Method for limiting protected data in storing device from being copied to personal computer (PC) end
A storage device and data replication technology, applied in the direction of program/content distribution protection, preventing unauthorized use of memory, etc., can solve the problems of rising R&D costs, unable to copy songs, unable to play, etc., to reduce the risk of inventory, protect Works well, achieves simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
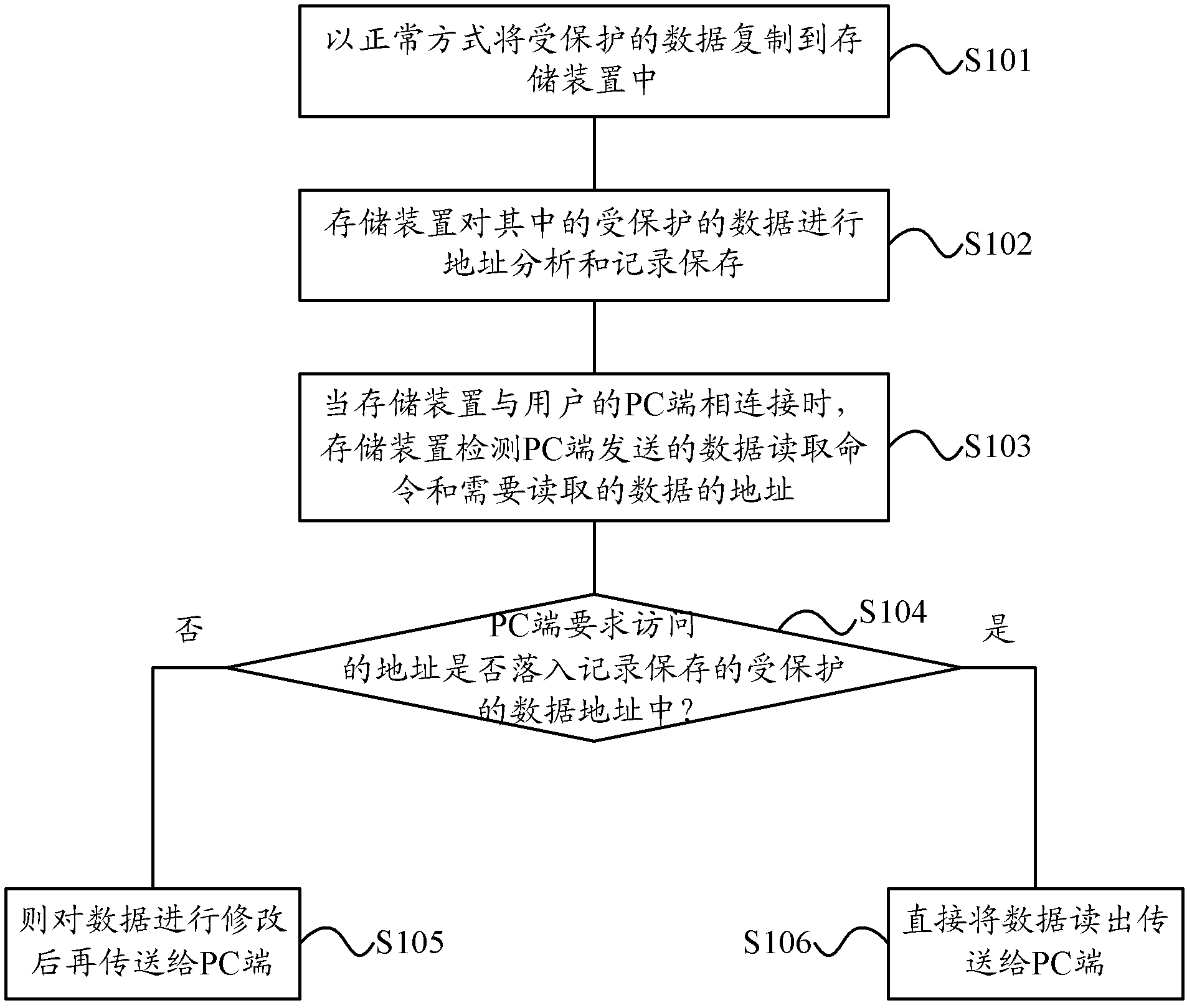
[0024] The present invention will be further described below in conjunction with specific embodiment and accompanying drawing, set forth more details in the following description so as to fully understand the present invention, but the present invention can obviously be implemented in a variety of other ways different from this description, Those skilled in the art can make similar promotions and deductions based on actual application situations without violating the connotation of the present invention, so the content of this specific embodiment should not limit the protection scope of the present invention.
[0025] figure 1 It is a flow chart of a method for copying protected data in a storage device to a PC under the limitation of an embodiment of the present invention. This method can be used to protect data when copying copyright-protected data in a storage device to a PC, to avoid acquired by the user. Such as figure 1 As shown, the above methods may include:
[0026...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com