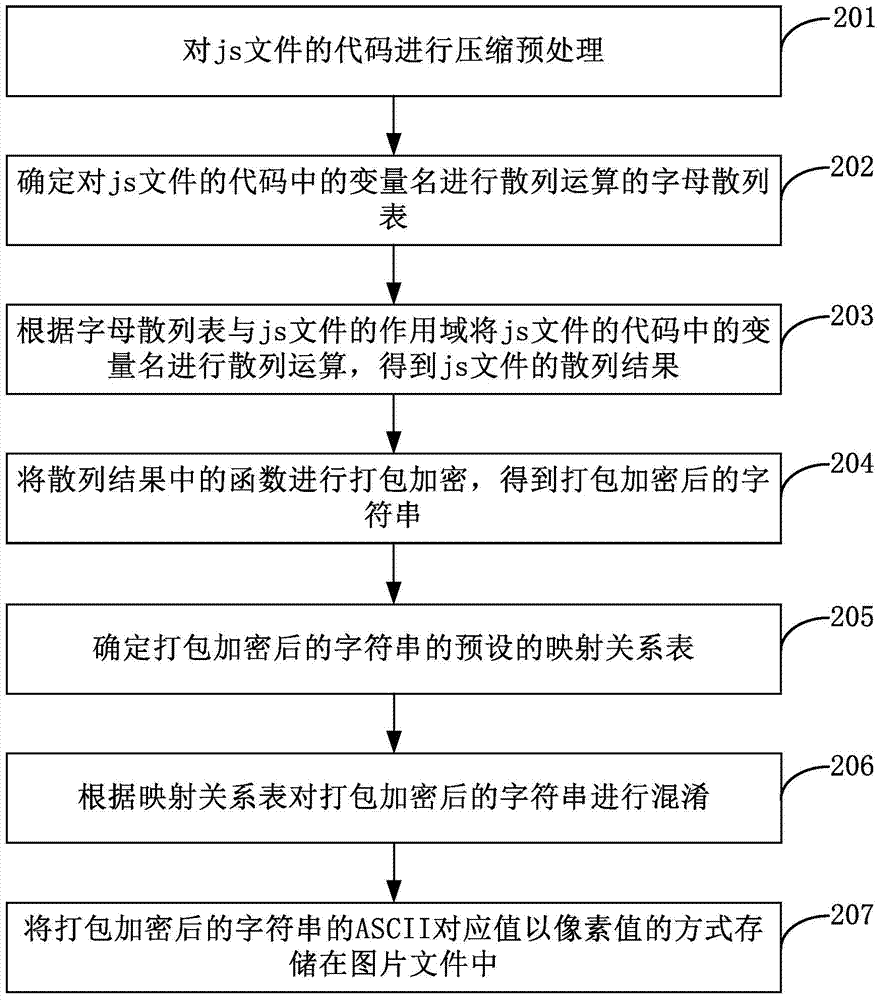
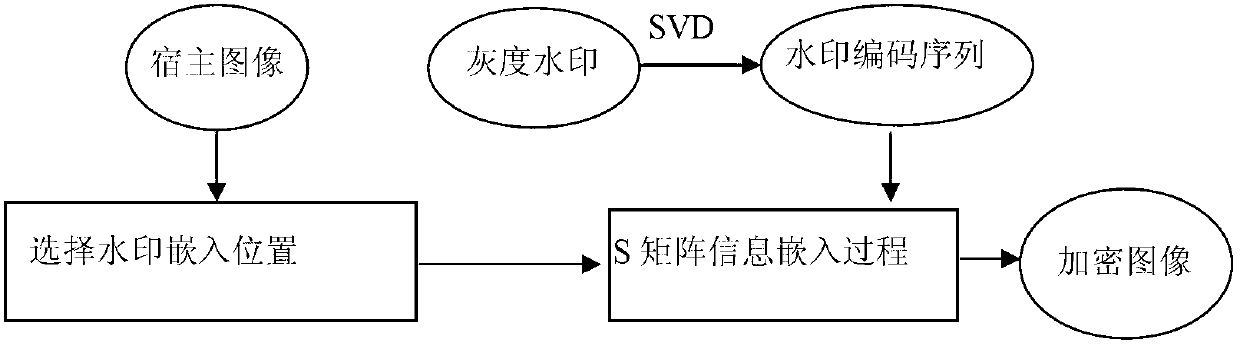
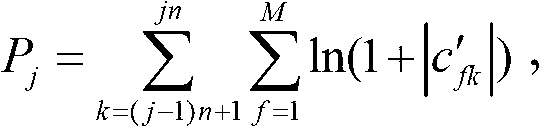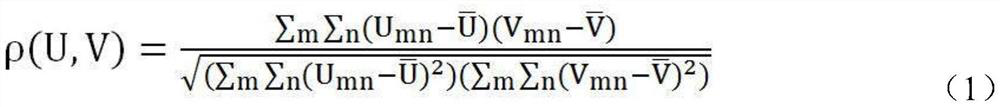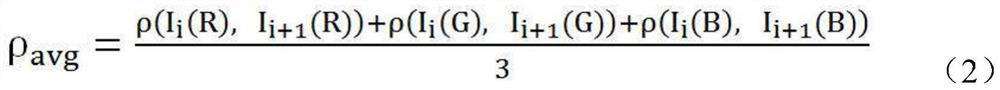Patents
Literature
72results about How to "Achieve copyright protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
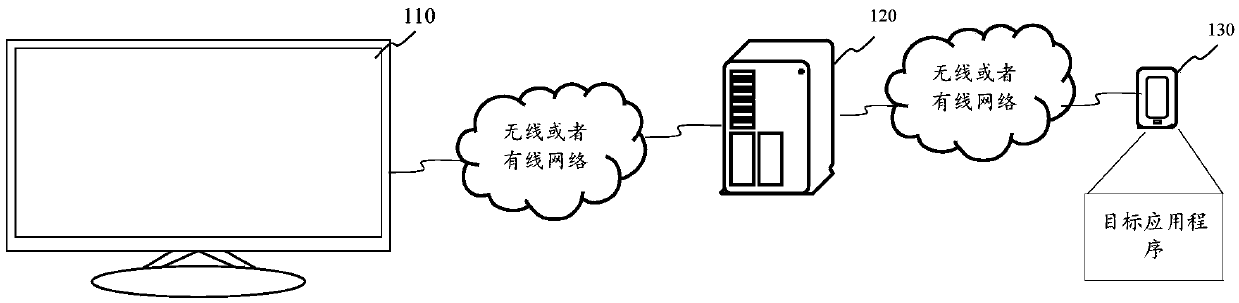
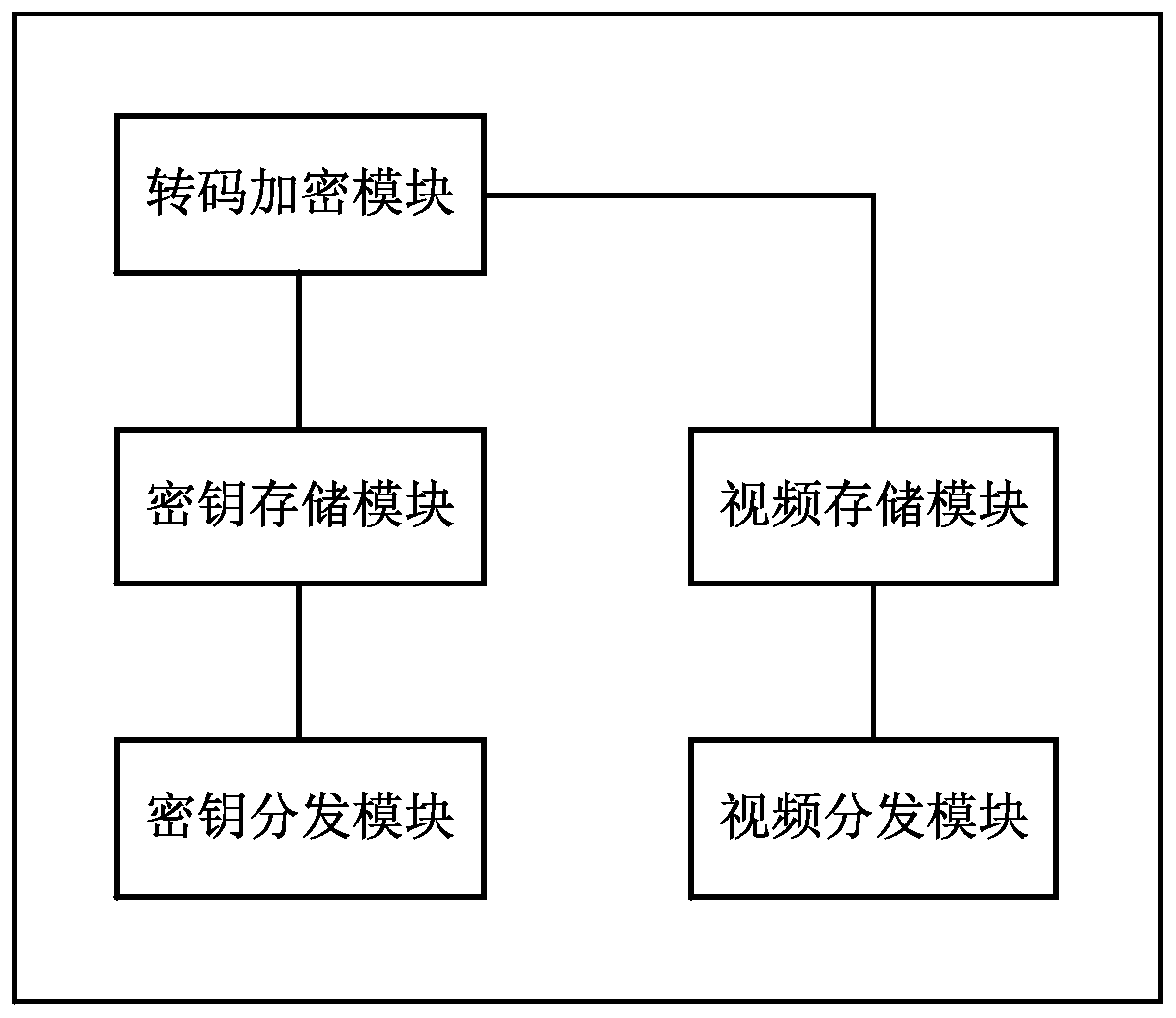
Information-processing device
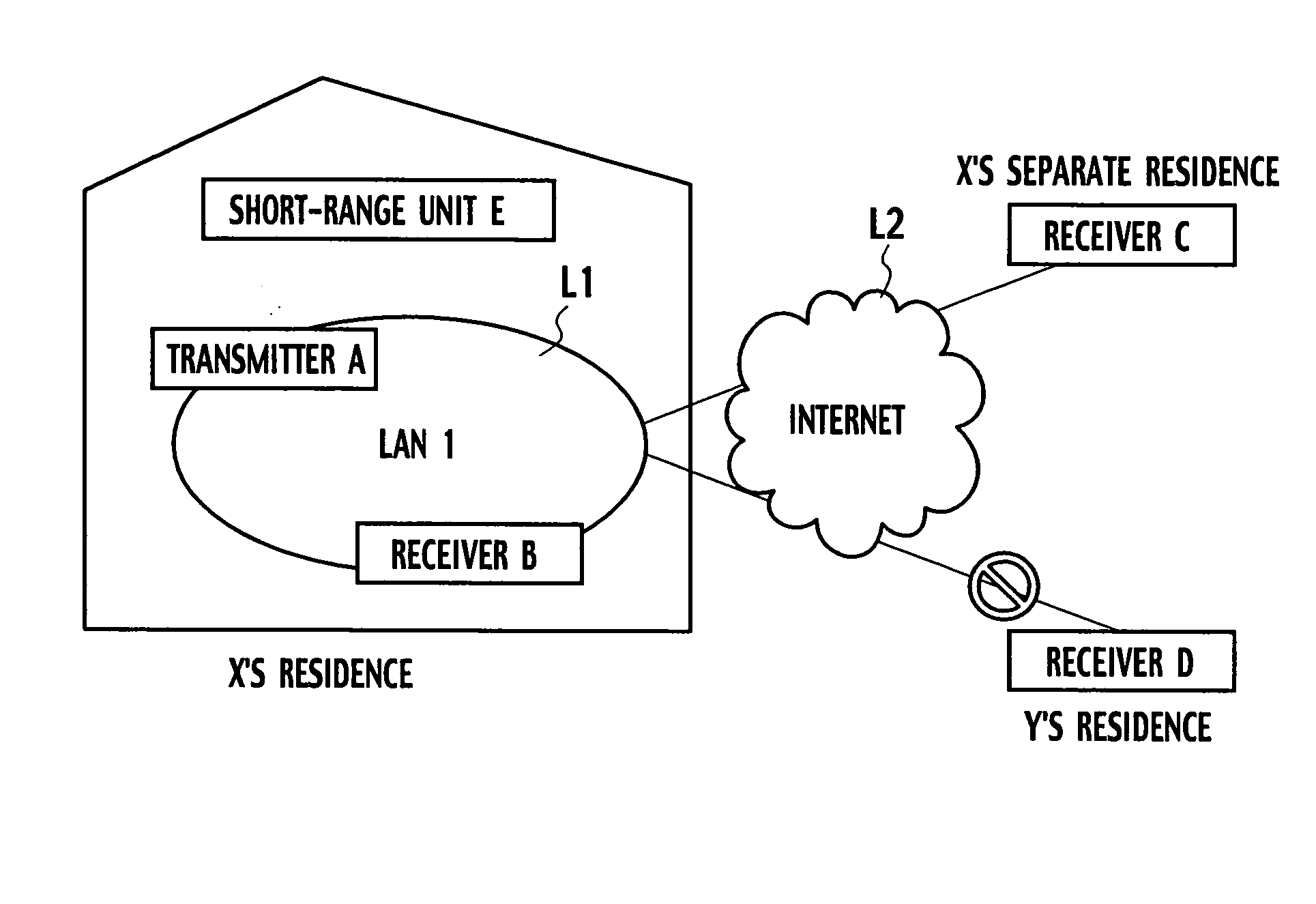
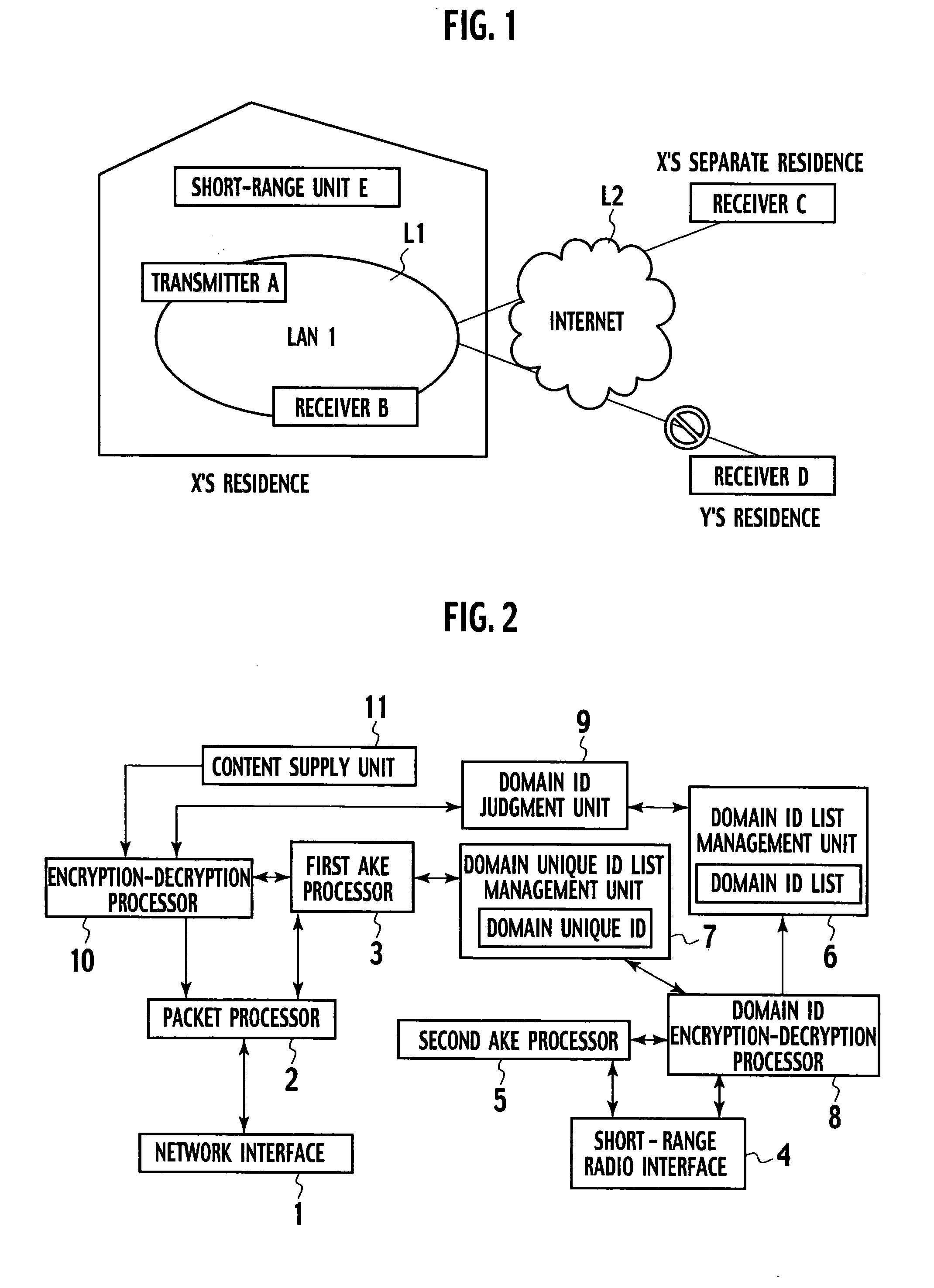
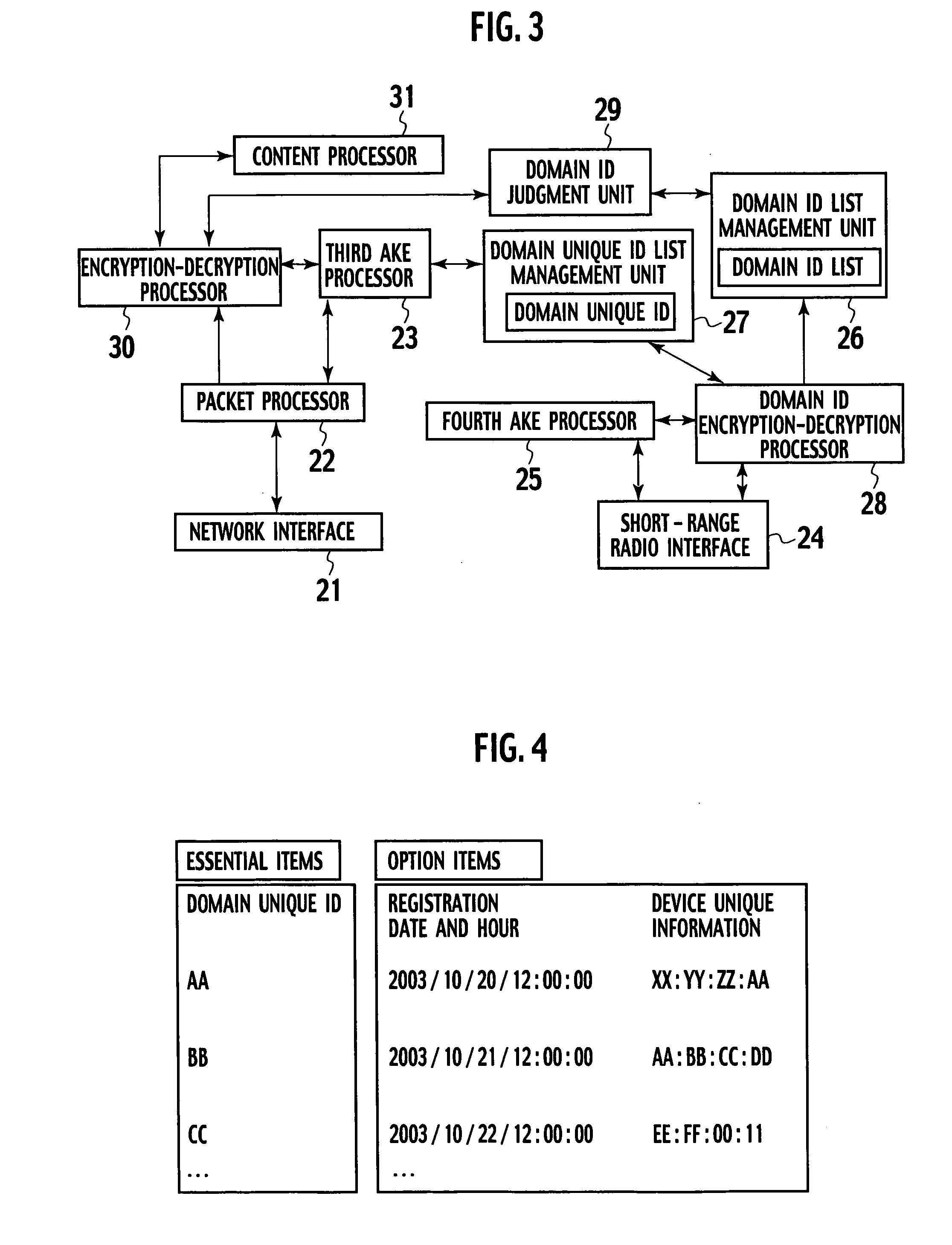
ActiveUS20050118987A1Efficient use ofAchieve copyright protectionKey distribution for secure communicationNear-field transmissionInformation processingComputer hardware
An information-processing device includes a first interface configured to transmit content to a first communication unit through a network, a second interface configured to receive a first unique identification allocated to the first communication unit from a second communication unit and transmit a second unique identification allocated to the information-processing device to the second communication unit, an identification list configured to store at least one unique identification through the second interface and an identification judgment unit configured to determine whether the first unique identification received through the first interface is stored in the identification list, wherein when the identification judgment unit determines that the unique identification of the first communication unit is stored in the identification list, the first interface allows the content to be transmitted to the first communication unit.
