Method, device and system for installing software
A technology of software installation and software, which is applied in the computer field, can solve problems such as illegal copying of software, leakage of user secrets, and loss of users, and achieve the effects of copyright protection, avoidance of leakage, and protection of interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
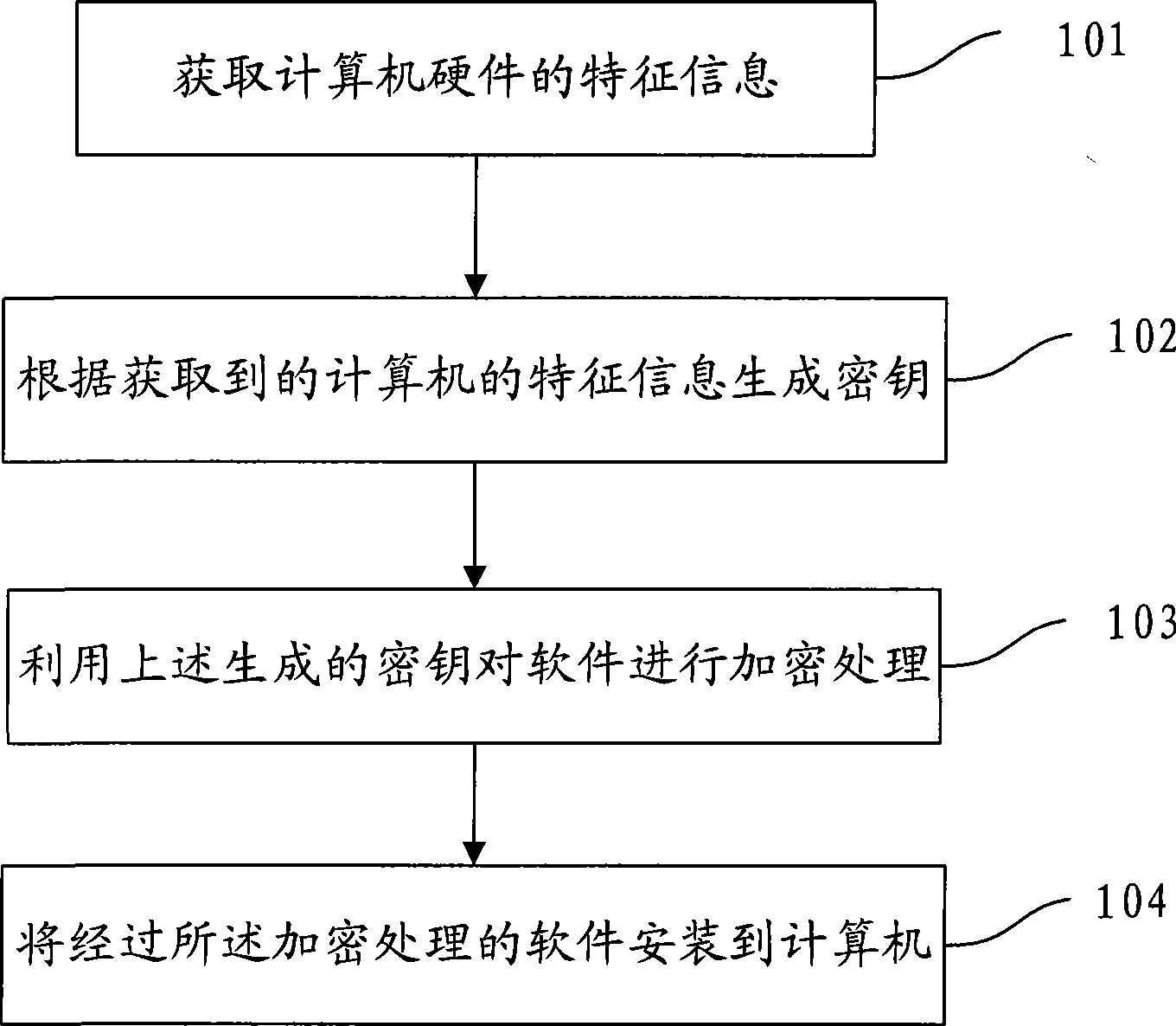
[0029] In order to make the software installed on the computer difficult to be illegally copied to other computers for use, the embodiment of the present invention provides a software installation method, such as figure 1 As shown, the method includes:
[0030] 101. Obtain the feature information of the computer hardware after starting the software installation program. The installation program mentioned here generally needs to complete the installation process. For example, the currently commonly used setup.exe program is the installation program mentioned in this embodiment.
[0031] 102. Generate a key according to the acquired feature information of the computer hardware according to certain rules.
[0032] 103. Use the key generated above to encrypt the software, mainly to encrypt important data in the software, such as: encrypt the kernel of the software or the user's secrets in the software.
