Method for enhancing stability of intelligent cipher key equipment and intelligent cipher key equipment
A smart key device and smart key technology are applied to a method for improving the stability of smart key devices and the field of smart key devices, which can solve instability, delay command processing, and reduce the stability of smart key devices and computers. Sex and other issues to achieve safe use and improve stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
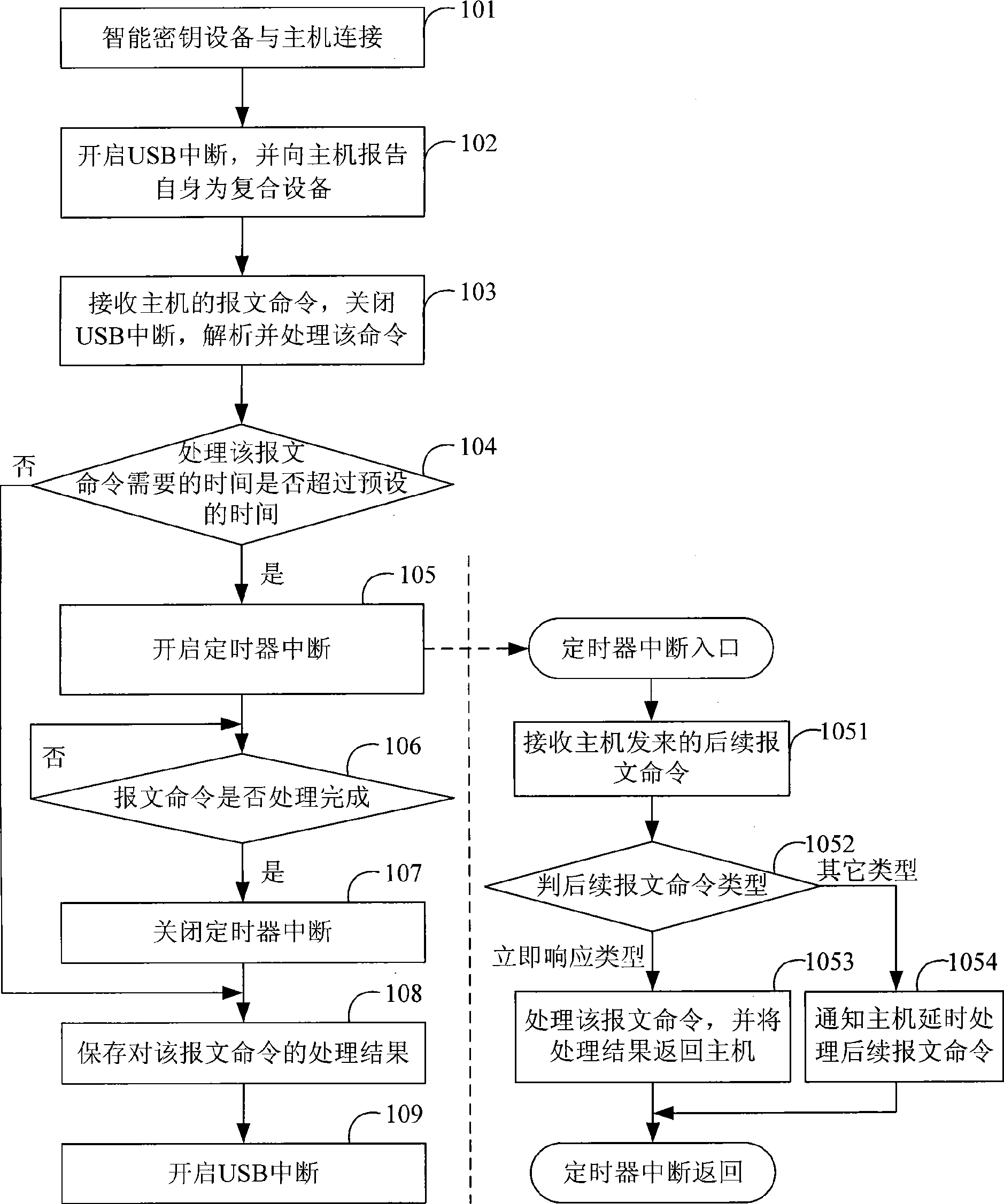
[0056] see figure 1 , this embodiment provides a method for improving the stability of the smart key device. In this embodiment, the composite device declared by the smart key device contains multiple virtual devices of different types. The method specifically includes:
[0057] Step 101: the smart key device is connected to the host;
[0058] Step 102: The smart key device starts the first interrupt, which is specifically the USB interrupt in this embodiment, and reports itself to the host as a composite device. In this embodiment, the composite device includes two virtual devices, a SCSI device and a HID device, as an example Be explained;
[0059] Step 103: the smart key device receives the message command sent by the host, closes the USB interrupt, parses and processes the message command;
[0060] Step 104: The smart key device judges whether the time required to process the message command exceeds the preset time, if yes, then considers that the message command needs t...