Owner:KK TOSHIBA
Decentralized image copyright protection system and method with infringement real-time detection
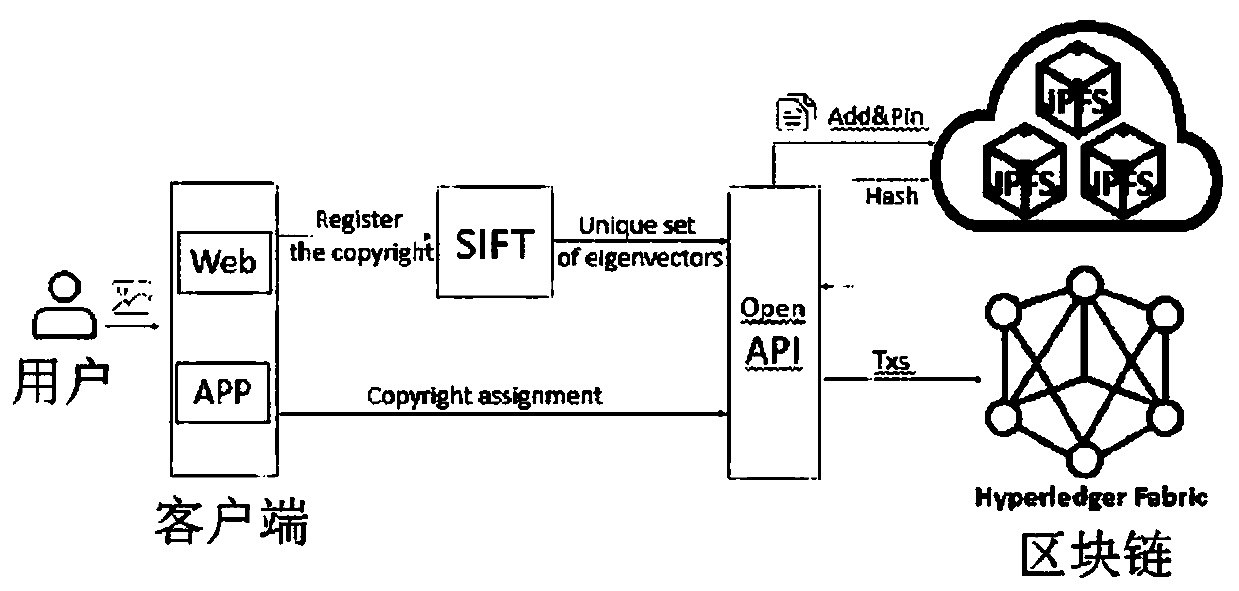
ActiveCN110110500AMeet the needs of copyright protectionGuaranteed to be authenticUser identity/authority verificationProgram/content distribution protectionTransmission protocolData set
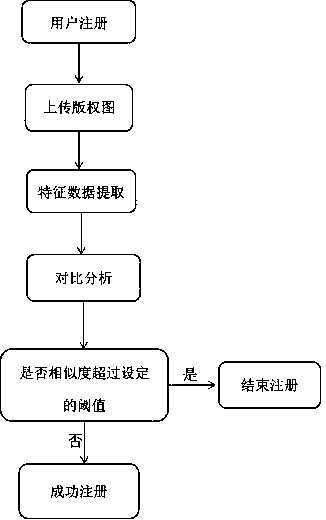
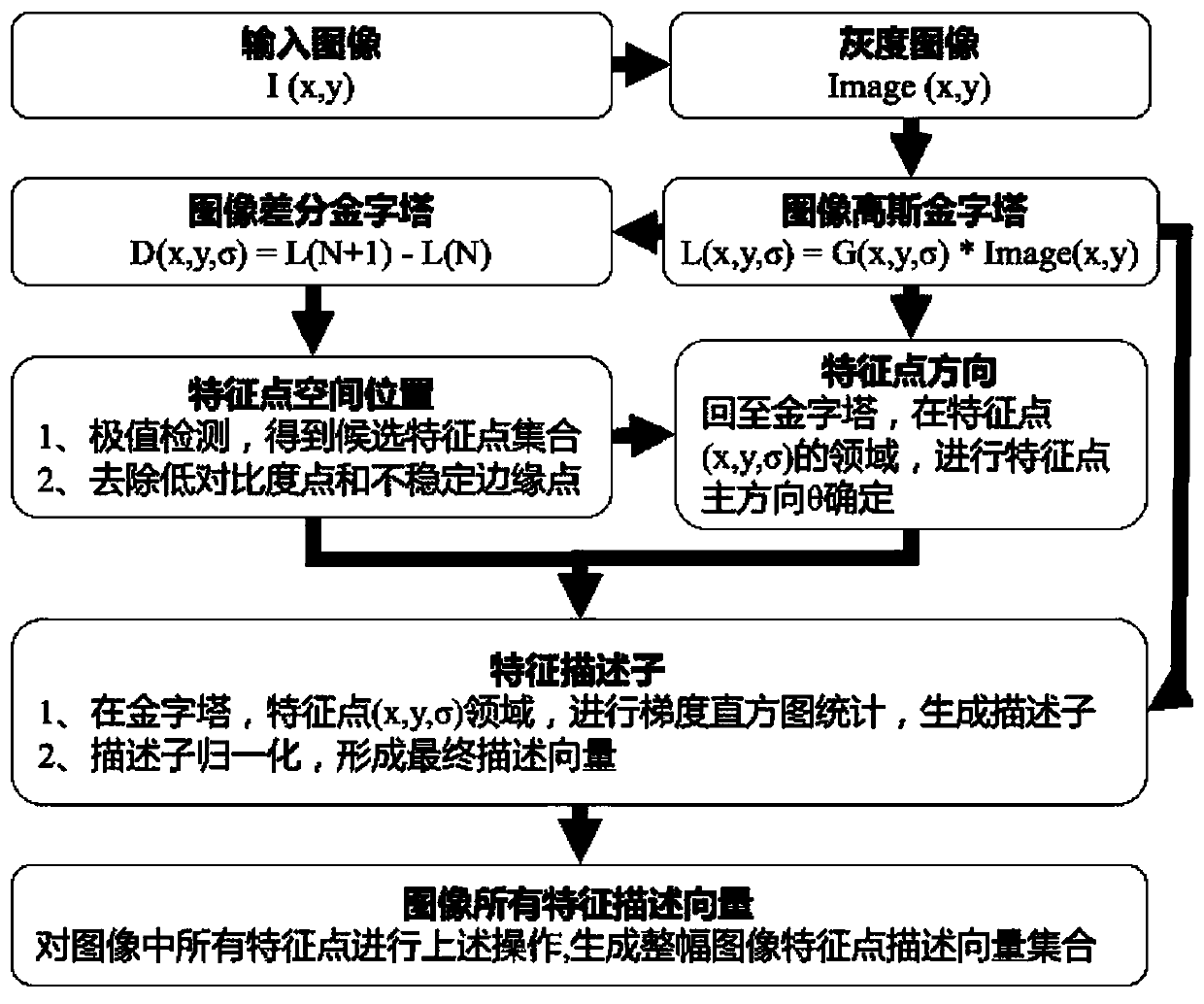
The invention relates to the technical field of copyright image protection, and provides a decentralized image copyright protection system and method with infringement real-time detection, and the method comprises the following steps of (1), enabling a registered user to upload an image through a client, and enabling an SIFT image feature extraction algorithm in the system to carry out the featuredata collection on the uploaded image; (2) extracting the invariant characteristics, such as visual angle, translation, affine, brightness, rotation, etc., of an existing copyright image by a user through an SIFT algorithm to form a local feature vector set of the image, and taking the local feature vector set as a registered image feature data set; (3) carrying out distributed storage on the feature data sets in the steps (1) and (2) by utilizing an IPFS (Internet Protocol File System), and constructing a network transmission protocol for persistent and distributed storage and file sharing;and (4) performing comparative analysis and calculation, and judging that the image does not accord with the condition of forming a new work. The system and the method provided by the invention have the characteristics of being tamper-proofing, realizing the high safety, permanent preservation and decentralization, being able to trace, being low in cost, etc.
Owner:施建锋
Copyright protection system, multimedia data transmitting and receiving equipment and method based on cloud media publishing platform
InactiveCN102170448AAvoid illegalAvoid using effectsTransmissionProgram/content distribution protectionData streamInternet users
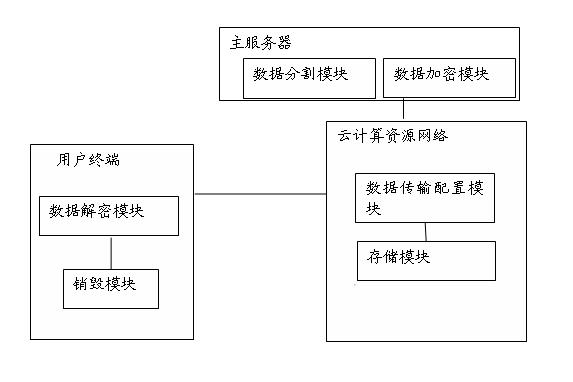
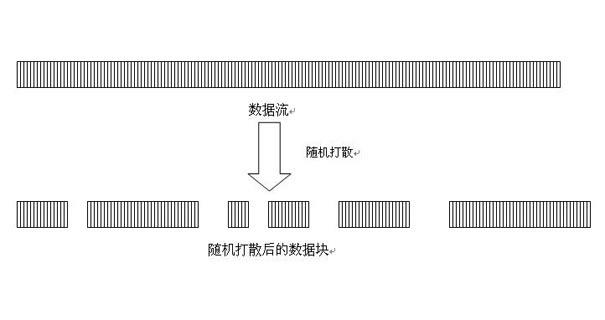
The invention discloses a copyright protection system, multimedia data transmitting and receiving equipment and a method based on a cloud media publishing platform, which are used for the technical field of information to be used for realizing that when multimedia content is published by computing the could publishing platform, the copyright protection to the published multimedia content can be safely and reliably carried out, and the content of a multimedia product can be prevented from being illegally copied or being used without authorization. When the multimedia content is published through an Internet, the content of the multimedia product is used as a data stream, the data stream is scattered, encrypted, dispersedly transmitted and then enters Internet user terminal equipment in sequence, so that the multimedia content can not allow an Internet user terminal to have a complete multimedia file at any node, and meanwhile, the data stream is subject to storage self-damage processing when being decrypted and loaded in an internal storage, so that the multimedia product can be prevented from being illegally used or being used and spread without the authorization, and further, the copyright protection of the multimedia product on the Internet can be realized.
Owner:WUXI RUISHIQING INFORMATION TECH
Infringement detection method and device for live broadcast stream
ActiveCN108881947ASpeed up query matchingPreserve timing informationCharacter and pattern recognitionSelective content distributionComputer networkGranularity
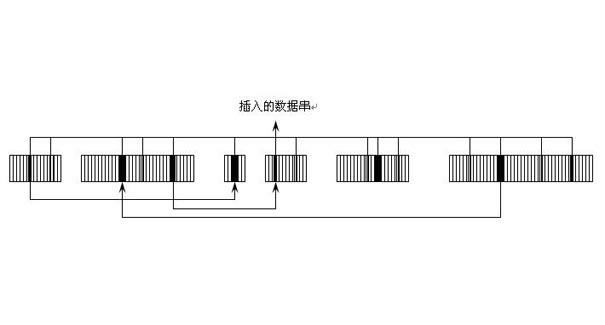
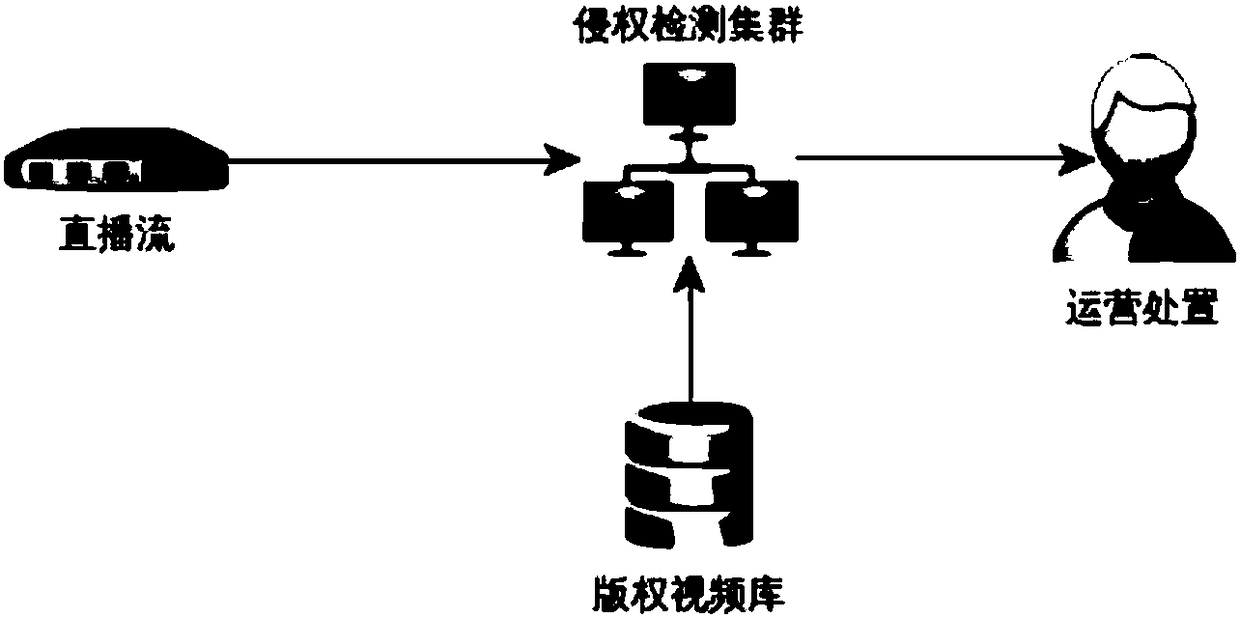
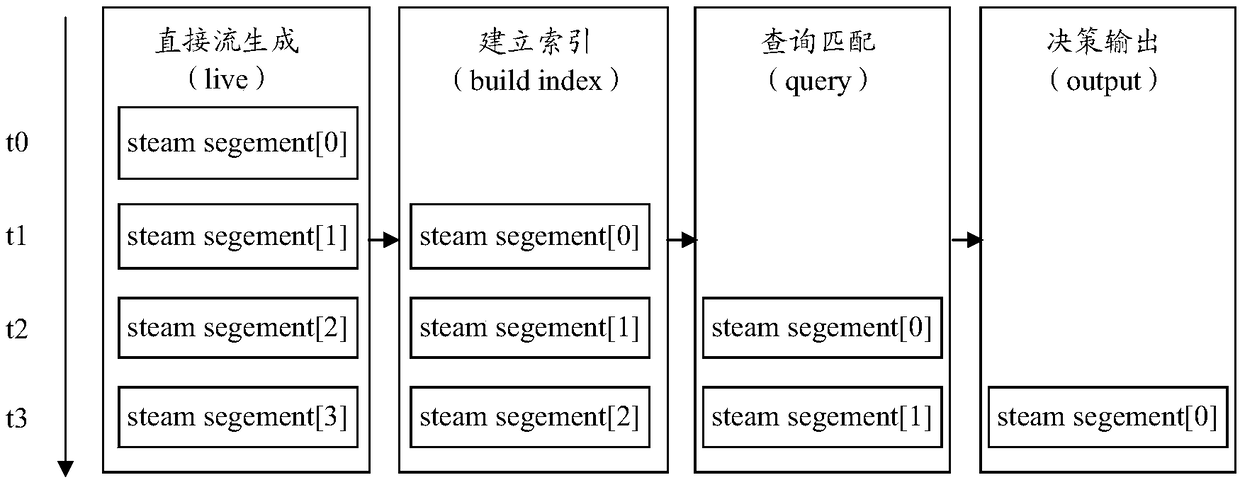
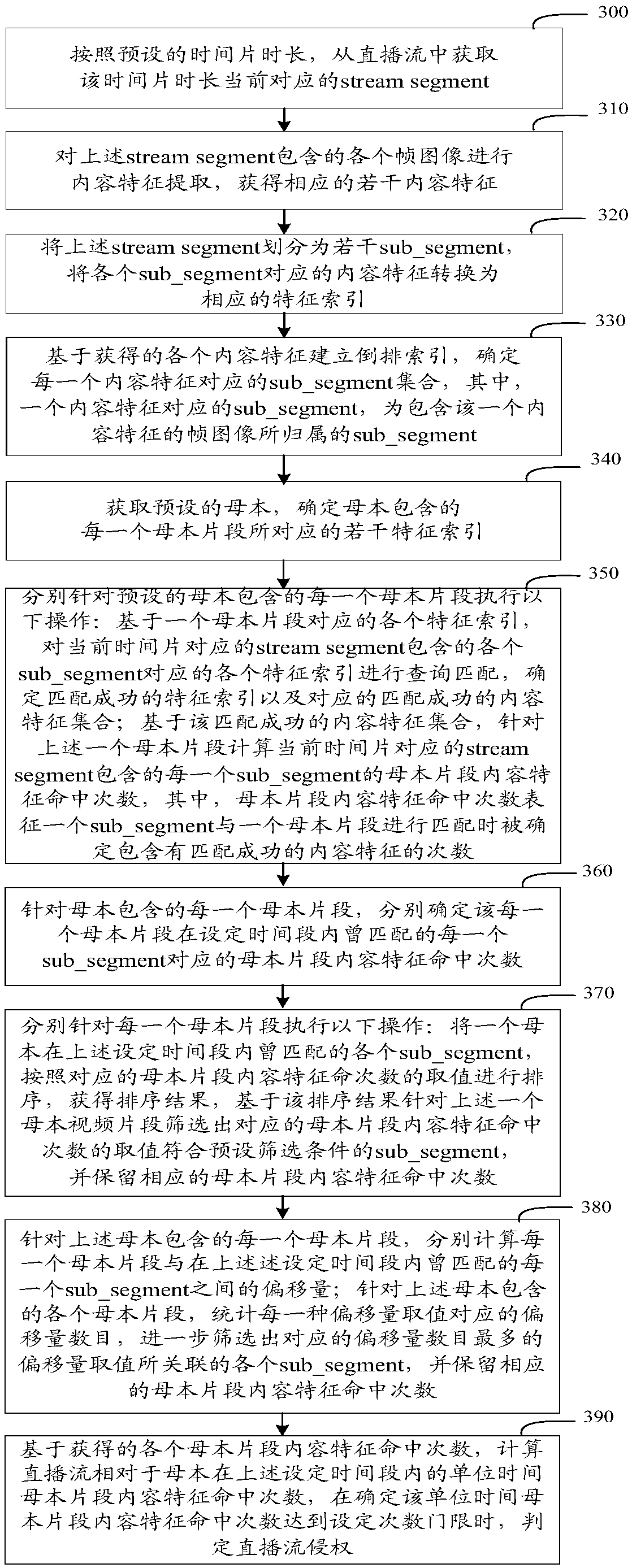
The invention relates to the technology of multimedia processing and particularly relates to an infringement detection method and device for a live broadcast stream. The method and the device are usedfor realizing infringement detection of a live broadcast video. The method comprises the steps of taking a time slice as granularity, extracting live broadcast stream segments from the live broadcaststream, for each live broadcast stream segment, dividing the live broadcast stream segment into a plurality of live broadcast stream sub-segments, extracting content features among the live broadcaststream sub-segments in parallel, and converting the content features into feature indexes; carrying out feature index query matching on the live broadcast stream sub-segments contained in each live broadcast stream segment and each body segment contained in a body, thereby determining unit time body segment content feature hit times of the live broadcast stream relatively to the body within a settime period; and judging that the live broadcast stream infringes copyright when it is determined that the unit time body segment content feature hit times reaches a set times threshold. Infringementcontent of the live broadcast video can be accurately and automatically monitored in real time, and copyright protection in a live broadcast scene is realized.
Owner:ALIBABA GRP HLDG LTD
Compression sensing theory-based interactive supported dual watermark generating and detecting method
InactiveCN102073980AGood encryptionPrevent leakageImage data processing detailsSingular value decompositionTheory based
The invention provides a compression sensing theory-based interactive supported dual watermark generating and detecting method. The method comprises a watermark generation part and a watermark detection part, wherein the method for generating the watermark comprises the following steps of: embedding a robustness watermark in a vector image by adopting a classical singular value decomposition (SVD) algorithm, extracting a semi-fragile watermark from an image Aw with a robust watermark, and saving the semi-fragile watermark as a zero watermark; and the method for detecting the watermark comprises the following steps of: extracting the robust watermark from the image to be detected, extracting a semi-fragile watermark from the image to be detected, and comparing the semi-fragile watermark with the registered zero watermark to determine the authenticity and completeness of the image content and recover the tempered part. Different from the condition that two watermarks in the conventional dual watermark system work independently and even influence each other, the method ensures that the two watermarks cooperate with each other to realize functions to generate a mutually enhancing effect, namely interactive support, which is mainly reflected in the security aspect and the function aspect.
Owner:HARBIN ENG UNIV
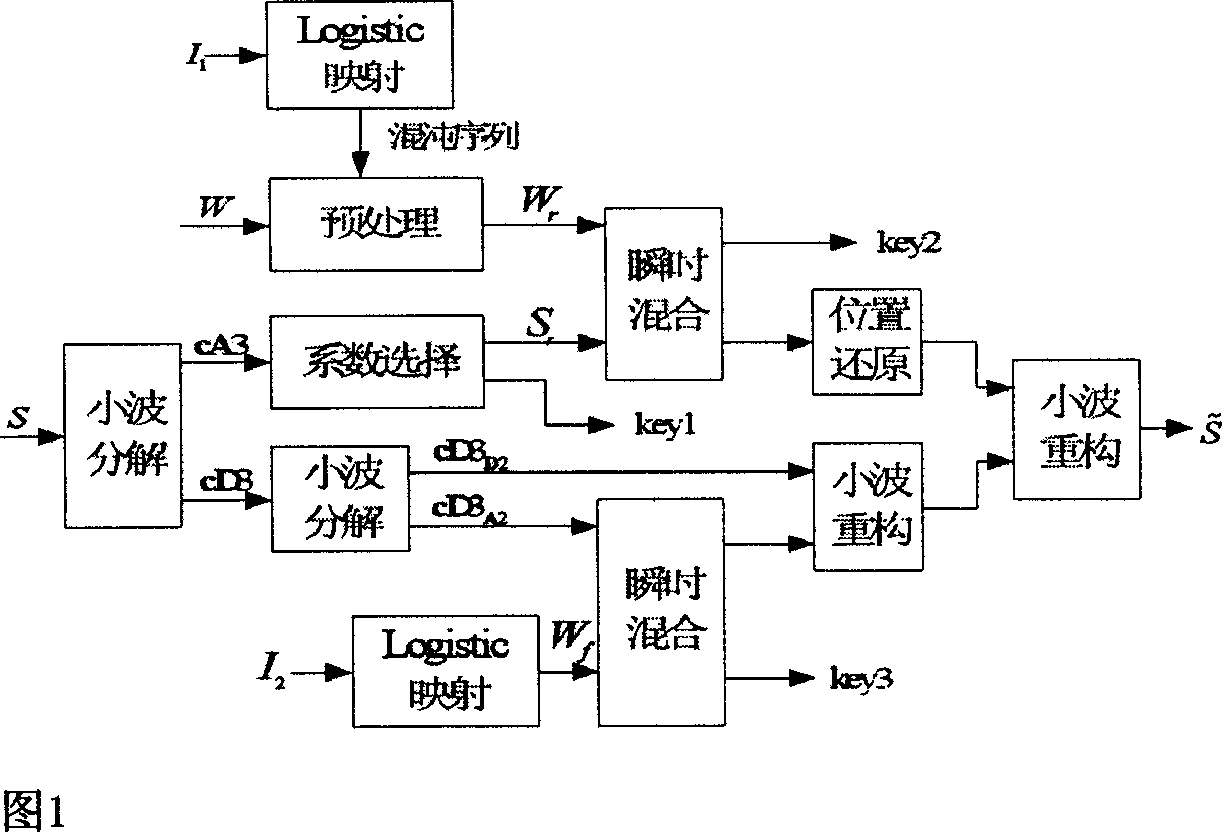
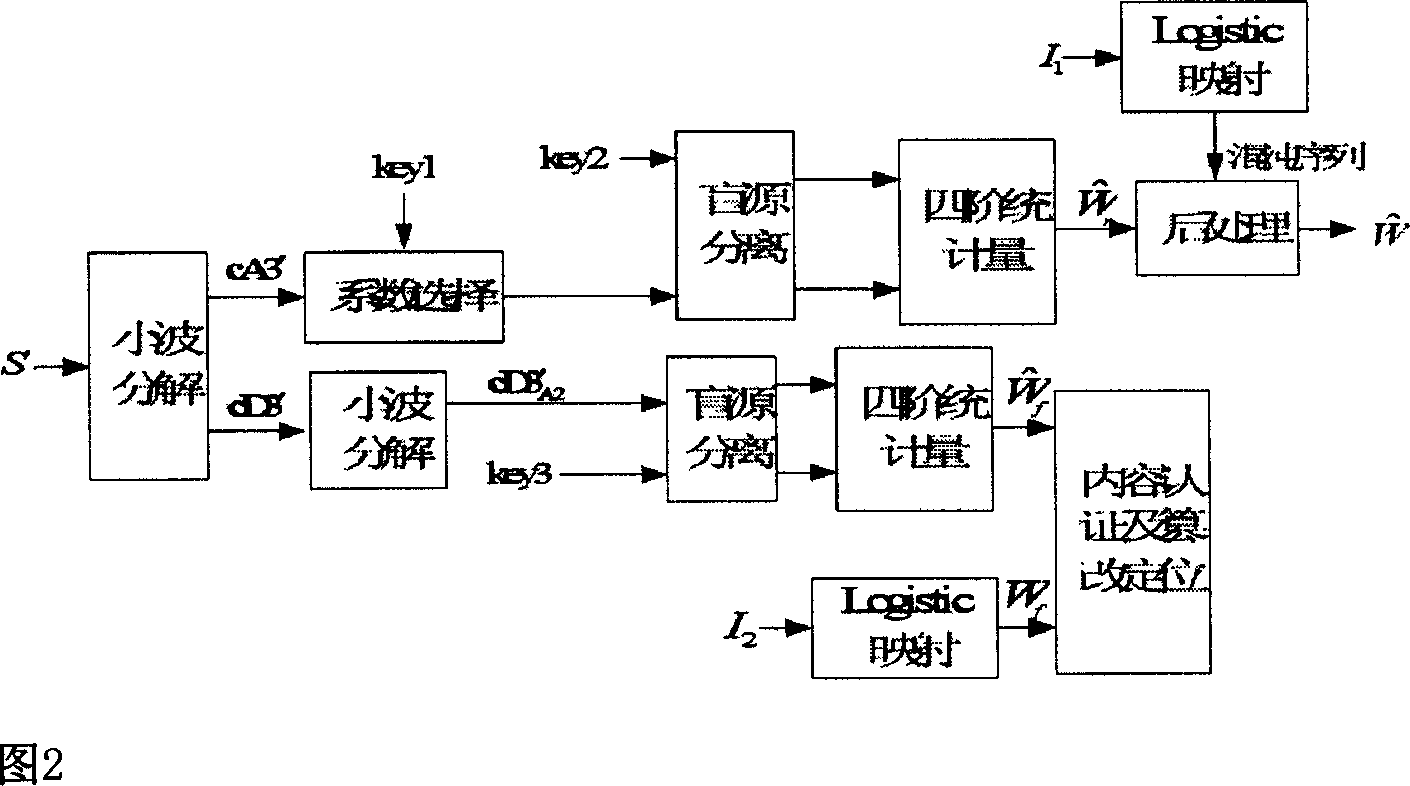
Method for watermarking small wave threshold digital audio multiple mesh based on blind source separation
InactiveCN1941693AReduce difficultyAchieve copyright protectionCharacter and pattern recognitionImage data processing detailsTime domainComputer science
The invention is concerned with compose method of robust watermark and fragile watermark in the multimedia information safety technology field, especially of the production of robust watermark and fragile watermark, inset, pick-up and juggle detecting method of watermark. Using the instantaneous mixing model of blind source separation, the robust watermark and fragile watermark with large mount of information inset into originality audio frequency signal in arbitrary sequence, and the accurate orientation of juggle reflects the wave of signal to originality audio frequency data. It opens multi-objective inset, pick-up and juggle detecting method of watermark, and the safety of watermark depends on the encryption key information. Input the robust watermark and fragile watermark to the audio frequency production at the same time to protect the copyright and local the juggle. Because the inset of robust watermark and fragile watermark is in arbitrary sequence without the restriction of inset order, without keeping secret and pick-up arithmetic, it reduces the difficulty of arithmetic.
