WAPI-based authentication method of wireless mesh network
A technology of wireless mesh network and authentication method, which is applied in the field of authentication in wireless mesh network, can solve problems such as transplantation application, security problems restricting the large-scale implementation of wireless mesh network, and affecting network communication security, so as to achieve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
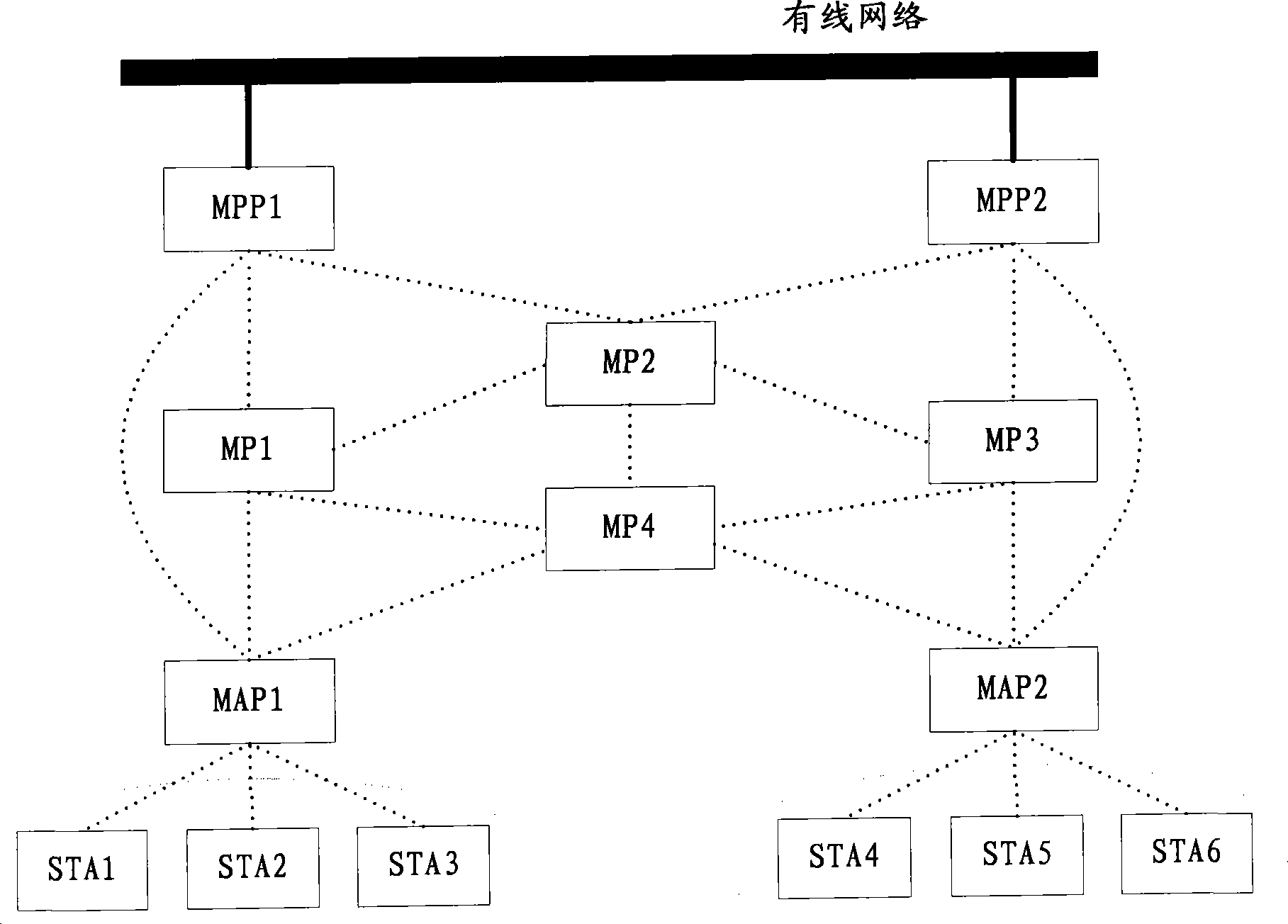
[0030] see figure 2 As shown, it is a schematic flowchart of Embodiment 1 of the WAPI-based wireless mesh network authentication method of the present invention.
[0031] In this embodiment, the default authentication server AS has issued corresponding certificates for each MPP, MP, and MAP node, and these MPPs, MPs, and MAPs have also installed the certificates issued to them by the authentication server AS. , and the authentication and authentication server is in a routeable location in the wired network.
[0032] Such as figure 2 As shown, the method in this embodiment includes steps:
[0033] Step S101: The requesting node completes the association with the node that has connected to the network, and proceeds to step S102;
[0034] Step S102: The node that has connected to the network sends authentication activation information to the requesting node, wherein the authentication activation information may specifically include the identification of the authentication ac...
Embodiment 2
[0056] see image 3 As shown, it is a schematic flow chart of Embodiment 2 of the WAPI-based wireless mesh network authentication method of the present invention. In this embodiment, it is mainly aimed at the description of the authentication process when a station accesses the network.
[0057] Such as image 3 As shown, it specifically includes steps:
[0058] Step S201: The station completes the association with any MAP node that has been connected to the network, and proceeds to step S202;
[0059] Step S202: The MAP node that has connected to the network sends authentication activation information to the station, wherein the authentication activation information may specifically include the identification of the authentication activation information, the identity information of the authentication server, and the certificate of the MAP node that has connected to the network and other information, because the identification process of WAPI adopts the elliptic curve signat...
Embodiment 3
[0117] see Figure 5 As shown, it is a schematic flowchart of Embodiment 3 of the WAPI-based wireless mesh network authentication method of the present invention. In this embodiment, it is mainly described for new nodes that newly join the network.
[0118] Such as Figure 5 As shown, it specifically includes steps:
[0119] Step S301: The new node completes the association with each node that has been connected to the network, and the process of completing the association between the new node and each node that has been connected to the network can be in any order, and enter step S302;
[0120] Step S302: Each node that has connected to the network sends authentication activation information to the new node, wherein the authentication activation information may specifically include the identification of the authentication activation information, the identity information of the authentication server, and the node that has connected to the network. Information such as certifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com