[0033] 104. Installing the above-mentioned encrypted software on a computer,...
Embodiment 2
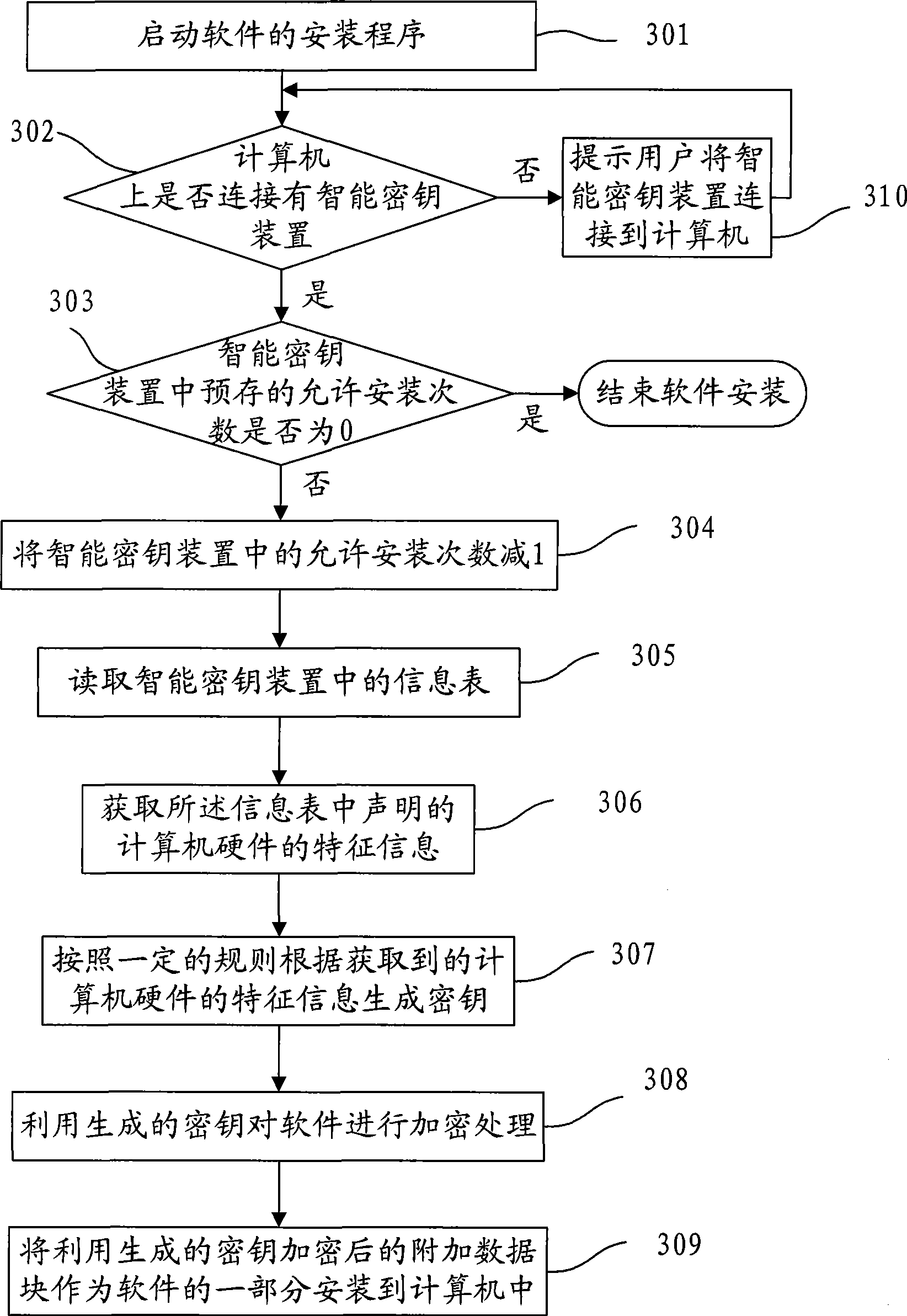
[0040] In order to introduce the technical solution adopted by the present invention more clearly, the present invention will be further described in detail below in conjunction with the software installation under the condition that the smart key device is connected to the computer. like image 3 As shown, the software installation method provided in this embodiment includes:
[0041] 301. Start the installation program of the software. The installation program mentioned here generally needs to complete the installation process. For example, the currently commonly used setup.exe program is the installation program mentioned in this embodiment.
[0042] 302. Detect whether a smart key device is connected to the computer. If there is a smart key device connected to the computer, perform the process of 303; if the computer is not connected to the smart key device, perform the process of 310.
[0043] By detecting whether the computer is connected with the smart key device, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com