Owner:DALIAN UNIV OF TECH
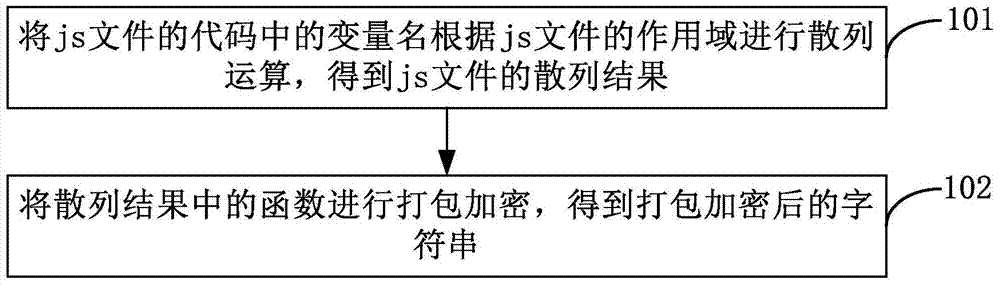
Confidential treatment method and device for code
InactiveCN104504313AIncrease the difficultyAchieve copyright protectionProgram/content distribution protectionEncrypted functionCode readability
Owner:BEIJING AMAZGAME AGE INTERNET TECH CO LTD
Gray image watermark embedding and extracting method based on singular value decomposition
InactiveCN103106636AInformativeIntuitive amount of informationImage data processing detailsSingular value decompositionPersonalization
The invention discloses a gray image watermark embedding and extracting method based on singular value decomposition. The gray image watermark embedding and extracting method based on singular value decomposition comprises the flowing steps: conducting singular value decomposition on an image and obtaining matrix components; conducting encoding and storage on singular values of a diagonal matrix of a singular value matrix and obtaining watermark signals; blocking a hosting image and choosing image blocks high in masking effect; conducting singular value decomposition on the image blocks and embedding the watermark signals into the image blocks; and conducting inverse transformation of the singular value decomposition on the image blocks. The gray image watermark embedding and extracting method based on singular value decomposition has the advantages that the embedding of the gray image watermark image is achieved, the watermark comprises a plurality of straight information, no using limiting exists on the size of the watermark image, and requirements of enterprises concealing personalized enterprise logos as watermarks can be met; the watermark embedding and extracting method can resist a plurality of image aggressive behaviors, and algorithm robustness is high; gray image watermark embedding and extracting method based on singular value decomposition can effectively detect watermark information content, solves the problem of image being illegally issued and the like, and is of great value for healthy and fast development of internet industries.
Owner:DALIAN NATIONALITIES UNIVERSITY
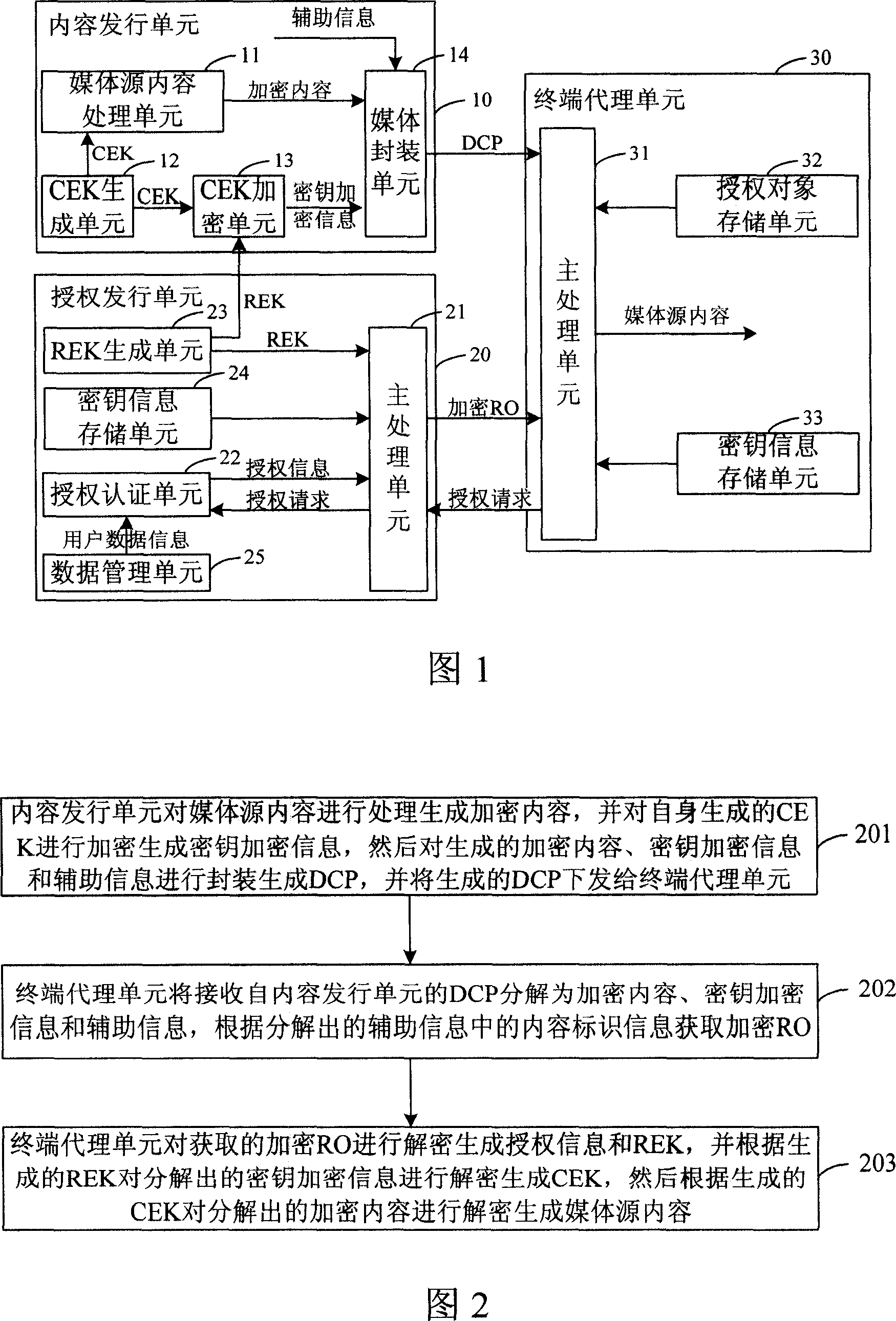
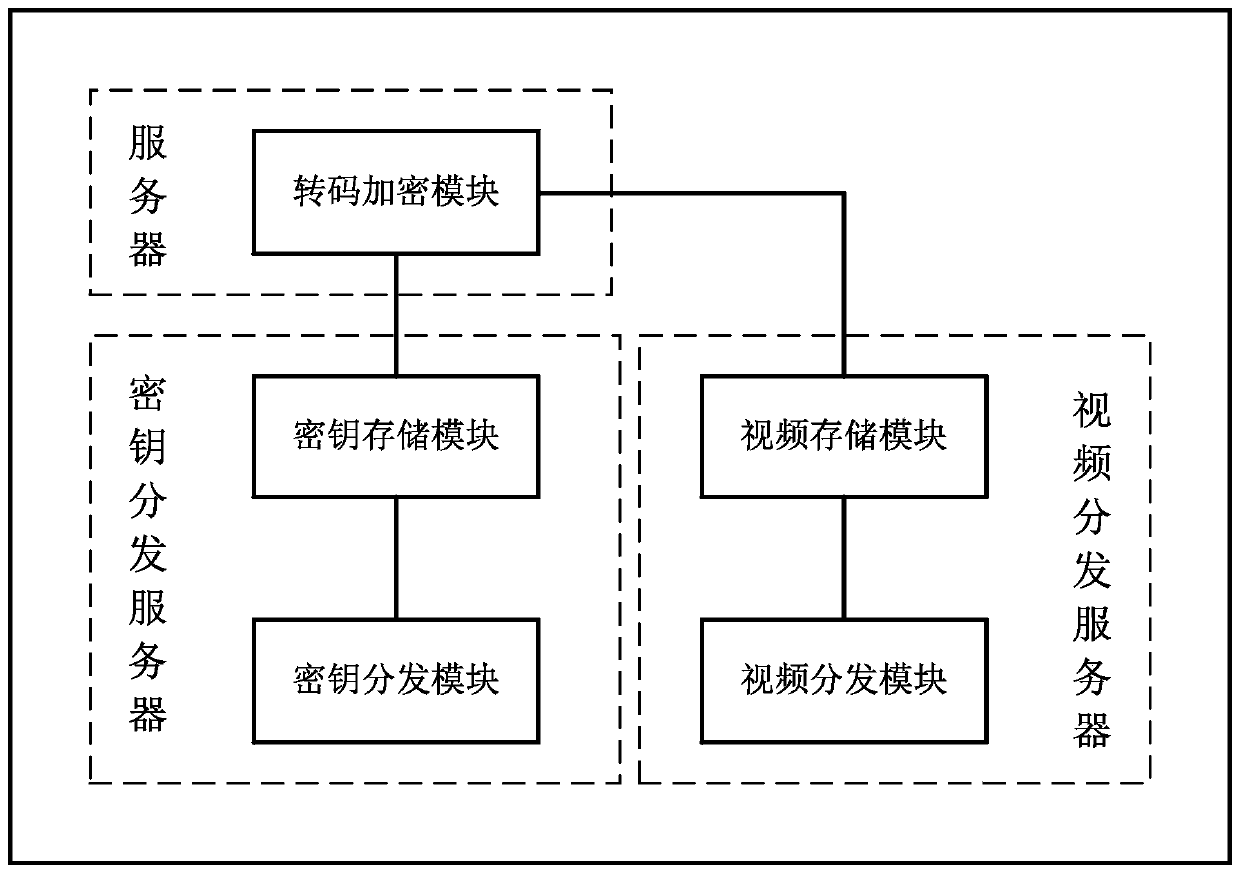
System and method for realizing real time medium copyright protection
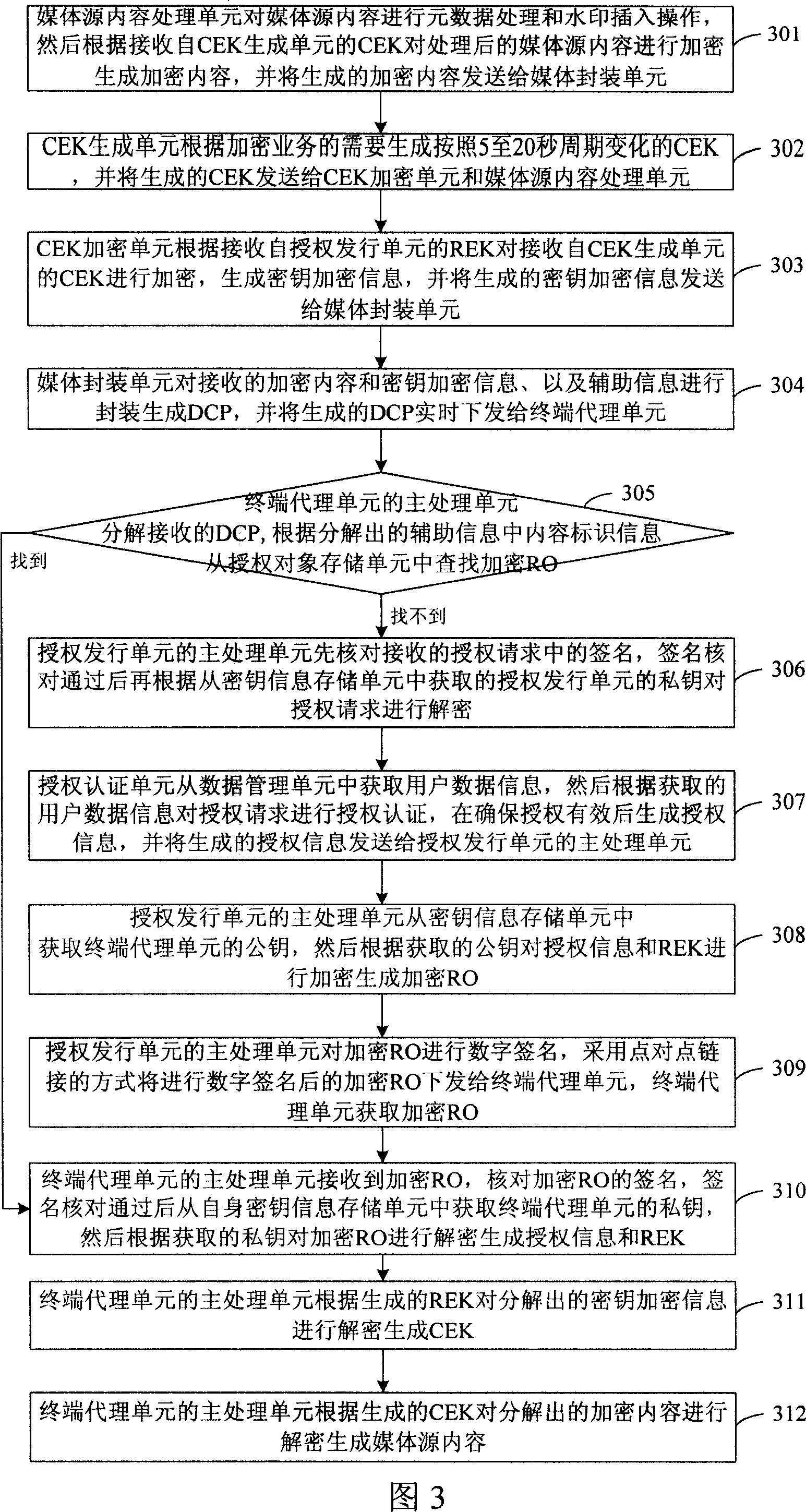
InactiveCN101118576ASolving Copyright Protection IssuesRealize copyrightProgram/content distribution protectionAuthorizationEncryption
The present invention discloses a system which can realize the copyright protection of the media in real time, and includes a content issuance unit used to process the media source content to generate encryption content, CEK is encrypted to generate key encryption information, the encryption content, the key encryption information and the auxiliary information that are generated are sealed to product DCP, the DCP produced is issued to a terminal substitutive unit; an authorized issuance unit used to decrypt the authorized requirement and authorize the certificate, after ensuring the availability of authorization, the authorization information is generated, the authorized information and REK are encrypted to generate encrypted RO, and the encrypted RO is sent to the terminal substitutive unit; and the terminal substitutive unit used to decompose the received the DCP, the encrypted RO is obtained according to discomposed content logo information, the obtained encrypted RO is decrypted to generate the authorized information and the REK, according to the REK, the decomposed key encryption information is decrypted to generate the CEK, according to the CEK, the encrypted content is decrypted to generate the media source content. The present invention discloses a method to realize real time media copyright protection.
Owner:北京数码视讯软件技术发展有限公司
Method, device and system for installing software
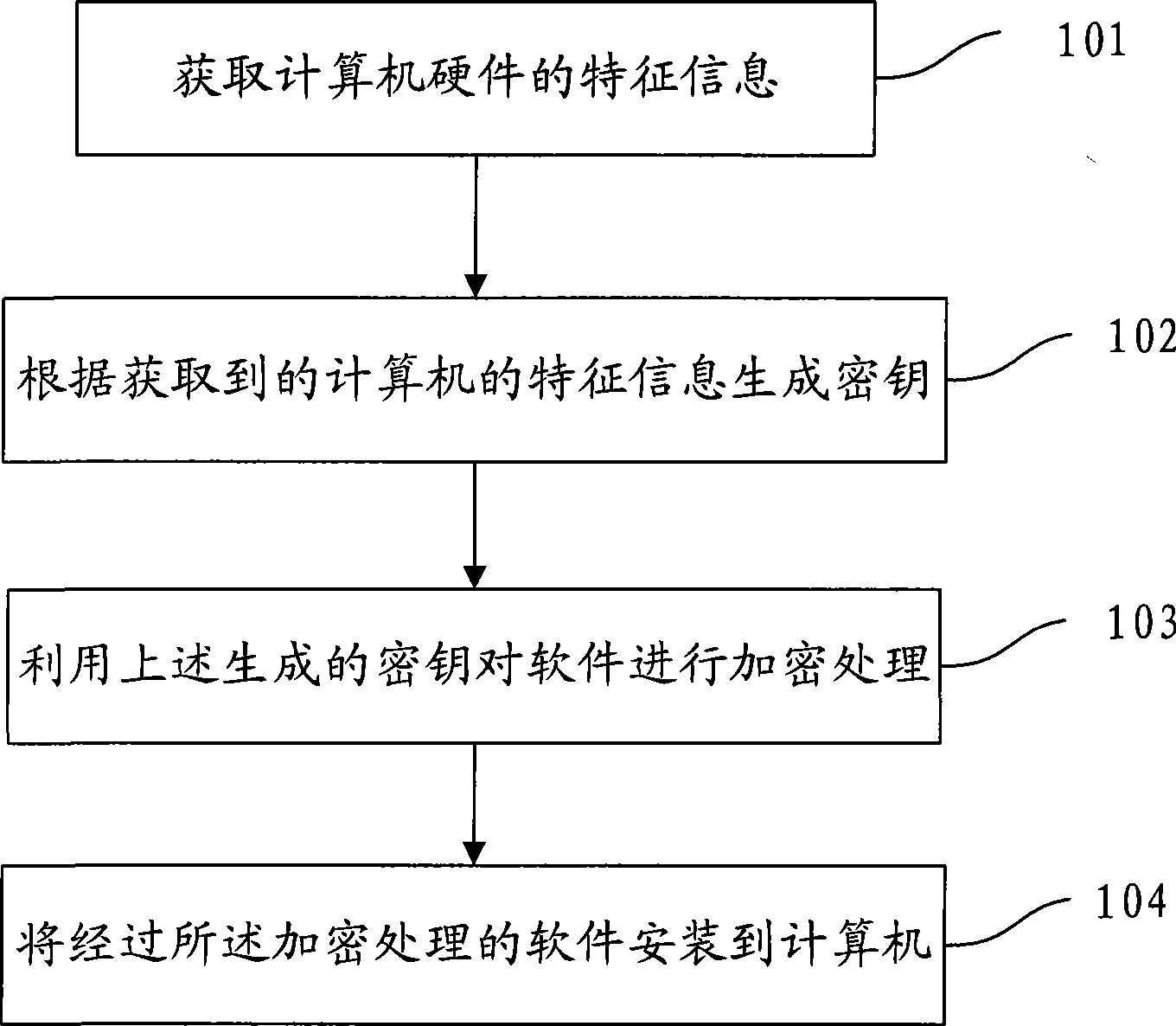
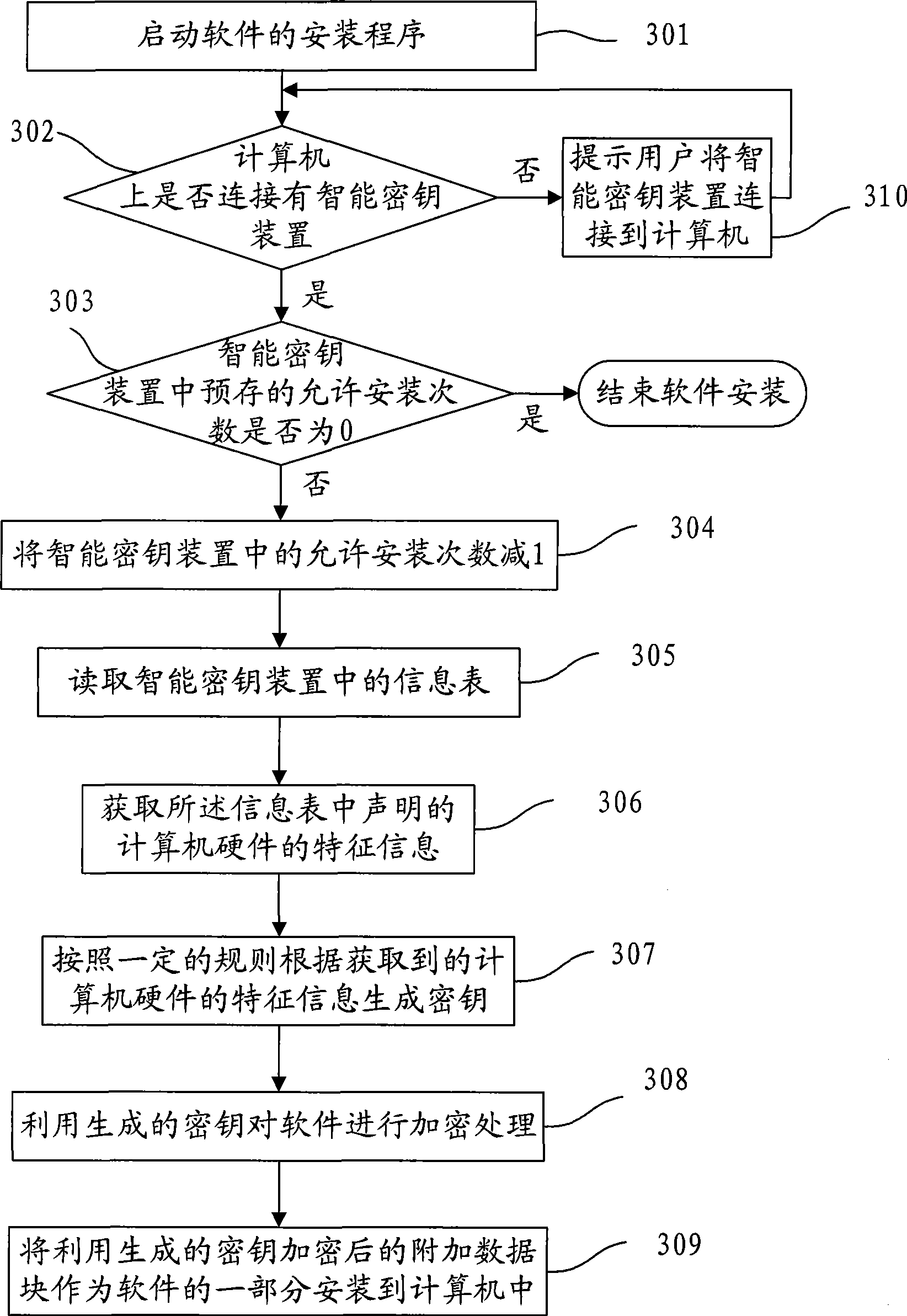
InactiveCN101447009AReduce usageAchieve copyright protectionComputer security arrangementsProgram loading/initiatingClassified informationAcquired characteristic
The invention discloses a method, a device and a system for installing software, relates to the technical field of computers, and solves the problem that after being installed on one computer, the software can be easily copied to another computer for use in the prior art. The embodiment of the invention comprises the following steps: acquiring the characteristic information of computer hardware when the software is run; generating keys based on the acquired characteristic information; then, encrypting the software by the generated keys; and finally, installing the encrypted software on the computer. The embodiment of the invention is suitable for running various software, particularly the software requiring copyright protection and classified information protection.
