Movable equipment based on credible embedded platform and its security storage method
A mobile device and secure storage technology, applied in computer security devices, instruments, computing, etc., can solve problems such as the inability to guarantee a reliable environment for encryption and decryption operations, and achieve the effect of solving transmission speed bottlenecks, high security, and highly secure data storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
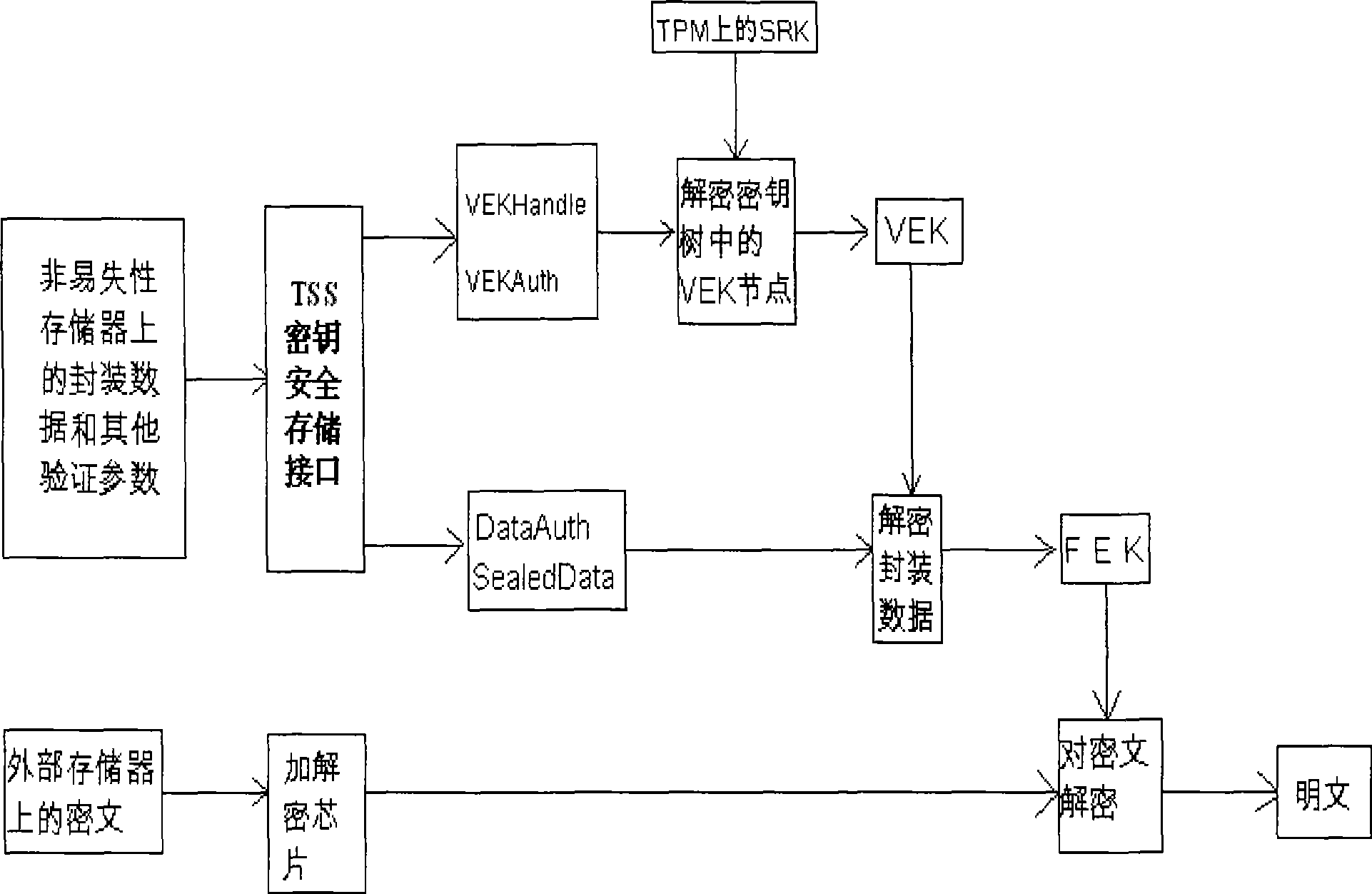
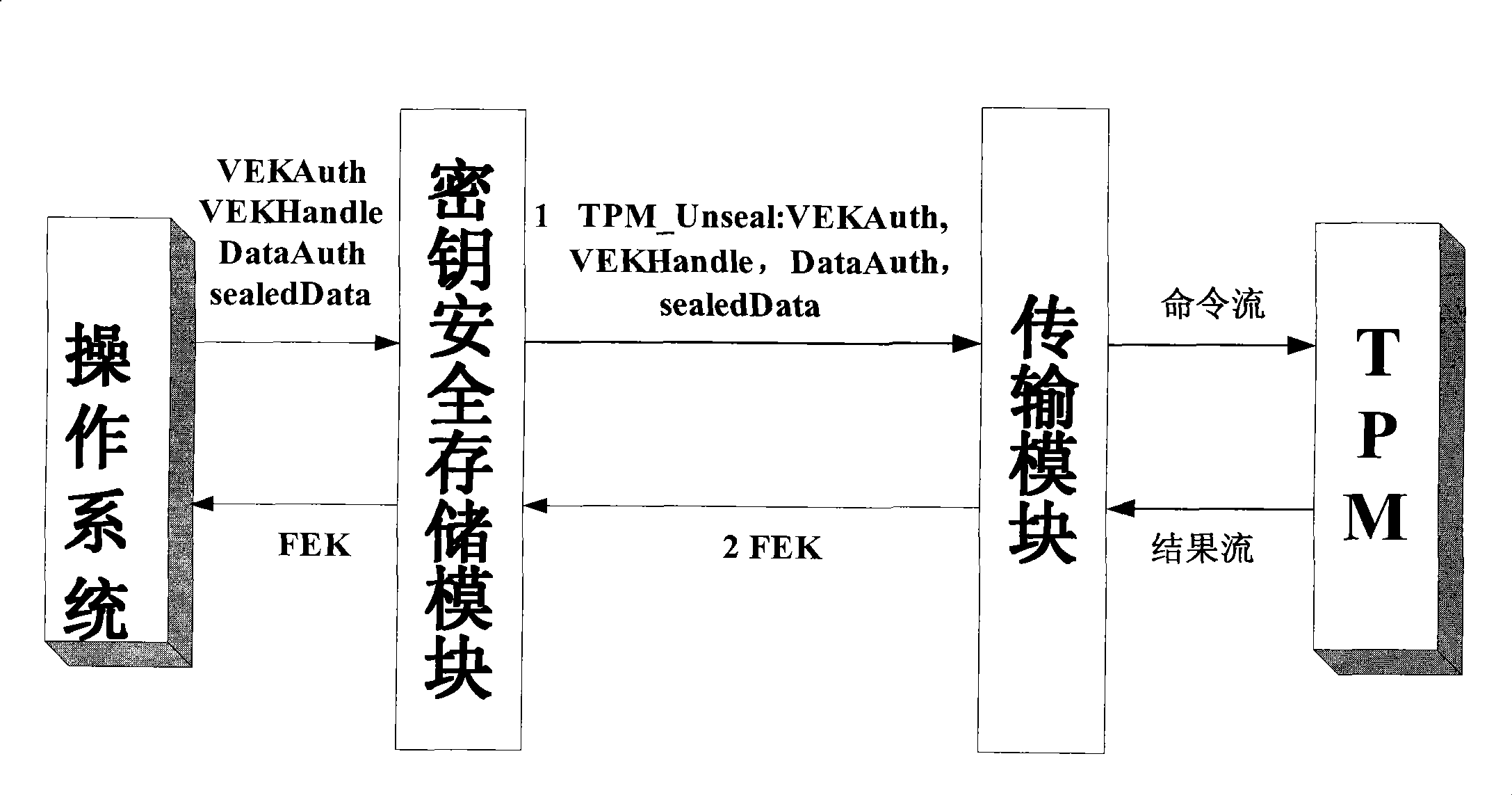
[0064] like Figure 4 As shown, the mobile device of the present invention includes an embedded platform, an encryption and decryption chip made by FPGA, and also includes a TPM module. Embedded platform, TPM module, encryption and decryption chip are connected through internal high-speed bus. The embedded platform includes CPU, non-volatile memory Nand Flash. The TPM module and the encryption and decryption chip constitute the encryption engine. The internal bus is connected with the external bus through the bridge Bridge. External devices such as IIC bus and USB are connected to the external bus.
