OBEX protocol bug excavation method and system
A vulnerability mining and protocol technology, applied in the transmission system, wireless network protocol, telephone structure, etc., can solve difficult problems such as OBEX protocol security detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
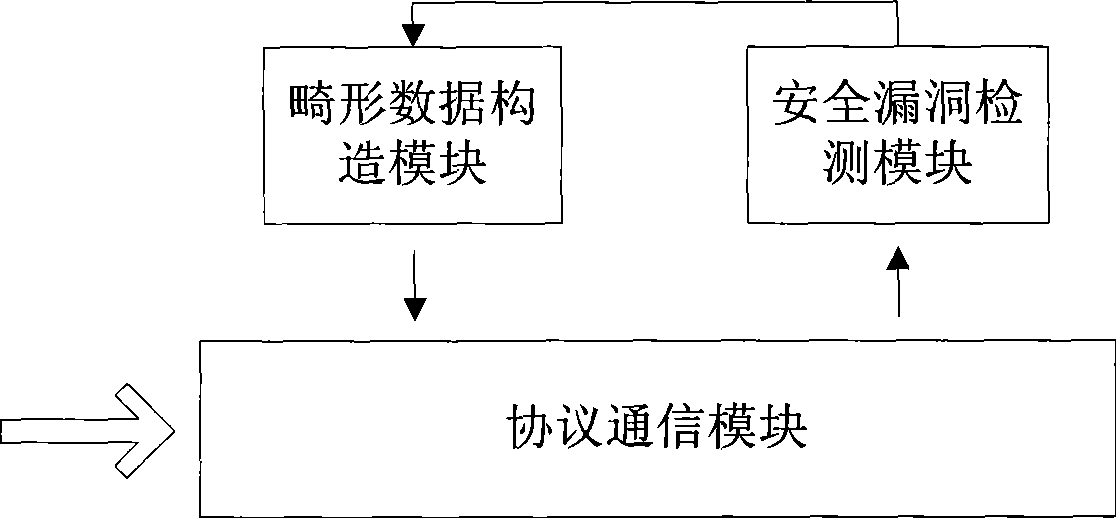
[0071] For specific implementation methods, see Figure 9 . The first thing to work is the protocol communication module, which will list the current Bluetooth devices that can be tested for vulnerabilities for users to choose. During a complete test, the user can only select one target Bluetooth device for testing. After the user's selection, the program enters the substantive testing phase. The substantive testing phase is composed of multiple loops between the malformed data construction module, the protocol communication module and the security hole detection module. Each cycle completes the independent testing process of a certain type of vulnerability at a certain vulnerable point in the OBEX protocol.
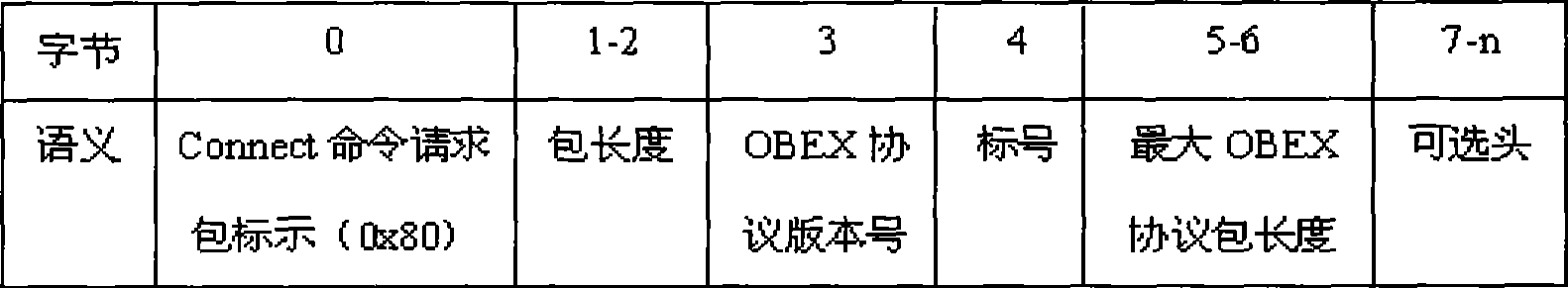
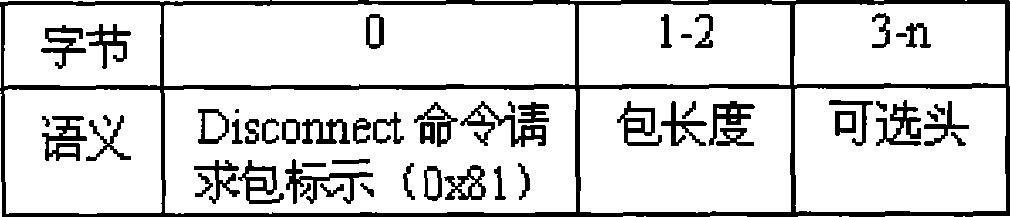
[0072] The malformed data construction module is responsible for generating malformed data packets for the vulnerability of the OBEX protocol. Then, the protocol communication module is responsible for communicating with the target Bluetooth device, and transmits the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com