Owner:FEITIAN TECHNOLOGIES
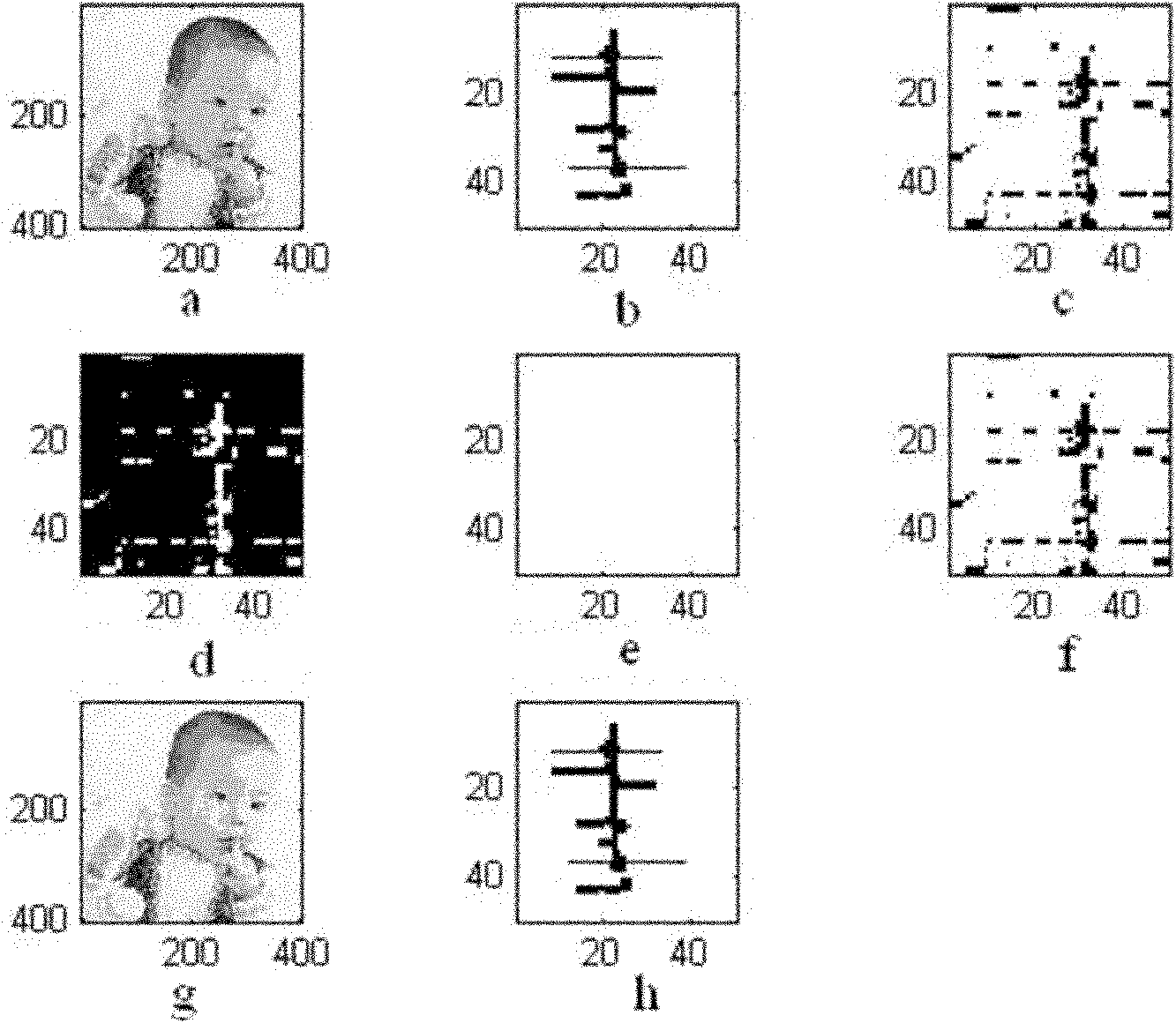
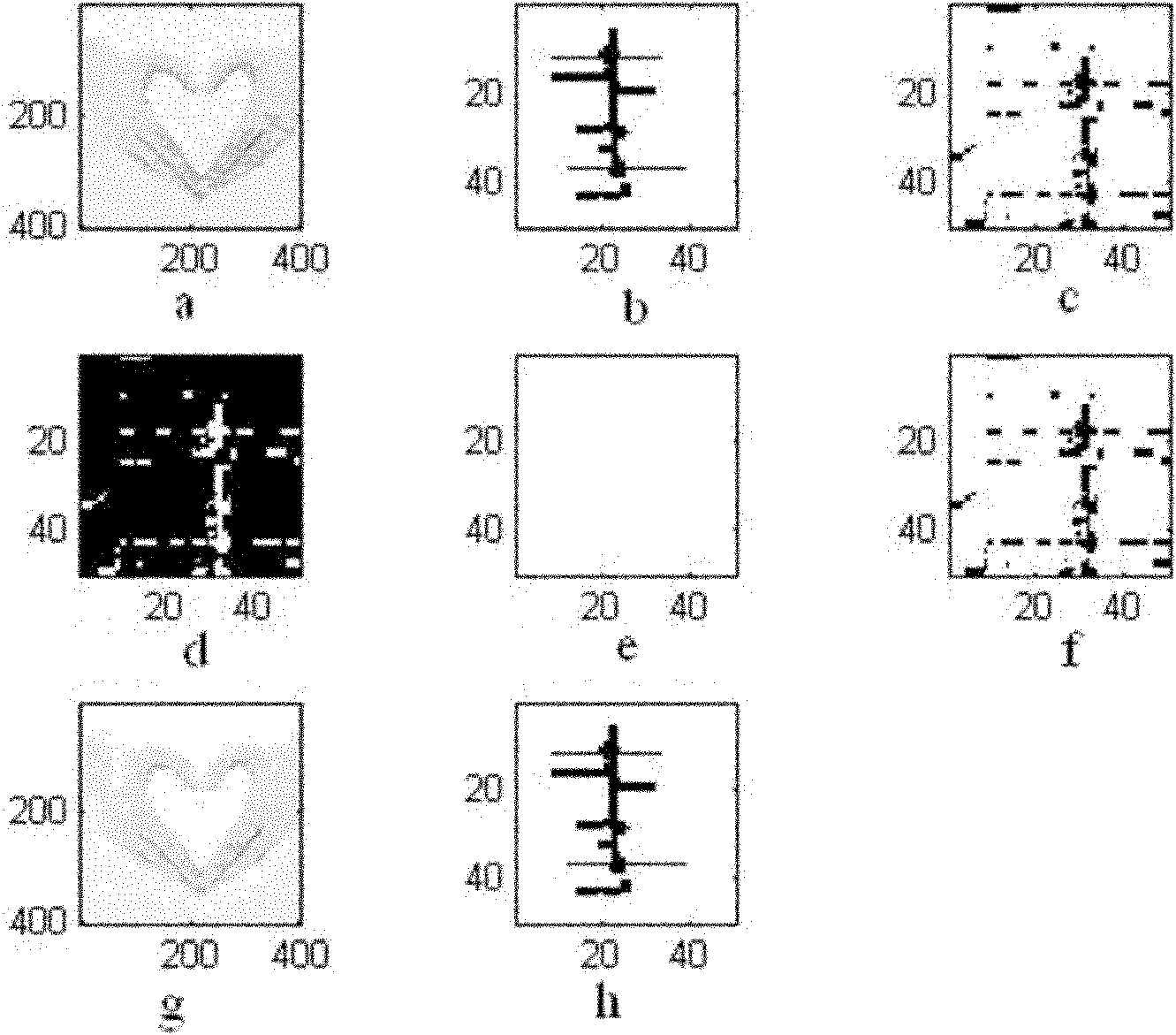
Visual secret sharing-based image content tampering detection method
InactiveCN102142129AReduce computational complexityImprove efficiencyImage data processing detailsPattern recognitionVision based
The invention discloses a visual secret sharing-based image content tampering detection method. The method comprises the following steps of: generating a watermarking image by using copyright information of the image; generating a verification shadow and a detection shadow by combining the content characteristic of the image; recovering a water mark from the verification shadow and the detection shadow by using a visual secret sharing technology; and comparing the recovered water mark with the original watermarking to determine whether the image is tampered so as to realize tampering detection and determine the position of a tampered region. In the method, the watermarking image is generated by using the copyright information of the image without embedding and extracting the watermarking, but the tampering detection of image content is realized by using the visual secret sharing technology on the premise of not damaging the original image data.
Owner:XIAN UNIV OF TECH
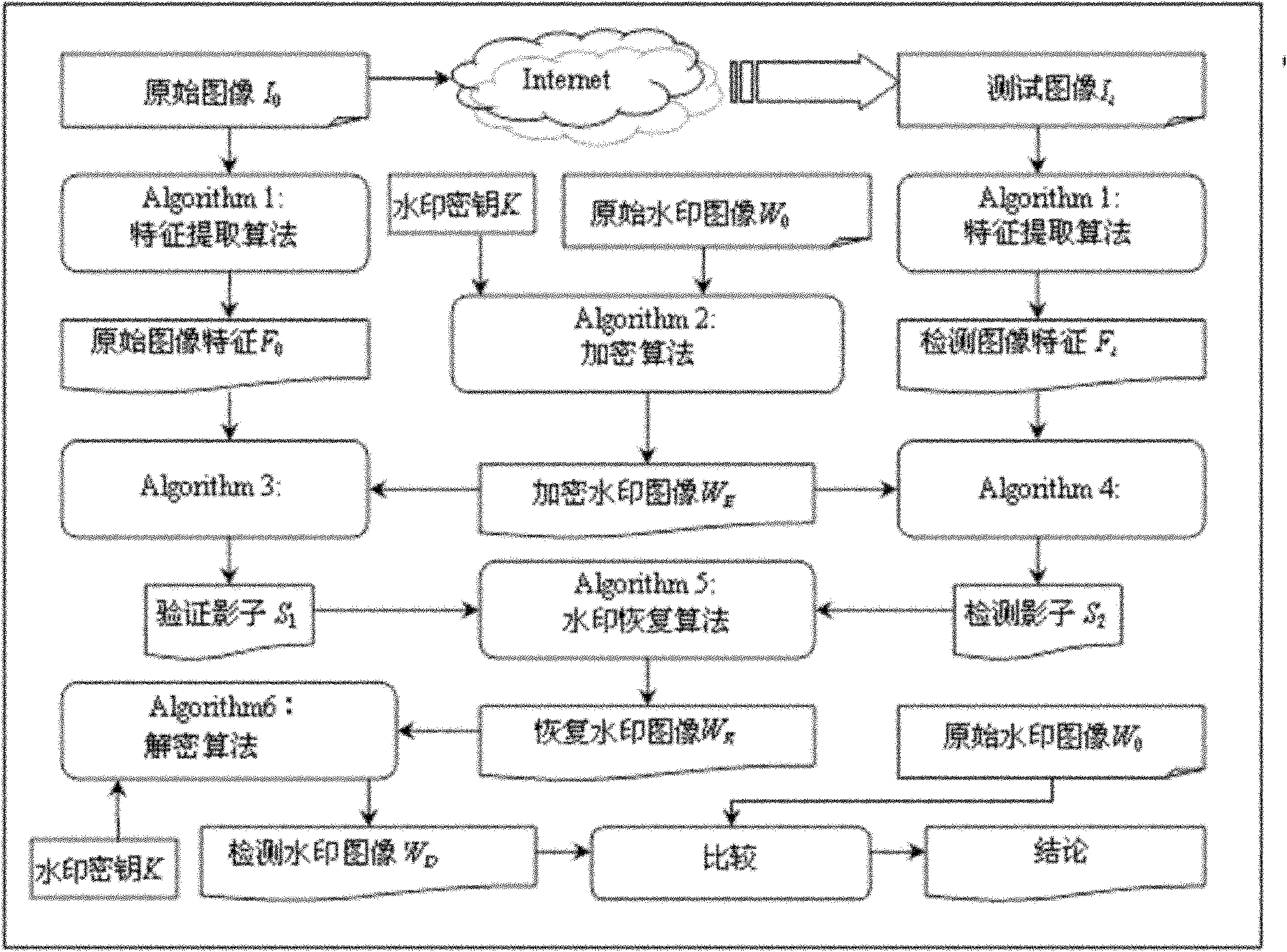
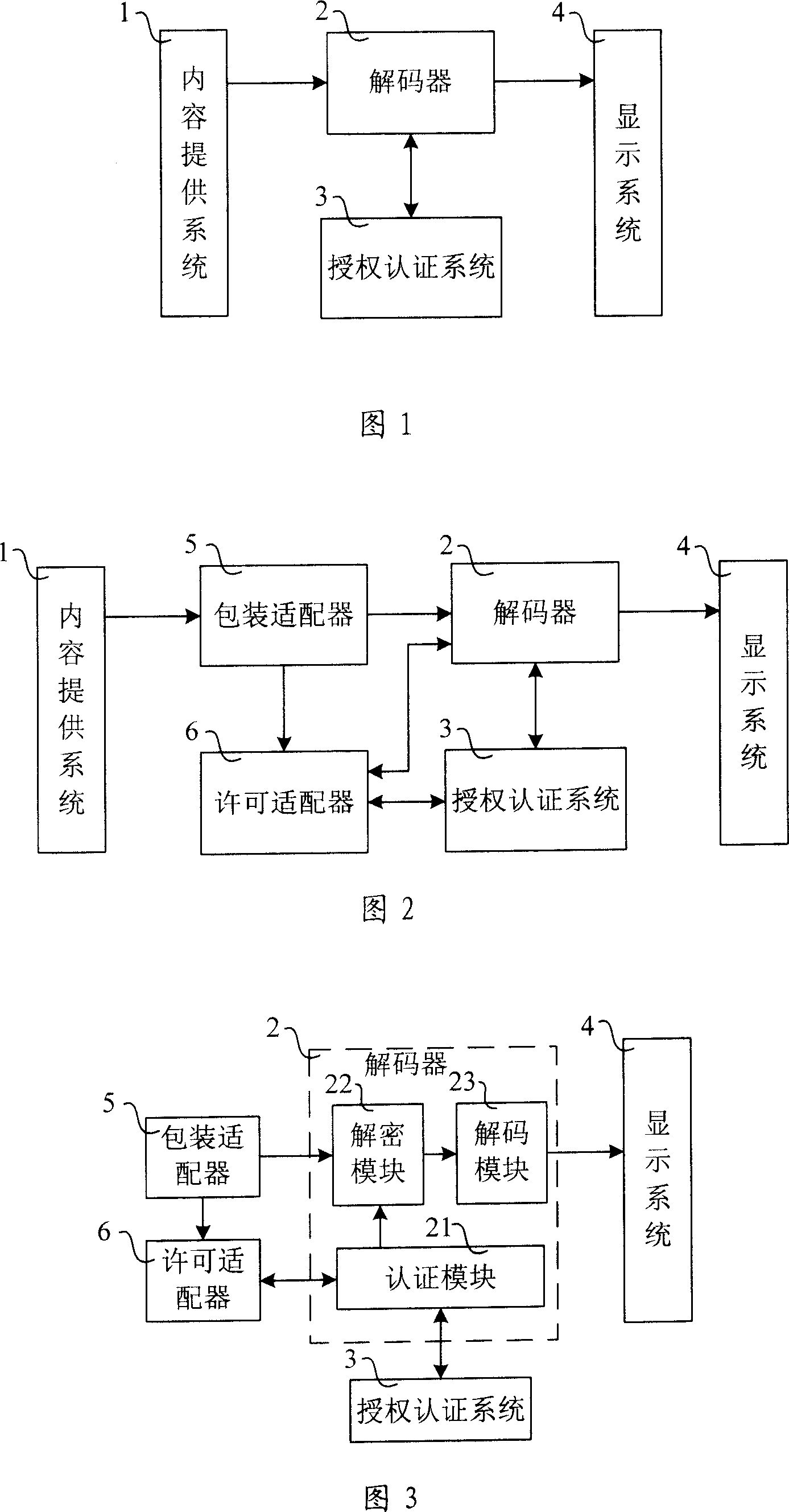
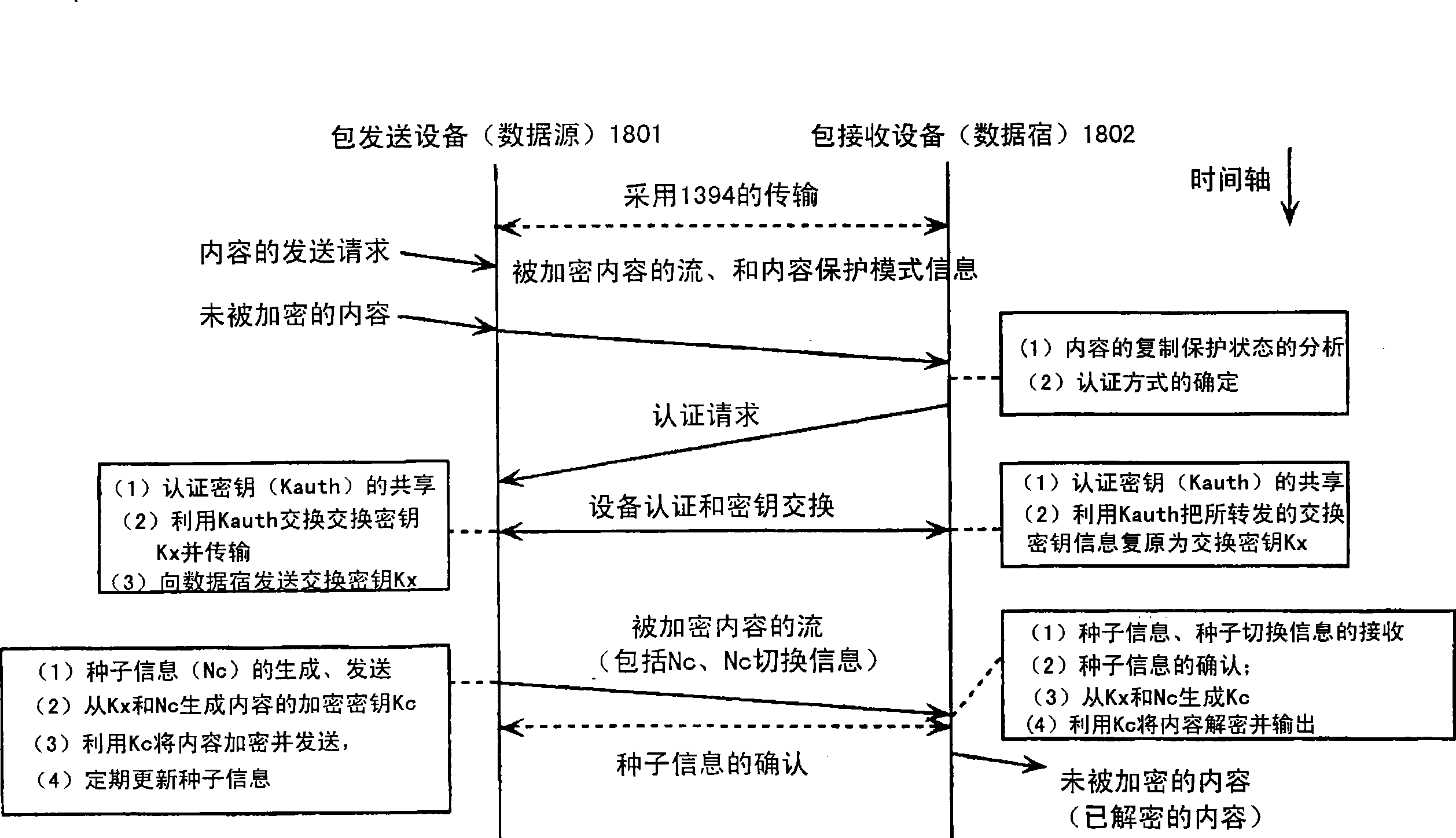
Data transfer system for digital copyright management
InactiveCN101009550AAchieve copyright protectionEffective protectionProgram/content distribution protectionSecuring communicationData informationSecure transmission
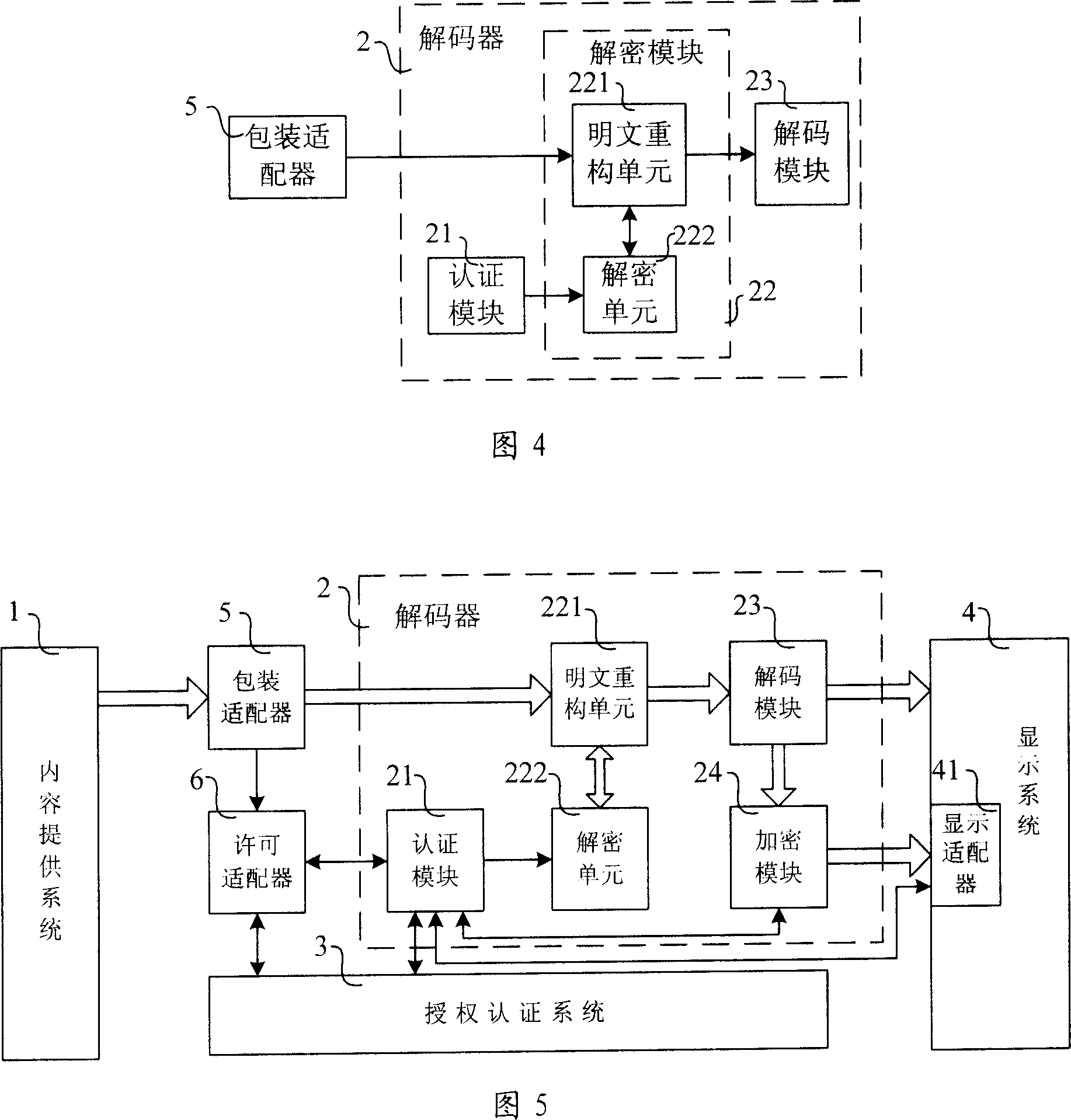
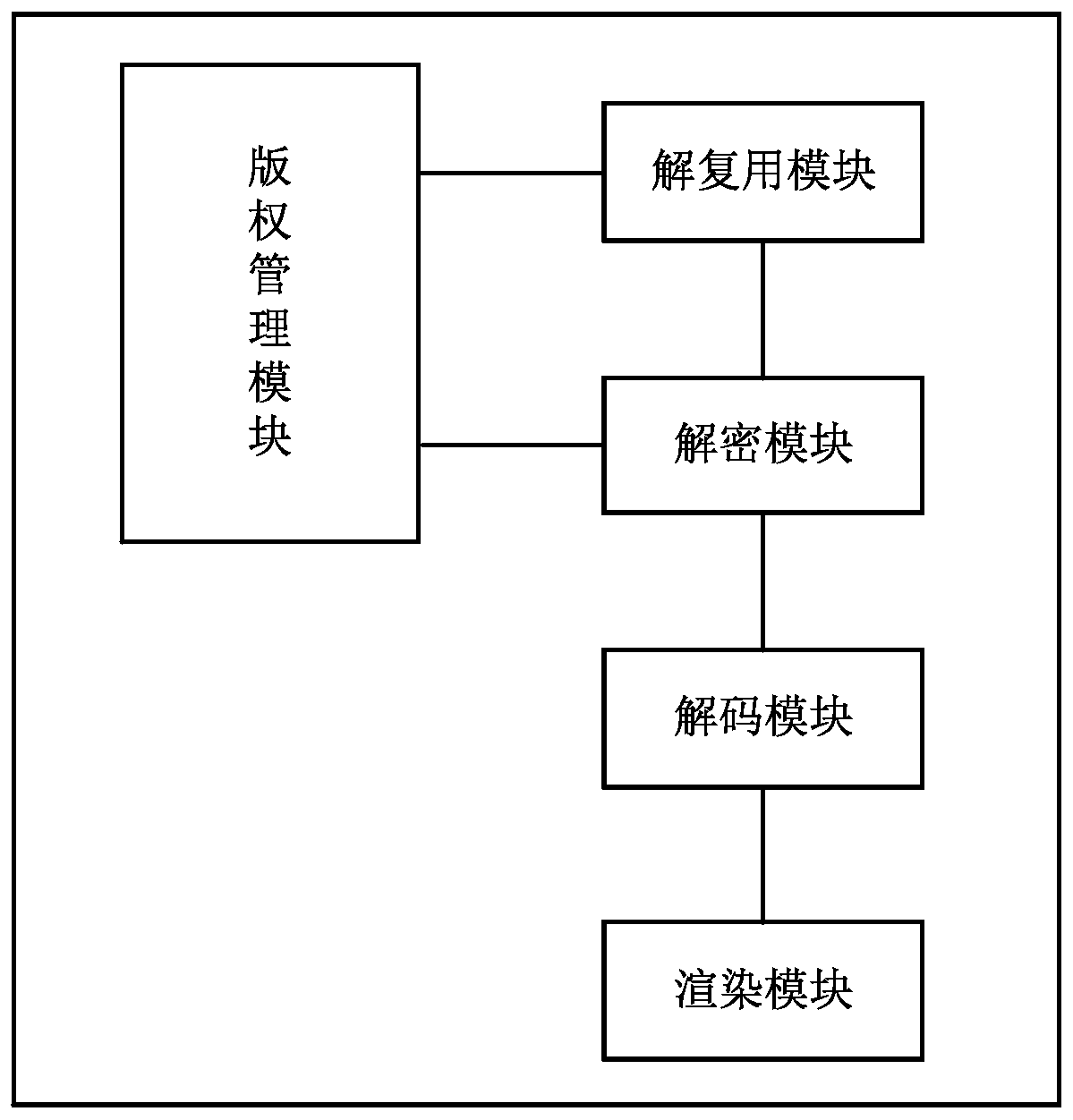
The invention relates to data transmission system for the management of digital copyright, the system includes: content providing system which is used to provide the media data; decoder which is used to connect with the content providing system to obtain the key and decipher and decode the media data; authorization certification system which is connected with the decoder and certify the decoder and provide key for the decoder; display system which is connected with the decoder and display the data information input by the decoder. The decoder includes: authentication module which is connected with the authentication system and permission adapter, deciphering module which is connected with the authentication module and the package adapter, and the decoding module which is connected with the deciphering module and the display system. The technical project of invention can realize the data transmission between the content providing system, decoder and display system, and it can protect the key and the media data effectively, and realize the media copyright protection for the system level.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Digital television timing charging and copyright protecting method based on watermarks
InactiveCN102740137AEasy extractionSpeed up the extraction processSelective content distributionStart timeDct coefficient
The invention discloses a digital television timing charging and copyright protecting method based on watermarks. The digital television timing charging and copyright protecting method comprises the following steps: 1) recording the starting time that a user watches a digital television and the program information; 2) reading a PDK (PERL Development Kit) in a smart card by virtue of a bidirectional set top box, enabling the PDK to generate watermark signals, and carrying out the error correction of coding on the watermark signals; 3) enabling the watermark signals processed by the error correction of coding through a decoder at the time of decoding into the middle-low frequency DCT coefficients of an I frame luminance component after the I frame is researched, and then outputting and playing the middle-low frequency DCT coefficients; 4) billing the digital television by hours through a user management system; 5) extracting watermarks of suspended illegal videos when the suspended illegal videos are played in the program of the digital television, and determining the copyright by utilizing the extracted watermark signals, and further judging the user illegally spreading programs of the digital television. The digital television timing charging and copyright protecting method disclosed by the invention has the advantages of novel and reasonable design, simplicity in operation, low cost, high accuracy in timing charging, and high popularization and application value, and also has the advantage that the source of the copyright infringement can be tracked. The digital television timing charging and copyright protecting method is suitable for the popularization and development of the digital television.