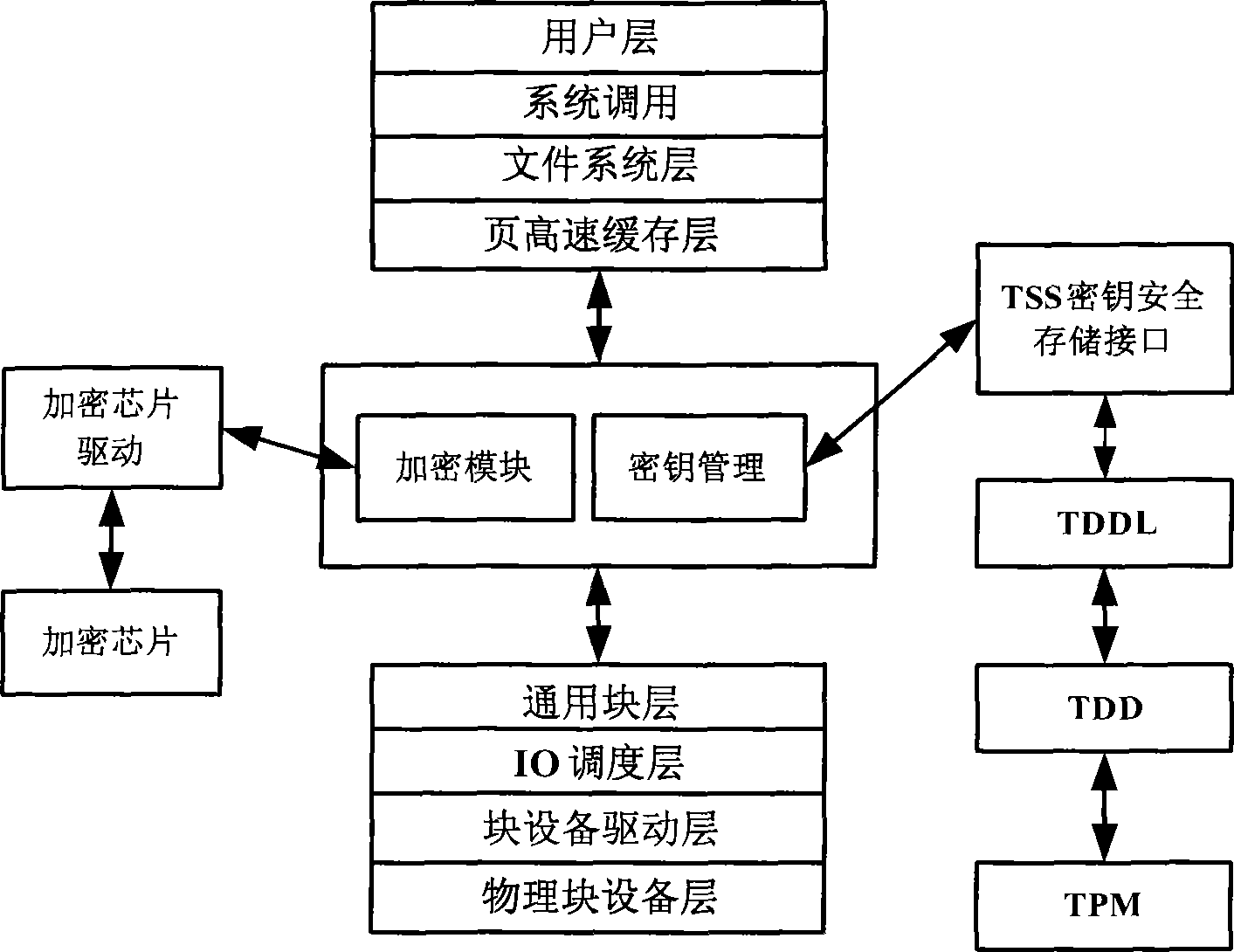
[0065] The functional architecture of this mobile device is as follows figure 1 shown. A secure storage method for mobile devices based on a trusted embedded platform includes user layer, system call layer, file system layer, page cache layer, general block layer, IO scheduling layer, block device driver layer, and physical block device layer. The user layer, the system call...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com