Embodiment 2
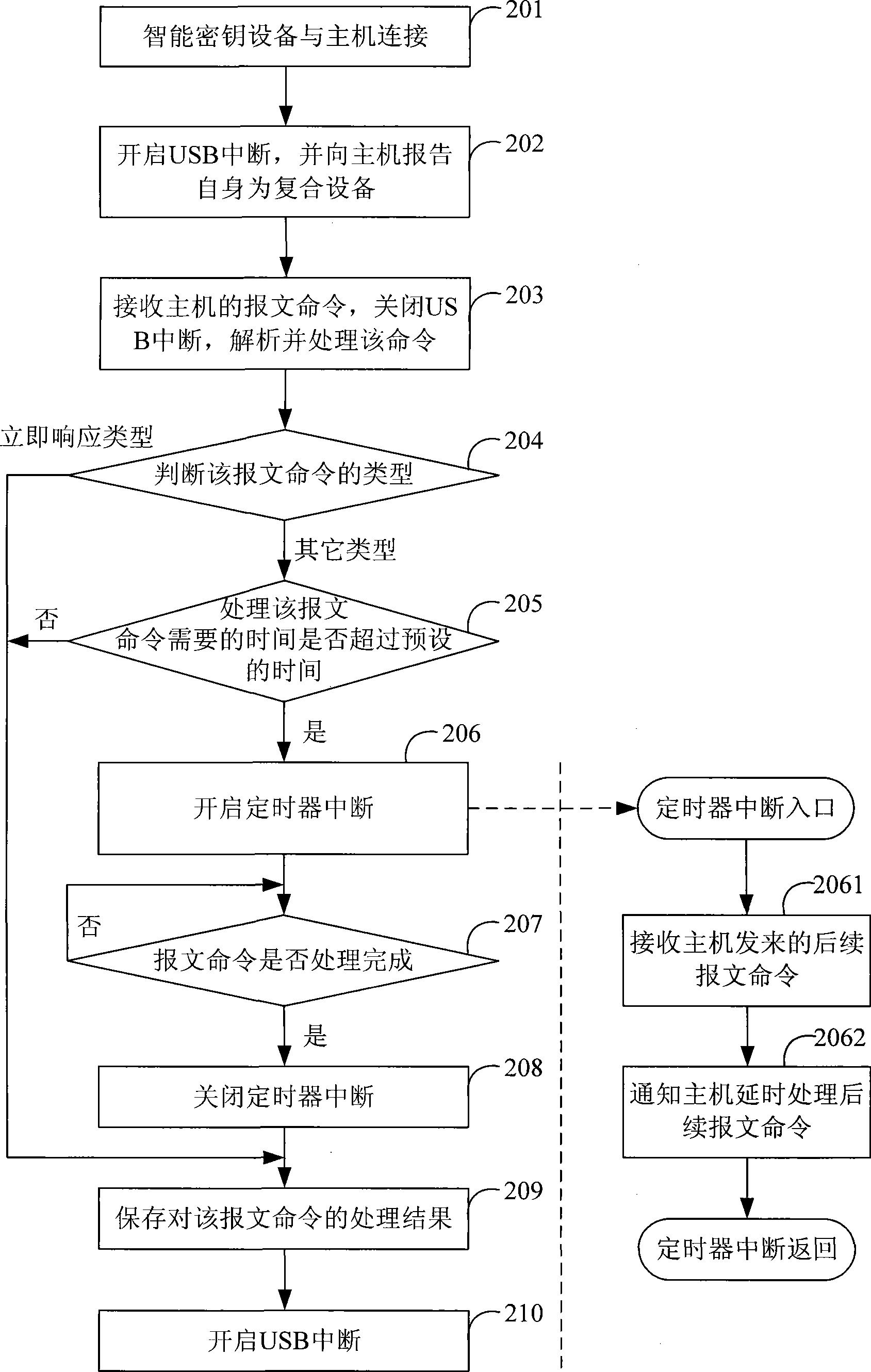
[0076] see figure 2 , this embodiment provides a method for improving the stability of the smart key device. In this embodiment, the compound device declared by the smart key device contains multiple virtual devices of the same type. The method specifically includes:
[0077] Step 201: the smart key device is connected to the host;
[0078] Step 202: The smart key device starts the first interrupt, specifically the USB interrupt in this embodiment, and reports itself to the host as a composite device. In this embodiment, the composite device includes three virtual devices: HID1 device, HID2 device and HID3 device. equipment as an example to illustrate;
[0079] Step 203: the smart key device receives the message command sent by the host, then closes the USB interrupt, parses and processes the message command;
[0080] Step 204: The smart key device judges the type of the message command according to the type of the virtual device, if the message command is an immediate resp...