Owner:XIAN UNIV OF SCI & TECH
Protection method of IP (internet protocol) core with determined validity
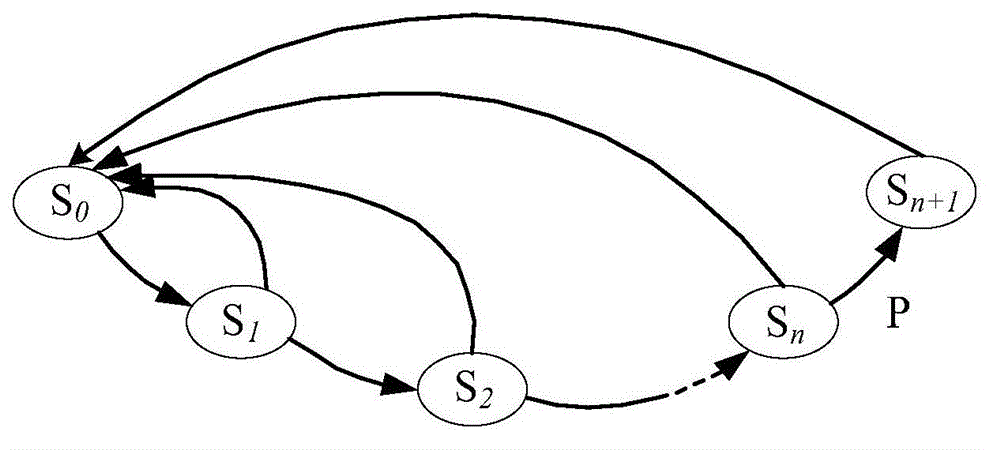
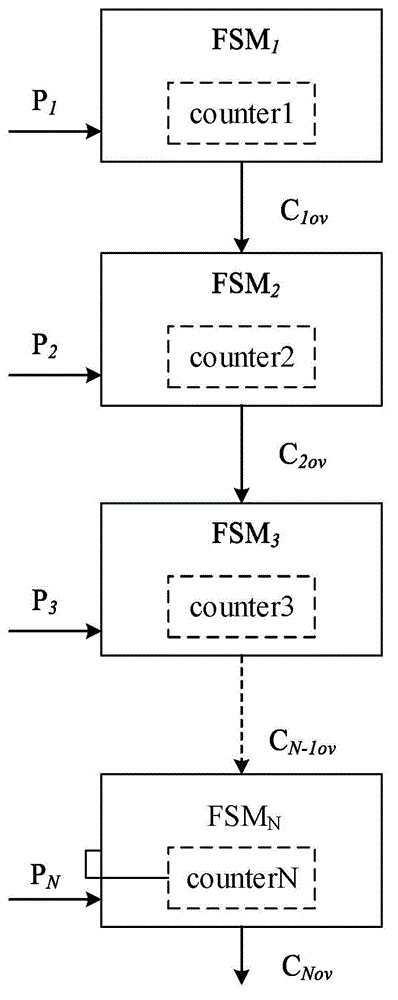
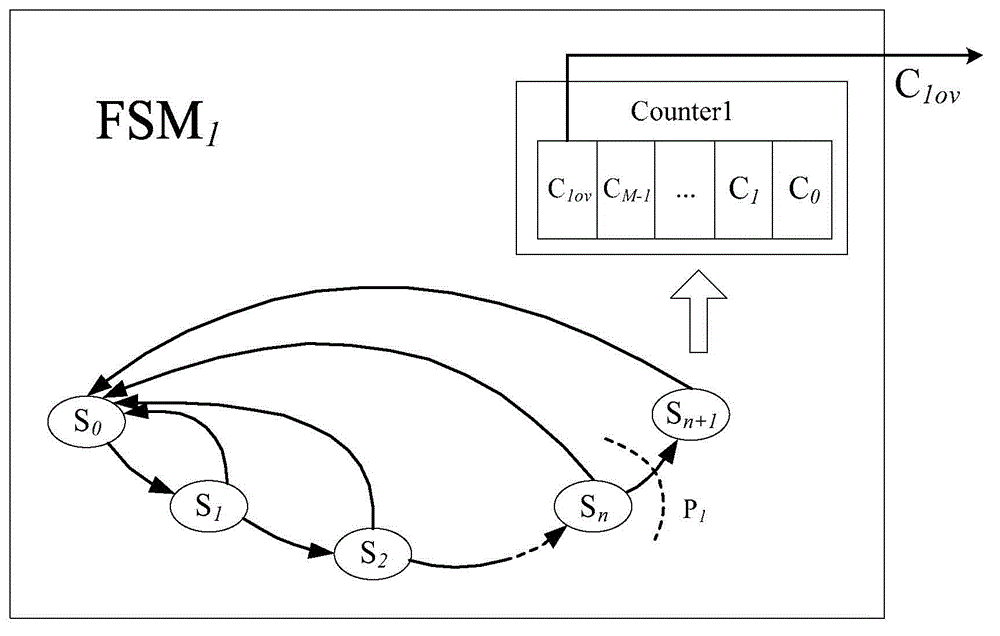
ActiveCN104484583AAchieve copyright protectionIntegrity guaranteedProgram/content distribution protectionTime rangeControl signal
The invention discloses a protection method of an IP (internet protocol) core with determined validity. The method is realized through implanting counters into redundant state of a plurality of state machines of the IP core, and using low-overturn probability node in the IP core circuit as trigger condition of the redundant state. A plurality of counters are arranged in a classification manner, the next class of counter is subjected to carrying when the front class of counter is full, and a control signal is transmitted to the IP core circuit when the last class of counter is full to make the IP core become unusable. In an actual use process, through changing the bits of the counters in the implanted state machines and reasonably selecting the number of the state machines, the IP core circuit is enabled to fail in a predetermined time range to limit the user of the IP core, so as to protect the IP core effectively. The service life of the IP core circuit is prolonged effectively by the structure in the primary IP core circuit on the basis of saving the IP core circuit area, so good elusive performance and high flexibility are realized.
Owner:TIANJIN UNIV
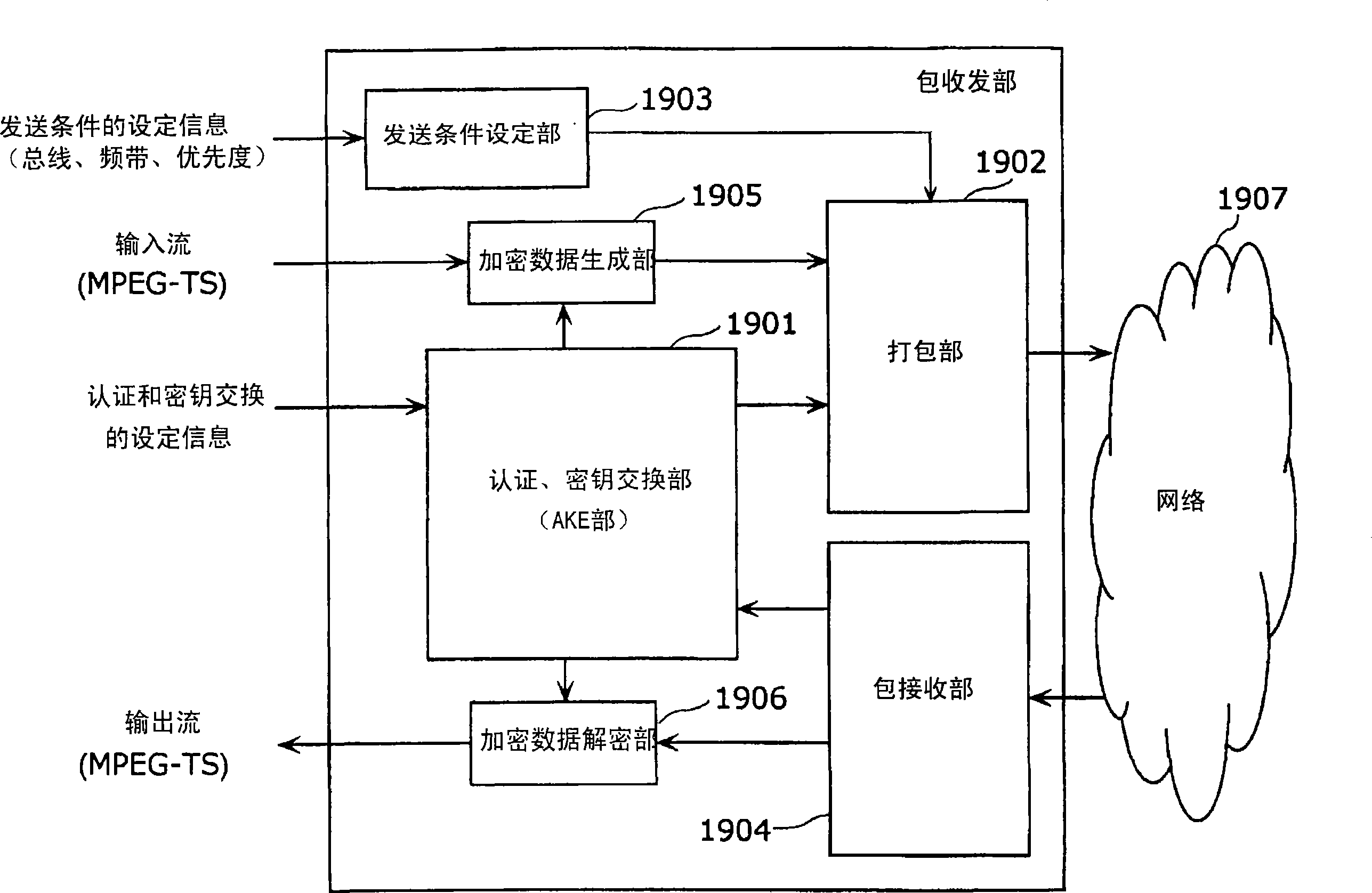
Packet transmitter apparatus
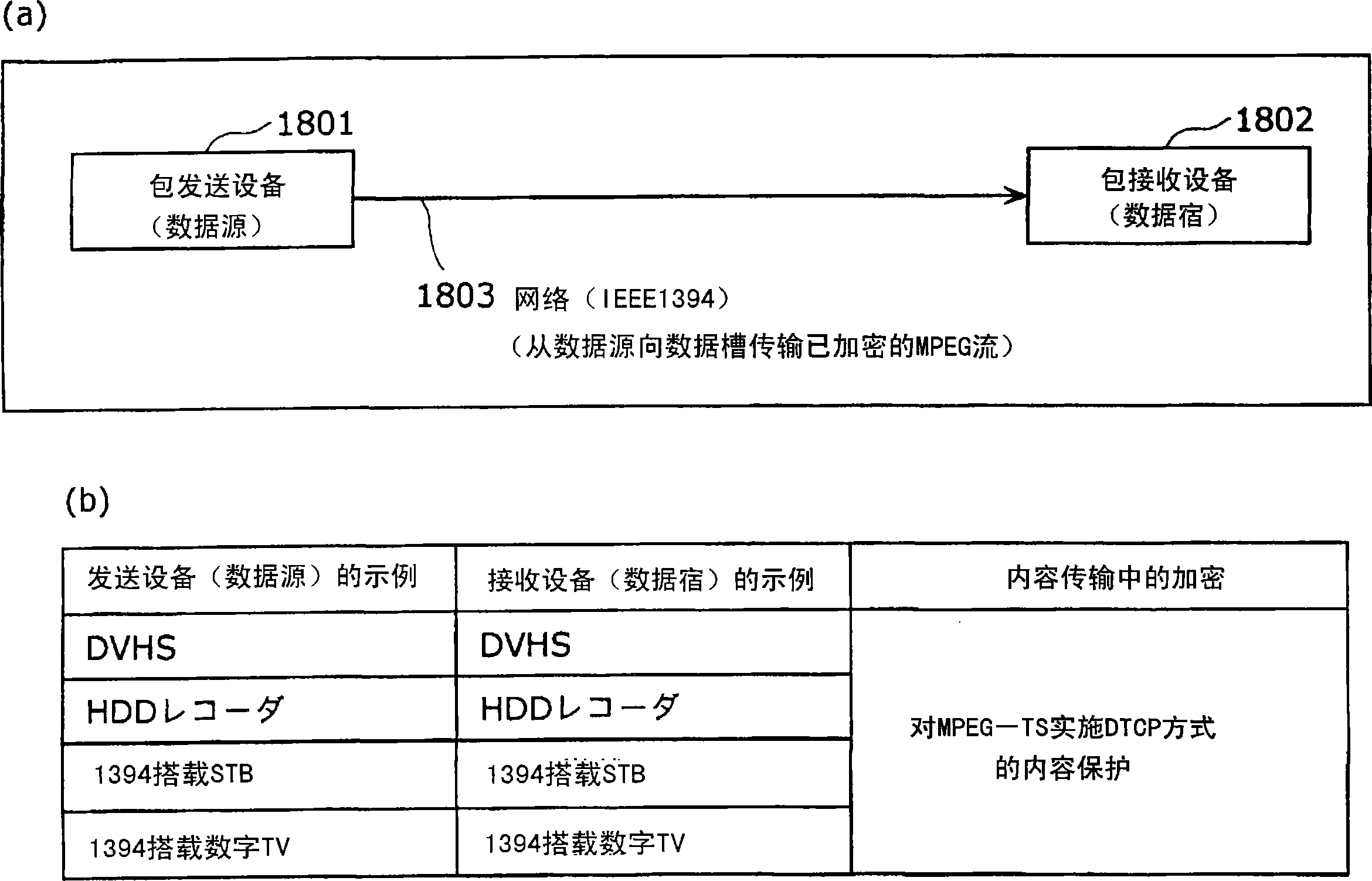
ActiveCN1894908AGuaranteed privacyEnsuring Signal InterchangeabilityData switching networksData formatCopy control
A packet transmitter apparatus capable of transmitting, by use of widely utilized packets such as IP packets and the like, contents protected by content protection technologies such as DTCP and the like. There are included a transmission condition setting / managing part(404) for extracting, from received non-A / V data or A / V data, at least one of A / V data billing information, reproduction control information and copy control information and for producing, from the extracted information, encryption mode information indicative of an encryption mode that is a condition when A / V data are transmitted; an encrypted data producing part(406) for producing encrypted data by encrypting, based on a transmission condition as decided by a combination of input terminal information, data format information and attribute information, the received A / V data and further by adding, to the encrypted A / V data, an encryption information header based on the encryption mode information; and a packetizing part(403) for producing a packet by adding a packet header to the produced encrypted data.
Owner:PANASONIC CORP
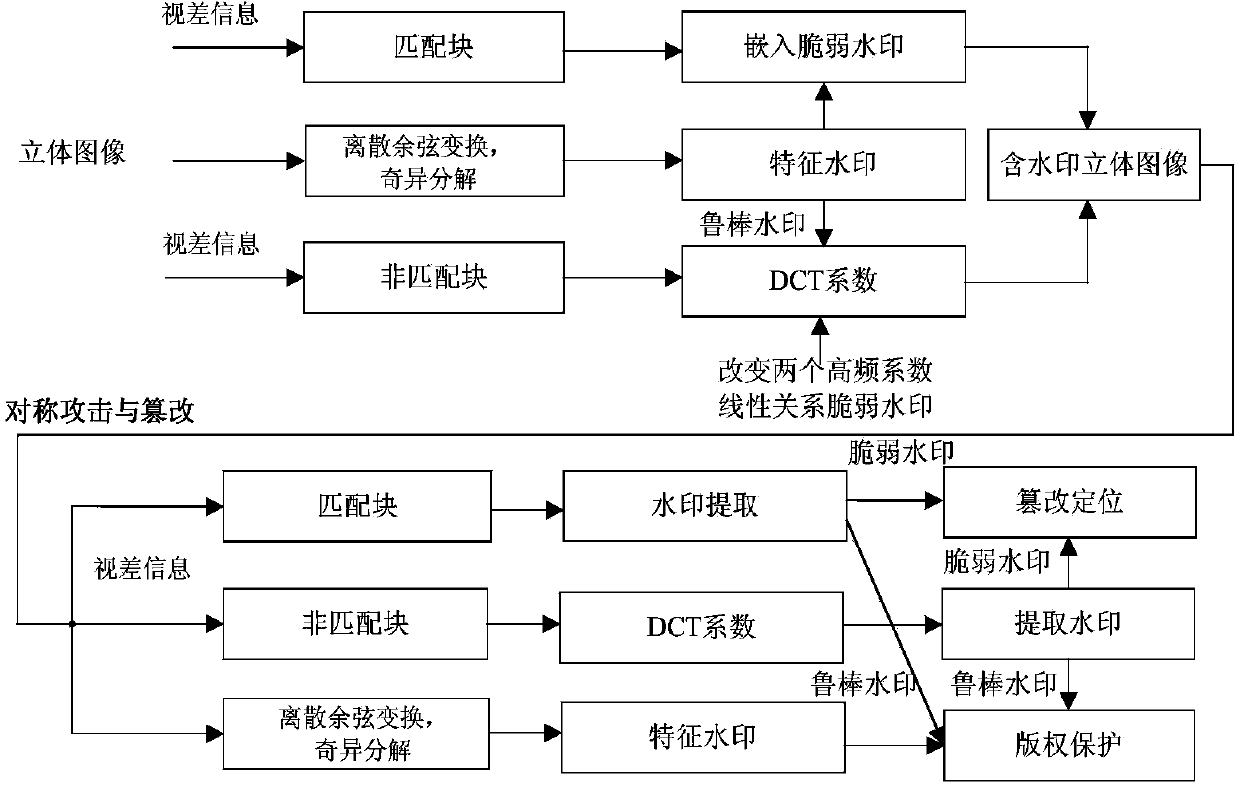
Multi-functional digital watermarking method for three-dimensional picture
ActiveCN104123693AImprove stabilityAchieve copyright protectionImage data processing detailsViewpointsLinear relationship
The invention discloses a multi-functional digital watermarking method for a three-dimensional picture. The multi-functional digital watermarking method for the three-dimensional picture includes watermark embedding, watermark extraction and temper localization, to be specific, using the similarity between the characteristic watermark extracted from the left viewpoint picture of an attacked three-dimensional watermark picture and a robust watermark and the similarity between the characteristic watermark extracted from the left viewpoint picture of the attacked three-dimensional watermark picture and a robust watermark as evaluation bases to realize the copyright protection for the three-dimensional picture; locating tempering blocks in the left viewpoint picture and the right viewpoint picture of the attacked three-dimensional watermark image in two steps, for non-matched blocks, realizing the temper detection through judging whether there is a set numerical linear relationship between two corresponding high-frequency DCT coefficients in a DCT coefficient matrix of each non-matched block, and for matched blocks, using characteristic watermarks and embedded fragile watermarks extracted from the matched blocks to realize the temper detection so as to realize the temper localization function of the three-dimensional image.
Owner:深圳荞漾人工智能集团有限公司
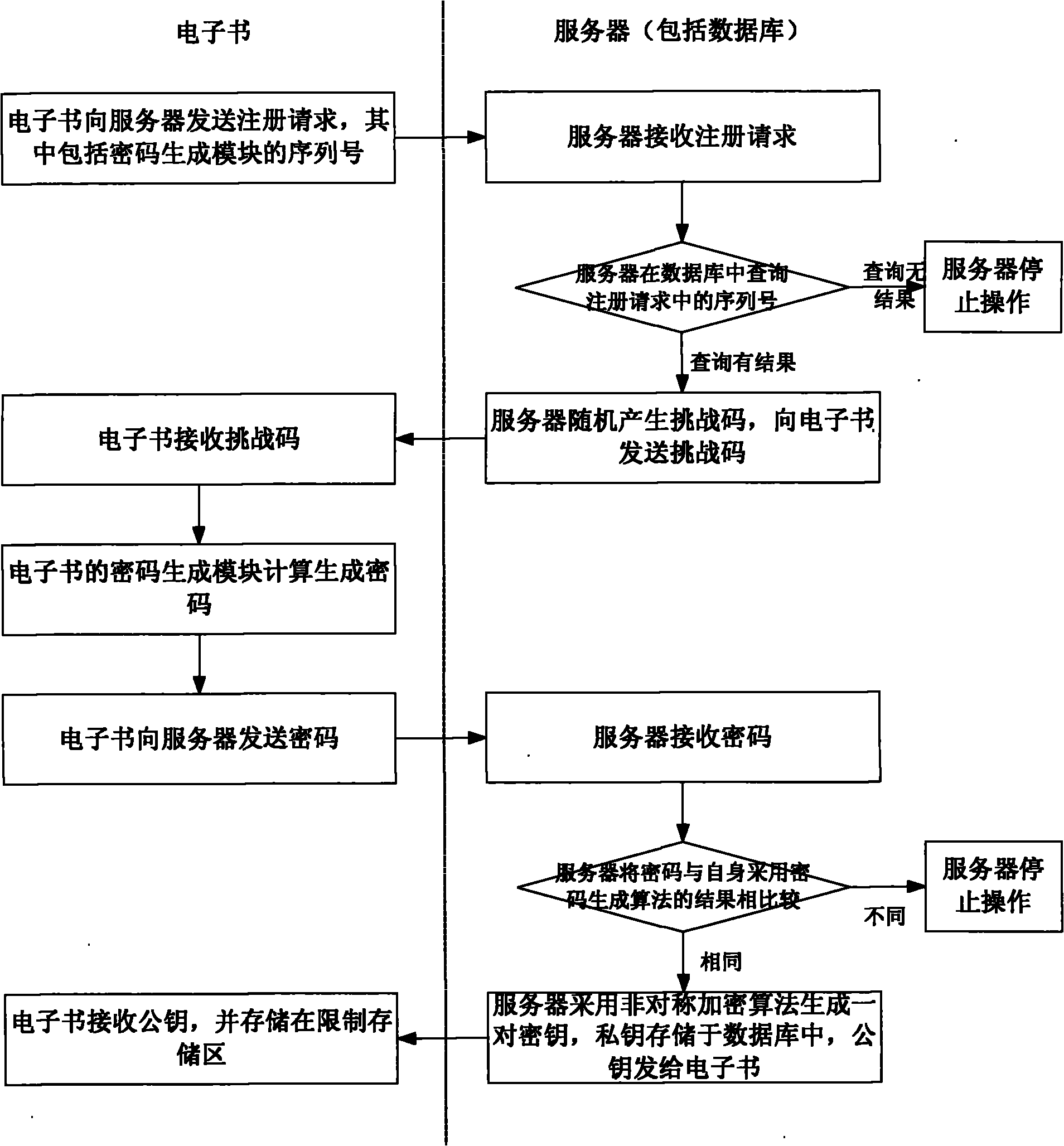
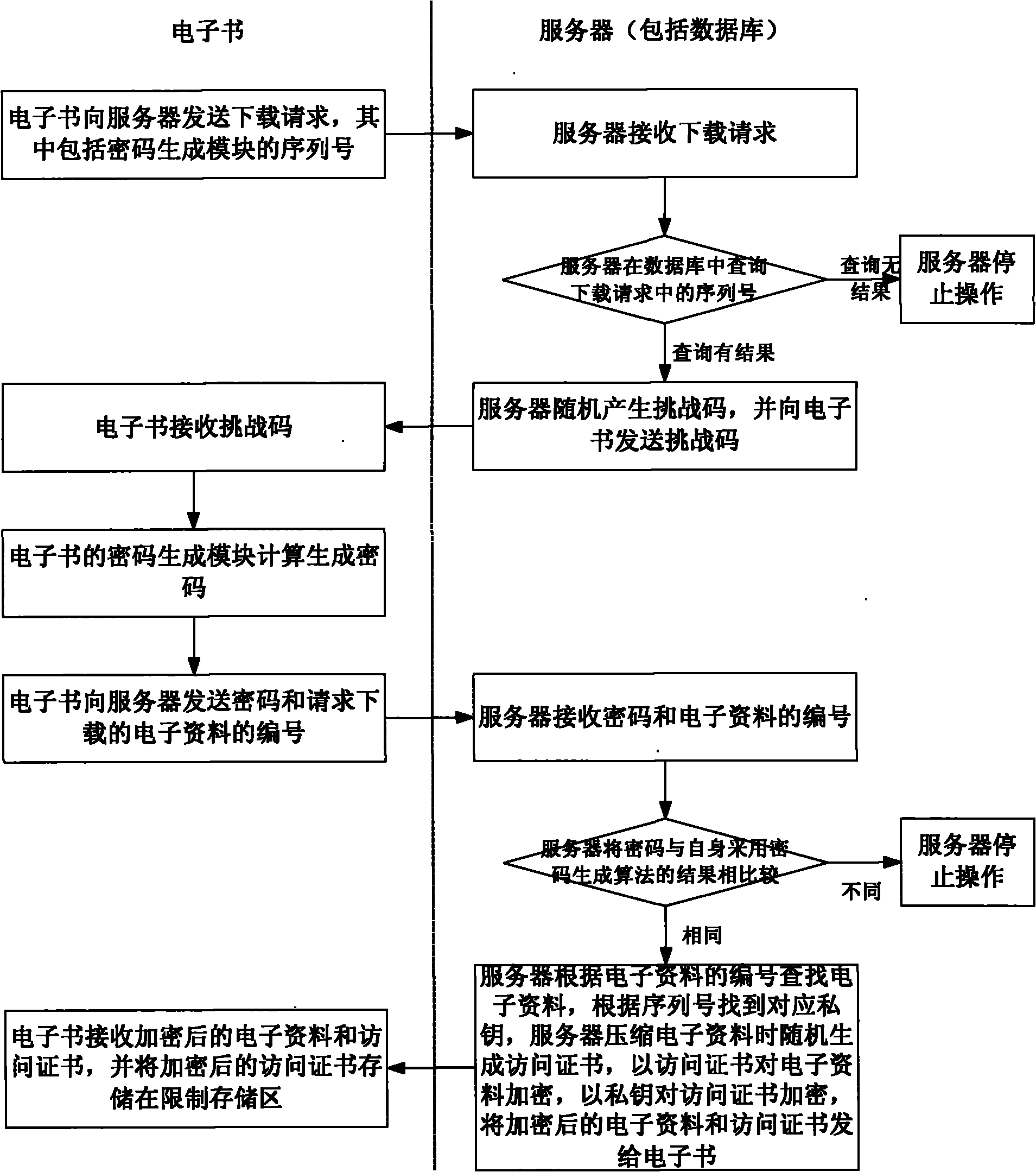
Electronic book with protection copyright
InactiveCN101782949AAchieve copyright protectionGuaranteed to be uniqueUser identity/authority verificationProgram/content distribution protectionNetwork connectionPassword
The invention discloses an electronic book with a protection copyright. The electronic book is an electronic data reading device comprising a processor, a memory module, a storage module, a display screen, a network connecting module, a bus and dynamic password generation modules, wherein the dynamic password generation modules are provided with serial numbers and internally provided with a dynamic password generation algorithm which is a computation rule between the inputs and the outputs of the dynamic password generation modules. Different dynamic password generation modules are provided with different serial numbers but are provided with the same dynamic password generation algorithm. The inputs of the dynamic password generation modules at least comprise the serial numbers of the dynamic password generation modules. The invention can verify a dynamic password in the download process of the electronic data and decrypt for two times in the access process, thereby effectively ensuring the unique identity of an electronic book user, being not easy to break and finally realizing the copyright protection on the electronic data.
