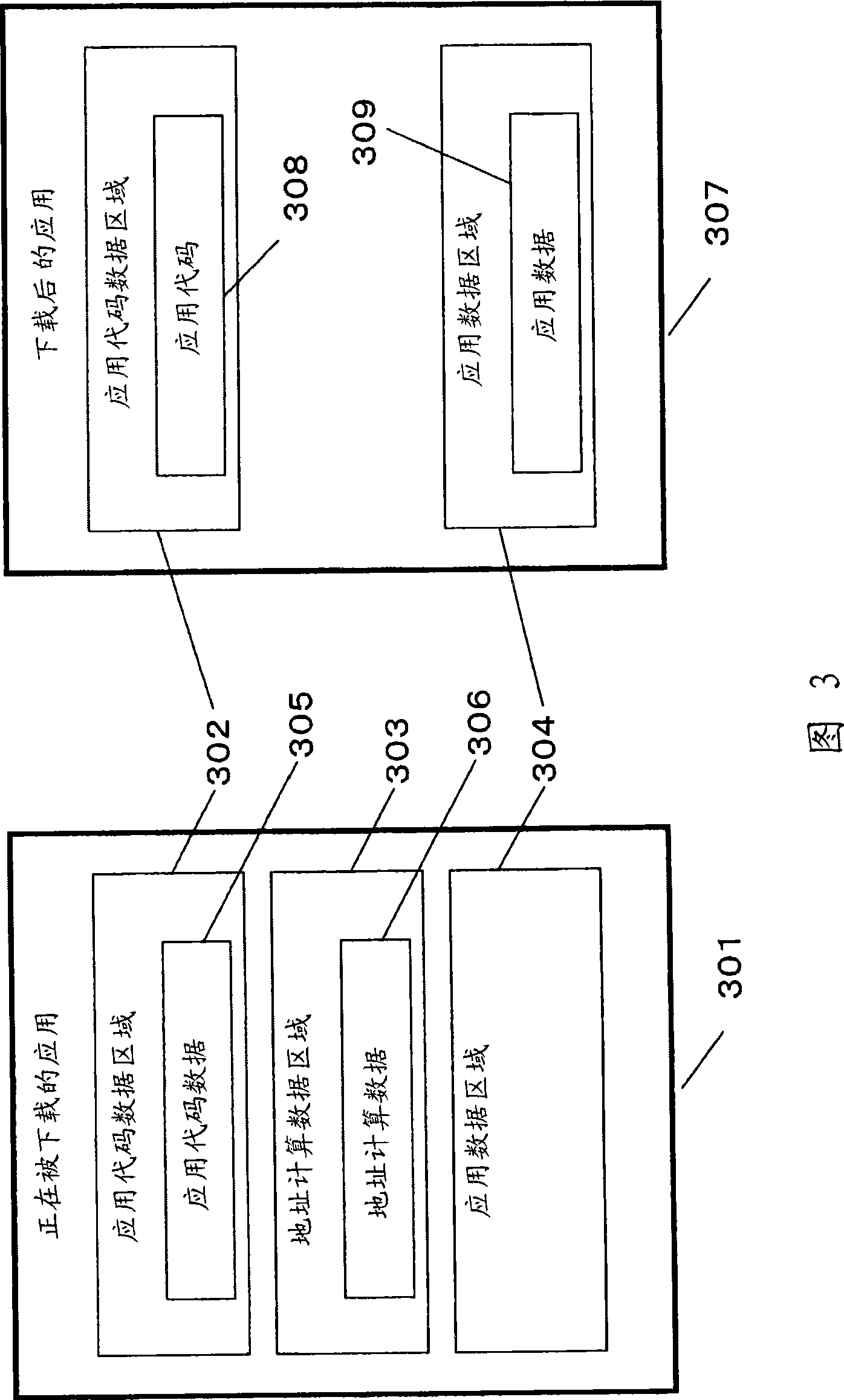
[0133] Embodiment 1 is an invention related to a security device for permitting downloading if a server application does not exist in the same card when the client application is downloaded, and when the client application is executed it is not the same as in a different card. Works in conjunction with server applications installed in .
Embodiment 2
[0134] Embodiment 2 is an invention related to a system for providing security when devices work in conjunction with each other.
Embodiment 3
[0135] Embodiment 3 is an invention related to a (first) system for checking the owner of a safety device and a different safety device when the safety device and a different safety device work in conjunction with each other. The identity of the owner of the device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com