Visual secret sharing-based image content tampering detection method
A technology of secret sharing and image content, applied in image data processing, image data processing, instruments, etc., can solve the problems of no image integrity authentication function, weak robustness of image processing operations, and no obvious update of algorithms, etc., to achieve Realize the effects of copyright protection, high efficiency and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
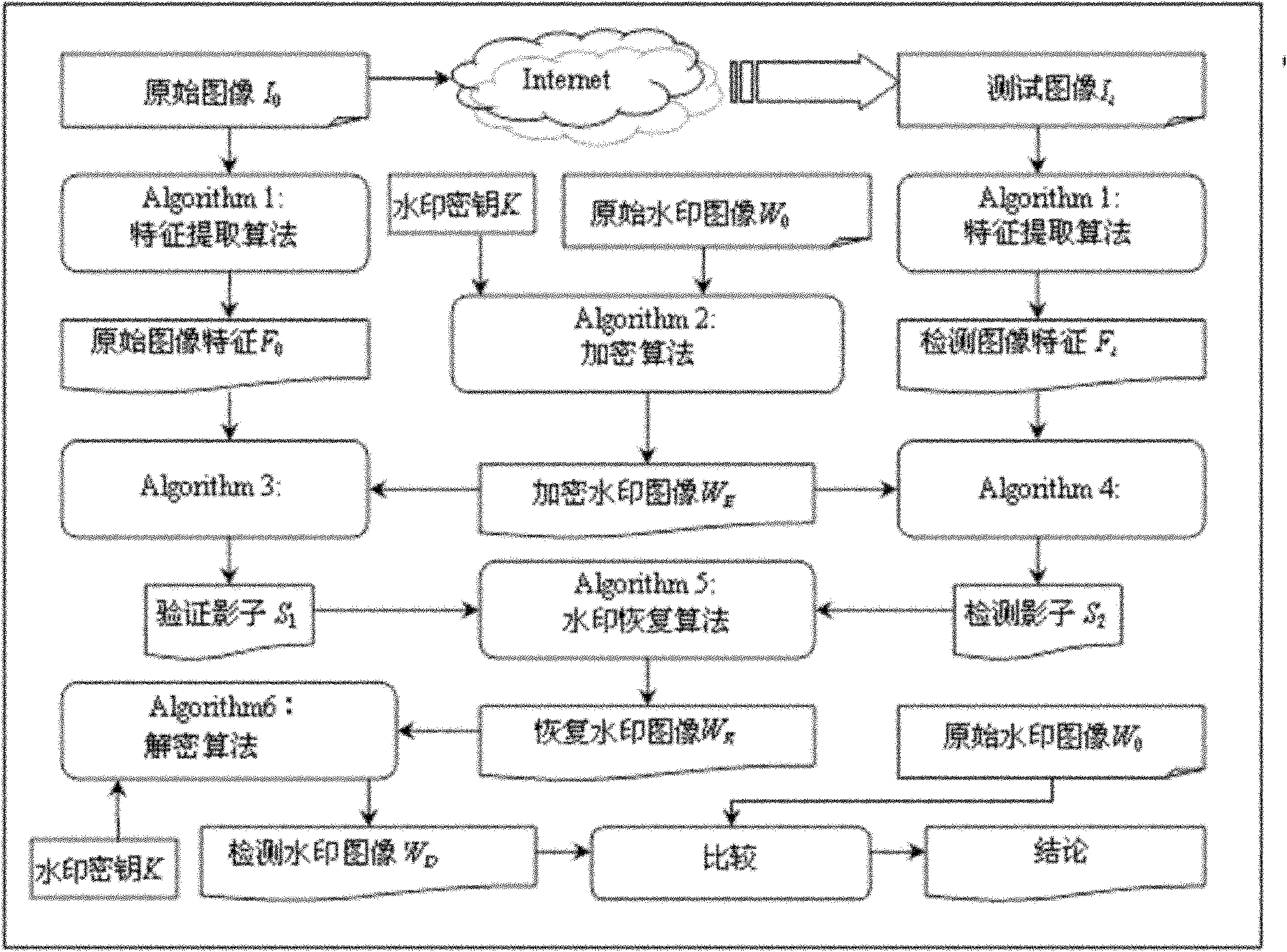
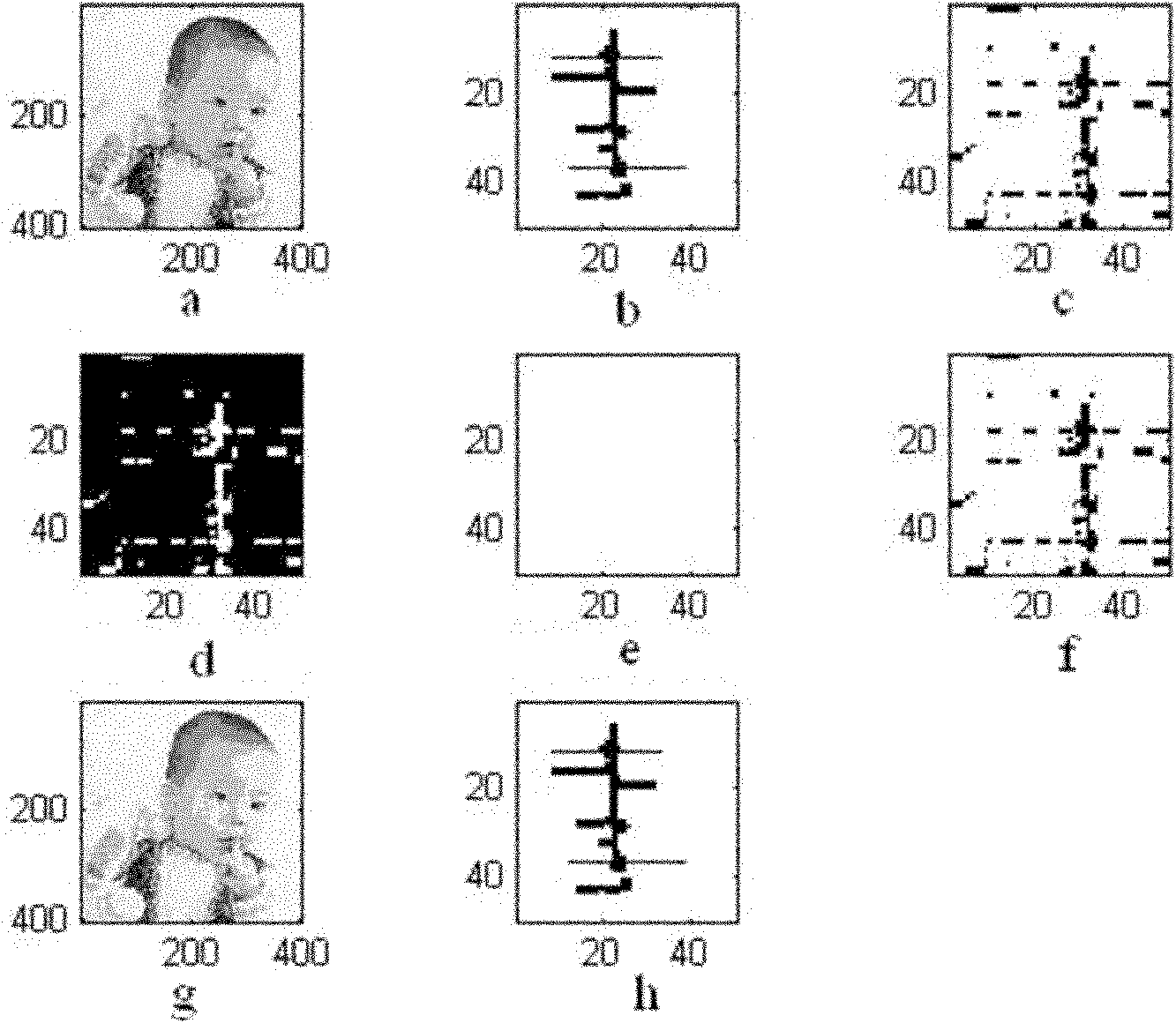
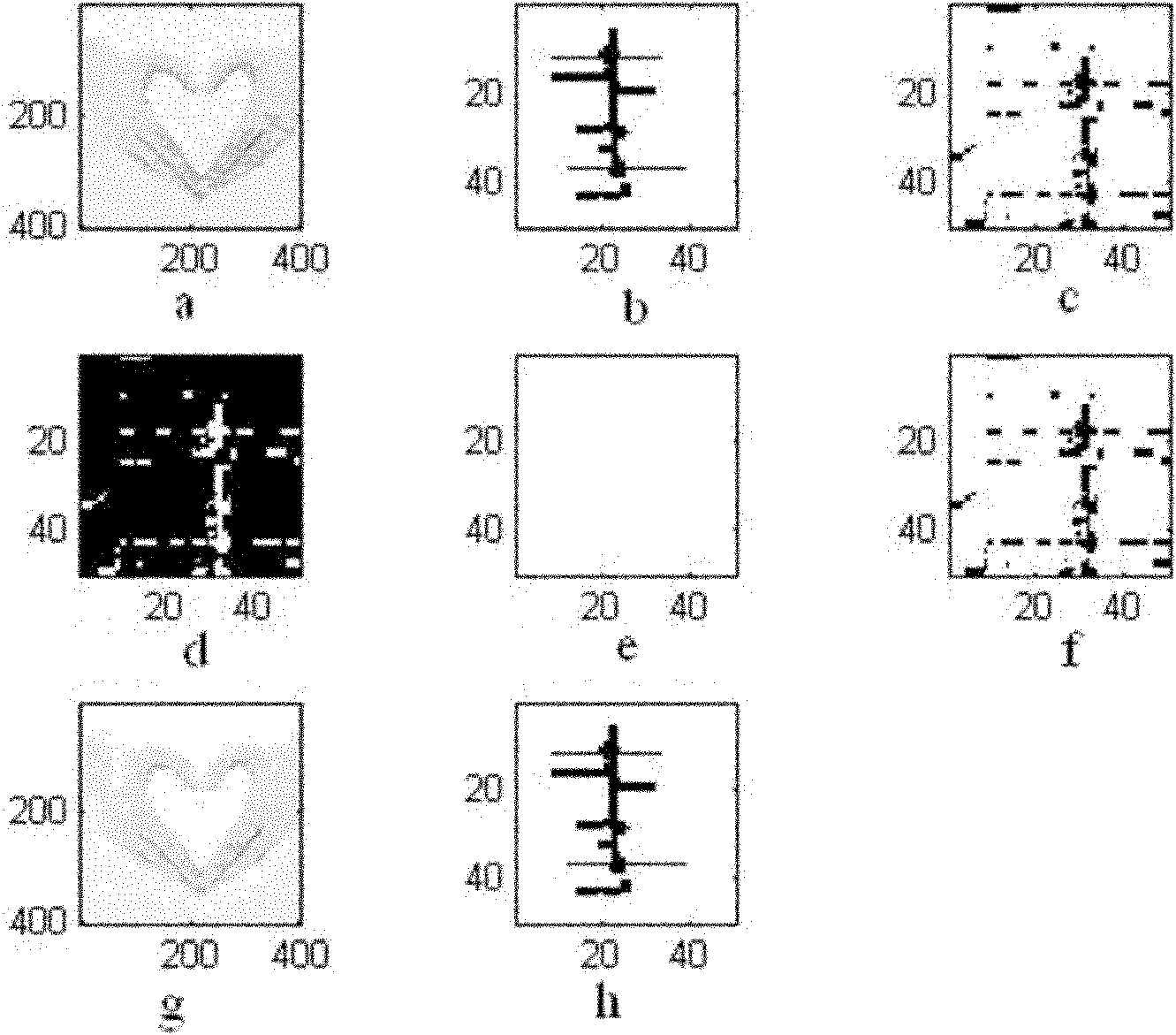
[0030] Such as figure 1 Shown, the present invention a kind of image content tampering detection method based on visual secret sharing, comprises the following steps:
[0031] Information sender:
[0032] Step 1. For a given original image I 0 , use the feature extraction algorithm Algorithm 1 to extract the original image feature F 0 ;
[0033] Among them, the feature extraction algorithm Algorithm 1 in step 1 is:
[0034] Take the input N×N original image I 0 Divide into 8×8 non-overlapping blocks to get N 2 / 64 image blocks, denoted as I ij , where i=1, 2,..., N / 8, j=1, 2,..., N / 8; perform 3-level db1 wavelet decomposition on each image block to obtain each 8×8 image block LL 3 Subband wavelet coefficient a ij (i=1, 2,..., N / 8, j=1, 2,..., N / 8), generate the original image feature F 0 :
[0035] F 0 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com