Owner:上海盛轩网络科技有限公司
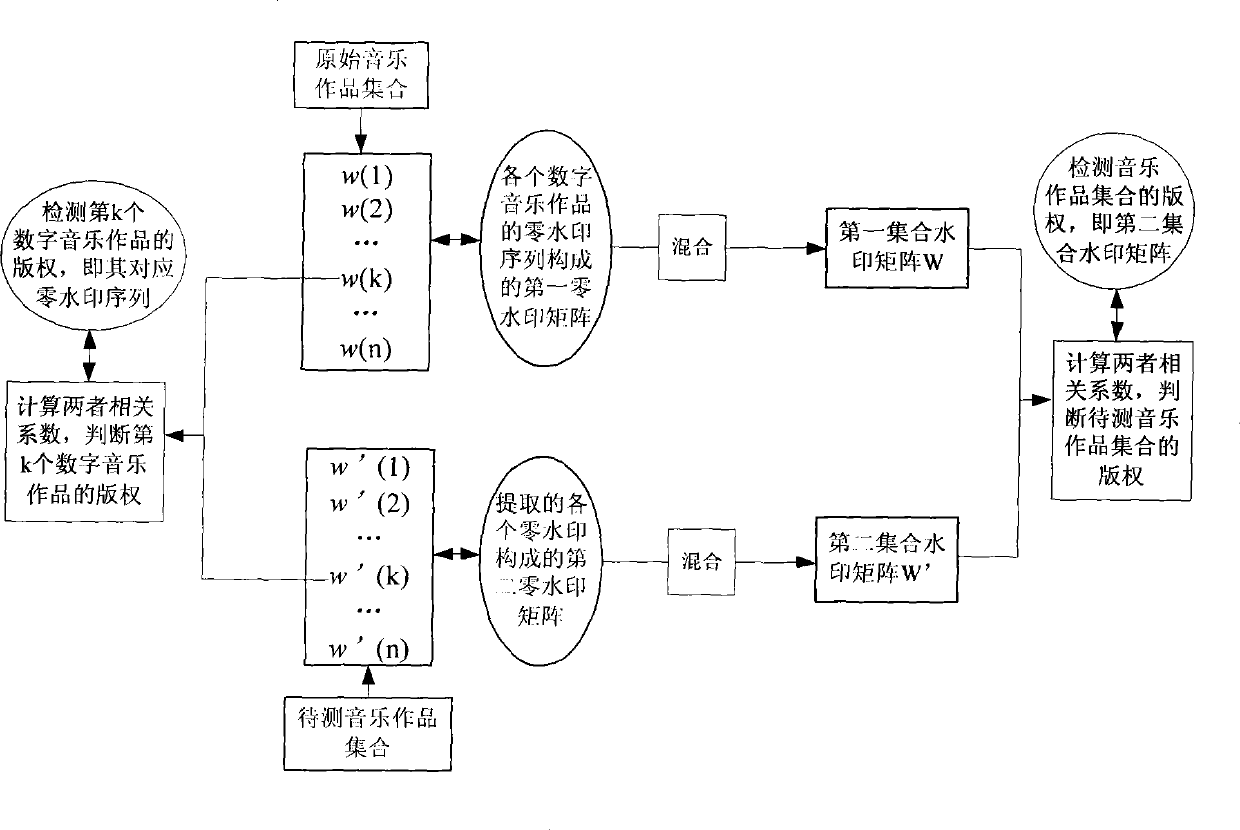
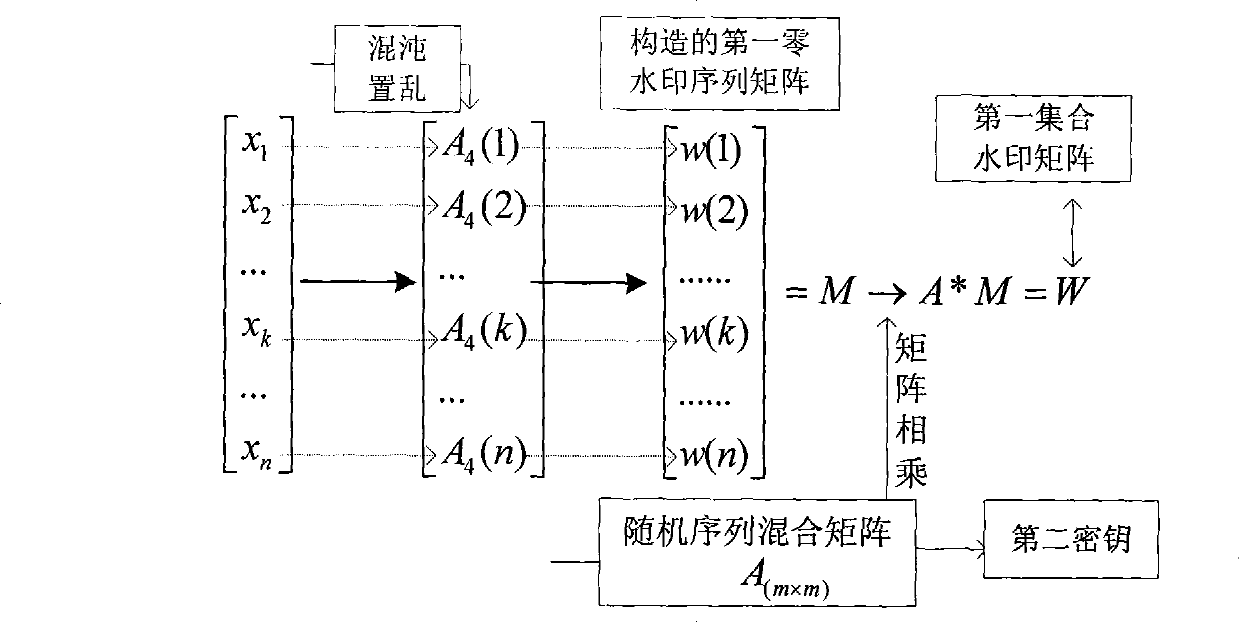
Digital watermark treatment method for copyright protection
InactiveCN101504850AAchieve copyright protectionReduce computational complexityRecord information storageRecording signal processingWorking setComputer science
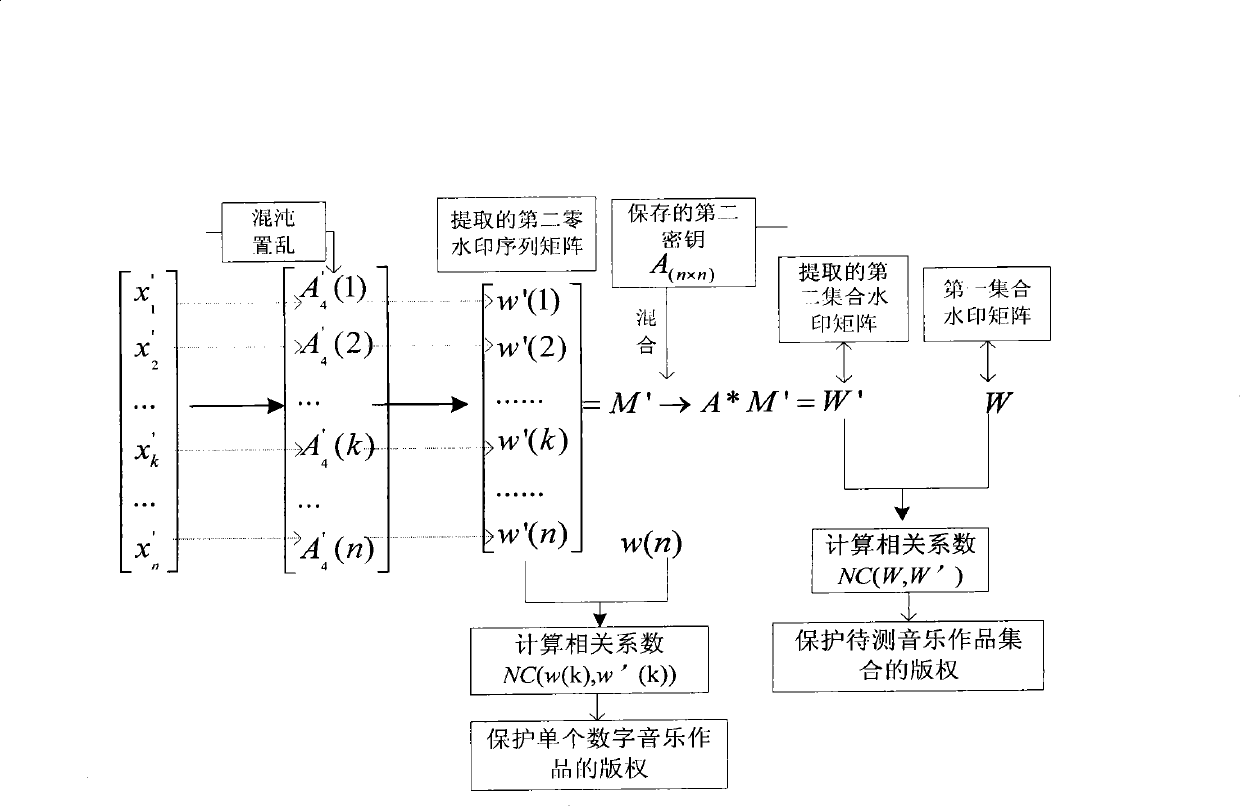
The invention discloses a digital watermark processing method for copyright protection, which comprises the following steps: by calculating related coefficients of a first set watermark matrix and a second set watermark matrix, judging whether the acquired related coefficients are more than a first set threshold value, and realizing the detection of the copyright protection for all digital musical works in a whole musical work set; and simultaneously, by calculating related coefficients of a first zero watermark sequence of each primary digital musical work and a second zero watermark sequence of the corresponding digital musical work to be detected, judging whether each acquired related coefficient is more than a second set threshold value, and realizing the detection of the copyright protection for a single digital musical work. Compared with the prior watermark processing method which uses the single digital musical work as a carrier, the method of the invention also can integrally protect the broadly existent musical work set in a form of set according to the characteristic that each digital musical work in the musical work set has the same copyright, and at the same time protects the single digital musical work.
Owner:NINGBO UNIV
A reversible information concealment framework with contrast pull-up utilizing histogram translation
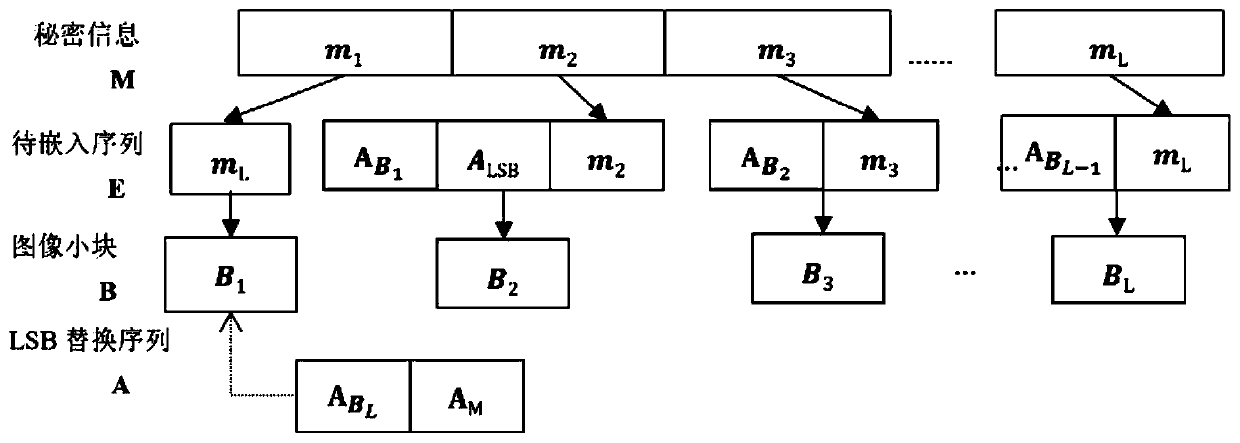
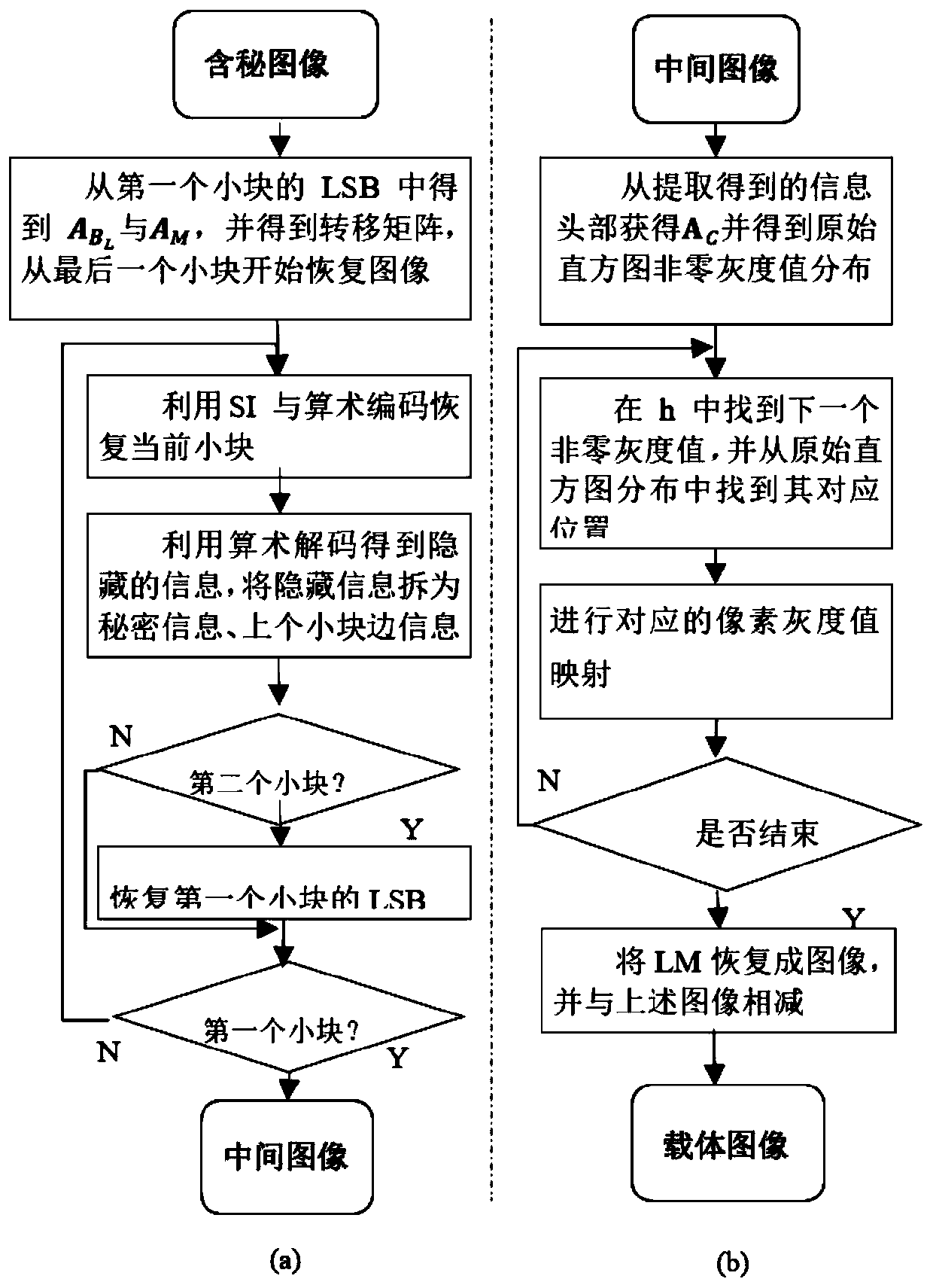
ActiveCN111464717AHigh embedding rateIncrease contrastImage enhancementDigital data protectionSteganalysisContrast level
The invention discloses a reversible information hiding framework with contrast pull-up by using histogram translation, and designs an improved RDH based on prediction error histogram optimal coding to expand a main body algorithm into an efficient hiding framework with dual embedding capability. Compared with a plurality of previous RDH technologies based on contrast ratio pull-up, the frameworkprovided by the invention not only has higher information embedding rate, but also can generate a secret-containing image with higher quality, and in addition, the security test also proves that the framework can effectively resist a plurality of famous steganalysis technologies (such as Enable classifiers and the like). Moreover, the framework has a dual-embedding function, and can embed copyright information such as an image identifier, a serial number, characters and the like into the carrier on the premise of ensuring the original appearance of the digital carrier, so as to achieve the purposes of copyright protection, integrity check and the like of the carrier.
Owner:章劲松
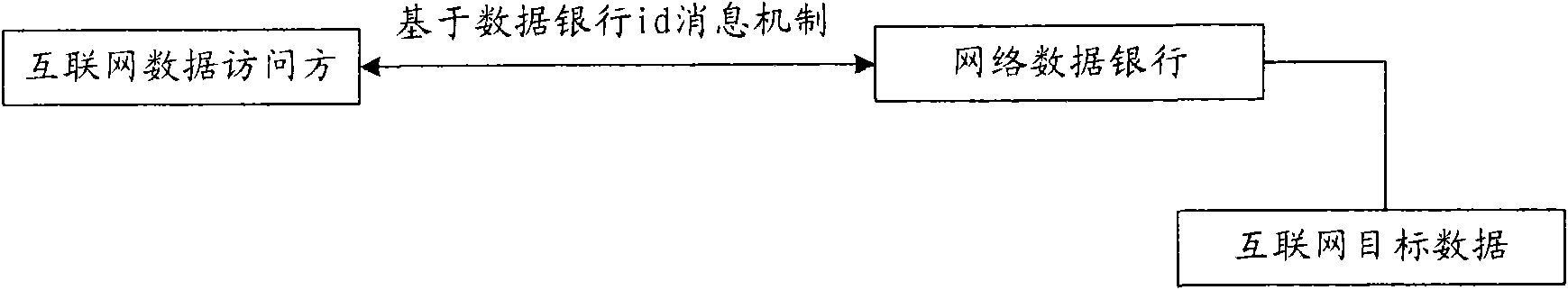
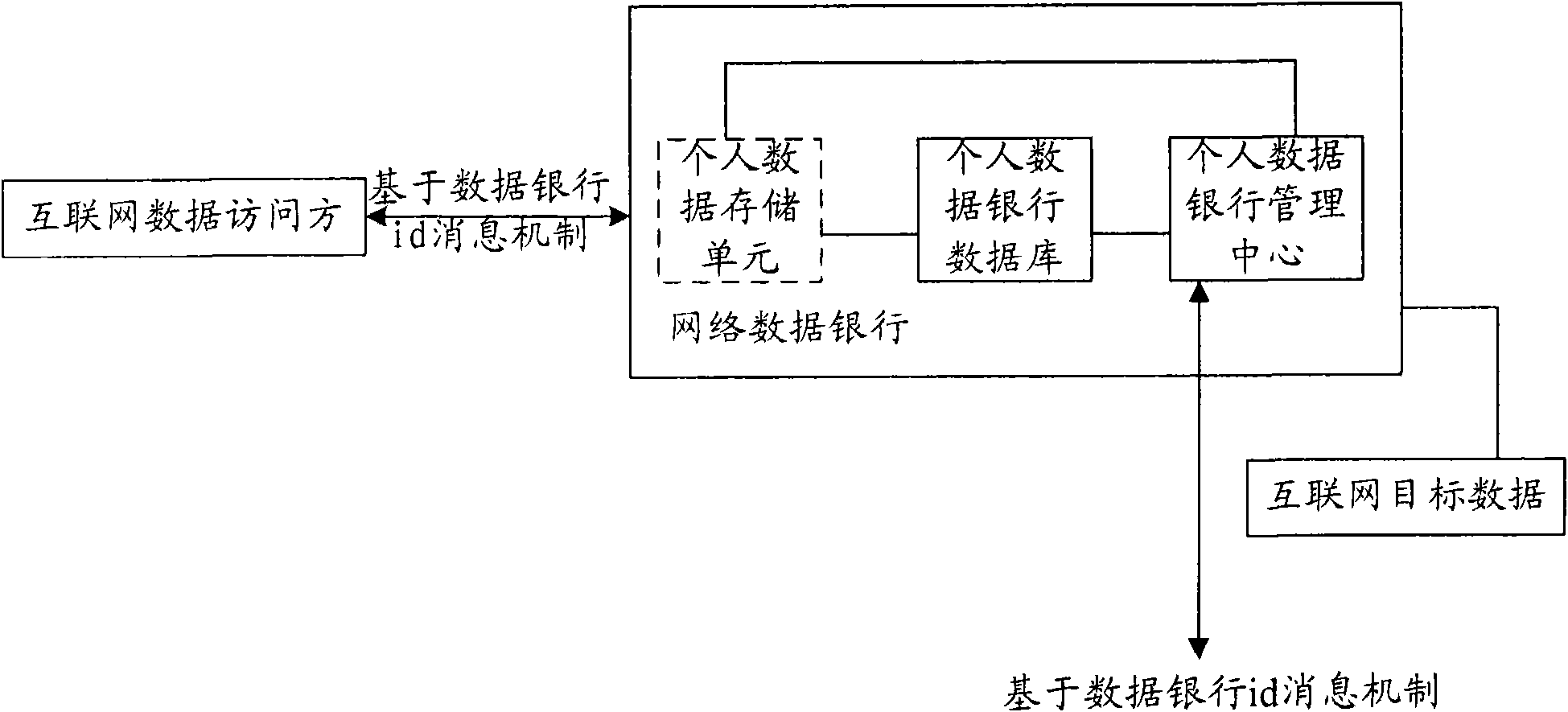
Method for managing data sharing in personal data bank and network side device
InactiveCN101561955AImprove security and confidentialityAchieve copyright protectionComplete banking machinesFinanceData sharingAuthorization
The invention discloses a method for managing data sharing in a personal data bank and a network side device, wherein the method comprises the following steps that: a management center of the personal data bank receives sharing management authorization information sent by a client, the sharing management authorization information comprises a time limit for accessing a personal data storage subunit, and the management center of the personal data bank acquires a personal data bank identification corresponding to the client and stores the time limit corresponding to the personal data bank identification; and the management center of the personal data bank receives access information sent by an access client, and feed back the data in the corresponding personal data storage unit to the access client after judging the current time is in the time limit corresponding to the personal data bank identification contained in the access information. The proposal of the invention achieves the management to the personal data storage subunit through the personal data bank identification similar to a bank account, and is convenient for by users to use; besides, the copyright protection of accessing personal data is achieved.