Embodiment 3
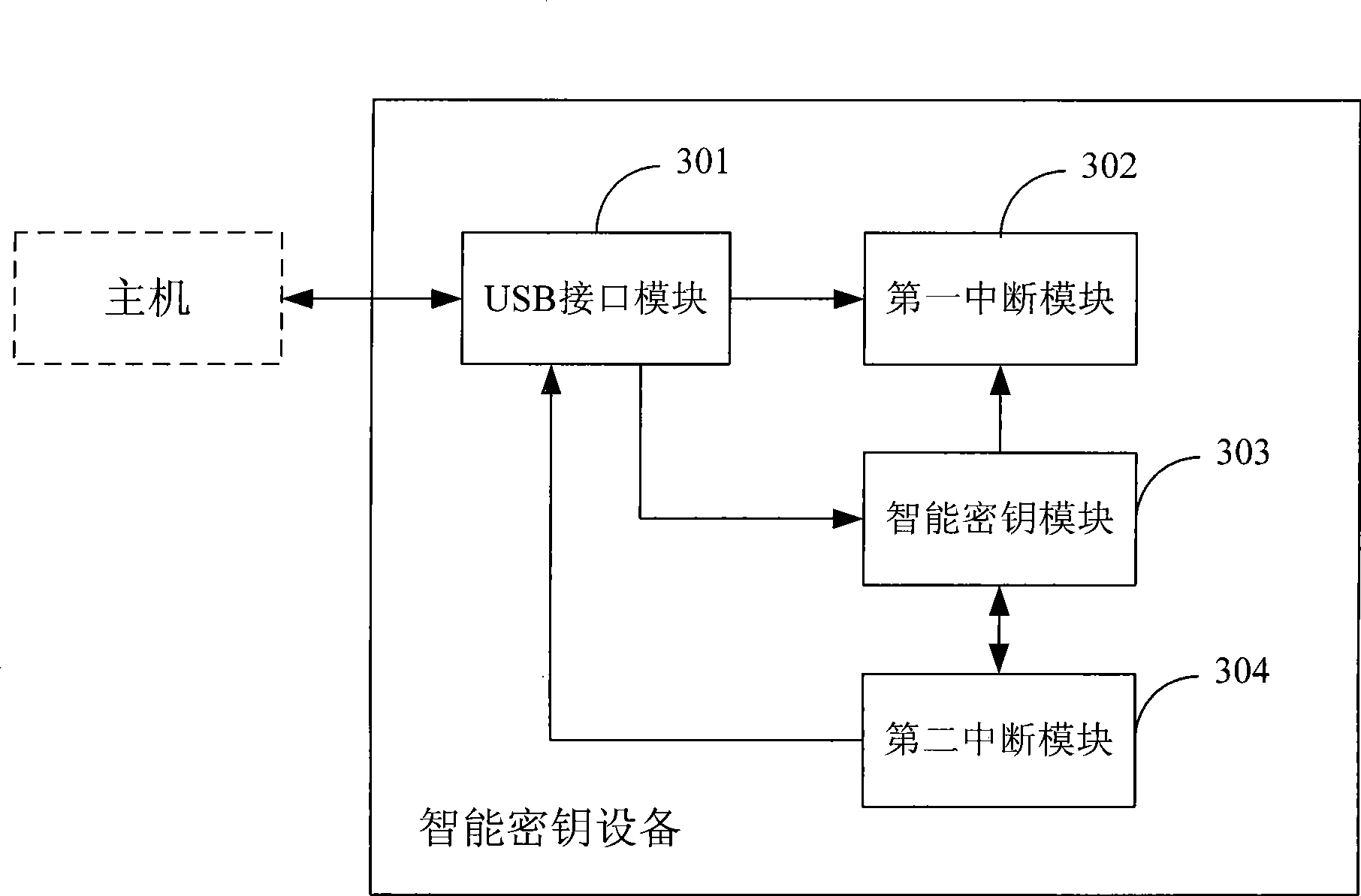
[0093] see image 3 , the embodiment of the present invention provides a smart key device, including:
[0094] The USB interface module 301 is used to establish a connection between the smart key device and the host;
[0095] The first interrupt module 302 is configured to enable the first interrupt, and report to the host that the smart key device is a composite device, the composite device includes at least two virtual devices, and after the USB interface module 301 receives the message command sent by the host, close the second One interrupt, open the first interrupt after receiving the notification;
[0096] The smart key module 303 is used to analyze the message command after the USB interface module 301 receives the message command, and judge whether the time required for processing the message command exceeds the preset time, if not exceed the preset time Set the time, then process the message command and save the processing result, then notify the first interrupt mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com