Protection method of IP (internet protocol) core with determined validity
A technology of validity period and state machine, which is applied in the fields of program/content distribution protection, instrumentation, and electrical digital data processing. Guaranteed integrity and good concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described in detail below in combination with specific embodiments.
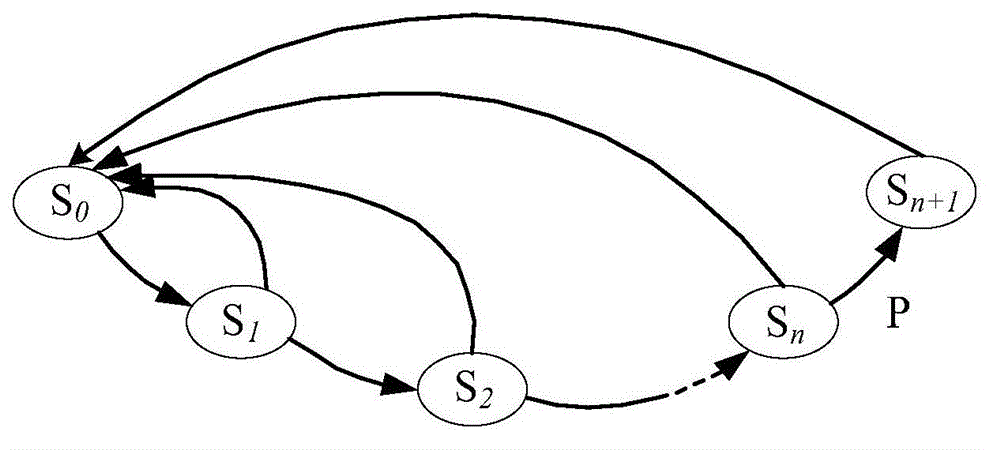
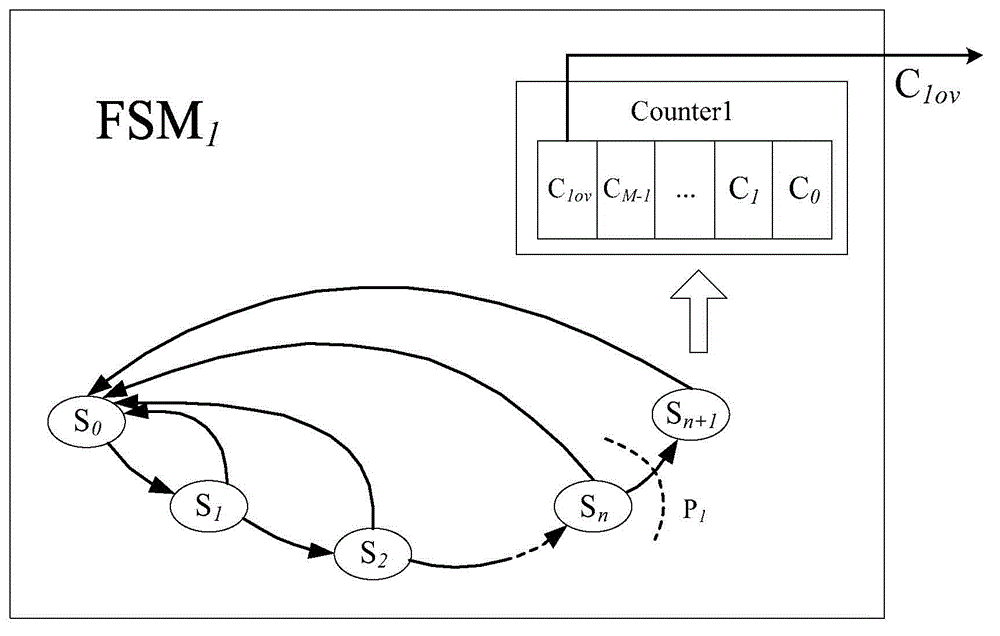
[0014] The timing function is usually realized by a counter in the hardware circuit, and an operation of adding 1 to the counter is triggered in each clock cycle of the IP core circuit. An n-bit counter consists of n registers. When the registers are all 1s, the overflow bit is set to 1, and the remaining bits are cleared to 0. The time for the counter to overflow once is:
[0015] T=2 n ·T clk (1)
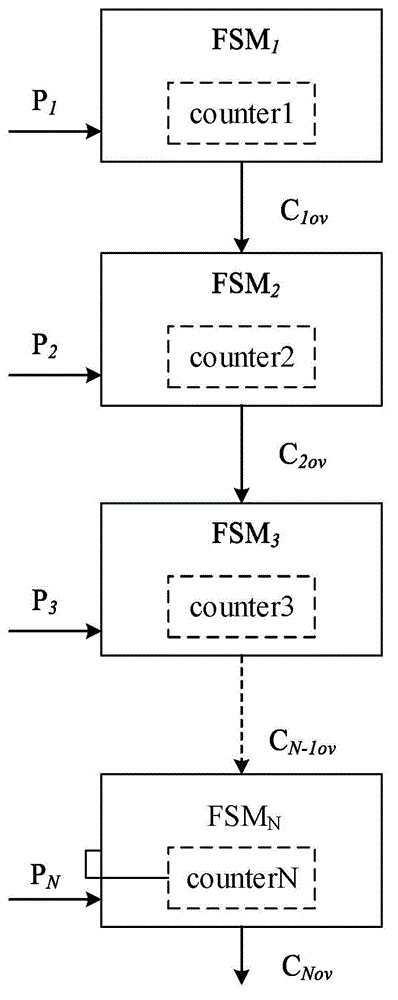
[0016] In some high-frequency clock IP core circuits, to achieve a longer counting period, it is necessary to increase the number of counter bits. For example, when the clock frequency is 100MHz, that is, when the cycle is 10ns, to enable the IP core circuit to work continuously for 1 day, according to the formula (1), the number of bits of the counter is about 43 bits. If this counter structure is directly used, it will not only greatly increase the area overh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com