Owner:SHENZHEN WILL KORTH TECH
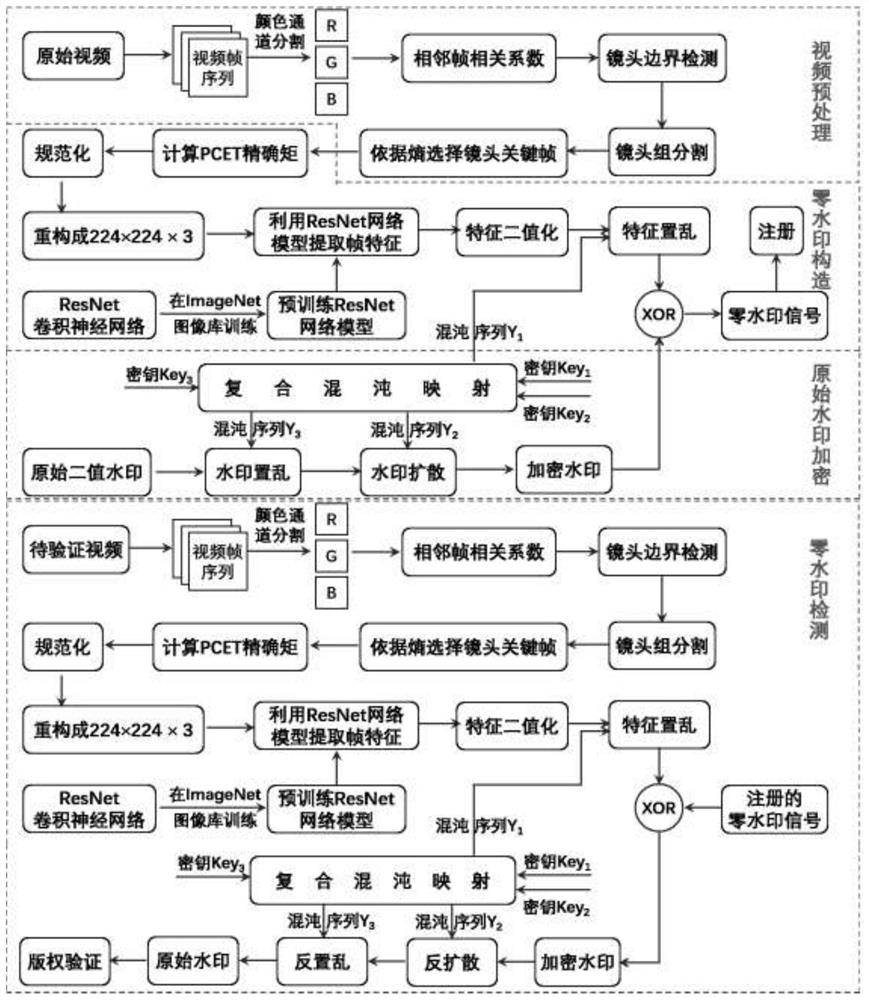
Robust video zero-watermarking method based on polar complex exponential transformation and residual neural network
PendingCN111984942ACopyright protectionSolve the extraction problem of robust featuresImage enhancementImage analysisPattern recognitionAlgorithm
The invention discloses a robust video zero-watermarking method based on polar complex exponential transformation and a residual neural network, and the method comprises the steps: carrying out the preprocessing of a video, and selecting a key frame of each group of shots; encrypting the original watermark of the video; obtaining an invariant moment of the key frame by means of polar complex exponential transformation; sending the invariant moment into a pre-trained deep residual neural network model; extracting robust content characteristics of the key frame; carrying out exclusive-OR operation on the robust content characteristics and the encrypted watermarks; generating a unique robust zero-watermark signal of the video, selecting a key frame from the to-be-verified video, extracting robust content characteristics of the key frame, and performing exclusive-OR operation on the robust content characteristics and the robust zero-watermark signal corresponding to the to-be-verified video to obtain an original watermark, thereby realizing copyright verification of the video. According to the robust video zero-watermark method, the balance problem between robustness and imperceptibility is solved, the desynchronization attack resistance is improved, and the copyright of video media can be effectively protected.
Owner:XIAN UNIV OF TECH
Method for downloading digital media information
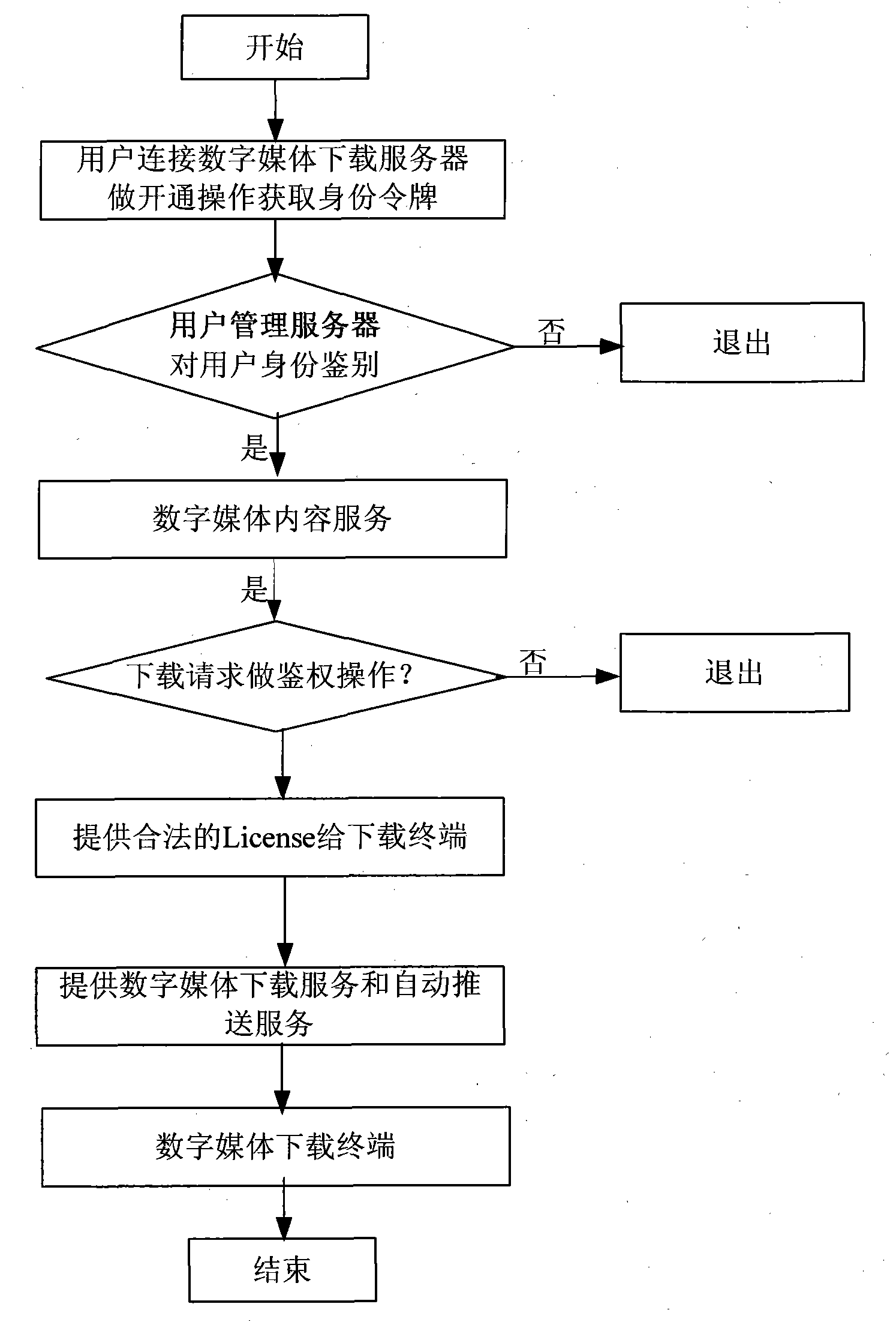
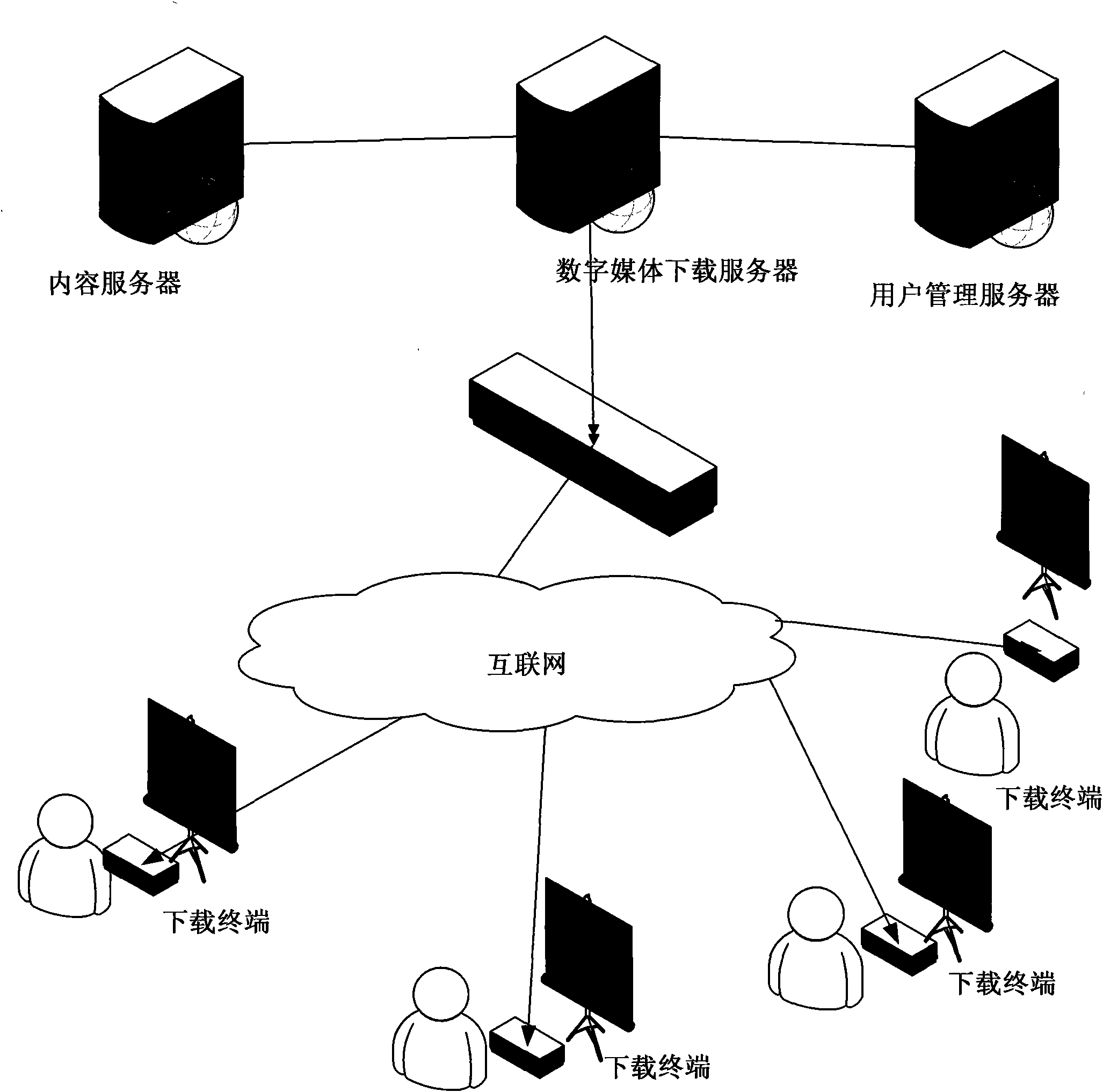
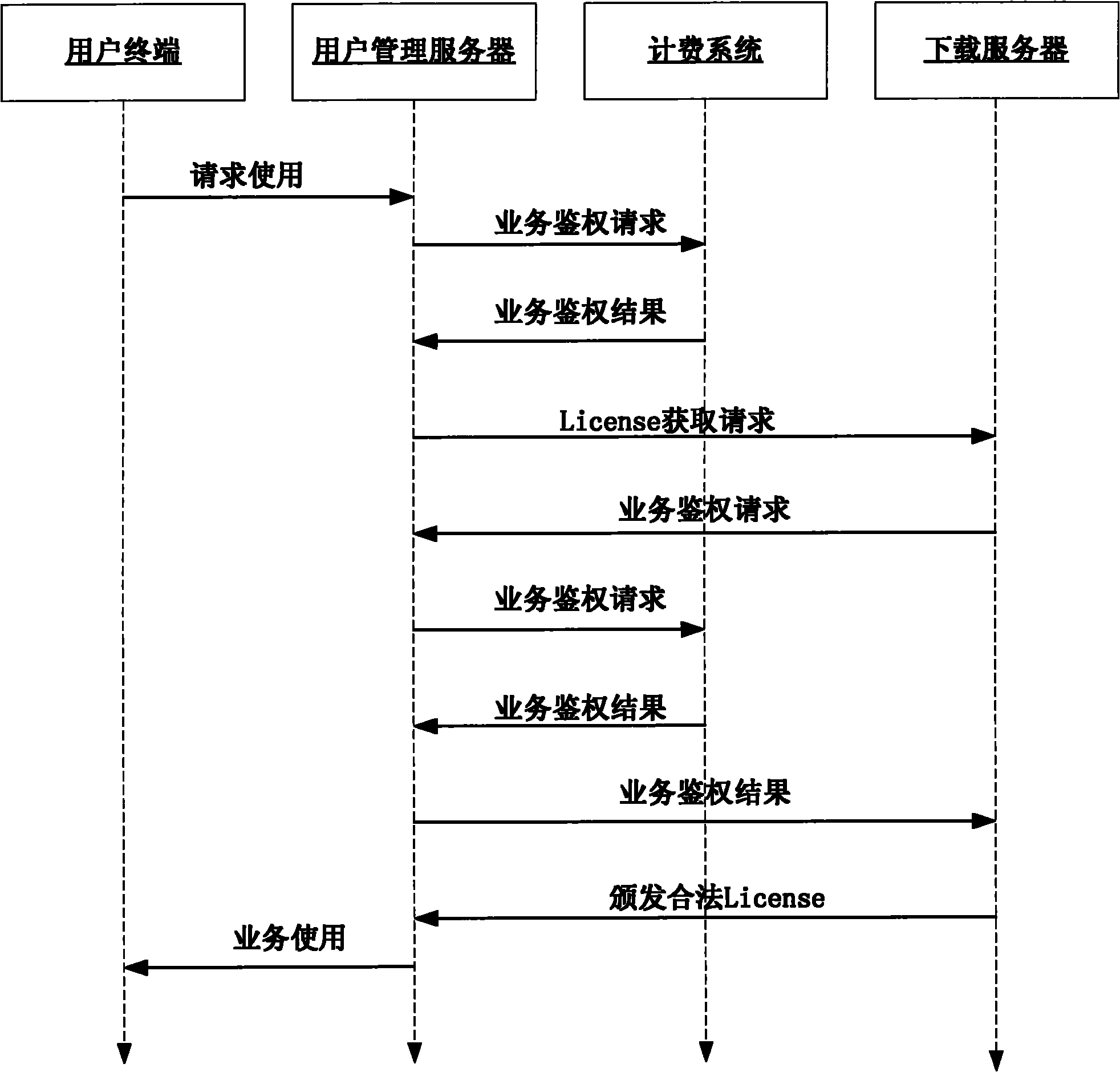
ActiveCN101795265APowerful download functionDownload to achieveUser identity/authority verificationQuality of servicePassword
The invention discloses a method for downloading digital media information. The method is characterized by comprising the following steps that: 1) a user registers and acquires an account and a password on a digital media downloading server; 2) the digital media downloading server performs identity authentication on a request sent by a digital media downloading terminal and issues an identity token for the user; 3) after the authentication succeeds, latest digital media information is checked; 4) after the user sends a program downloading request, a user management server performs downloading authentication; 5) a downloaded torrent file starts corresponding protocol downloading digital media information; and 6) the digital media downloading server automatically transmits the latest digital media information to the authenticated digital media downloading terminal and automatically downloads the transmitted digital media information. After the method is used, rapid flow and convenient share of the digital media information is achieved, the safety of the media information is ensured and the service quality and reliability of an entire digital media downloading system are enhanced.
Owner:CHINA HUALU GRP
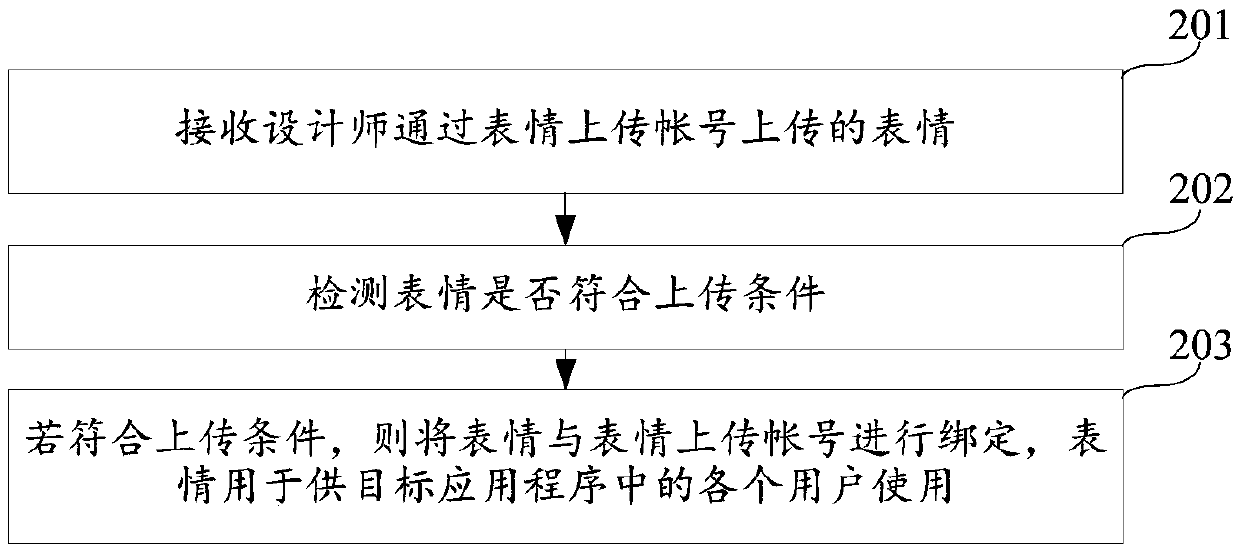
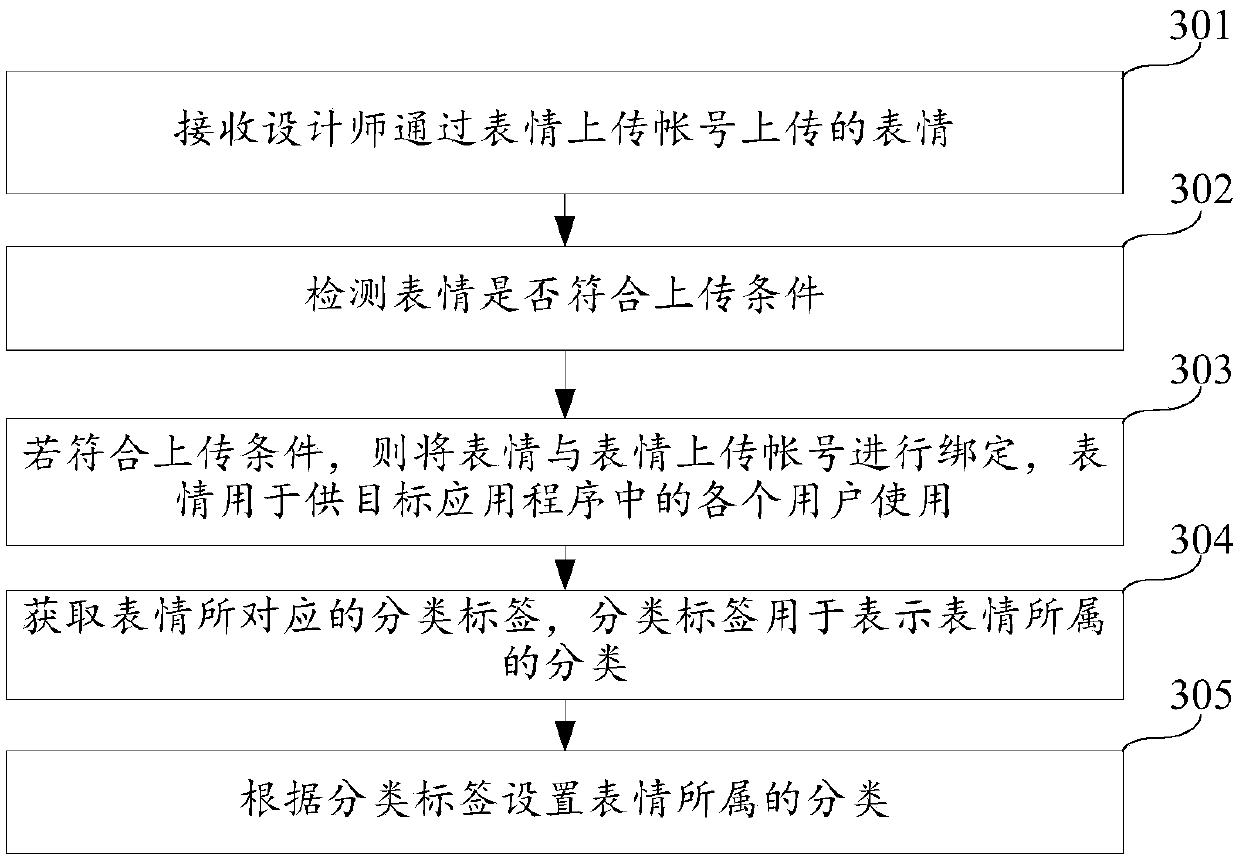
Expression uploading method and device
InactiveCN105512516AAchieve copyright protectionSolve the problem that the expression cannot be copyrightedProgram/content distribution protectionApplication softwareOperating system
Owner:TENCENT TECH (SHENZHEN) CO LTD
Immune and digital image watermarking method for leveled rights management of digital works
ActiveCN106408503AGuaranteed robustnessAchieve copyright protectionImage data processing detailsTechnical supportInformation technology
The invention relates to an immune and digital image watermarking method for leveled rights management of digital works. The method comprises a part of watermark embedded and leveled quality lock control processing and a part of leveled rights management and protection; watermark embedded and leveled quality lock control processing is composed of a watermark embedding process and a leveled quality lock control process; the watermark embedding process comprises watermark pre-processing, copyright watermark embedding, rights watermark embedding and quality lock and control thereof, and after watermark embedding, different levels of image qualities are locked and controlled in the leveled manner; and leveled rights management and protection is formed by key distribution and rights distribution. According to the invention, leveled using rights and copyright rights protection are realized, related rights are separated effectively and are thus not overlapped, attacks according to similarity of adjacent pixels can be prevented effectively, and thus, the method serves as a rights management mode in the authorization mode, is highly safe, and provides technical support for safe sharing of digital image works in a digital community.
Owner:HAINAN UNIVERSITY
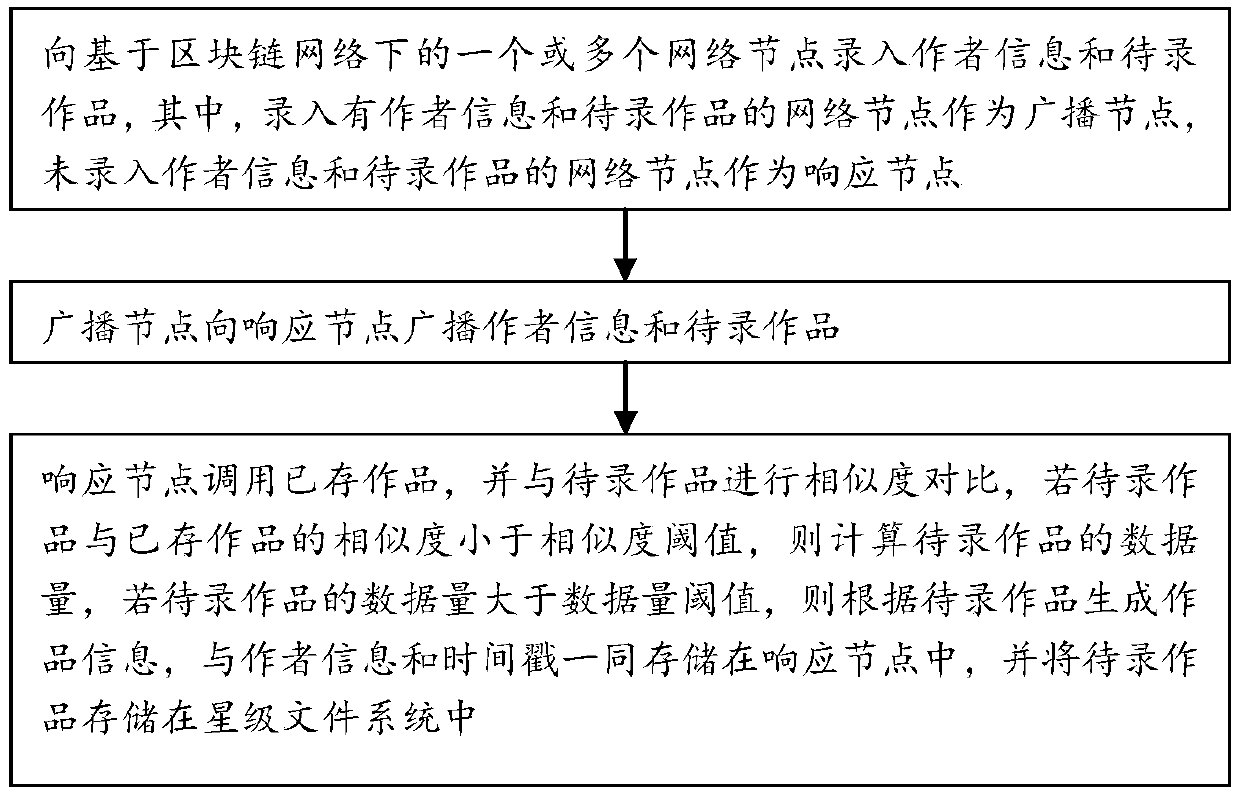
Screening method and a screening system for work input based on a block chain
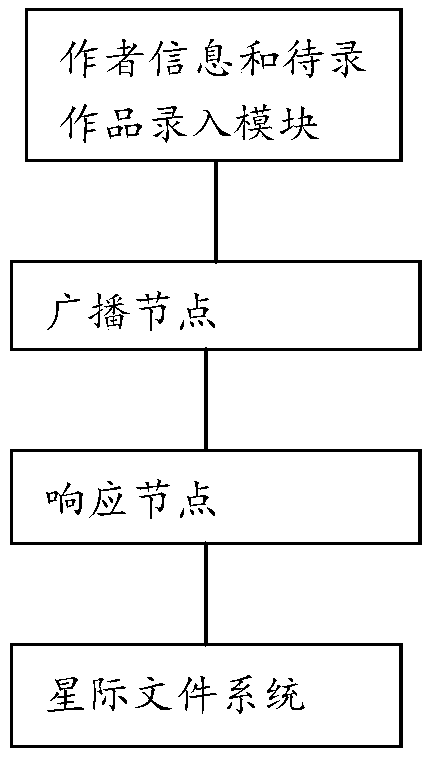
ActiveCN109582641AAchieve copyright protectionRealize on-chainFile access structuresProgram/content distribution protectionScreening methodChain network
The invention relates to a screening method and a screening system for work input based on a block chain. The method comprises the following steps that author information and to-be-recorded works areinput into one or more network nodes based on a block chain network, the network nodes where the author information and the to-be-recorded works are input serve as broadcast nodes, and the network nodes where the author information and the to-be-recorded works are not input serve as response nodes; The broadcast node broadcasts author information and to-be-recorded works to the response node; Calling the stored works by the response nodes, comparing the similarity with the to-be-recorded works, and storing author information and the to-be-recorded works if the similarity between the to-be-recorded works and the stored works is smaller than a similarity threshold value. According to the method and system, similarity comparison is conducted on the to-be-recorded work and the stored work, ifthe similarity between the to-be-recorded work and the stored work is smaller than the similarity threshold value, the to-be-recorded work and author information are stored, a user can conveniently input personal information and work information through a block chain, and therefore copyright protection is achieved.
Owner:BEIJING RZXT TECH DEV CO LTD
Method for adding digital watermark to three-dimensional model layout and detecting digital watermark
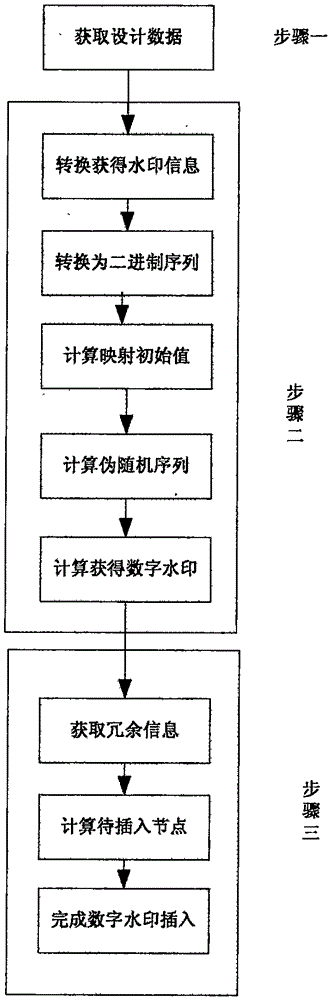
InactiveCN106815798AImprove robustnessDoes not affect geometryImage data processing detailsTimestampComputer science
The invention discloses a method for adding a digital watermark to a three-dimensional model layout and detecting the digital watermark, and the method is characterized in that the method comprises the following steps: firstly obtaining the three-dimensional model layout, and reading the design data of the three-dimensional model layout; secondly converting the design data and timestamp information into binary watermark information, employing a pseudorandom sequence for modulation, and obtaining the digital watermark; enabling the generated digital watermark to be embedded into the redundancy information of the three-dimensional model layout, calculating an insertion node at each binary bit, and carrying out the insertion. The method can effectively solve a copyright protection problem of the three-dimensional model layout.
Owner:北京慧点科技有限公司
Video processing method, device, equipment and medium
InactiveCN110611830AReduce data volumeSmall amount of calculationSelective content distributionResource consumptionVideo processing
The invention discloses a video processing method, a device, equipment and a medium, is applied to the technical field of encryption, and is used for solving the problems that a video encryption and decryption method in the prior art is relatively high in calculated amount and resource consumption and relatively low in encryption and decryption efficiency. The method specifically comprises the steps that a server encrypts metadata in a video file to obtain an encrypted video file; and a client acquires the encrypted video file from the server, decrypts the encrypted metadata in the encrypted video file and then decodes and plays the encrypted metadata. Thus, by encrypting the metadata in the video file, copyright protection of the video file can be realized, the data volume of the metadatais relatively small, the calculation amount during encryption and decryption of the metadata is relatively small, the encryption and decryption efficiency is relatively high, and occupied processingresources are relatively few.
Owner:TENCENT TECH (SHENZHEN) CO LTD
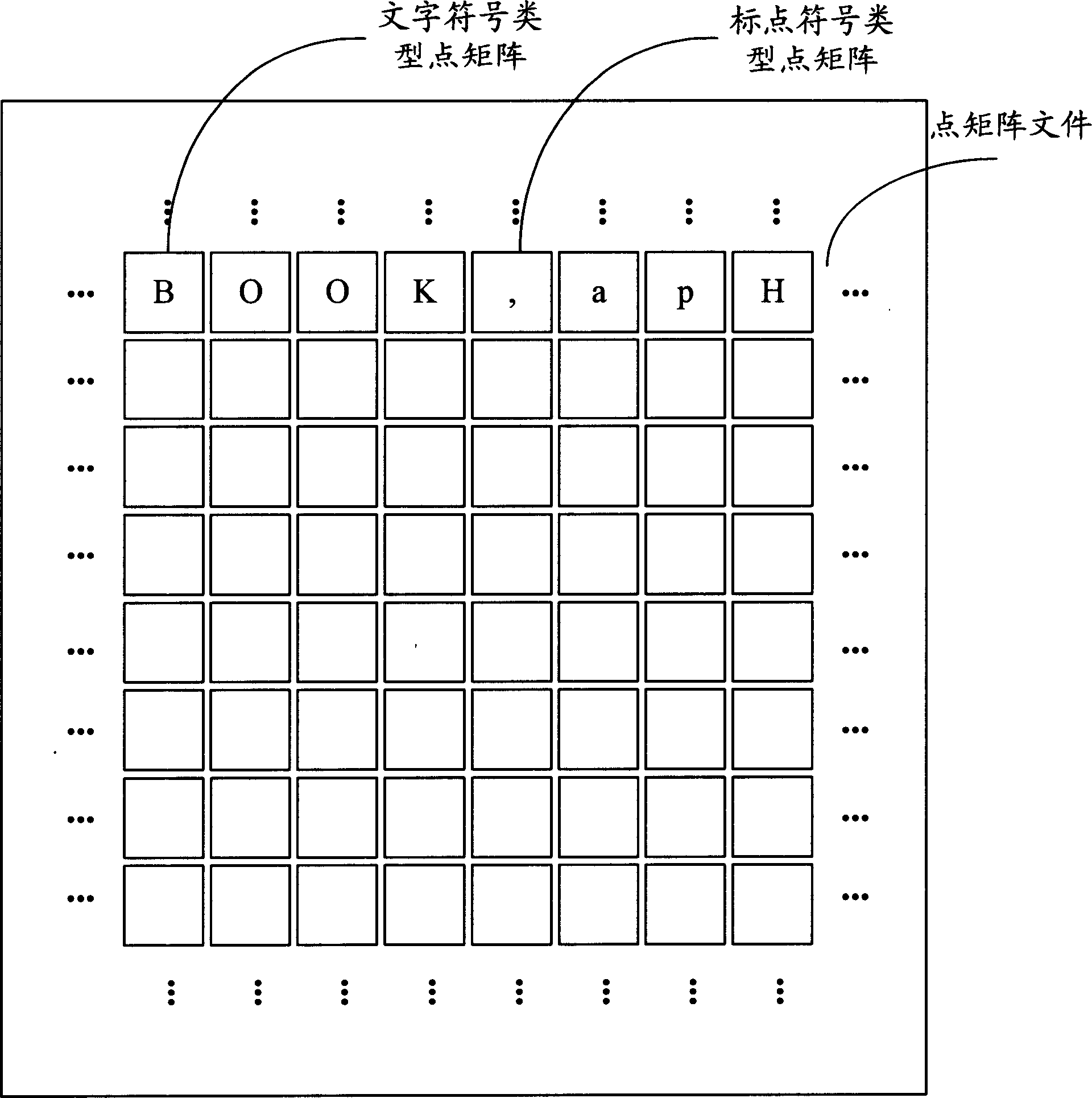
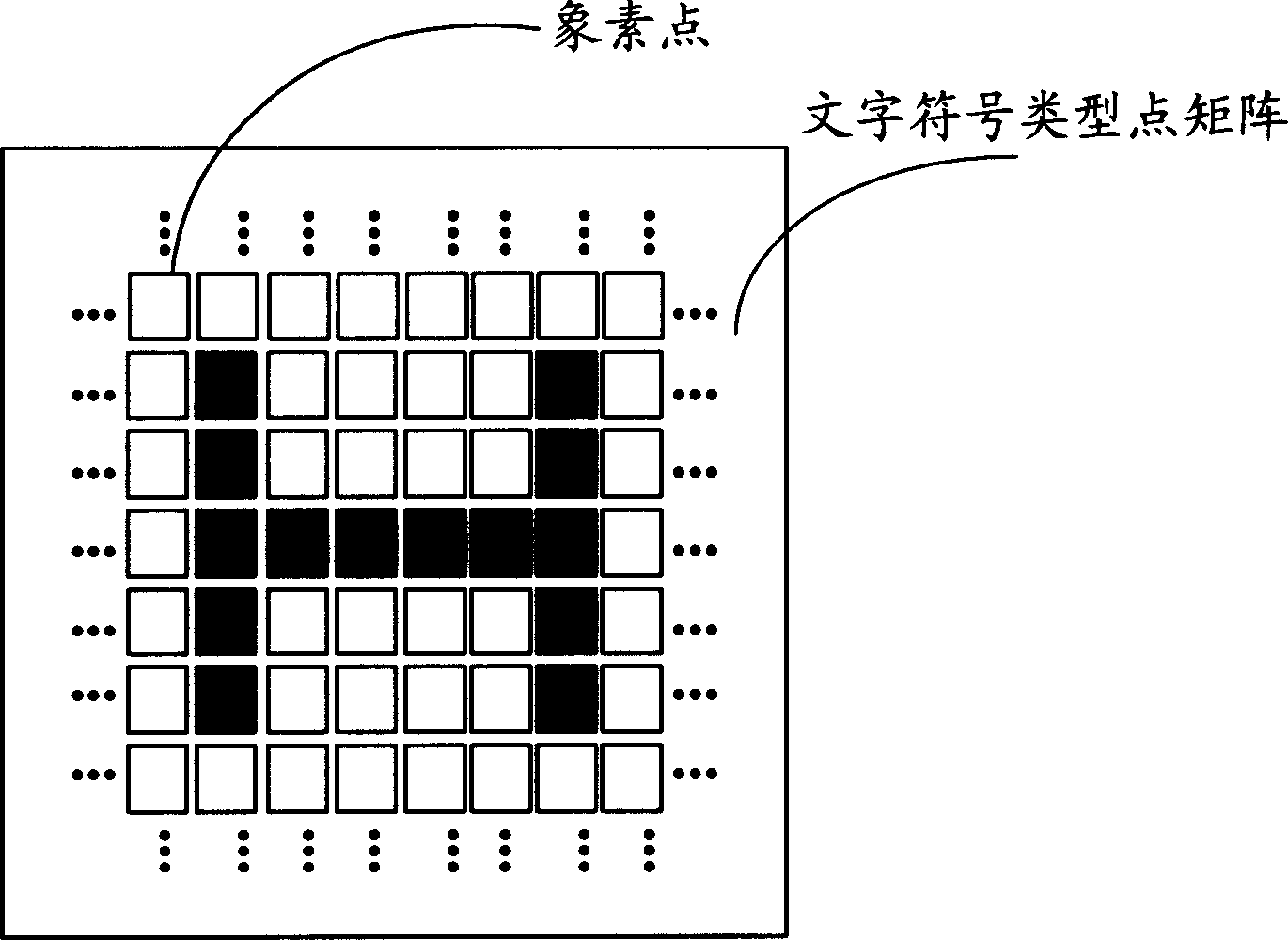
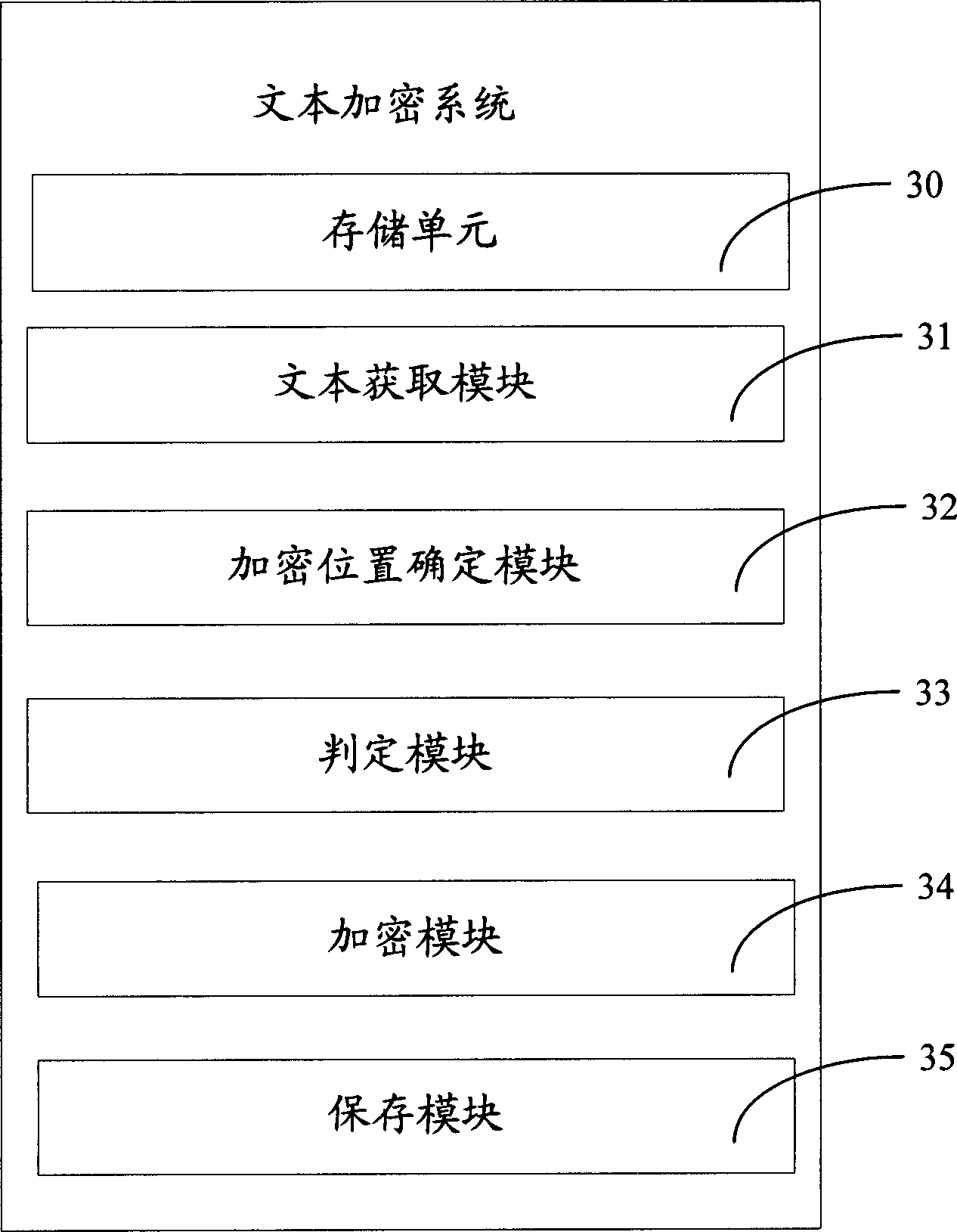
Text encryption system and method
InactiveCN1881382APrevent piracyAchieve copyright protectionImage data processing detailsCoding/ciphering apparatusComputer hardwareDot matrix
Disclosed is a text encryption system and method, wherein the system includes a memory unit for storing text information, a text acquisition module for acquiring dot matrix file of the text to be enciphered from the memory unit, each dot matrix in the dot matrix file corresponding a sign pattern (character symbol or non-character symbol), each pixel dot corresponding a display attribute and a brightness value, an encryption position determination module for determining encryption position according to preset position parameters, a decision module for deciding symbol pattern of the dot matrix and display attribute of the pixel dot on the encryption position, an encryption module for adjusting brightness value of the pixel dots on the encryption position, and a storage module for storing the enciphered text information to the memory unit. The system can be used to adjust the brightness value of the pixel dot corresponding the characters in the text, thus realizing explicit encryption for the text, wherein the encryption information of the text can be indicated explicitly during the display procedure in the mode of paper document, the owner of the copyright can be identified and copyright protection can be implemented.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
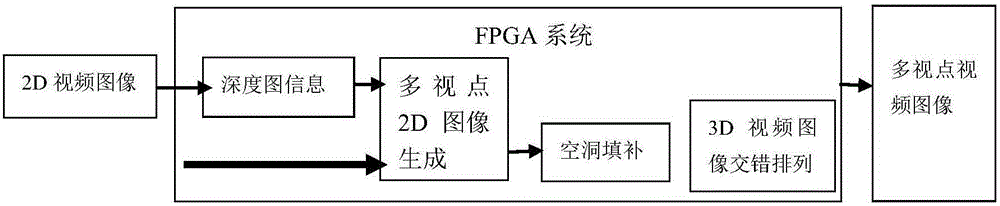
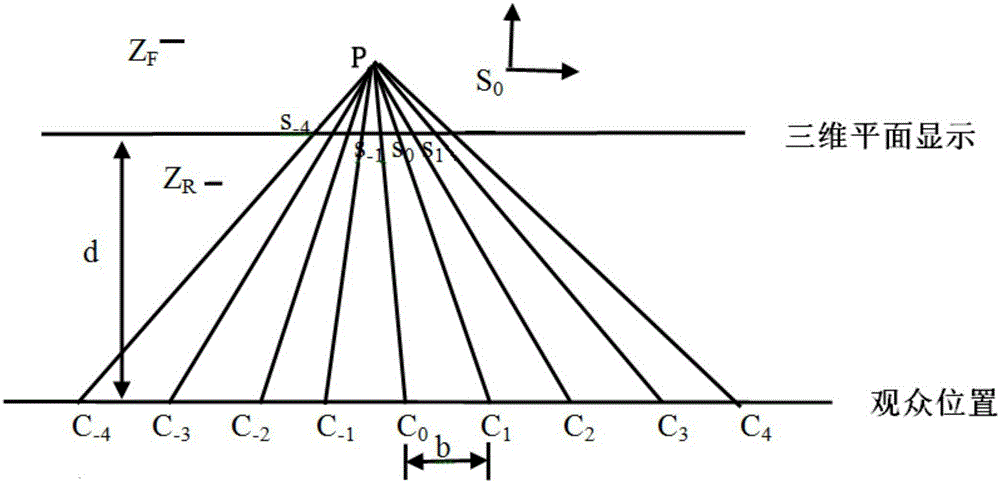
Glass-less 3D video encryption method based on digital watermark encryption and system
InactiveCN105187817AGood encryptionAchieve copyright protectionSelective content distributionViewpointsComputer graphics (images)
The invention discloses a glass-less 3D video encryption method based on digital watermark encryption and a system. The method comprises steps that, step 1, randomized numbers are combined to form an original digital watermark in a random arrangement mode, and the original digital watermark is divided into m sub digital watermarks randomly; step 2, the m sub digital watermarks are respectively embedded in each viewpoint image of an two-dimensional frame image to acquire the watermark encryption two-dimensional frame image; step 3, step 1 and the step 2 are cycled till watermark encryption for all two-dimensional frame images is carried out, and the watermark encryption two-dimensional frame images are converted into glass-less 3D videos; and step 4, sub digital watermarks of viewpoint images included by glass-less 3D video frame images are extracted to acquire original digital watermarks. The method has properties of excellent robustness and invisibility, glass-less 3D videos can be rapidly and conveniently encrypted, copyright protection for the glass-less 3D videos can be further realized, and the video playing and displaying effects are not damaged.
Owner:WUHAN UNIV
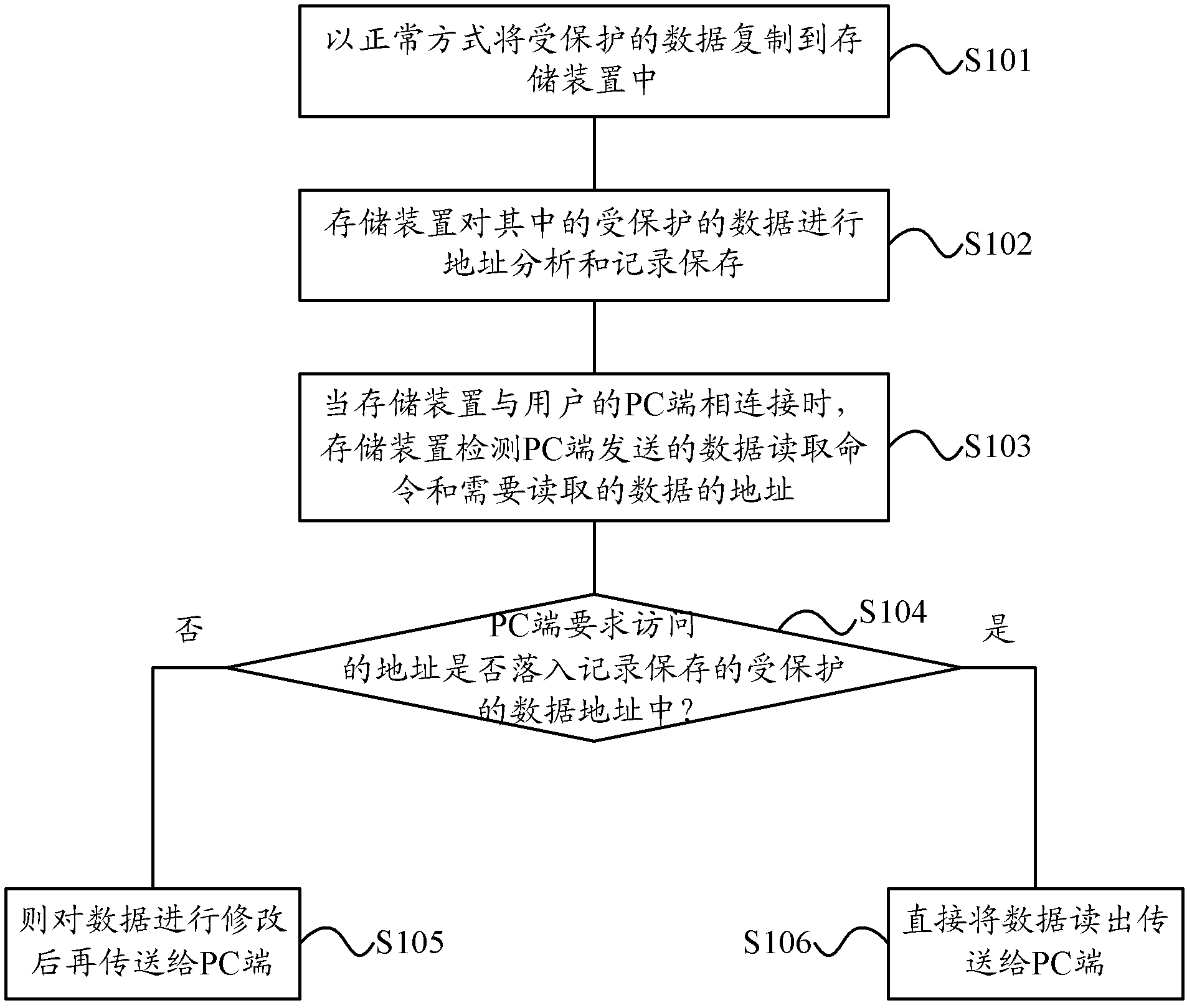
Method for limiting protected data in storing device from being copied to personal computer (PC) end
InactiveCN103106354AEasy to implementEasy to useUnauthorized memory use protectionProgram/content distribution protectionData needsPersonal computer
The invention provides a method for limiting protected data in a storing device from being copied to a personal computer (PC) end. The method includes that the protected data is copied to the storing device with a normal method; the storing device performs address analysis and recording storage on the protected data; the storing device detects a data reading command sent by the PC end and an address of data needing to be read when the storing device is connected with the PC end; the storing device compares the address required by the PC end to be accessed with an address of the protected data which are recorded and stored; and if the address required to be accessed is located in the address of the data recorded and stored, the data are transmitted to the PC end after being modified, and otherwise, the data are directly read and transmitted to the PC end. The method for limiting the protected data in the storing device from being copied to the PC end is simple to achieve, convenient to use, and dispensed with a complex authorization mechanism. The storing device can achieve the data copy limiting only through the method of firmware modifying, hardware modifying is not required, and hardware cost is not increased.
Owner:SINO WEALTH ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com